How to route internal traffic destination 'my public services' back via the WAN-interface
-
There's no real way to do that in pfSense. You could add a bunch of NAT rules and VIPs to try to emulate it but it wouldn't actually test the traffic flow from an external client. The source address can never be something external. The traffic would not actually pass the WAN ruleset.
It's always better to actually test from an external client.
-
@louis2 if you want to test wan connectivity rules, etc. Then put something on your wan network.
Lets say you get 1.2.3.4/24 from your isp on pfsense wan.. Put a box with say an address of 1.2.3.5/24 on your wan. You could always add a switch to allow for this.. or run your wan connection through a managed switch, etc.. Now you can do whatever you want from that client to pfsense 1.2.3.4 IP address as if it was on the actual wan/internet.
-
I would still advise testing from something actually external. Something in the WAN subnet directly will always be routable and may bypass policy routing etc.
-
@stephenw10 true - some actually out on the internet would be best.. But if you want something easier to play with.. Putting something on pfsense wan interface network would be next best.. Without having to get fancy with a local router upstream to talk to your pfsense wan interface, etc.
-
How / I do not want to emulate the ISP ?
Perhaps ..... ??? .... I could add a second WANNo idea ... it does not feel as easy .....
-
@louis2 What IP do you have on your wan interface of pfsense.. 1.2.3.4/24 in my example.. on this same network - you might need a dumb switch if pfsense is plugged directly into your cable modem or ont, etc.
Now fire up a pc or laptop and give it 1.2.3.x/24 IP on its interface.. There you go that is all there is to it.
Your network mask might be bigger, my isp uses /20 for example
Now pfsense will not be able to connect to this 1.2.3.x IP address actually out on the internet, etc. - But when do you ever talk to an IP on your isp transit network your connected too? Never! Worse case scenario you step on some other clients IP from your isp.. But that shouldn't be an issue really - and if that did happen it would be a really bad design by your isp that could even allow that to happen. When you ping say 1.2.3.Y do you see an arp entry for it?
But to be nice you could try pinging the IP before you use it. And wouldn't leave it up unless your testing, etc.
Now on this pc/laptop send traffic to your pfsense wan IP 1.2.3.4 for anything you want to test - this will fully test your port forwarding firewall rules, etc. etc.
BTW your not emulating the ISP your just creating a device on your wan network that will talk to pfsense just like any other client out on the internet.
Sure you could if you wanted to spin up another wan interface and put a client on that network to test with.. That would work too - but it wouldn't be actually testing your current wan rules and port forwards, etc.
This is really no different than adding a device to your lan network.
-
@johnpoz said in How to route internal traffic destination 'my public services' back via the WAN-interface:
@louis2 What IP do you have on your wan interface of pfsense.. 1.2.3.4/24 in my example.. on this same network - you might need a dumb switch if pfsense is plugged directly into your cable modem or ont, etc.
John I have a sophisticated network. The core build with managed 2.5 and 10G switches. The connection is like this:
- The ISP is arriving with a fiber. Converted to 1G UTP
- That UTP goes to a managed switch separating the arriving VLAN's.
- Vlan-6 the internet is connected to the pfSense WAN-port.
- Where the PPPOE signal is handled
- The ISP connection contains one IPV4-address and a /48 IPV6 range.
That has not changed in the past years!
I made a screenshot of the WAN-interface status, but be aware since today, I have a critical IPV6 issue. So the screenshot is probably not fully correct!
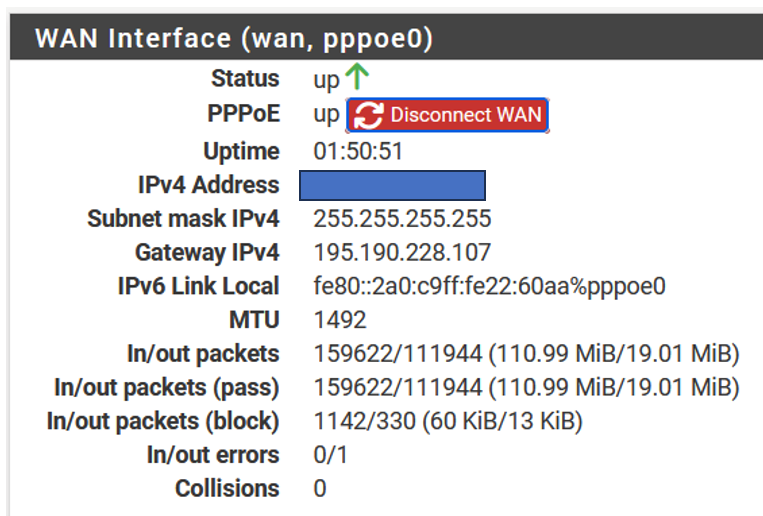
What surprise me is that seems to have am IPV4 subnet where I have only one !! (So I can not send from one IPV4 to another IPV4)@johnpoz said in How to route internal traffic destination 'my public services' back via the WAN-interface:
BTW your not emulating the ISP your just creating a device on your wan network that will talk to pfsense just like any other client out on the internet.
I do not understand this. I have a mikrotik switch which could act as a PPPOE-server, but that is complex and I would like to test with the normal connection active!
What I do at this moment is:
- using my mobile network / phone as external network
- and using sites on the internet which can generate test traffic
It would be nice ...... it you could inject traffic at the point where the 'pfSense PPPOE adapter' hands over the bitstream to the pfSense 'rule filter' / 'packet capture' function block

-
Nothing to do with the actual subject, however it is very strange to see that my IPV4-address is not part of the network to which the Gateway IPv4 belongs.
Perhaps ..... just guessing ...... the provider is 'faking' my IPV4 address to keep my IPV4 the same, when they switched their network ..... just just guessing .......
-
@louis2 said in How to route internal traffic destination 'my public services' back via the WAN-interface:
PV4-address is not part of the network to which the Gateway IPv4 belongs.
your using pppoe.. That is going to be harder to do then.. Because your rules would be on your pppoe interface which is where traffic would hit.. And looks like that is a /32
-
Laptop connected to a cell phone solves this problem and is usually pretty easily accessible.

Just test from a real external IP address.
-
@stephenw10 Yup!! great solution - way easier too.