upgraded to pfsense 2.8.0, WiFi devices report intermittent 'no internet access'
-
@skubany2 that is an OUTBOUND rule.. So you have some rule in floating..
That is the answer from server you were trying to talk to on port 80.. But you have an outbound rule in floating tab.. Why would you have such rules??
And what do you think hiding some rfc1918 address does you... Oh no your IP address is 192.168.1.42 - someone will hack you?? Like telling someone hey.. I am on the planet earth.. There is zero reason to hide rfc1918 space..
example;
$ ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : i9-win Primary Dns Suffix . . . . . . . : home.arpa Node Type . . . . . . . . . . . . : Broadcast IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No DNS Suffix Search List. . . . . . : home.arpa Ethernet adapter Local: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Killer E2600 Gigabit Ethernet Controller Physical Address. . . . . . . . . : B0-4F-13-0B-FD-16 DHCP Enabled. . . . . . . . . . . : Yes Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Lease Obtained. . . . . . . . . . : Wednesday, August 27, 2025 1:36:28 PM Lease Expires . . . . . . . . . . : Thursday, September 4, 2025 1:36:27 PM Default Gateway . . . . . . . . . : 192.168.9.253 DHCP Server . . . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 192.168.3.10 NetBIOS over Tcpip. . . . . . . . : EnabledThat is info from my pc - what do you think anyone could possible do with the info that my machine is 192.168.9.100 on a /24 network whose gateway is 192.168.9.253, and my pihole (dns is on 192.168.3.10..
What do you think someone could do with such info?
-
"hiding some rfc1918 address", I think I saw you reply similarly to someone else or at least someone did as I remember seeing something like this two days ago when I was looking into my issue :)
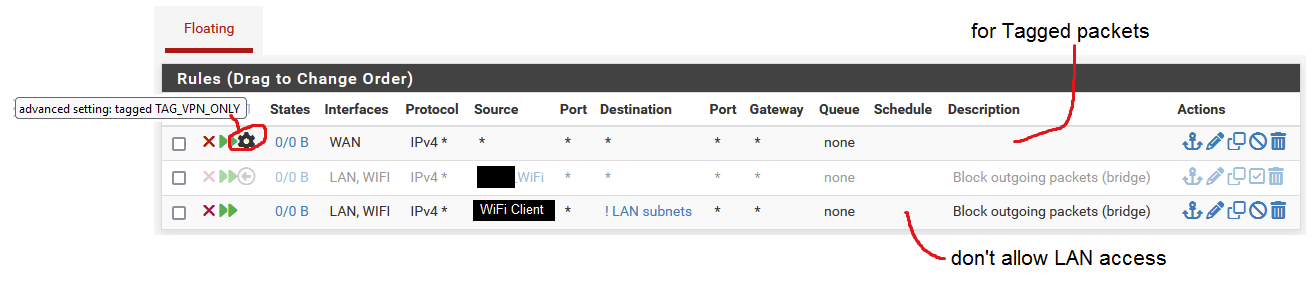
Onto "Outbound rule". I have three Floating rules. One disabled, another enabled but applies to a specific client which does not play a role in my troubles with TCP:SA. I set those up to enable Tagging for a 'VPN client' I was configuring on my router a while back but not using (disabled) at this time.
I run packet capture on WiFi interface:
First my WiFi AP (using MAC, APs MAC) sends RRB packet.
Then my cell phone (using MAC) sends LLC packet to Broadcast.
Then my cell phone (using MAC) sends ARP packet to Boradcast asking "who has <my LAN IP>?"
Then my WiFi Interface (using MAC, expansion card's MAC) answers to my cell phone.
Then my cell phone (using IP) sends syn to external_host:80.
Then my firewall log shows that the acknowledgement on LAN interface is blocked when sent by external_host to my cell phone (using IP). Ports on request and response match."using MAC" means that entries in packet capture are showing destination/source addresses as MAC.
"using IP" means that entries in packet capture are showing destination/source addresses as IP.Any of that looks out of place?
I tried capturing packets on WAN and LAN but that didn't really show anything interesting.
-
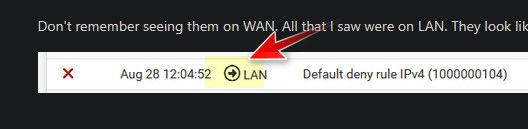
@skubany2 The rule clearly shows it blocks outbound on your lan - the only way to have outbound rules is in your floating tab - show a screen shot of your floating tab..
How do you have a default deny outbound rule?? Post up all your rules.. There is clearly something borked with your setup.
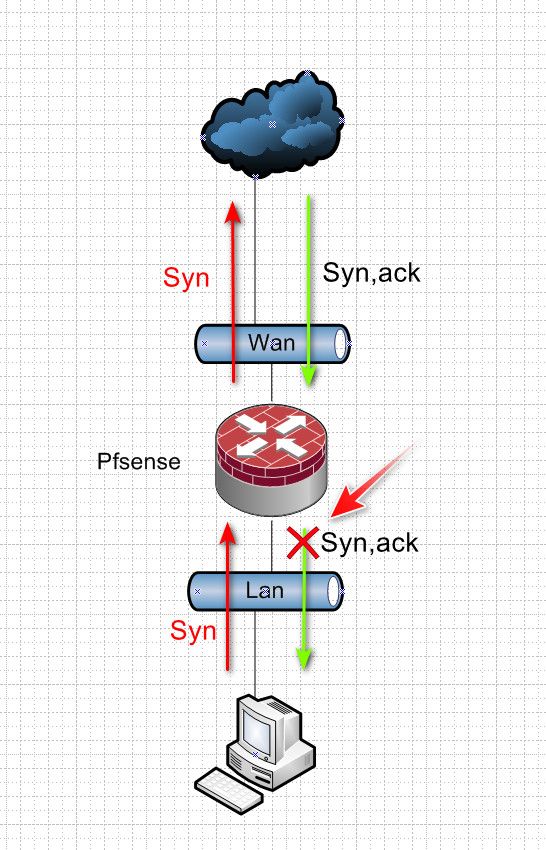
This is a client wanting to talk to something out on the internet - it sends a S (syn) to pfsense gateway, I want to go to 1.2.3.4, pfsense nats this traffic to your wan IP, lets say its 5.6.7.8 and sends it out its wan.. This is allowed by your normal default any any lan rule inbound into your lan interface, this creates a state..
When 1.2.3.4 answers your syn with a SA (syn,ack) he sends it back to your IP 5.6.7.8 pfsense says hey that is to port X from 1.2.3.4:80 that state I have says send to 192.168.1.100 because that is who I allowed out and created the state for.. This would be outbound on your lan interface..
That firewall log you posted says hey block outbound on my lan..
There should never be a block outbound on your lan like that, and it sure shouldn't be a default deny rule..
Your AP for wireless has ZERO to do with pfsense logging a default deny outbound on the lan.. Please post up your rules if you want help.
-
You will see blocks like that with the default outbound rule if the SYN from the client didn't come into the LAN. Which is excatly what the floating state binding would allow.
So it appears that you have some other route into the firewall that wifi clients are using. That is creating asymmetry and that is causing the problem here and should be corrected.
To make that happen though you need to have some unusual network setup like bridged interfaces perhaps?
-
-
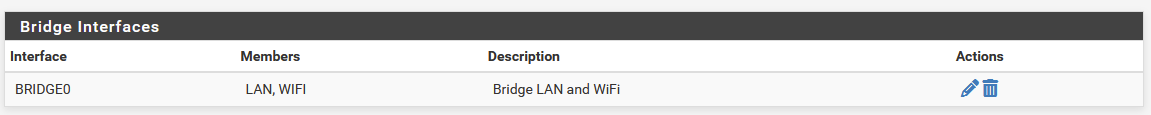
Yes, I do have a bridge and I expect that I will have to remove it and connect interfaces LAN & WiFi via rules.
-
You shouldn't have to you just need to make sure traffic is opening states on the correct interface.
Do you have bridge filtering set to the bridge members or the bridge itself?
Do you have the bridge assigned?
-
@stephenw10
I only have the bridge because when adding external AP the tutorials I looked at said I need it.
I don't have it assigned to anything. I don't filter on it. I don't explicitly use it for anything.In 'Floating' rules I had entries because under WiFi interface I have a rule that WiFi should not go out to 'LAN subnet'. I don't want WiFi devices to reach my LAN in general, unless explicitly allowed (via rules). Sometimes, the "WiFi Client" from the picture with Floating rules I posted reached my LAN and I wasn't sure why so I put a Floating rule to forbid it. The Floating rules are executed before any other in the firewall.
-
@skubany2 your last rule there where you say don't allow lan access is wrong.. That is a ! lan subnets - it would block everything that is NOT the lan subnets.
none of those rules show any hits..
-
I would guess that traffic from the clients is coming in the WIFI interface and going out the LAN because that's where the subnet is defined. The bridge allows that to work because everything uses the same subnet but pf sees that as asymmetric.
Unless you need to filter between the wired and wireless segments you should move filtering to the bridge, assign the bridge and add the subnet on the bridge directly with neither member having a subnet defined.
-
This is such a borked up config.. Why are you bridging? Why would you bridge if you don't want to allow wifi talk to lan?
I take it your again hiding your rfc1918 space where you put in wifi clients - so these are different networks - again why bridge?
What exactly are you trying to accomplish - there is almost never a good reason to bridge..
If you want to leverage a port on pfsense for your AP - then put it on its own network, and just allow what you want. If you want wifi on the same network as lan plug your AP into your switch.
If you want multiple networks on your AP via vlans and one of those is your lan network - then have a vlan capable switch and again plug your AP into your switch.
-
Commonly such a setup is used when you want to have wired and wireless clients in the same subnet but also want to filter traffic between them.
I hadn't, until now, considered how interface bound states might affect that.

But, I agree, it's almost always better to just use two subnets and not bridge them.
-
@johnpoz
You are right, I misspoke. The "WiFi Client" is not supposed to go out to the internet. I almost never use that client though. -
@johnpoz said in upgraded to pfsense 2.8.0, WiFi devices report intermittent 'no internet access':
This is such a borked up config.. Why are you bridging? Why would you bridge if you don't want to allow wifi talk to lan?
If you want to leverage a port on pfsense for your AP - then put it on its own network, and just allow what you want. If you want wifi on the same network as lan plug your AP into your switch.
If you want multiple networks on your AP via vlans and one of those is your lan network - then have a vlan capable switch and again plug your AP into your switch.
The config is at least 8 years old. I used to have pfSense run on a laptop with WiFi adapter. When moving my pfSense to a custom PC I decided that it is more flexible to have an external AP rather than internal. That way I can change AP in the future easily. Also choice of AP would not be dictated by support provided by Unix on which pfSense is based. To add an external AP to pfSense I jumped online to see how others do it. The tutorials I saw used bridging and so did I. I didn't really understand why but it worked so I was happy. I'm more versed now at working with pfSense and understand networking better than in the past, though as you can see I'm far from an expert.
I will be going (attempting) the route of running AP off of a dedicated pfSense port. This will give me the separation of LAN and WiFi and should work with 'Interface Bound States' in pfSense. I have an idea how to achieve that, so we'll see if it works.
-
Yup that will work if you don't need them on the same subnet.
Or moving the filtering and subnet assignment to the bridge interface would also work.
-
I am now configured with 'Interface Bound States' and no longer bridged.
Thanks for your help guys.
I like this way better. Better organized and more precise.
-
Nice. Yes that's a much better setup if you don't need them on the same subnet.

-
A related question. As I moved to unbridged LAN and WiFi networks, I noticed that a device on WiFi interface can't reach a device on LAN interface using it's host name. Using IP works.
What do I need to change in my firewall to fix this? I assume DNS is not propagating correctly.
When the two networks were bridged, this was not an issue.
-
Hmm, by default both subnets would use the pfSense interface IP as the DNS server. The would be Unbound in pfSense and if LAN devices are registered there then they should resolve for both subnets.
First try resolving from the wifi client and see how it fails. Perhaps that device is using a hardcoded DNS server? Did you ever include firewall rules to redirect DNS?
-
When the WiFi client is wired (cable) then it can access the other device via it's host name, because they're both on LAN at that point.
WiFi client is assigned DNS Servers by DHCP Server running on WiFi interface. I tried adding LAN's DNS Server as secondary entry under WiFi interface's DHCP Server but that did not change anything. I did notice at that point that WiFi client was showing two DNS Servers configured, instead of the usual one.
I did not explicitly set any DNS redirection firewall rules.