Unexpected alias behaviour - two ranges / size limits with FQDN
-
Create base Alias
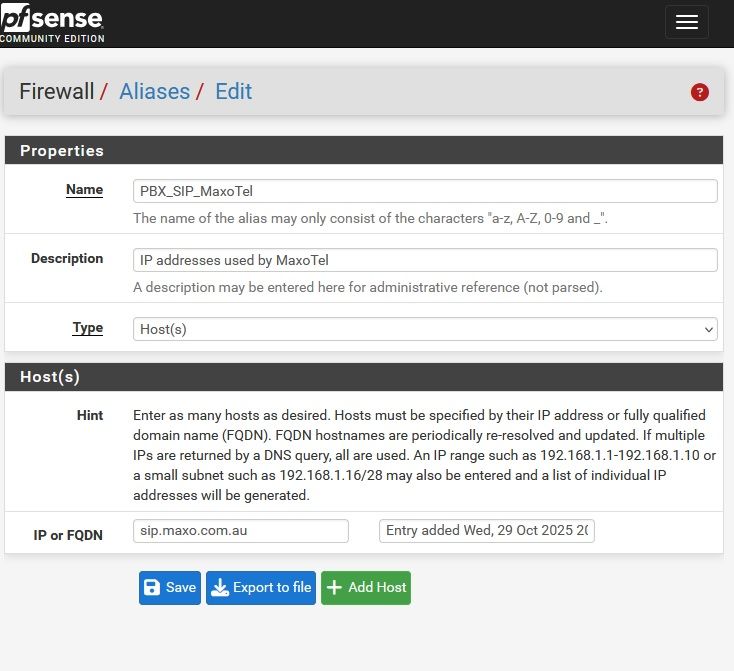
Try to add two networks as single entry
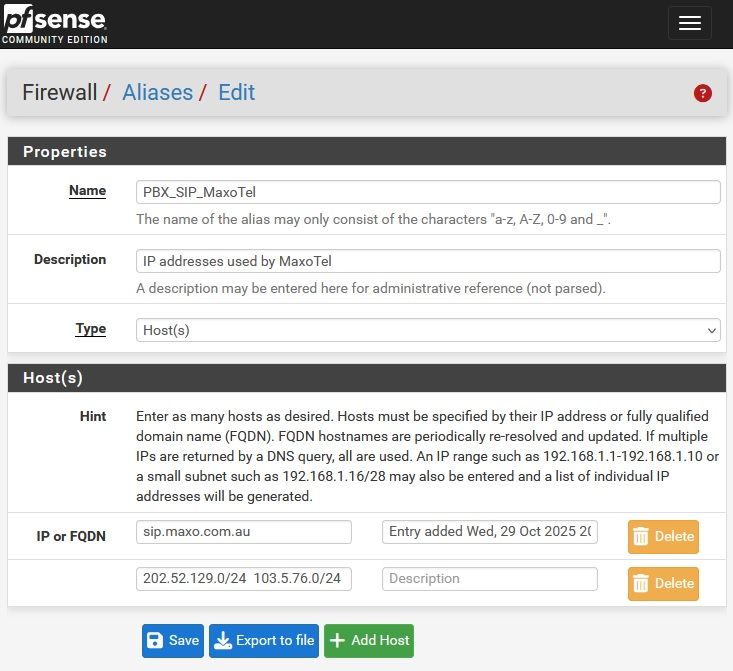
Error reported with empty host visible on scrolling
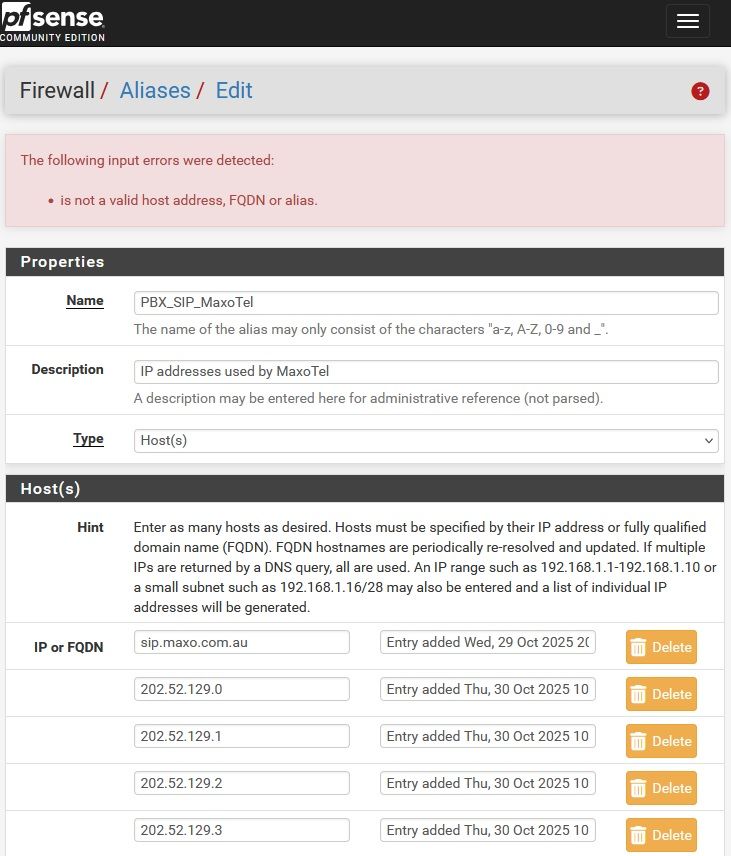
...
Deleting empty host (by clicking on it's delete button) then save alias appears to work but corrupts configuration. Rules which use the alias behave unpredictably.
Solution.
Restore configuration from prior to above entry then enter networks on separate lines
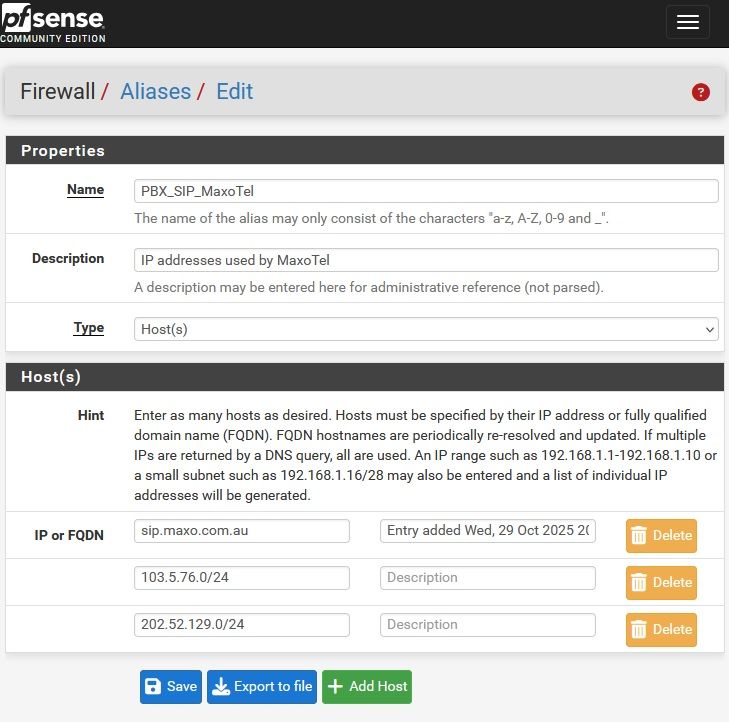
-
Hmm, that seems correct. You can't add two subnets as a single entry there. Valid entries are: An FQDN, an IP address, a subnet or a range of IP addresses. Not multiple subnets.
-
@stephenw10 said in Unexpected alias behaviour - two ranges:
Valid entries are: An FQDN, an IP address, a subnet or a range of IP addresses.
Adding a list of IP addresses does work and is very useful, such as copying a list of IP addresses from a spreadsheet then pasting into an alias entry. The list is automatically expanded to separate entries for each IP address.
My use case for this is some supplies have an online multicolumn table of IP addresses they use. To in add that to pfsense:
- copy the table of IP addresses from their web site
- paste into a speadsheet
- sort the list
- copy the column of IP addresses
- open pfsense GUI -> edit alias, delete old entries
- add a new entry to the alias
- paste the column of IP addresses from the spreadsheet into the single entry in pfsense
- save Alias, pfsense automatically expands the list to one host IP per line
@stephenw10 said in Unexpected alias behaviour - two ranges:
You can't add two subnets as a single entry there.
I have no problem at all with that.
The behaviour I'm less sure about is it appearing to work but corrupting the pfsense configuration if you do. -
@Patch I think he’s saying the input validation shouldn’t allow you do that and that is a bug. :)
I’m not near a config file but IIRC there are IPs stored with spaces. I’d guess something is trying to split the string on the space.
If it was on a web server you could update that file as a URL table alias as desired and not touch pfSense.
I wonder if there’s a way to do that using localhost like pfBlocker and then Diag>Edit File?
-
You can import data into an alias but the format is
subnet hostnamewith each on a separate line. See: https://docs.netgate.com/pfsense/en/latest/firewall/aliases-config.html#bulk-import-network-aliasesBut, yes, the input validation should prevent creating an invalid config.
-
@stephenw10 said in Unexpected alias behaviour - two ranges:
But, yes, the input validation should prevent creating an invalid config.
Thanks, that's was really the only thing which was concerning me. As finding a PBX error was due to input parsing error in pfsene corrupting it's configuration took more time than is desirable to track down.
@stephenw10 said in Unexpected alias behaviour - two ranges:
Valid entries are: An FQDN, an IP address, a subnet or a range of IP addresses.
@stephenw10 said in Unexpected alias behaviour - two ranges:
You can import data into an alias but the format is subnet hostname with each on a separate line.
While I don't doubt that is the case, for what I'm trying to do pfsense currently supports a more efficient method. It would be great if this capacity was retained.
To illustrate,
For one of my VoIP suppliers, after logging into their web interface they show their IP addresses in the following format
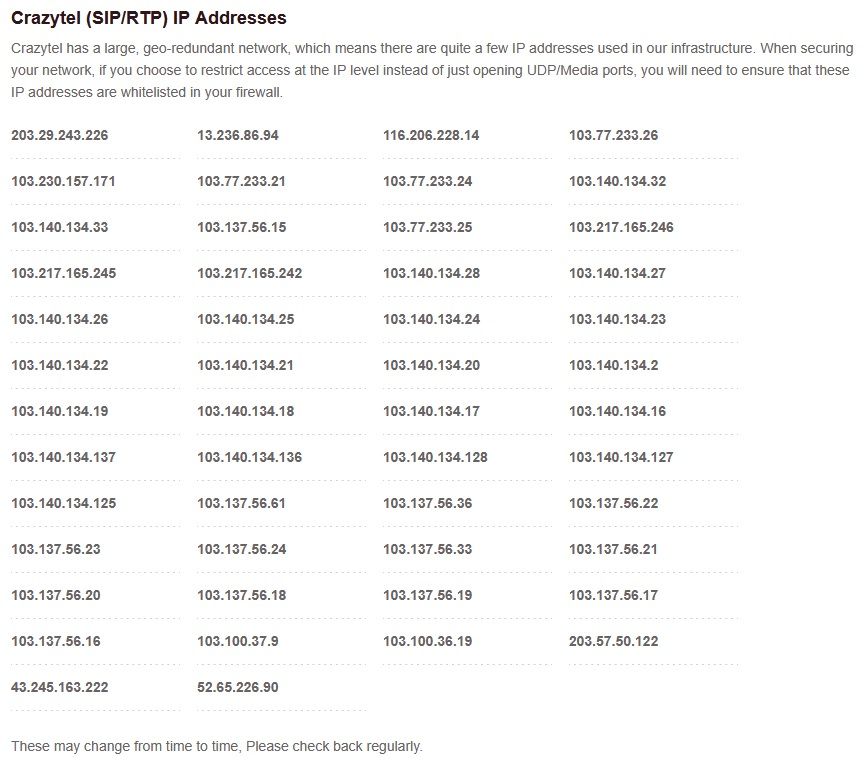
The IP address section can be selected then copied into LibreOffice - Calc
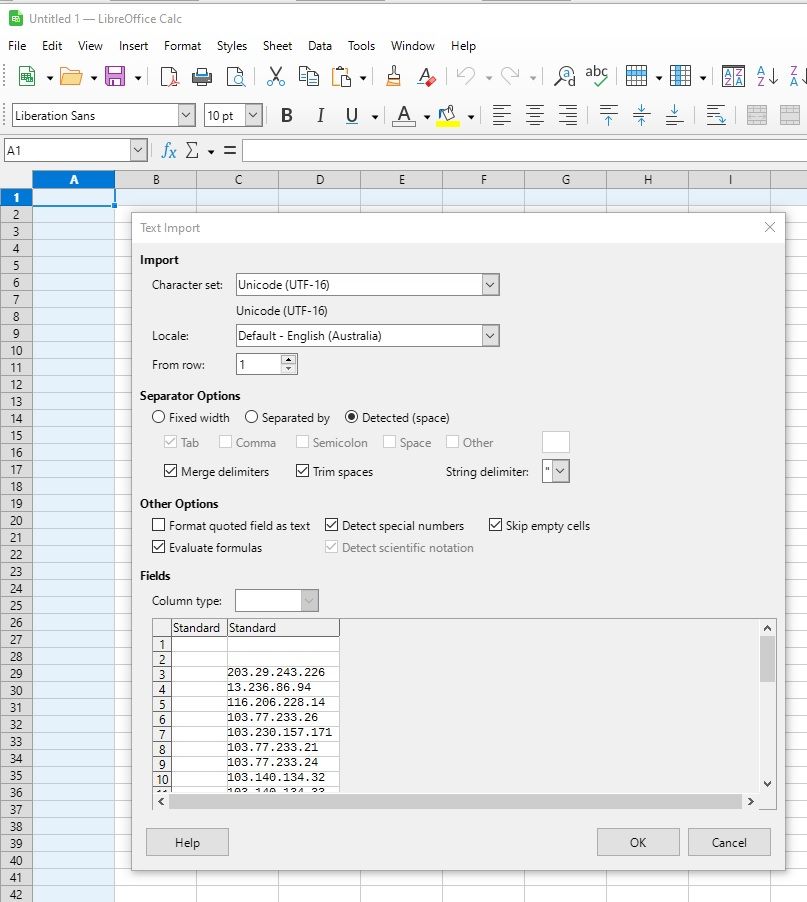
Which results in a list of IP addresses. Optionally sort then select and copy
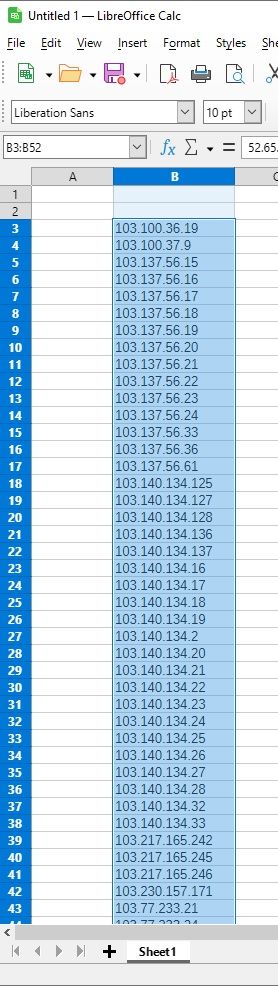
Goto pfsense -> Firewall -> Aliases -> select appropriate alias
Delete old data leaving a blank host. Paste spreadsheet clipboard
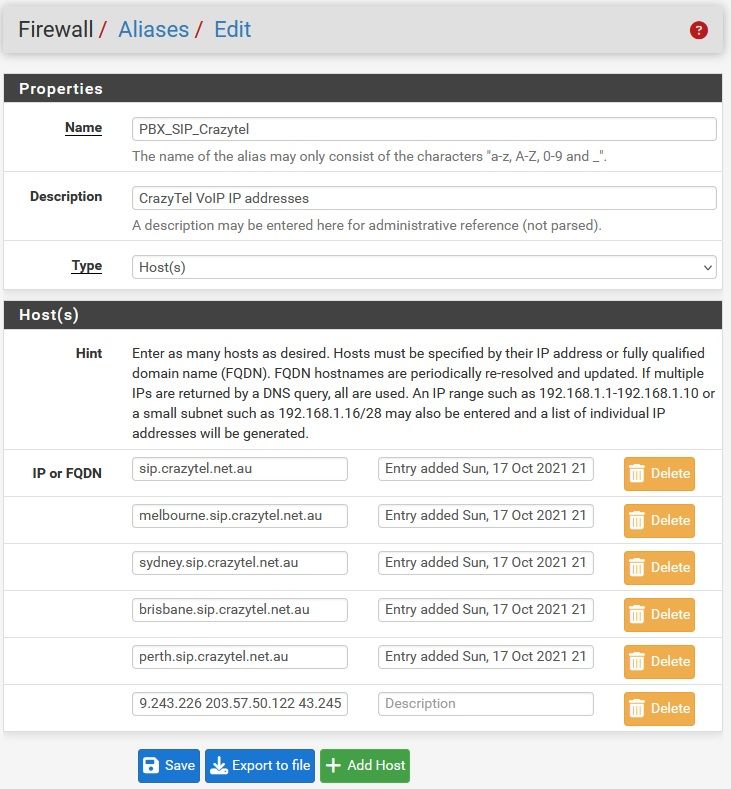
Click save and pfsense expands as shown by editing that alias again
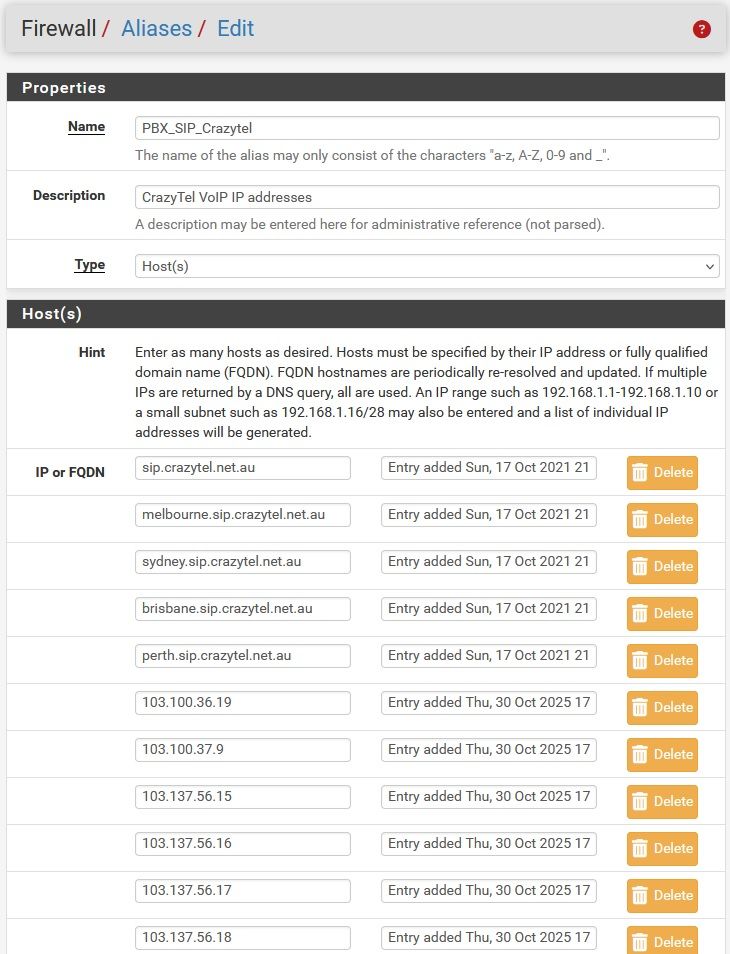
-
Hmm, interesting. That functionality is not expected there. It seems more like a happy accident that it works!
The bulk import page is provided for exactly that. But you would have to remove and reimport the alias every time which could be painful.
You could host that list on something locally and just reference it in a url table alias so it updates automatically. It's a shame they put the list behind a portal or you might be able to reference it directly.
-
@Patch my programmer hat thinks there might be hidden CRLFs in there after the paste.
-
Yeah that does seem entirely possible.
@Patch can you post the actual list that triggers this? Since we can't access that portal to test.
-
@stephenw10 I replicated quickly...make any spreadsheet. I had one with columns:
1
1
18
5
23it's accepted and saved as:

XML is:
<alias> <name>a_test</name> <type>host</type> <address>1 1 18 5 23</address> <descr/> <detail> Entry added Thu, 30 Oct 2025 09:07:42 -0500||Entry added Thu, 30 Oct 2025 09:07:42 -0500||Entry added Thu, 30 Oct 2025 09:07:42 -0500||Entry added Thu, 30 Oct 2025 09:07:42 -0500||Entry added Thu, 30 Oct 2025 09:07:42 -0500 </detail> </alias>Did not try to apply, just deleted it.
-
Hmm, I imagine it would try (and fail) to resolve those. Let me see here...
-
Hmm, nope it interprets them as an IP address. Which is interesting. I expect that to fail the input validation but perhaps the fact it can be an fqdn allows it.
Oct 30 14:37:58 filterdns 25069 Adding Action: pf table: Test1 host: 1 Oct 30 14:37:58 filterdns 25069 Adding Action: pf table: Test1 host: 18 Oct 30 14:37:58 filterdns 25069 Adding Action: pf table: Test1 host: 5 Oct 30 14:37:58 filterdns 25069 Adding Action: pf table: Test1 host: 23 Oct 30 14:37:58 filterdns 25069 Adding Action: pf table: Test1 host: pfsense.org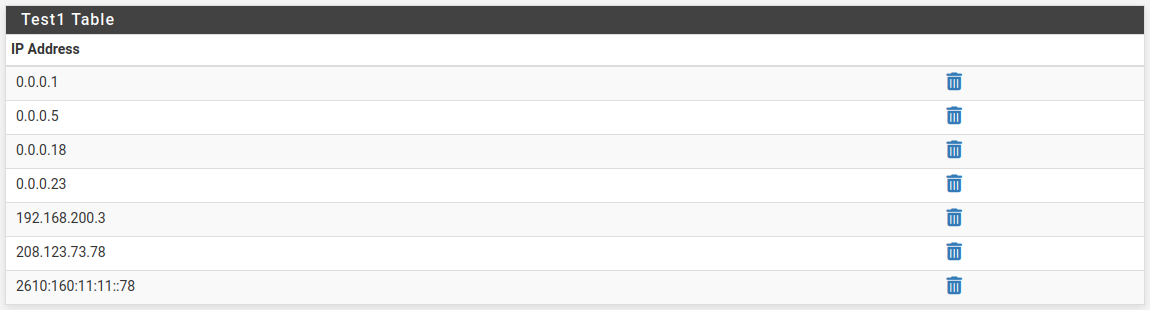
-
It doesn't validate them separately either. Probably assumes "anytext" is a hostname even without dots, though the docs say "fully qualified domain names."
A quick solution (to break @Patch's "feature"
 ) is to reject spaces in the form field.
) is to reject spaces in the form field.@Patch The pfB aliases pull from a URL like https://127.0.0.1:443/pfblockerng/pfblockerng.php?pfb=pfB_PRI1_6_v6.
-
Yup. However I also can't replicate the original issue where an empty line is created. Adding multiple subnets there creates a valid alias with all subnets expanded.
So I suspect there was a rogue character in @Patch's imported list as you suggested.
As such I'm inclined to do nothing here. Anything we did do would likely break the workflow for anyone using the undocumented behaviour.
-
Now that I know about this “feature” I can see where it’s going to save me some time. :)
-
Sorry about the delay in responding.
pfsense was behaving very strangely which was complicated by- testing on my home active router
- pfsense configuration evolved over many years and includes a 3 packages (eg pfBlockerNG)
- frequent restarts required
- fault detection I suspect was using failure to include specified entries in an alias -> hybrid NAT rule failed -> after firewall restart failure to register of 1 of 4 VoIP suppliers
Solution, simplify the test set up
- Create a new VM on another appliance, with at least 2 NIC (actually 3 passed through)
- Clean install pfsense v2.8.1 via installer v1.1. Allow DHCP over ride of DNS & network time.
- Enable Kea, enable pfsense GUI from Wan (wan pass rule, un-check Block private network and loopback addresses)
- Slowly rebuild aliases of interest, regularly saving configuration after each error free entry
- Error detection based on comparing the Alias definition shown in Firewall -> Aliases -> IP -> <Alias> -> edit. Compared to Diagnostics -> Tables -> <Alias>
The result of which is:
@stephenw10 said in Unexpected alias behaviour - two ranges:
I suspect there was a rogue character in @Patch's imported list
You are correct. The networks were separated by a double space. Sorry the forum removes double spaces so you could not copy from my post. Using a single space prevents creation of the blank host. But doing so does not fix the problem with creating the desired Alias.
I believe the task which creates the table from the alias definition is too resource limited and the performance optimisation some times means the desired table is never created.
For example
-
Create an Alias (network type). Add a couple of /24 networks and a couple of FQDN or /32 addresses. Save and apply changes. They show up in the Alias table as desired. Edit the Alias definition to delete the /24 networks and on of the /32 addresses. Save and apply the changes. The /32 address will be removed but the /24 networks will stay. Reboot pfsense and the /32 will also be removed leaving only the valid /32 entry
-
Create an Alias (host type). Add a FQDN and two /24 networks one of which includes the FQDN IPv4 address. Save and apply. Look at the filter reload screen, when complete look at the created table for the Alias. For me it shows about 470 entries initially. Manually triggering Status -> Filter Reload -> adds about a couple more entries to the table for the alias. Wait 5 minutes for the Aliases Hostnames Resolve Interval to time out -> Alias table shows all 512 entries (duplicate removed)
-
Delete all the /24 network entries from the above alias definition, save and apply. Look at the Alias table, in now contains no entries. The single table entry for the duplicate address was deleted on removal of the explicit IP address. Filter reload and waiting >5min makes no change. Restart pfsense and the entry is repopulated.
-
Repeat test 2. but use with a single line entry of both /24 networks in one line. For me about 150 entries appear initially in the table, a few more with each Filter reload, all on waiting 5 minutes
-
A similar difference is seen in loading the 50 Crazytel IP. Initially pasting the 50 IP in on line sorted in reverse order loaded 7 entries. Repeating the test after the VM had been running for several hours loaded 25 entries. Pasting them in sorted in ascending order may have resulted in a couple more being initially loaded. As before manually triggering a filter reload added a few more. Wait 5 minutes and they are all loaded. Manually entering each IP into a separate line in the Alias and all 50 are loaded initially.
-
Running similar tests on configuration with many other Aliases (and pfblocker) and less is done initially. The 5 minute alias reload appears not to have the resources / time to ever complete some aliases
Summary
- pasting multiple single space separated entries into as single line is very efficient for data entry but appears to reduce initial processing done on alias entry by about a halve to a third.
- pfsense spreads alias processing over multiple Aliases Hostnames Resolve Intervals if required. More processing is done on reboot. Less processing is done on Filter reload.
- More complex configurations slow the Alias processing (perhaps to a stand still at times)
- Alias processing optimisation maybe over zealous at times requiring pfsense reboot to resolve.
- a force alias full regeneration option would be nice during configuration updates. Or perhaps more time devoted to it on manual filter reload
-
The alias processing does to some cool things which I like such as:
- enter range IP xx.xx.xx.xx-yy.yy.yy.yy in Host or network aliases
- in Network alias paste xx.xx.xx.xx/yy -> sets mask without needing to manually select via menu
- Change Host alias to Network alias to enable adding networks to an existing alias (The reverse can be done however that expanded networks which are not automatically re-compressed if you change your mind).
- Alias can included an alias simplifying maintenance and documentation.
- Multiple entries can be added in a single line which pfsense automatically expands. Doing so reduces initial table processing which is not trivial to accelerate.
- Duplicate host entries are automatically removed. However there is some risk of no entry being left there if one of the entries is delete (or maybe also changed). Duplicate covered by a network range appear not to be removed (depending on the filter design this may have minimal performance impact and maintaining a single entry for these duplicates maybe difficult). Similarly a relatively long consecutive sequence of host IP appears not to be converted to a range (but maybe else where in actual filter design)
-
@Patch said in Unexpected alias behaviour - two ranges:
Using a single space prevents creation of the blank host. But doing so does not fix the problem with creating the desired Alias.
Yes it does. The rest is a super longwinded way of saying, 'my bad.'
-
@Patch said in Unexpected alias behaviour - two ranges:
5 minute alias reload appears not to have the resources / time to ever complete some aliases
Are you talking about FQDNs or the /24 subnets here? I thought the 5 minute timer was for resolving FQDNs via DNS. We have a scenario where some either stop resolving or are maybe never added to the table...hard to tell since 99% of the time they're not used. However per your description, some may overlap (laptop goes to an allowed public IP) so I'm wondering if one fails it is removing "both" IPs/entries?
-
Hmm OK I can replicate case 2 here. Digging....
Do you see the full alias set shown in the Resolver logs when you add it?
For me I see that and it does load all 512 entries after a delay.