25.07: protocol "options" in default block all rule
-
I upgraded my 1100 from 24.11 to 25.07 yesterday. Since then I have seen a ton of blocks on my OPT (wireless) interface of IPv6 traffic, see attached screenshot, with protocol "options"
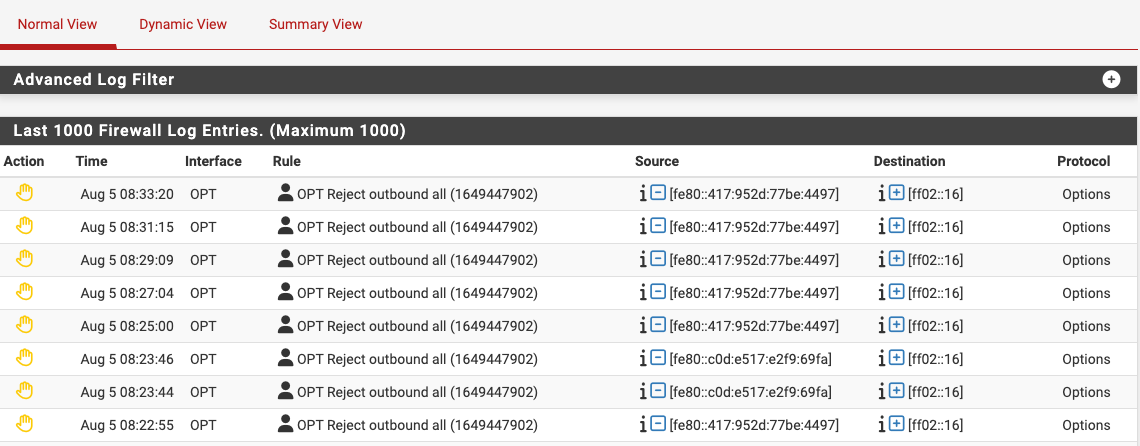
This seems to be ICMP broadcast traffic -- I cannot find the addresses ending in 4497 and 69fa in the NDP table or anywhere else so I don't know the source.
I went into the advanced area of the rule and turned on "allow packets with IP options to pass". That did not quell the block msgs. Plus I don't want ICMP traffic to be tracking my devices anyway. I tried both "block" and "reject", no difference. The rule looks like:
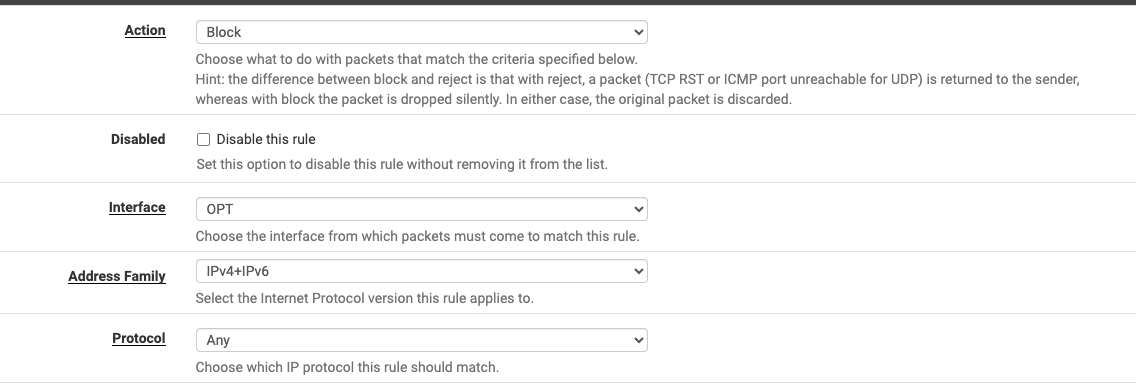
What is going on here?
-
-
@beerguzzle ff02::16 is not icmp it is multicast "All MLDv2-capable routers"
If you want to create a rule to allow that doesn't log that you would need to set options in the rule, and then set it not to log.
what is the order of rules on your opt interface? outbound is only available in the floating tab.
-
https://redmine.pfsense.org/issues/16194
Hover your mouse over the action icon and look at the details it shows you there.
-
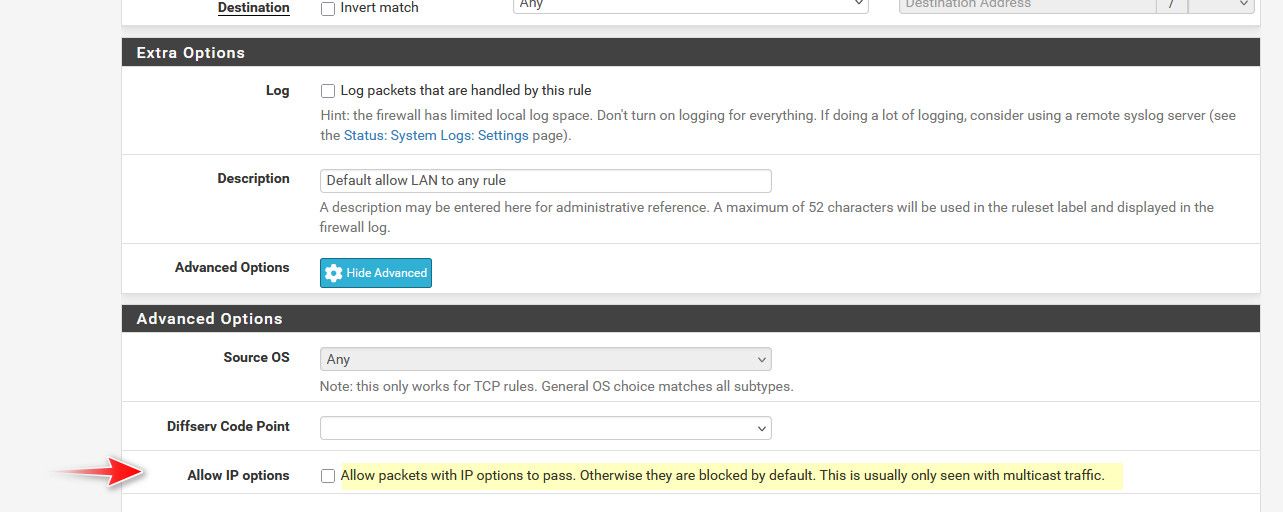
This rule is the last (bottom) rule for my OPT interface, a default "block anything not allowed above" rule. I have a similar rule for LAN, that also fires this "options" blurb too in 25.07. Hovering over the action shows:
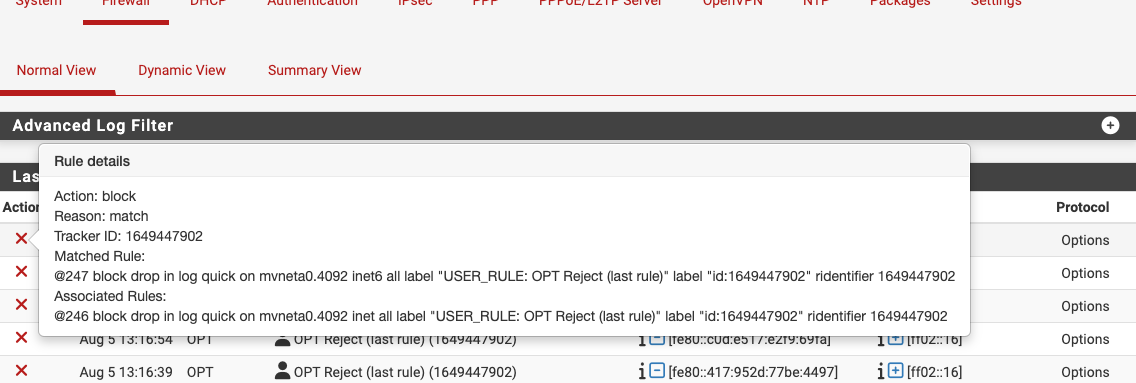
which looks similar to (but not identical) to redmine 16194.
I went into advanced options for the rule and turned on "Allow IP options", but nothing changed after the rules reloaded.
I also searched the pfsense docs for MLD, not much came up. In head scratch mode. Is this a redmine 16194 style "feature"?
-
If you can find the line that corresponds to those log messages in
/var/log/filter.log, copy/paste it here. It may be a similar packet to the redmine issue but maybe not identical.Since I was able to reproduce the one I was seeing I got a packet capture of it to see what it was, but depending on what you are seeing that may not be viable.
-
Here it is:
Aug 5 13:49:59 cleo filterlog[66564]: 247,,,1649447902,mvneta0.4092,match,block,in,6,0x00,0x00000,1,Options,0,56,fe80::417:952d:77be:4497,ff02::16,HBH,PADN,RTALERT,0x0000,
which should match with this from the gui:
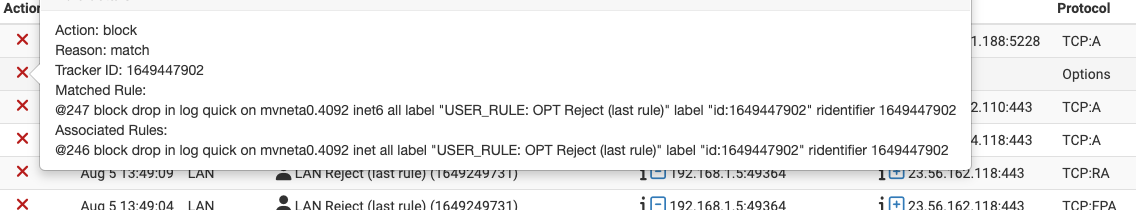
-
I'll state the obvious here... I went to System->Advanced->Networking and unchecked "Allow IPv6". Poof, the firewall log entries went away. I had found the reddit webpage on this topic:
https://www.reddit.com/r/PFSENSE/comments/1hzmc5y/ipv6_noise_protocol_options_to_ff0216/
and started down knox203's suggested fix for quieting the syslogs. I already had "Allow IPv6" checked, and wondered why I need IPv6 on my network at all. Unchecked it and bliss.
-
@beerguzzle said in 25.07: protocol "options" in default block all rule:
and wondered why I need IPv6 on my network at all
You, as a person, you don't.
Look again at our LAN network. Get you hands on a dumb switch - also known as a hub, and now do some network sniffing for IPv6 packets on your LAN and you discover that most IP traffic is IPv6 - not IPv4.
Only traffic to and from the Internet is still IPv4 for you, because you didn't set it up yet - or maybe your ISP doesn't support it.True, you have still some time to dive into IPv6.... but the clock is set and counting ;)
-
@Gertjan said in 25.07: protocol "options" in default block all rule:
LAN and you discover that most IP traffic is IPv6 - not IPv4.
Not true at all..
You will most likely see a lot of extra noise from IPv6 from window machines - most iot devices don't even support IPv6, and they don't use it to talk to each other that is for sure.
While true IPv6 is the future - if you have no need to access public resources via IPv6, name one resource you want/need that is only IPv6 or your not stuff behind some cgnat for IPv4 and need IPv6 to allow for unsolicited inbound traffic. The typical user has zero need for IPv6.
If I access my nas via its rfc1918 IPv4 address, it doesn't in the background say oh, I am going to use IPv6 to transfer these files. Because that nas also has a IPv6 link local address.
My isp doesn't even provide IPv6 if I wanted to use it. And shoot most isp that do provide it, do so in some borked fashion.
Even if devices did use it internally between devices on the same L2. linklocal doesn't route, so from the point of view of the user on their router, it means nothing.
-
@johnpoz said in 25.07: protocol "options" in default block all rule:
Not true at all..
True, a load of conditions apply.
If the network is mostly cameras doorbells and other (look to the east) 'connected stuff', IPv4 is probably used more. That said, the small stuff normally don't transfer a lot of data.But the classic company network, my case : a load of windows PCs and servers, unifi stuff, NAS (Syno) and 'modern networked printers : I persist : IPv6.
All 'recent' PCs phone pad etc OSes use IPv6 be default.
For that to happen, true, IPv6 must work flawlessly of course. A 'perfect' IPv6 starst with an ISP that supports it.A global overview of IPv6 usage in the ancient world (Europe, France to be exact) : Baromètre IPv6 Arcep 2025
edit : even amazon and facebook (in Europe) went full '6' recently.
edit : I found a command on my PC that tells me .... well, look for yourself :
C:\Users\Gauche>netstat -s Statistiques IPv4 Paquets Reçus = 4546224 Erreurs d’en-tête reçues = 0 Erreurs d’adresse reçues = 2 Datagrammes transférés = 0 Protocoles inconnus reçus = 0 Paquets reçus rejetés = 52200 Paquets reçus délivrés = 4517503 Requêtes en sortie = 1816206 Routages rejetés = 0 Paquets en sortie rejetés = 0 Paquet en sortie non routés = 4 Réassemblage requis = 0 Réassemblage réussi = 0 Défaillances de réassemblage = 0 Fragmentations de datagrammes réussies = 0 Fragmentations de datagrammes défaillantes = 0 Fragments Créés = 0 Statistiques IPv6 Paquets Reçus = 8223619 Erreurs d’en-tête reçues = 0 Erreurs d’adresse reçues = 99 Datagrammes transférés = 0 Protocoles inconnus reçus = 0 Paquets reçus rejetés = 6430 Paquets reçus délivrés = 8237200 Requêtes en sortie = 3910188 Routages rejetés = 0 Paquets en sortie rejetés = 1 Paquet en sortie non routés = 0 Réassemblage requis = 8 Réassemblage réussi = 4 Défaillances de réassemblage = 0 Fragmentations de datagrammes réussies = 0 Fragmentations de datagrammes défaillantes = 0 Fragments Créés = 0 Statistiques ICMPv4 Reçus Émis Messages 307 4655 Erreurs 0 0 Destination inaccessible 66 4178 Temps dépassé 117 0 Problèmes de paramètres 0 0 La source s’éteint 0 0 Redirections 0 0 Réponses échos 124 0 Echos 0 477 Dates 0 0 Réponses du dateur 0 0 Masques d’adresses 0 0 Réponses du masque d’adresses 0 0 Sollicitations des routeurs 0 0 Annonces des routeurs 0 0 Statistiques ICMPv6 Reçus Émis Messages 33934 36651 Erreurs 0 0 Destination inaccessible 7 3247 Paquet trop grand 1 0 Temps dépassé 333 0 Problèmes de paramètres 0 0 Echos 0 1071 Réponses échos 86 0 Requêtes MLD 0 0 Rapports MLD 0 0 MLD appliqués 0 0 Sollicitations des routeurs 0 2 Annonces des routeurs 841 0 Sollicitations du voisin 19556 12773 Annonces du voisin 13110 19558 Redirections 0 0 Renumérotation du routeur 0 0 Statistiques TCP pour IPv4 Ouvertures actives = 21632 Ouvertures passives = 4966 Tentatives de connexion non réussies = 835 Connexions réinitialisées = 1549 Connexions en cours = 31 Segments reçus = 4717564 Segments envoyés = 3744453 Segments retransmis = 3531 Statistiques TCP pour IPv6 Ouvertures actives = 15844 Ouvertures passives = 506 Tentatives de connexion non réussies = 708 Connexions réinitialisées = 1772 Connexions en cours = 29 Segments reçus = 8004344 Segments envoyés = 3715614 Segments retransmis = 491 Statistiques UDP pour IPv4 Datagrammes reçus = 2437005 Aucun port = 52126 Erreurs reçues = 0 Datagrammes envoyés = 135305 Statistiques UDP pour IPv6 Datagrammes reçus = 232795 Aucun port = 6356 Erreurs reçues = 0 Datagrammes envoyés = 151262yeah sorry, it's VO language :(