DNS Domain override not working between 2 pfSense boxes
-
@soupdiver I assume this is caused by the same problem as when attempting it using IPsec. Local PfSense services cannot by default query pfsense services on the remote box because when sending packets in that direction, it uses a wrong source address.
With IPsec this is resolved by creating a GATEWAY under SYSTEM -> ROUTING that is the Local LAN/Inside interface address on which the local DNS is running.
After that you create a static route with the remote LAN network (Where the remote DNS listens) using the new gateway. -
After that you create a static route with the remote LAN network (Where the remote DNS listens) using the new gateway.
But I already have a route for that network. Pointing to my wiregaurd gateway
-
@soupdiver said in DNS Domain override not working between 2 pfSense boxes:
I have added 10.0.0.0/8 to the access list on both sides.
But what do you have set for the interface for outbound in unbound? Is it set to all?
If football wasn't starting like now - I would setup wireguard connection between say my VM pfsense and my real pfsense and test this. Maybe halftime or before the night game..
-
@johnpoz said in DNS Domain override not working between 2 pfSense boxes:
But what do you have set for the interface for outbound in unbound? Is it set to all?
Yes on both ends
-
@soupdiver how exactly are these connected - with those 2 different networks - do you have a transit setup with routes?
Why would not just use the transit networks IPs?
edit: ah they are connected via wireguard, so that is the transit..
So when you setup the access list, what does the query look like its coming from - is it natted to the wireguard IP?
-
ah they are connected via wireguard, so that is the transit..
yup
So when you setup the access list, what does the query look like its coming from - is it natted to the wireguard IP?
You mean on the wire or in theory?

I haven't checked with wireguard yet what excatly is being sent on the interfaces...Network A is 10.0.0.0/16
Network B is 10.10.0.0/16
Wireguard Network is 10.251.0.0/16I can access 10.10.0.1 from 10.0.0.1 directly without problems, no NAT happening there I think.
-
@soupdiver Sorry to necro, but did you ever resolve this? I cannot get domain overrides working over Wireguard. Host overrides work fine but not domain.
Very frustrating. -
@Squuiid where are you pointing for your domain override - also with a domain override, which is unbound asking another name server is answer is rfc1918 you could have a rebind issue.
-
Hi @johnpoz thanks for the quick reply!
domain overrides are as follows:domain.xxxx.edu -->. 10.20.30.10 (DC01 on other side of Wireguard s2s tunnel, site-b)
domain.xxxx.edu -->. 10.20.30.20 (DC02 on other side of Wireguard s2s tunnel, site-b)Site-a subnet 10.20.0.0/22
site-b subnet 10.20.28.0/22
I can ping remote site-b by IP from site-a just fine and vice-versa but I can only resolve DNS if I set a HOST Override. Domain overrides don't seem to work.
Client NIC on site-a has static DNS entries of the remote IPs (DCs) of site-b above.What am I doing wrong here?
-
@Squuiid said in DNS Domain override not working between 2 pfSense boxes:
Domain overrides don't seem to work.
because they would be a rebind most likely.. Can your client on your own network query pfsense and get an answer from the domain override?
When unbound on pfsense forwards to another name server, be it an actual forward or a domain override and the answer is rfc1918 - that is a rebind. And you would have to set the domain as private. I don't recall off the top of my head if when you set the domain override if that gets set as private or not and allows for the rfc1918 response.
But simple enough to check, do a directed query to pfsense IP - do you get an answer? with the rfc1918 IP you are expecting..
edit: ok setting a domain override does seem to auto add the private domain. I haven't used my test setup of this in a while.. But here setup a domain override.
See my domain override works for both public or rfc1918
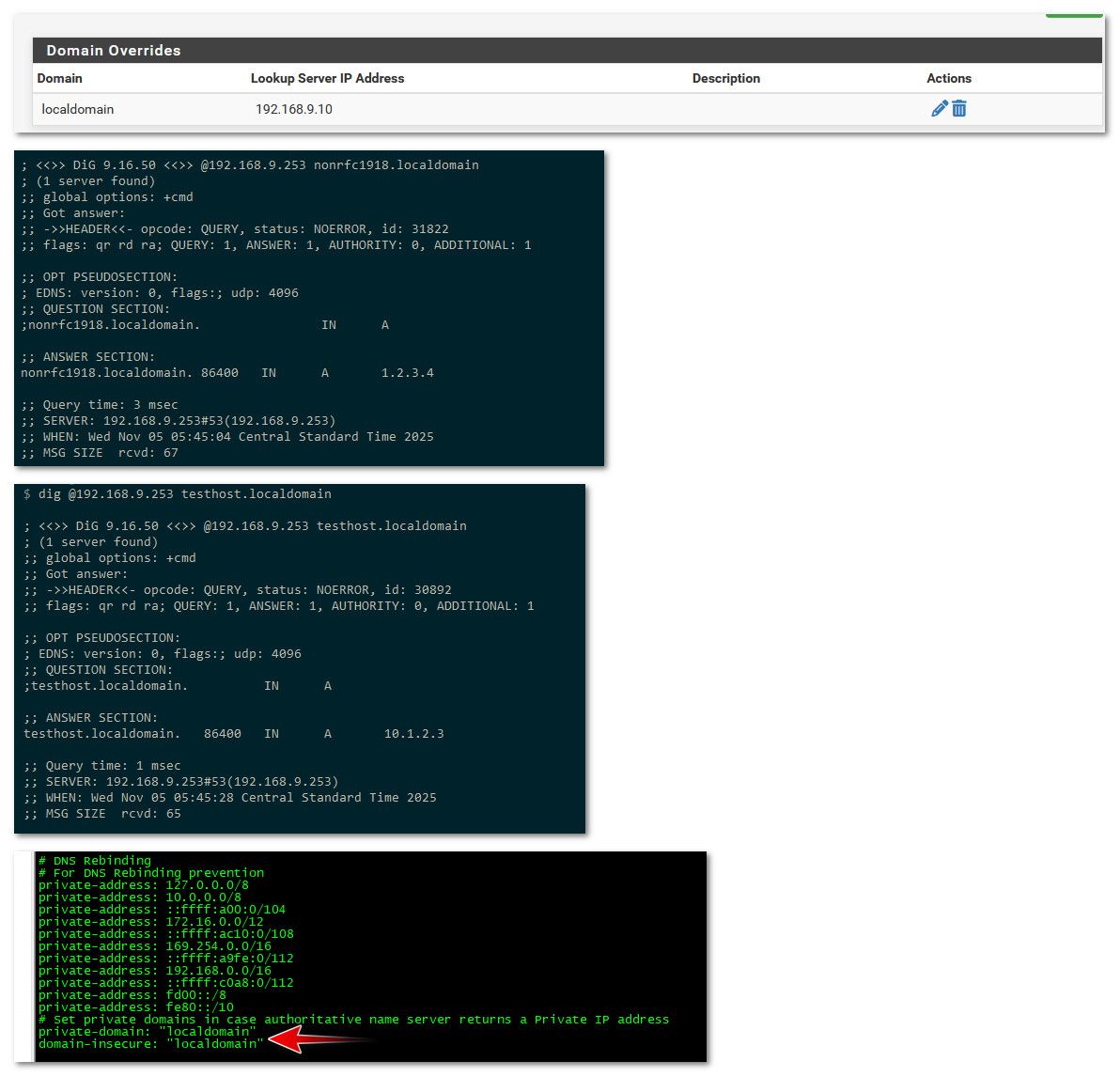
If I look in my /var/unbound/unbound.conf you can see that the private domain localdomain was added
What version of pfsense are you using - if old, this might not work.. But first step in troubleshooting this is validating if a client on your local network queries pfsense IP for some record in your override domain is you get an answer.
Does this work?
-
Using latest pfSense+ at both sites, 25.07.1
With HOST override:
PS C:\Users\Administrator> nslookup dc01.domain.xxxx.edu
Server: dc01.domain.xxxx.edu
Address: 10.20.30.10Name: dc01.domain.xxxx.edu
Address: 10.20.30.10Host not in Host overrides and hoping to use domain overrides:
PS C:\Users\Administrator> nslookup apps01.domain.xxxx.edu
Server: dc01.domain.xxxx.edu
Address: 10.20.30.10*** dc01.domain.xxxx.edu.ar can't find apps01.domain.xxxx.edu: Server failed
Using local pfSense IP and trying to use domain override:
PS C:\Users\Administrator> nslookup apps01.domain.xxxx.edu 10.20.0.1
Server: UnKnown
Address: 10.20.0.1DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to UnKnown timed-out
PS C:\Users\Administrator>No go unfortunately. Thank you for checking your unbound.conf though, really appreciate the help here.
-
@Squuiid said in DNS Domain override not working between 2 pfSense boxes:
Dude if your going to use nslookup, set debug so you can see exactly what is happening.. If unbound is listening on 10.20.0.1 this is a clear sign of failure.
Server: UnKnown Address: 10.20.0.1If you can not even resolve the nameserver your asking for its own name - you have something wrong.
$ nslookup Default Server: pi.hole Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.home.arpa Address: 192.168.9.253my windows pc defaults to using my pihole for dns, see how that pihole answered with its name when nslookup sent the ptr query.
And when I changed the server to use to my pfsense IP, unbound on pfsense answered the ptr that happens with its name.
This tells me more than likely there is no name server even running on 10.20.0.1
Server: UnKnown Address: 10.20.0.1 DNS request timed out. timeout was 2 seconds. DNS request timed out. timeout was 2 seconds. *** Request to UnKnown timed-outOr your client can not talk to that address, or your firewalls block talking to dns from that client to that IP, etc.
But any time you get an unknown for the name server your talking to - something is clearly wrong.
-
@johnpoz Oh dear. My Outgoing Network Interfaces on the resolver did not include my WireGuard tunnel. Problem solved. So sorry to have wasted your time, I'm incredibly grateful for your help. It got me there in the end quite honestly, thank you.
Oh and on this, "Dude if your going to use nslookup, set debug so you can see exactly what is happening",
 agreed, my bad!
agreed, my bad!