Problem with firewall and virtual IP addresses.
-
Ok so the target server is in the 172.21.16.0.X subnet?
Hmm, I would expect that to work.
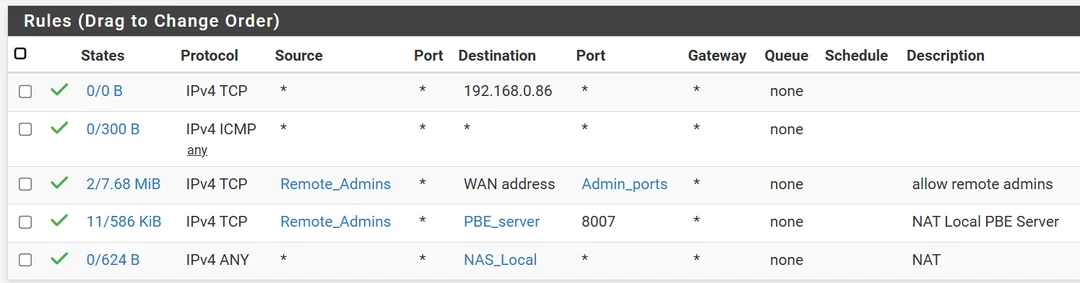
If you don't have the port forward in place can you ping the VIP directly? That should work if the firewall rules allow it.
-
@stephenw10 It didn't work.
-
You can't ping the VIP? And you added firewall rules to allow it?
Perhaps something in the hypervisor is blocking it?
-
@williamsilverstein in general I’d go with 1:1 NAT instead of trying to forward all ports.
Often in cases like this the server firewall isn’t set to allow connections from outside its subnet but if you disabled the NAT rule and can’t ping pfSense that’s not relevant for that stage.
-
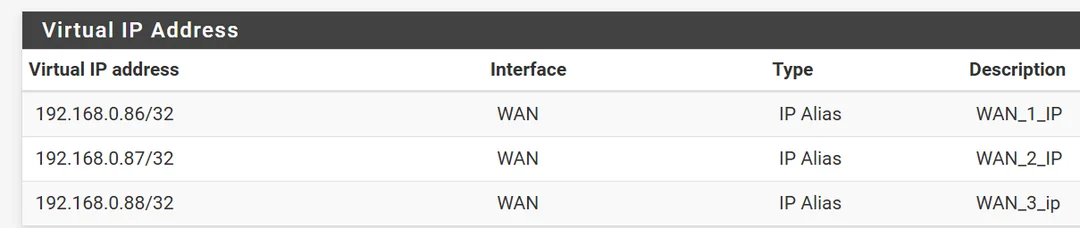
@williamsilverstein, If I'm not mistaken, I believe the VIP's need to have the same mask as your WAN subnet. For example, if your ISP assigns a /29 block to you, the VIPs must also be configured with a /29.
A previous post stated that your WAN interface is configured in the 192.168.0.0/24 subnet; therefore, you'll need to modify your VIP's to reflect a /24 mask... i.e.:
192.168.0.86/24
192.168.0.87/24
192.168.0.88/24 -
@marvosa I had tried that.
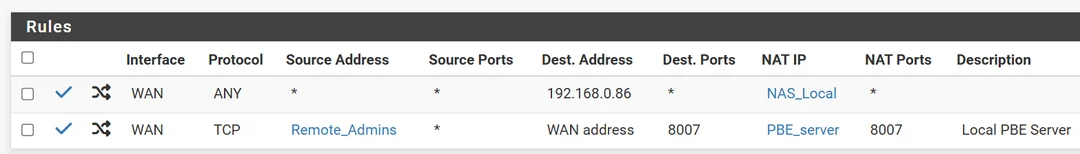
F figured out the problem. I was using an IP alias for the target of the NAT redirect target. If I placed the actual value value into the target, it works. Its a bug.
The inability to ping was the proxmox node firewall was on. I thought I had turned it off.
-
@williamsilverstein hmm normally no problem using an alias as a NAT target. Just one IP in it?
Note without outbound NAT or 1:1 outgoing traffic from that host will use the default WAN IP.
-
@williamsilverstein said in Problem with firewall and virtual IP addresses.:
I was using an IP alias for the target of the NAT redirect target.
If there are multiple IPs in the alias or its type is network, port forwarding will not work.
-
Mmm, you should be able to use an alias there. But, yes, it has to be a single IP.
-
@SteveITS I have everything working, but the ssh forward does not work. I can access the server through the webadmin interface, but not ssh 192.168.0.86, it fails. I tried the first rule
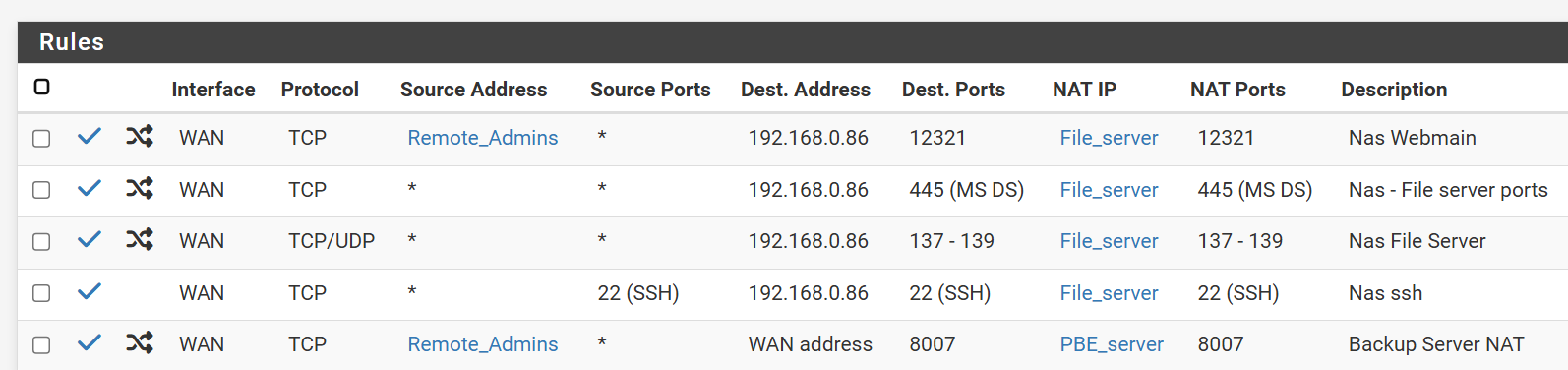
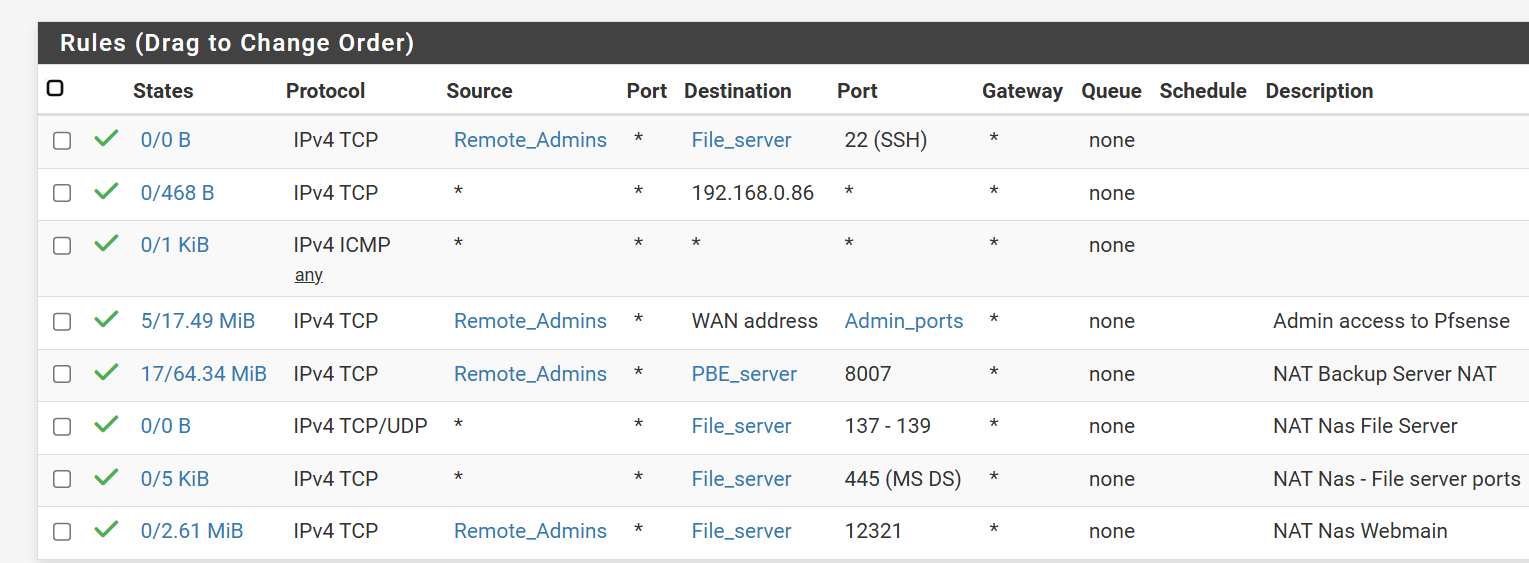
When I try to access webmin through port 12321 it works, from the same address ssh timesout.
Any suggestions?
-
You should not have a source port set in the port forward for it. The source port is almost always a random ephemeral port.
-
@stephenw10 That was the problem. Thanks.