BGB Routing with multi WAN and own AS
-
Hey fellow pfsensians!
I have a question in regards to routing and firewalling traffic from my own AS. Lets start with the setup:
Everything runs on vmware esxi
pfsense 1 (does all of the BGB peering and announcements using FRR)
WAN1 & WAN2 are two links and ASN peers (2 fiber interfaces)
Edge (192.168.150.1/24) is an internal interface between pfsense 1 and 2pfsense 2
Edge (192.168.150.2)
AS (public /24 block) and .254 as gateway for the VMsAS VM(s)
- using pfsense 2 AS gateway (no NAT)
- AS has access to the internet once i create (and enable 4th rule) floating rule
The situation:
I get port scanned and spammed/hammered to hell. How can I can ensure that only existing states created by the source IPs get allowed through the firewall.Been battling this for a few days, any help would be appreciated!
-
@entrio You’re getting scanned because your /24 is directly exposed without NAT. Create a top floating rule that allows only established and related states, then another below it that blocks new inbound connections. This keeps your AS reachable for return traffic but drops all unsolicited packets.
-
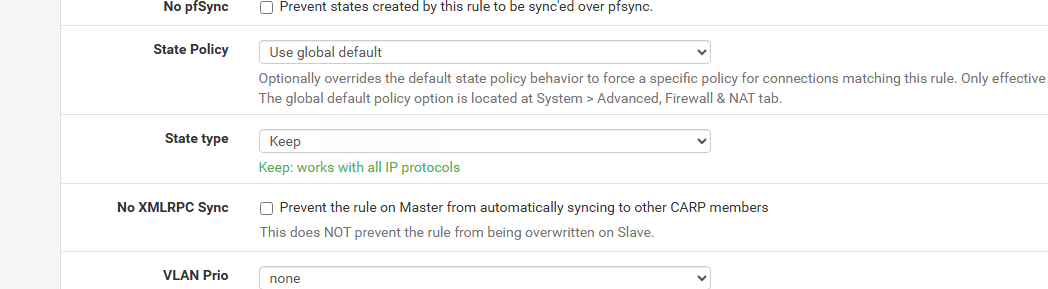
@Jaritura I thight that states are kept by default on interfaces, no? I can only see state type: Keep
I scoured the internet on how to do established or related like in ip tables, but everywhere i look, it is said that automagically done.
This allow new incoming connection too
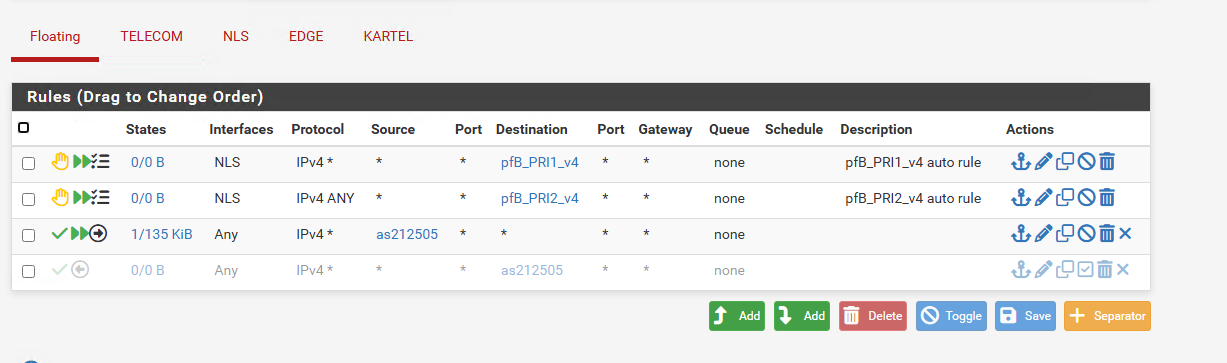
Do i make a block rule that has State type: None to prevent scanning?
If you dont mind, can you clarify how to create the rule with said states

Thank you far taking your time to reply
-
Yeah you’re right, pfSense already keeps states by default. When you set “State type: Keep”, it already behaves like the “established, related” match in iptables, so you don’t have to configure that manually.
If you want to stop new inbound connections from scans but still allow replies for your outbound traffic, you can do it with two floating rules. Make one at the top that passes traffic, check Quick, apply it to your WAN (or Any if you’ve got multiple), set the direction to In, and leave State type as Keep. That one keeps your existing connections working.
Then right below it, add another floating rule that blocks everything else. Also mark it Quick and set State type to None. This setup lets return traffic from your sessions pass normally but drops any random inbound scans hitting your /24.