IPsec multiple Phase 2
-
Hi all,
I have a newbie question about IPsec :). I have set up IPsec with EAP-MSCHAPv2 and multiple Phase 2 split tunneling with destinations.
Tunel A - Client - Pfsense - 10.10.10.10
Tunel B - Client - Pfsense - 10.10.11.10
Is it possible to configure it so that, for instance, user A has access only to 10.10.10.10, and user B has access only to 10.10.11.10 or something similar to restrict access per user?
Thanks for help. -
@0x44 Yes, by not allowing the listed traffic in the firewall rules on the interface on which the clients exists. If you have a "any - any" rule there to allow full access to to internet (and in effect also everything else through VPN, the firewall itself and so on), create a block rule above that from the clients to the networks they are not allowed to reach.
-
@keyser I might not have expressed myself very clearly. But tunnels A and B share the same virtual IP pool, for example, 192.168.50.1/24, so the source IP address is the same for both tunnels.
In this configuration, both clients have access to both networks — 10.10.10.10 and 10.10.11.10. That means, in order to restrict access from tunnel A to tunnel B (or vice versa), we would need to filter by source IP in the firewall. However, since the source is the same for both tunnels, this becomes problematic.
Please correct me if I misunderstood your point or if I'm wrong about something.
Below is an example of the allow rules I'm currently using.

-
@0x44 I'm not quite sure I'm following your problem then.
pfSense does not have a "layer 7" user concept on which you can create rules (rules against users/identities). It only does layer 2/3/4 (Ethernet/IP/Protocol) filtering.You mentioned virtual pool, is this because the users are also VPN clients, and you are looking to restrict to which S2S tunnel targets they are allowed to reach?
Anyways, the only way you can restrict the access is by doing sourcefiltering in firewall rules, so you need a mechanism to make sure user A and user B always has IP addresses you know and can filter against. For regular LAN users this can be achieved by VLAN segmentation and different subnets if users A and B are each actually a large group of users. If it's just one user, you can do it by fx. DHCP reservation or use of static IPs on some clients. If they are VPN clients themselves, you need to use the "new" IP Pool feature and radius authentication of the VPN clients where you return the "Class" attribute from radius to assign which IP pool the client belongs to. If it's just two local VPN users on the firewall, you can assign their user a static VPN pool IP in the EAP-secret section, or by using Radius to return the framed-IP attribute.
In all cases you can then filter access with source rules in the firewall rules. -
@keyser I understand now. I'm in the process of configuring RADIUS. Really appreciate your support!
-
I wasn't able to configure a static VPN pool IP assignment using the method where the IP is set in the EAP-Secret section, the IP address was assigned dynamically every time the user logged in.
However, assigning a static IP via the RADIUS Framed-IP-Address attribute works perfectly. It's a reliable and effective way to ensure users always get the same IP.@keyser Thanks for help!
-
@0x44 Yeah, the EAP-secret assignment model is flaky as it doesn't work with Windows Clients. If you are only working with at few clients the radius framed-ip model is great, but if you have a lot of clients I can really recommend the IP-Pool group model and returning the Class attribute instead. Then you don't have to micromanage every single client, and it works spectacularly great.
After I got Netgate to push that feature into pfSense+ it has become an entirely new and really GREAT contender for large scale VPN deployments. I have a customer with several thousands of users where we have replaced VERY costly Cisco appliances with a "cheap" 8300 Appliance and no license costs, and are now using built OS VPN clients and EntraID 2FA authentication. They love it :-) -
@keyser Can I ask where Class is? A while back we set up one with a few users, and used the "IPv4 Network Configuration" setting on the user. Not that we need to change, just curious.
-
@SteveITS Class is a Radius standard attribute you can ask the Radius server that authenticates the VPN user to return along with the “accept” message. If the string value of the attribute equals the IP Pool Group name you configured in pfSense, the VPN user is assigned an IP address from the specified IP pool instead of the default VPN Virtual pool you have configured on the Mobile VPN setup page.
-
@keyser Is it in the FreeRADIUS package though? I've clicked around and may be blind but am not seeing it. I did find a forum post from 2015 mentioning it though. :)
-
@SteveITS I’m 100% sure that Freeradius can do it - it’s very standard (for decades) radius behavior. But I don’t know if it’s available as an GUI option in the Freeradius package for pfSense. Most likely its something you have to configure as an advanced return setting on the user object or somewhere similar. I’m sure google can help here…
I use Microsoft NPS for my Radius needs in this case because that offers the Azure 2FA integration that requires the users to authenticate in their “Microsoft Authenticator app” on their mobile phones to establish a VPN connection. -
@keyser OK thanks. I will table it until needed then. I did try searching and didn't find much. It's probably just not in the package.
-
@SteveITS It’s there - its only a question of how to use it. I have done some Freeradius config previously, and I had freeradius return an Aruba hardware specific radius attribute to the Accesspoints. When I did that, all I had do to was use this field on the user object in freeradius:
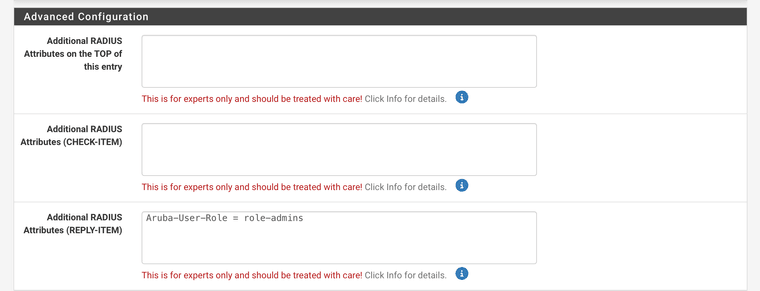
-
@keyser Ah. Silly me I was looking for "class" :)