DNS resolution barely works on backup node
-
@benbrummer are you forwarding to a DNS server on LAN? WAN would be the expected way to get to the Internet…. The default of ALL should also work.
-
@SteveITS trough the lan interface a DNS Server can be queried trough an IPsec, to have DNS available for names on the other side
Default would indeed work, but we have interfaces e.g. to external parties, where we do not want to send any DNS queries.For my understanding if WAN is not selected in our HA Cluster, which was the case I should expect DNS issues on master AND backup, but master works and backup does not respond on 127.0.0.1.
Current working configuration:
- General configuration: Quad9 DNS servers
- Resolver runs in resolver mode to query root servers
- Network Interfaces: All
- Outgoing Network Interfaces: WAN, Localhost, LAN
- Strict Outgoing Network Interface Binding: Enabled
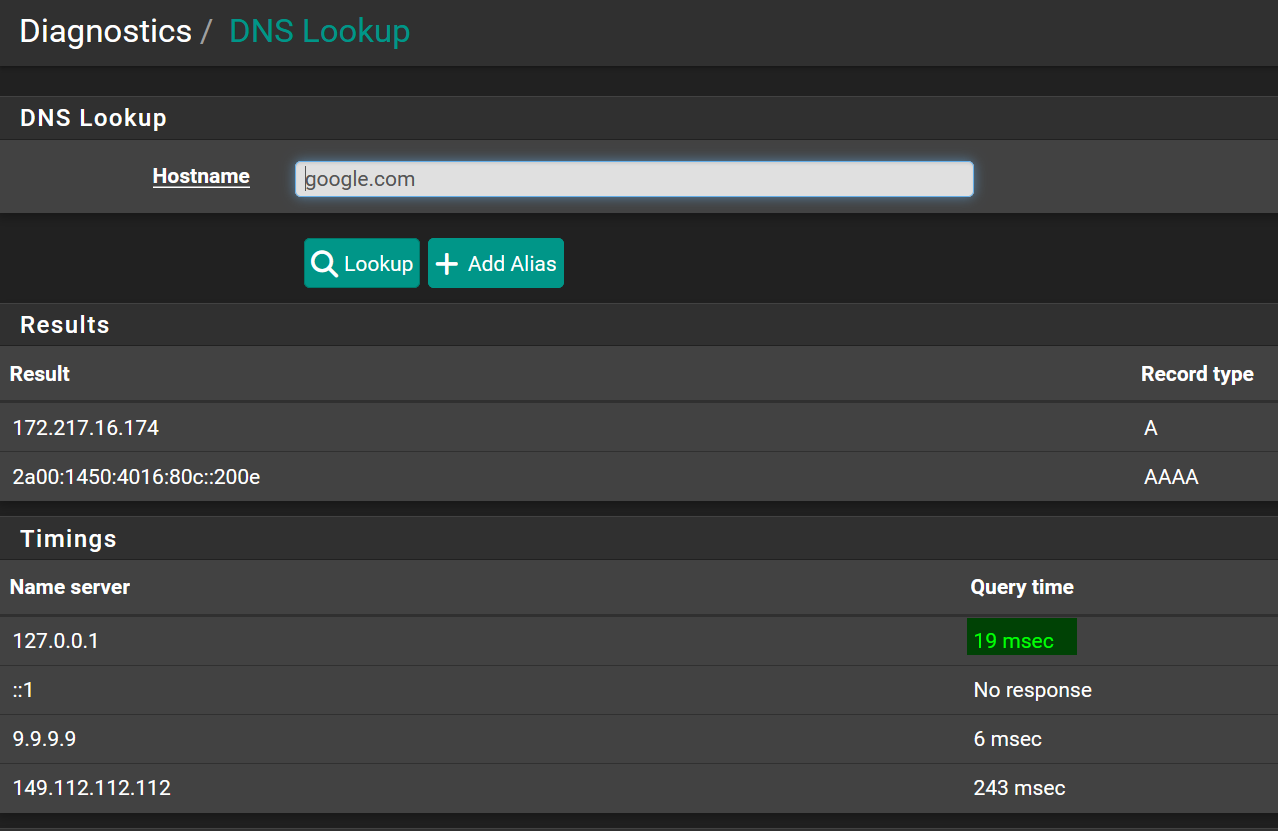
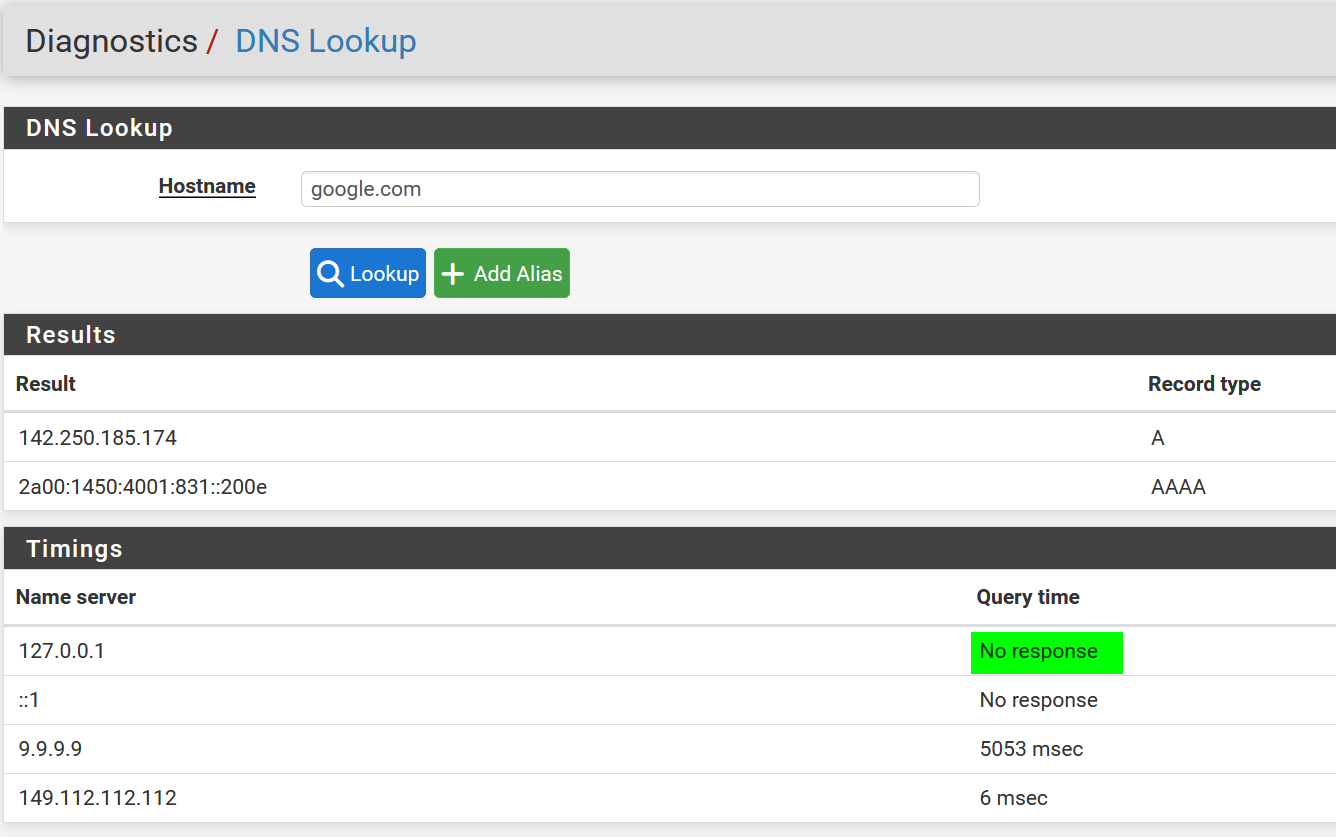
If the WAN is removed from Outgoing Network Interfaces, backup firewall has DNS issues and navigating the Webinterface is incredible slow. Login takes 30 seconds or longer. DNS Lookup, gets no response from 127.0.0.1.
- Not sure why DNS works on the master, when WAN is removed
- Single instance at a different location with Outgoing Network Interfaces: Localhost, LAN works
By the way, thanks for the support!
-
@benbrummer said in DNS resolution barely works on backup node:
DNS Server can be queried trough an IPsec
And this VPN is not originating on pfSense? Something else is creating that tunnel? It sounds like the backup router can't connect to it...maybe try dig/nslookup on the backup router using that "LAN" DNS server.
The web GUI being slow (when DNS isn't working) was a problem in earlier pfSense versions but IIRC it was fixed a year or two ago.
-
- #1 Everything works now, with Outgoing Network Interface WAN, LAN, OPTx and Localhost.
- #2 Everything was working before without WAN being activated for Outgoing Network Interface, except DNS on Backup pfsense.
I'm fine if #1 is the correct way to configure it, but I try to understand, why DNS was working in #1 without WAN being activated for Outgoing Network Interface.
So my expectation is a consistent behaviour for master and backup:
With WAN: DNS resolution on both
Without WAN: No DNS resolution for both -
@benbrummer Did you try a traceroute? Seems like an asymmetric routing scenario possibly.
-
No difference for traceroute when Outgoing network interfaces are with or without WAN. It works without issue for netgate.com.
But the DNS Resolver status page on backup is basically empty. Zone contains always "-".
Wan WAN is activated again the Resolver Status page quickly populates with ips and zones.
-
@benbrummer traceroute works to netgate.com or to the internal DNS server?
-
@SteveITS yes traceroute works internal and external.
But the problem is changing now.
If I select "Outgoing Network Interfaces" all , DNS resolution for the b.example.com is starting to fail, "Query refused", so the wrong interface is sending the queries.
With WAN, LAN, Localhost resolution is slow, 1-2 timeouts before successful resolution.
With just LAN and Localhost resolution for internal works instantly, but public addresses fail.
So it looks like I need to ensure, that the correct interfaces are used fro the right DNS server
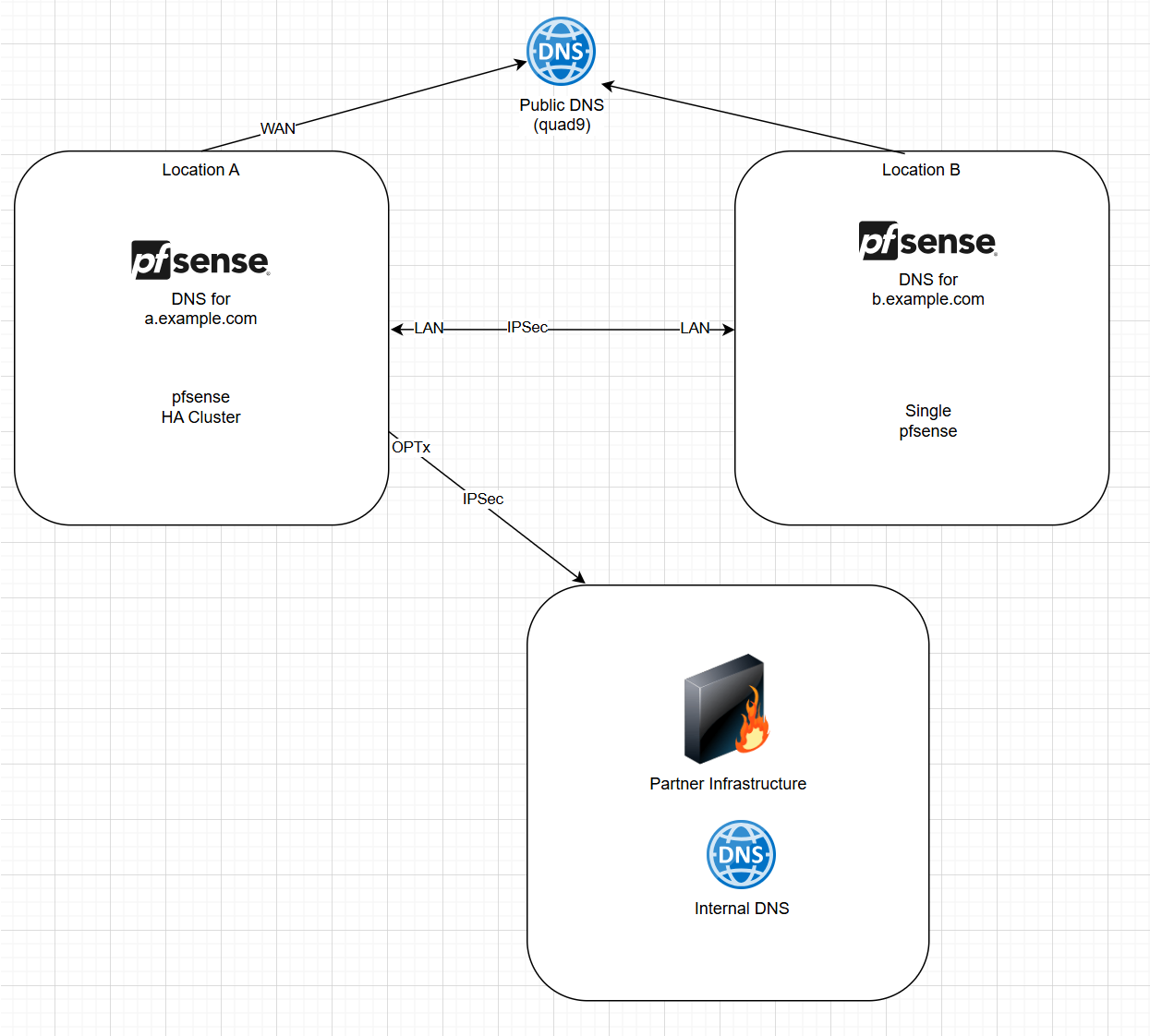
WAN => Public DNS
LAN => DNS at Location B
OPTx => DNS at PartnerAdditionally:
On the master the DNS resolution without WAN seams to work, but slow, too. Eg fqdn aliases are populated slowly or sometimes failing, causing firewall rules to not apply.Conclusion
WAN is mandatory, but I need to find out how to send specific DNS queries from specific interfaces.Will check on this: https://docs.netgate.com/pfsense/en/latest/multiwan/interfaces-and-dns.html#dns-forwarding-and-static-routes
-
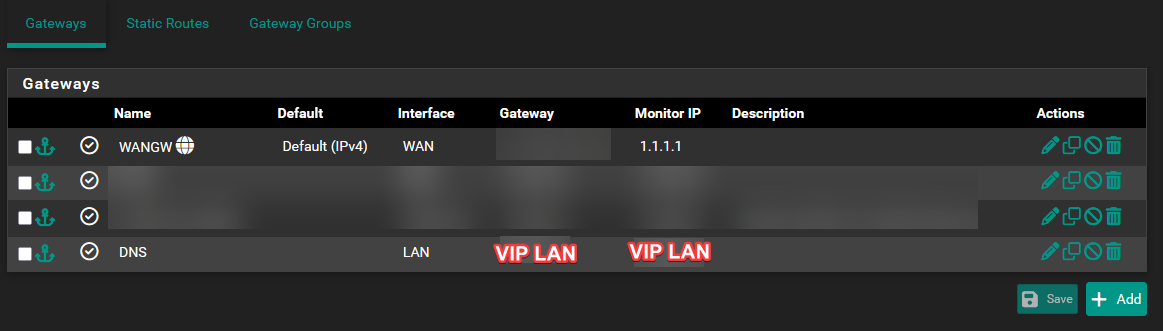
Current status: It works now
- Created a GW for Interface LAN with the VIP for LAN. The ACL on other pfsense expect that queries originate from this IP
- Created an alias, holding all our internal DNS servers on other locations
- I created a static root for the new gateway to this alias
- Same was done for another interface and an alias for the partners DNS servers
-
DNS for internal servers is not working on the secondary
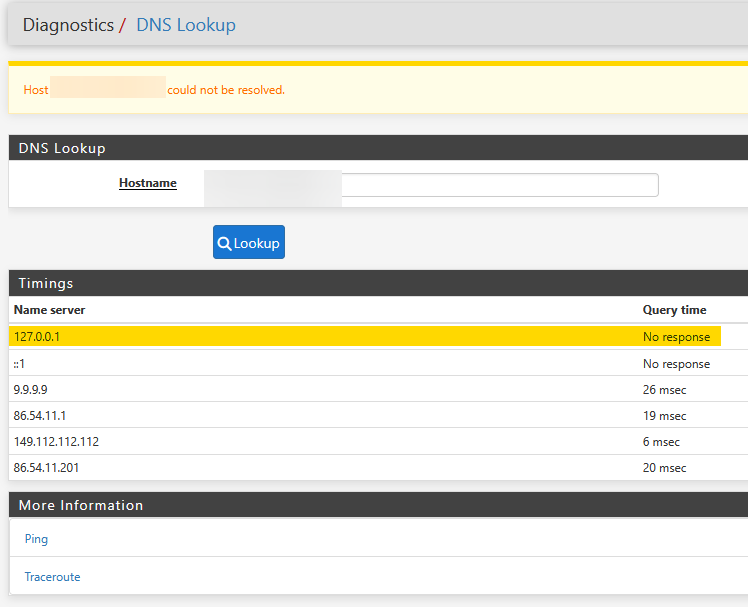
- traceroute 2 hops
- ping works
- Public DNS works fine, Interface is responsive
primary works great, with
 and a static route
and a static route -
So I'm back where I started following
- https://forum.netgate.com/topic/149472/solved-remote-dns-not-working-over-ipsec
As WAN is not selected primary works, internal and external dns is reliable
Secondary is slow on the webinterface and has basically no DNS
nslookup google.de ;; communications error to 127.0.0.1#53: timed out ;; Got SERVFAIL reply from 127.0.0.1, trying next server ;; communications error to ::1#53: connection refused ;; communications error to ::1#53: connection refused ;; no servers could be reachedSo the secondary firewall is basically not listening to dns requests at all. As I removed now all DNS server on general settings to only use the root servers.
(Identical behaviour for snmp monitoring, only the primary firewall can be monitored.)