Nat stop working after certificate renewal
-
@nirmelamoud said in Nat stop working after certificate renewal:
The rules are specific client IP to specific port go to specific local IP , same port - and I have like 5 rules like that
Maybe show them but it is highly unlikely that this is related unless the certificate was also used somehow elsewhere?
-
@nirmelamoud Yeah, unless it's not only NAT but perhaps a HA Proxy reverse HTTPS config you are running, then certificate renewal will have no impact on access through the firewall.
-
HA Proxy ? Other web servers using the same certificate (@Bob.Dig ) ?
Normally (in my world, that is), certificates are renewed way before they expire.
So the system worked before renewal. If something went wrong, and the GUI died because the new certificate was 'invalid/broken/other problem' the the GUI would fail to start up. But the loss of the pfSense GUI will not stop NAT rules from working.edit : True, a lot of info is missing ....
-
@Gertjan said in Nat stop working after certificate renewal:
HA Proxy ? Other web servers using the same certificate (@Bob.Dig ) ?
Yeah, if the OP is running HA reverse proxy on his pfSense using the WebUI certificate for HTTPS reverse proxying, then HA proxy needs to have the new certificate selected for reverse HTTPS publishing.
-
@nirmelamoud said in Nat stop working after certificate renewal:
the error I get with the browser is access denied
The logs show that the default IP4 rule blocks the accessIf the firewall blocked your access - your browser wouldn't show an error, it would just time out.
Can you post up the error page your seeing in the browser. As mentioned if something wrong with cert and you were using haproxy, its possible that could give you some sort of browser error back.
But if the firewall did not forward your traffic, and denied it in the logs then your browser would never haved talked to the webserver your forwarding too - so there would be no error in your browser other than hey couldn't talk to that. It would not be an access denied message if the client never actually talked to your webserver.
Are you using HA Proxy as reverse to your stuff behind pfsense? If so - why would it be using the web gui cert? Are you using ACME wild card cert or something? But that you mention web configuration for the certificate - that seems to indicate just the self signed web gui cert, which really wouldn't make a lot of sense to use in reverse proxy.
-
@Bob.Dig no haproxy
-
The client's browser has a white page with nothing but "access denied."
The system log shows" Aug 21 19:21:40 WAN Default deny rule IPv4 (1000000103)"but I do have a NAT rule that was working few days ago, for specific IP addresses, to allow them in
all of them stop working (without client IP change)Im not sure the certificate is related of course, but that's the only change I made, right before it stopped working
The router UI is workingI use direct DNS rules in CloudFlare (so the port will work as its not a standard port) but its not related to CloudFlare as even if the browser go to my direct IP , I see the same behavior
any idea how I Can debug this , find why the rules been passed through ?
the rule is basically single host - specific IP, from to port (both other -- both 8200) redirect to internal IP, same other port 8200
nat reflection - default -
@nirmelamoud said in Nat stop working after certificate renewal:
The client's browser has a white page with nothing but "access denied."
That is not what would happen with a firewall block.. Even with a redirection.
So here are the 2 different blocks - a just block, ie firewall just ignores the traffic.
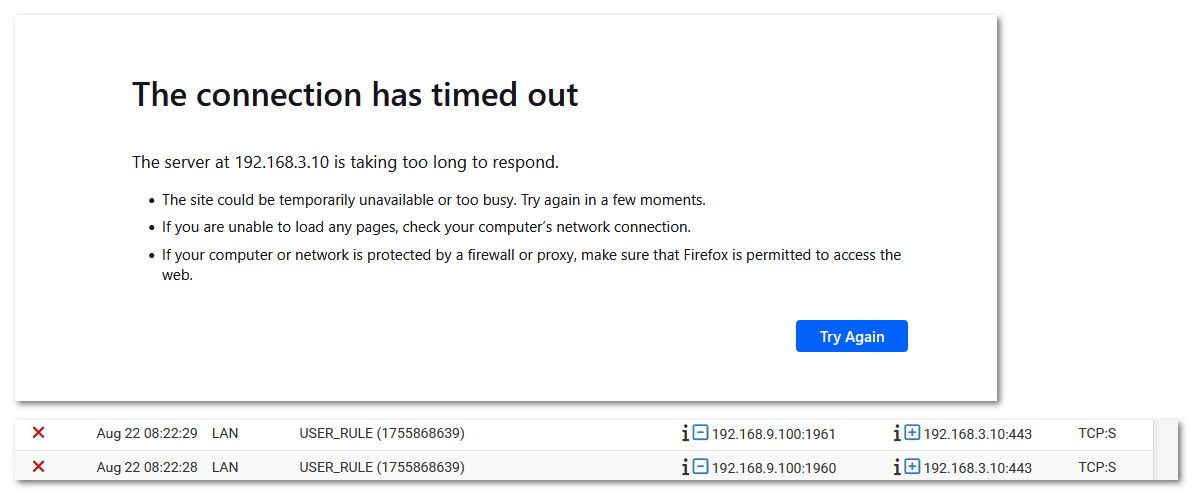
And then here is a actual reject where the firewall sends a response saying hey you can't get there..
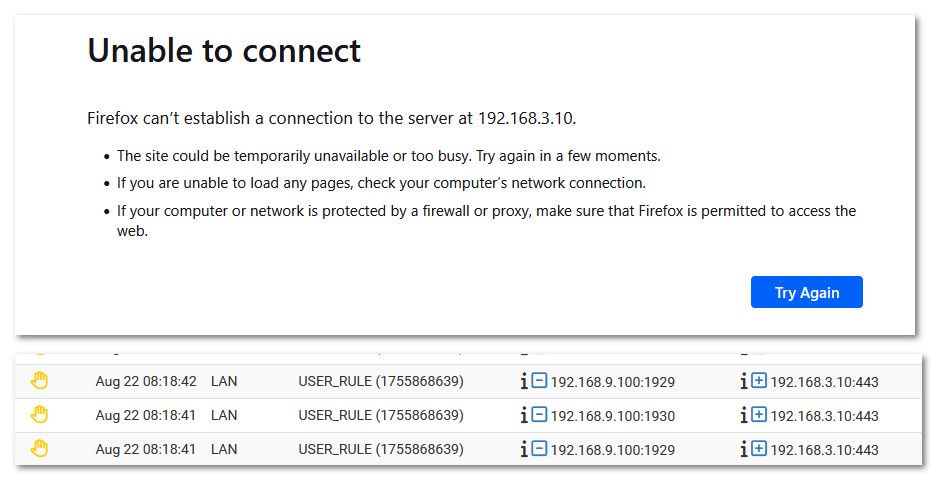
For browser to say access denied, the only way it should really know that is if the webserver trying to talk said hey buddy sorry your not allowed, which would be a 403 error.
So not exactly sure what is going on, but would follow standard port forwarding troubleshooting..
Here is how chrome shows it
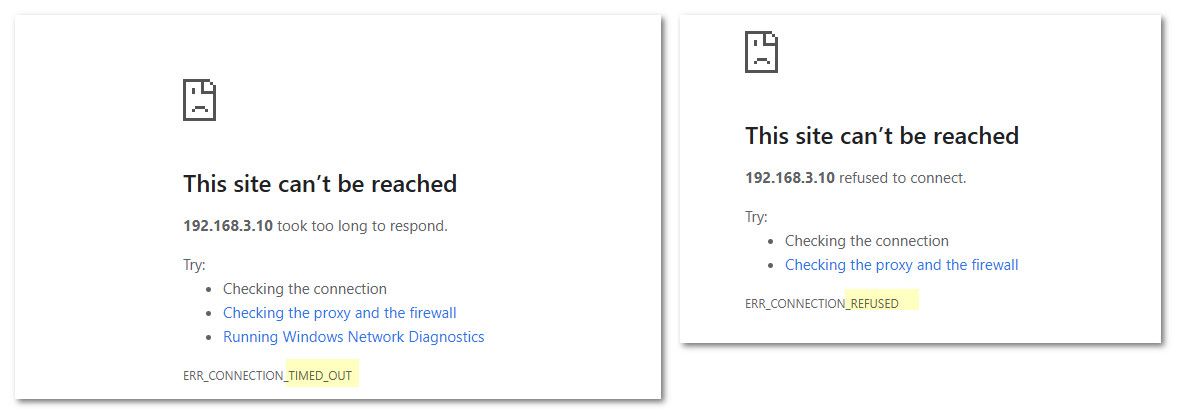
What browser are you using? But a access denied would come from the webserver or a proxy, not a firewall even with a reject.
Are you forwarding this traffic to some internal proxy you are running?
-
@johnpoz THANKS for the detailed respone,
my rounter fw it to another router that fw it to a web server
I do not see the traffic in the internal router
I see the rule on the external router that say it block the traffic , so I do not think it passed the fw
agree I do not understand why I see access deniedI used edge and chrome (on windows, and chrome on android phone)
I do have pfblockgerNG on, but dont think its involved, it is blocking mainly other countries
-
@nirmelamoud said in Nat stop working after certificate renewal:
I see the rule on the external router that say it block the traffic , so I do not think it passed the fw
pfSense is the internal router or the external ?
-
@Gertjan pfsense is the external
-
@nirmelamoud again troubleshoot the problem.. If traffic from outside hits your pfsense wan and is blocked by the default rule, then your rules are not right, they didn't load?
Do you have rules in floating? Lets see your port forward rules and the rules you have on pfsense wan..
None which would have anything to do with renewing the web gui certificate.
edit: btw if hit IP you talked to the forum with on just http (port 80) stuff is served - looks like some pictures. https times out.
-
@johnpoz no floating rules, all rules
all these nat rules are https , I do have one HTTP rule, and its working.
I do not see any https timeout anywhere is the logs,any command line trick (or logs to look at) to see if NAT rules not loaded (although I see them on the NAT table) ?
-
@nirmelamoud do a cat /tmp/rules.debug
Here is how you can see the full ruleset
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
You can always reload them and look at the output.
Status / Filter reload
What rules I see no rules posted - all rules tell me nothing..
https timeout anywhere is the logs,
Why would you think you should see anything of the sort in the logs.. I already went over this is great detail. A timeout in your browser is if pfsense blocked the traffic..
if you want any help your going to have to give us something to look at to see if we can spot where the problem is..
example
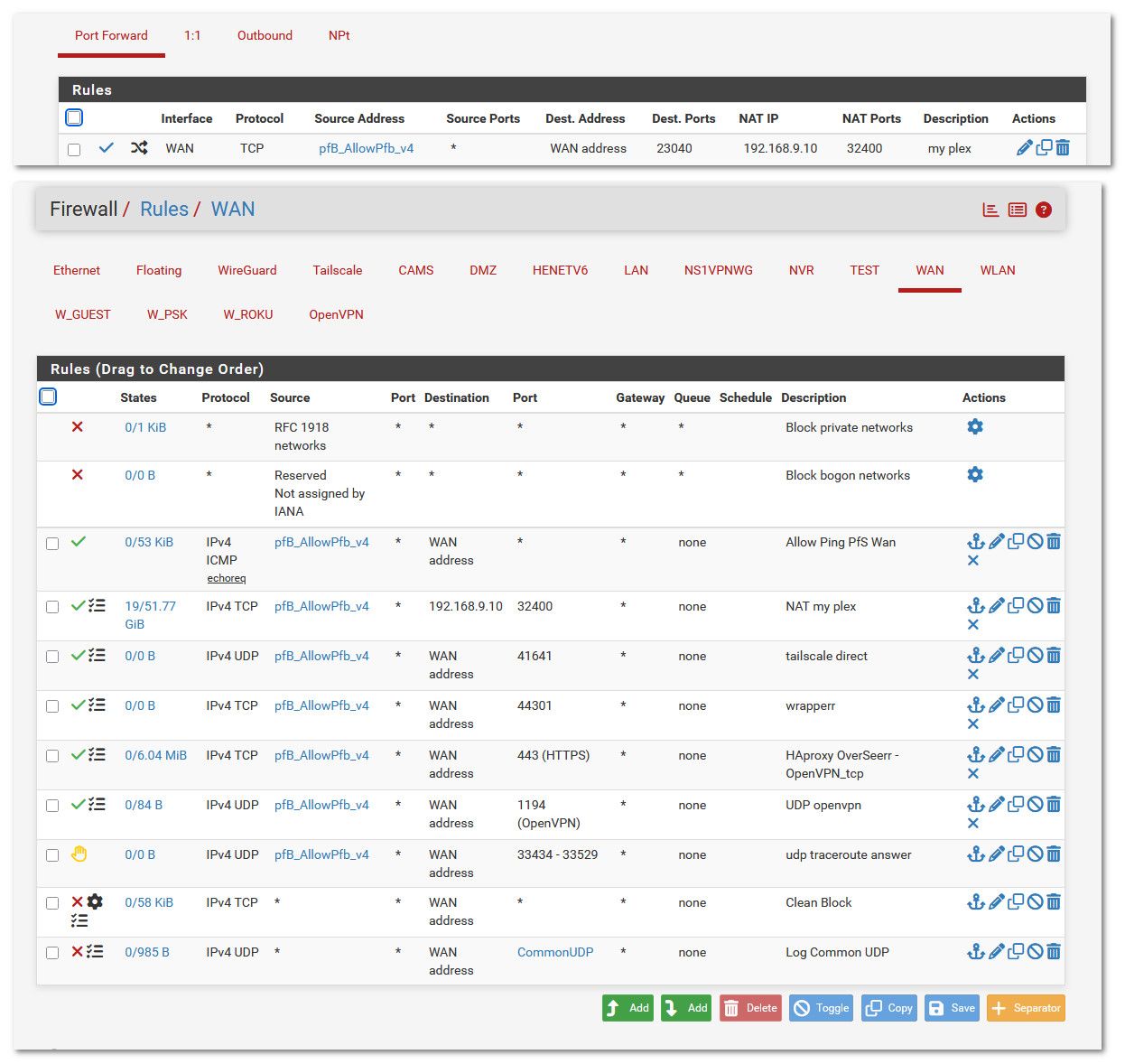
-
@johnpoz
thanks I see all the rules in the command prompt , as I said there is no timeout on browser I See access denied (its 403) -
@nirmelamoud said in Nat stop working after certificate renewal:
I See access denied (its 403)
There is no possible way pfsense could do that - and when I go to the IP and see your website with pictures via https - I just get a timeout I get no 403, a 403 is telling you you can't got there.. Not the firewall.
And if your seeing traffic to 443 blocked in the logs - why/how could it be sending a 403??? You understand when you block in a firewall all it does is ignore the traffic.. So your client just never gets an answer.
If you are not going to actually show us your rules, rule order matters, maybe you have it set for udp or something, nor do any off the basic port forwarding troubleshooting that takes all of 30 seconds tops to do - nobody is going to be able to help you..
Go to can you see me . org - send traffic.. Sniff on your wan do you see the traffic come in.. Do you see any sort of response, ie a Syn,ACK?
If you see no response, now sniff on the lan side do the same test do you see pfsense send on the traffic.. If you do then pfsense did its thing whatever is not working for you has zero to do with pfsense.