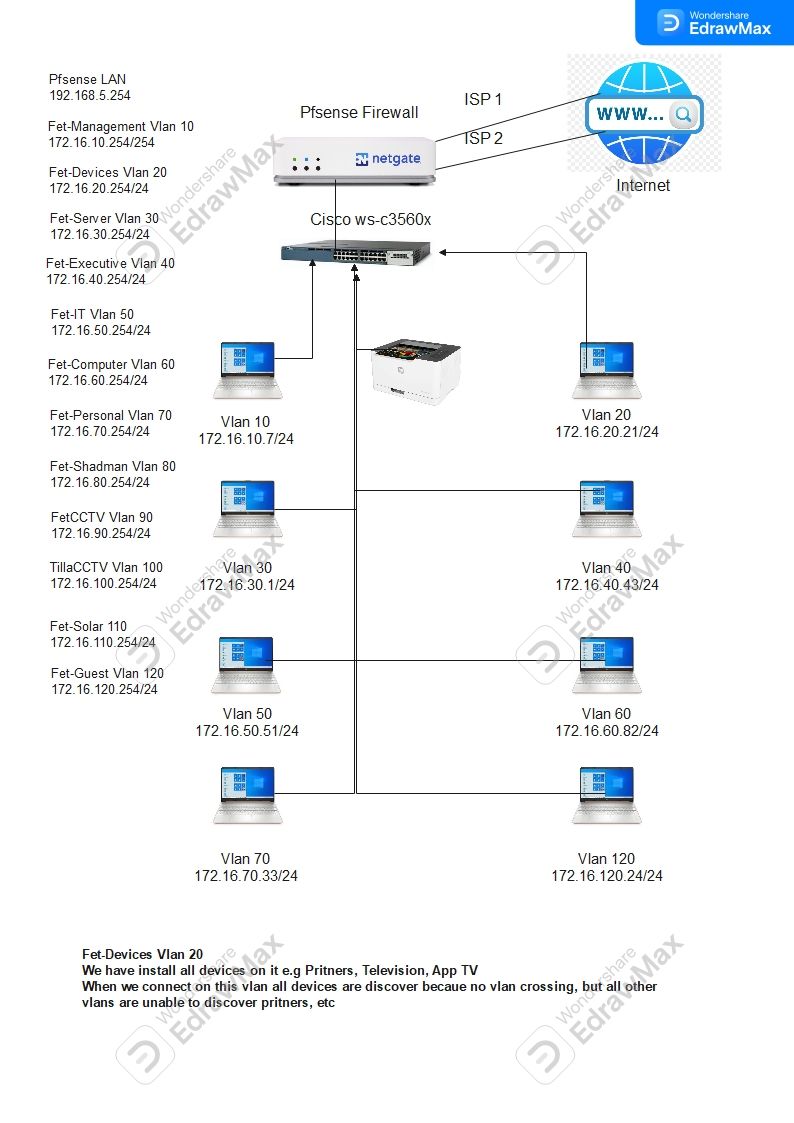
mDNS or Multicast Traffice Not Passing Between Multiple Vlans
-
@ayansaari said in mDNS or Multicast Traffice Not Passing Between Multiple Vlans:
I follow your seggestions but still unable to access printer devices from the other vlan
"unable to access printer devices" isn't sufficient detail to identify your issue.
Are you using an mDNS browser and not finding any entries? If so, this would be an Avahi issue. If this is what you are seeing, please post screenshots of the mDNS browser when connected to the various network segments.
Or are you seeing the printer, but not able to connect to it? If so, this would be a firewall rules issue. I'm sure you are aware of this, but just to make sure, mDNS (Avahi or mdns-bridge) is only used to facilitate discovery of services. Actual access to the services following discovery would be controlled by firewall rules. If this is what you are seeing, have you checked the firewall log?
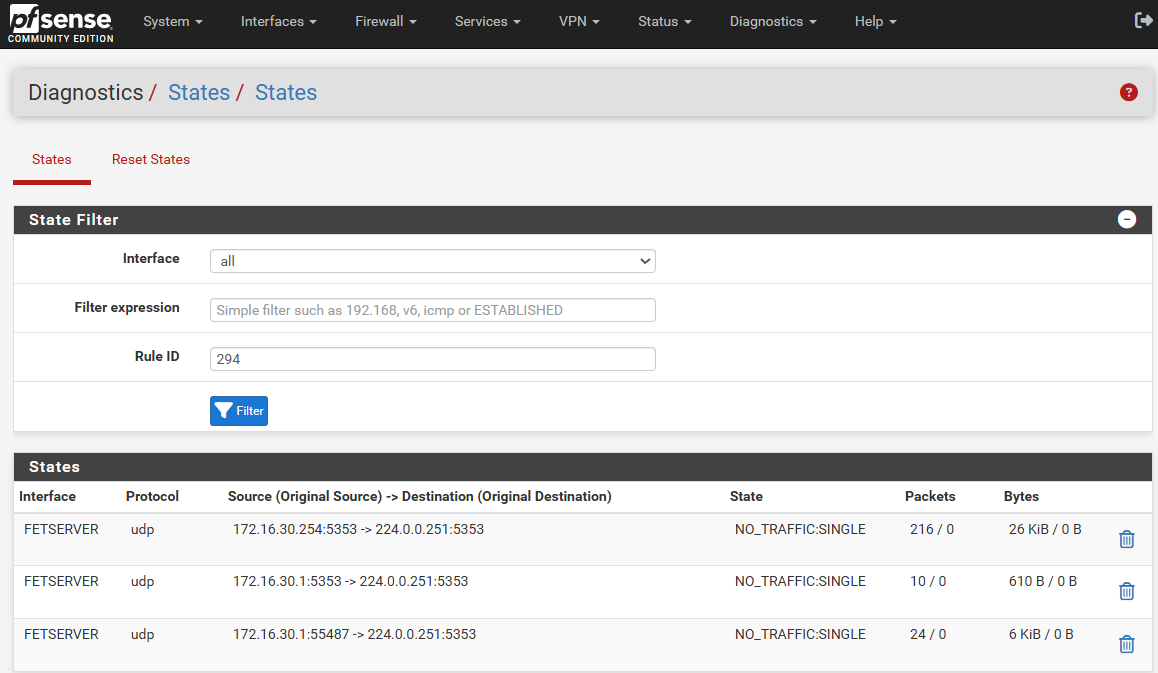
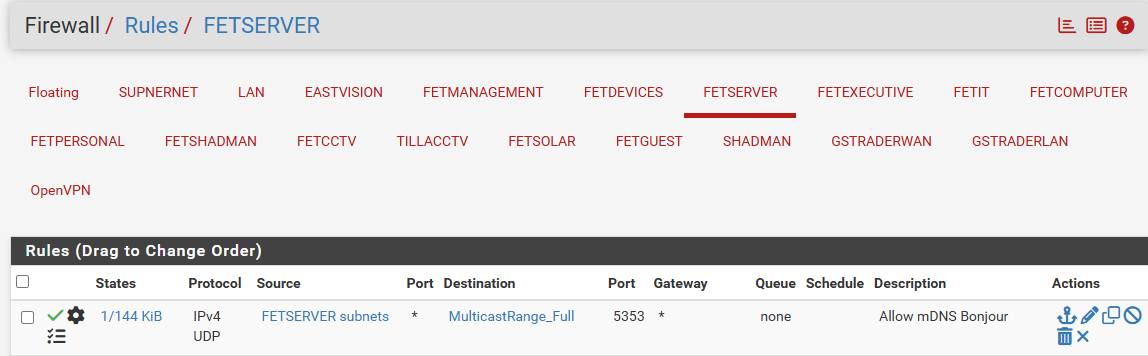
FWIW, assuming that your firewall is at address 172.16.10.254, your states information for FETMANAGEMENT shows for that the firewall has received mDNS from hosts .7, .8 and .9, and also sent messages. Did you disable publishing in Avahi as I suggested? Assuming so, messages sent from the firewall would be mDNS information that has been forwarded from another interface.
That's the only interface shown, so I cannot say anything about the others... Have you looked at all the interfaces to check mDNS activity? Choose Interface "all" and filter on "5353".
-
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
@ayansaari Two things I told you previously:
Please re-read my posts above.
As I said previously, firewall rules are not used to forward mDNS. The firewall rule forwarding port 5353 has absolutely no purpose. Avahi does not forward packets from the source network to the destination network -- it sends packets that it creates to the destination containing information gathered from packets it receives in the source network.
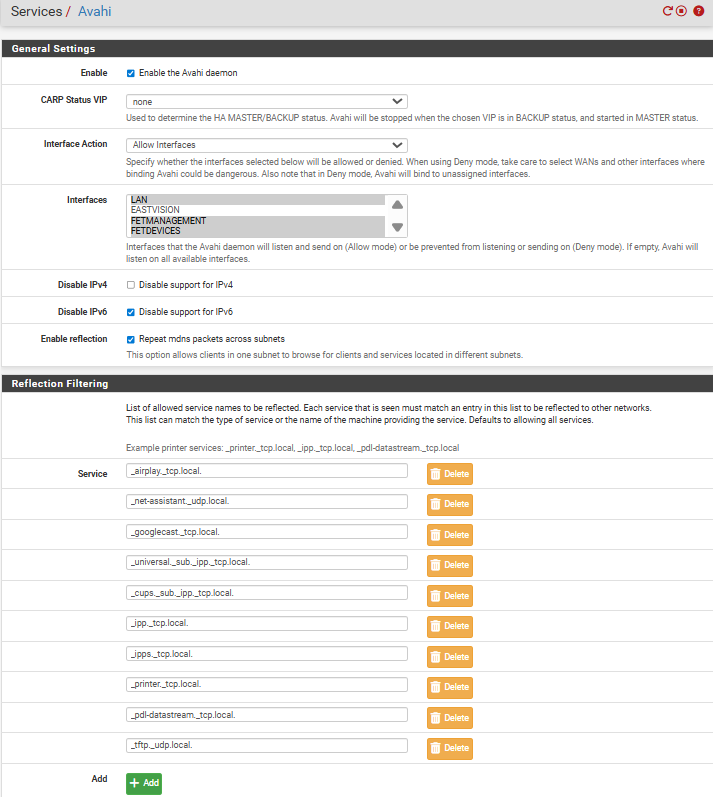
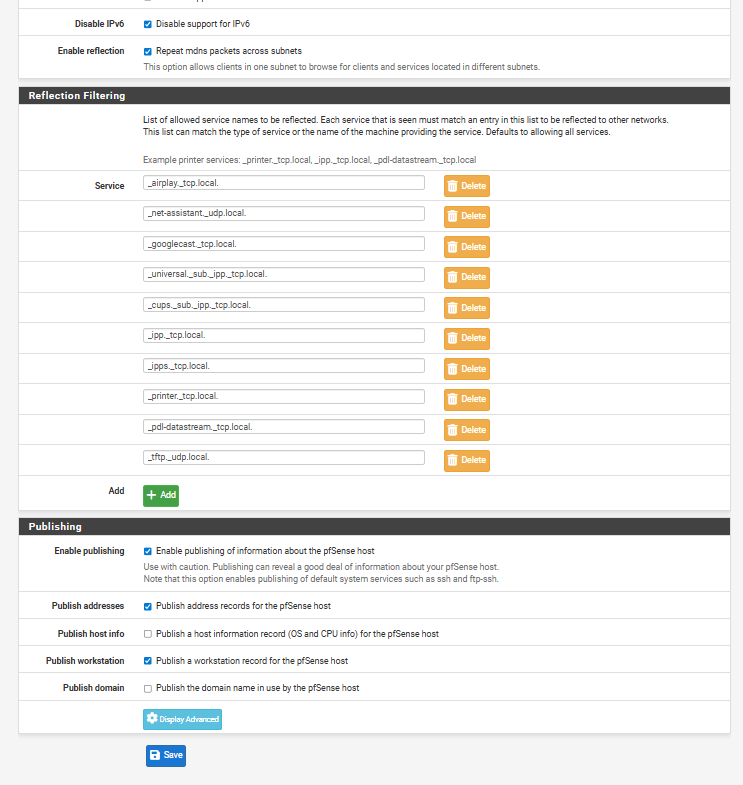
Also as I said previously, remove every entry you have in the Service list for Avahi Reflection Filtering, and do not add any entries to the Service list until you have successfully tested. And again, disable Avahi Publishing -- having this enabled is a bad idea, especially if you do not understand the basics of mDNS.
-
@dennypage I’ve tried almost everything to resolve this issue, but I’m still unable to find a solution. I also asked you to give me a few minutes to check it remotely, but unfortunately, you didn’t respond to my request.
Sometimes, live support is necessary—please try to understand.
Just for remote access
+92 321 4050 320
ayansaari@gmail.com -
Why not just add the printer by IP address and forget about mDNS?
But if you must did you try an mDNS browser to see what is being advertised?
-
@ayansaari said in mDNS or Multicast Traffice Not Passing Between Multiple Vlans:
I also asked you to give me a few minutes to check it remotely, but unfortunately, you didn’t respond to my request.
Are you asking to hire me as a consultant to fix your firewall via remote login? I don't think that is a particularly good choice, not only for security reasons, but also for cost reasons -- I am very, very expensive.

I recommend you hire someone locally who has pfSense experience instead. Failing that, I believe Netgate offers professional services. I don't know what countries they offer services in or what their rates are, so you would have to contact them and ask.
-
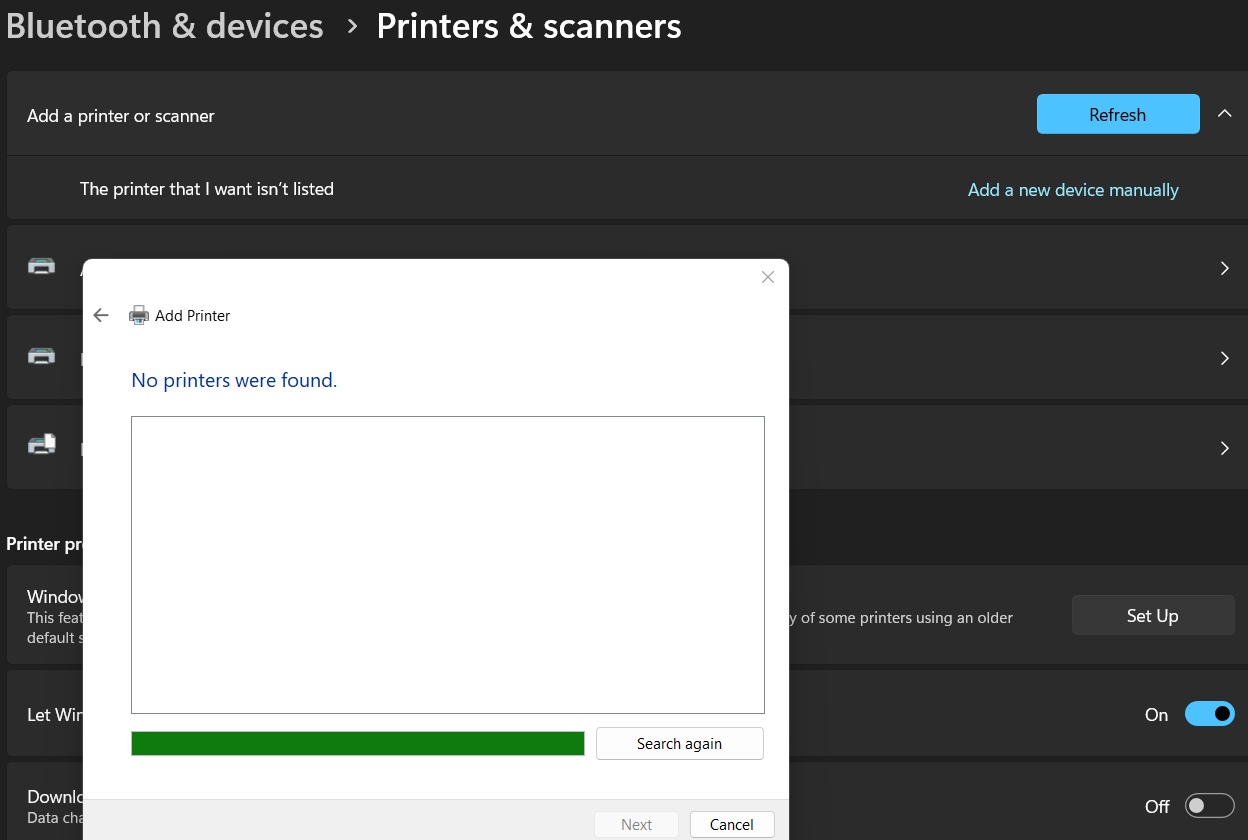
@stephenw10 dear I was tried by giving IP Address of the printer and no chance to discover it
I think Pfsense is not have the ability to multicast traffic between vlans
-
If you add the device by IP address then mDNS is not involved at all. No multicast traffic is required. The firewall just routes traffic between the subnets like any other traffic.
Now you may not be able to add things by IP because for some reason developers like to remove that option in order to somehow make it.... easier I guess.

But if you can, like in Windows, it should just work. -
@dennypage dear as you give suggestions I done at and still unable to discover devices from the other vlans
so I think pfsense is not have the ability to manage multiple vlans
I think it is a good firewall when we have a single subnet -
@ayansaari said in mDNS or Multicast Traffice Not Passing Between Multiple Vlans:
I think pfsense is not have the ability to manage multiple vlans
Of course it does. Most pfSense deployments include multiple subnets.
So when you used an mDNS/Bonjour browser tool to discover advertised services what did it show?
-
This is my setup and this is the IoT VLAN where the printer is located, and this VLAN is isolated:
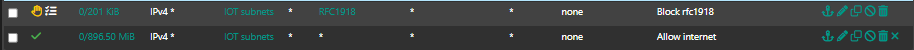
This is the only VLAN where I created a rule to allow access to the printer:
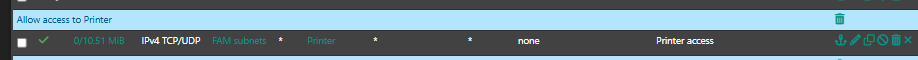
and is isolated too.
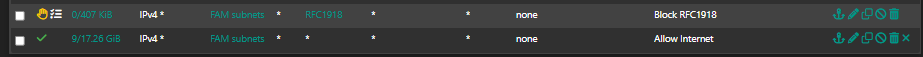
From my LAN network, I can access the printer without creating any rules. My computer discovers the printer on the IoT VLAN.
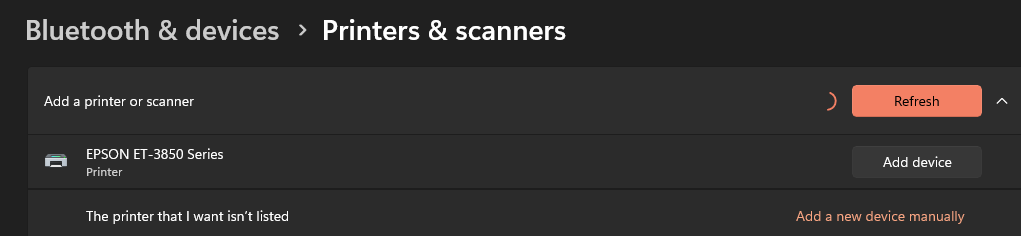
But I do have mDNS rule active under Floating rule:
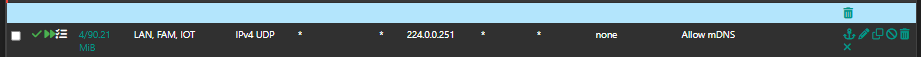
The interfaces is: LAN, FAM and IOT
And I have Avahi installed with the same interfaces active
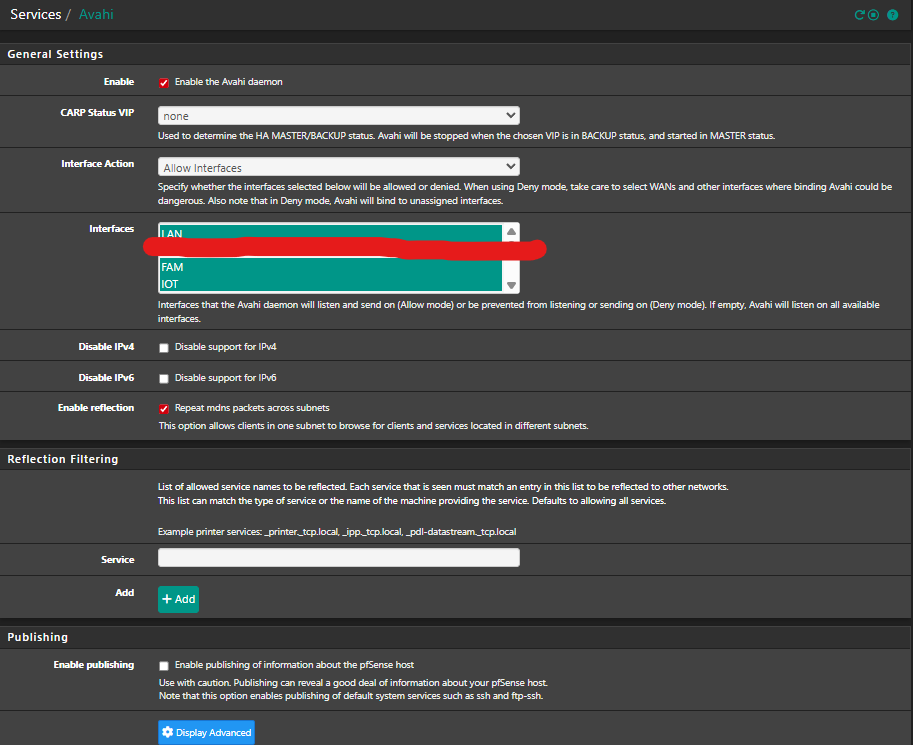
-
Yeah, just to prove it out I ran a simple test. Since I don't have anything I can easily use that advertises mDNS I just turned on Publishing in Avahi itself on 4 firewalls:
steve@steve-NUC9i9QNX:~$ mdns-scan + 4860 [00:08:a2:xx.xx.xx]._workstation._tcp.local + 4860._ssh._tcp.local + 4860._sftp-ssh._tcp.local + fw1 [00:08:a2:xx.xx.xx]._workstation._tcp.local + fw1._ssh._tcp.local + fw1._sftp-ssh._tcp.local + pfsense [00:01:21:xx.xx.xx]._workstation._tcp.local + pfsense._sftp-ssh._tcp.local + pfsense._ssh._tcp.local + 1100-3 [f0:ad:4e:xx.xx.xx]._workstation._tcp.local + 1100-3._sftp-ssh._tcp.local + 1100-3._ssh._tcp.localIn that result 4860 is in the same subnet as the client I'm testing from. fw1 is the router on that subnet. pfsense and 1100-3 are other firewalls in different subnets connected to fw1.
You can see the scan tool is able to see all of them no problem.