Problems with IPsec in HA
-
Good afternoon everyone,
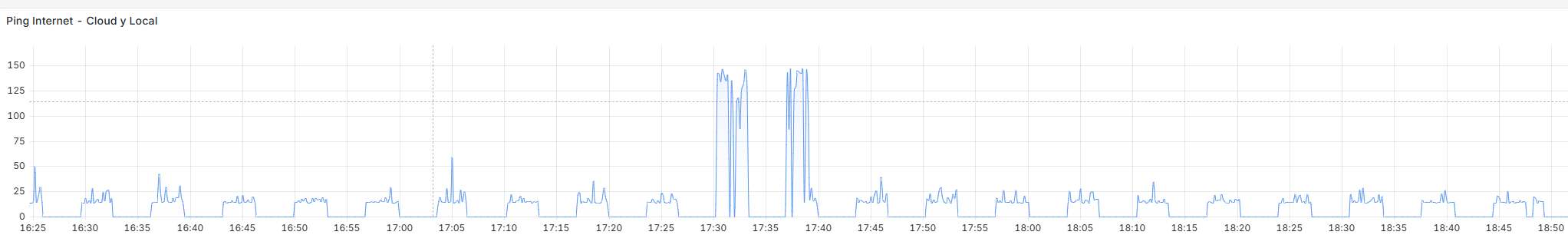
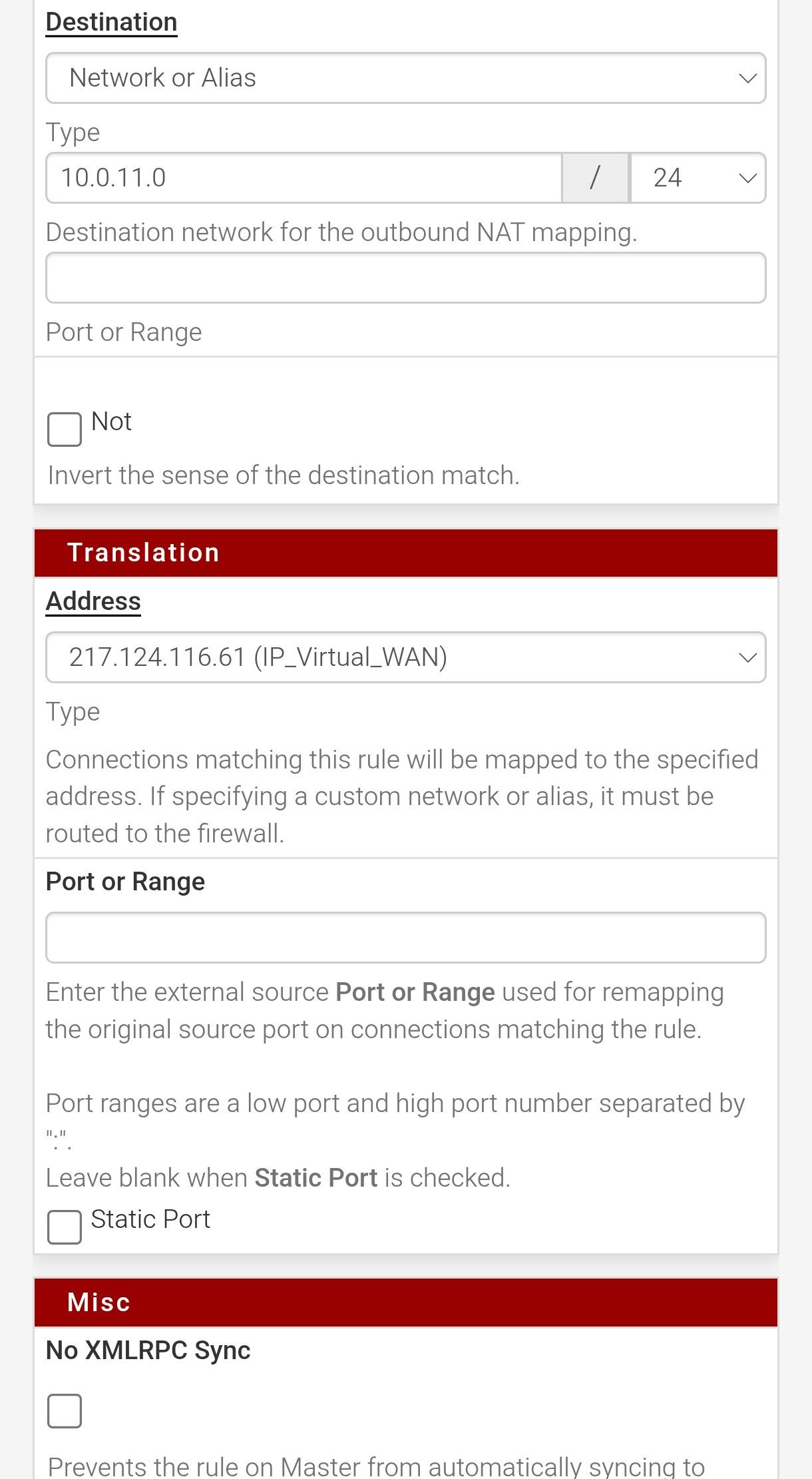
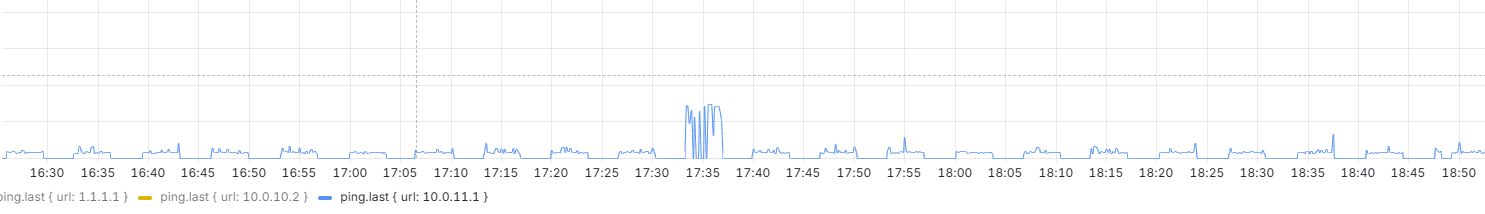
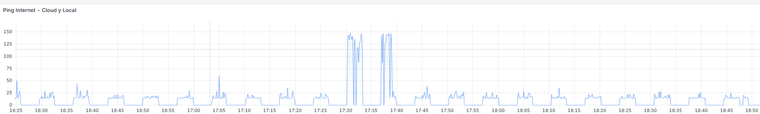
I'm having a problem that is driving me crazy. I have an IPsec tunnel in an HA environment, and the issue is that both HA members are continuously connecting and disconnecting. I’m using the CARP VIP on the WAN interface as stated in the official documentation. DPD is set to 20, I’ve tested with it disabled as well, and the behavior is the same. As I mentioned, one node brings the tunnel up and then the other takes over, and this happens every 3–4 minutes.
As you can see in the graphs:
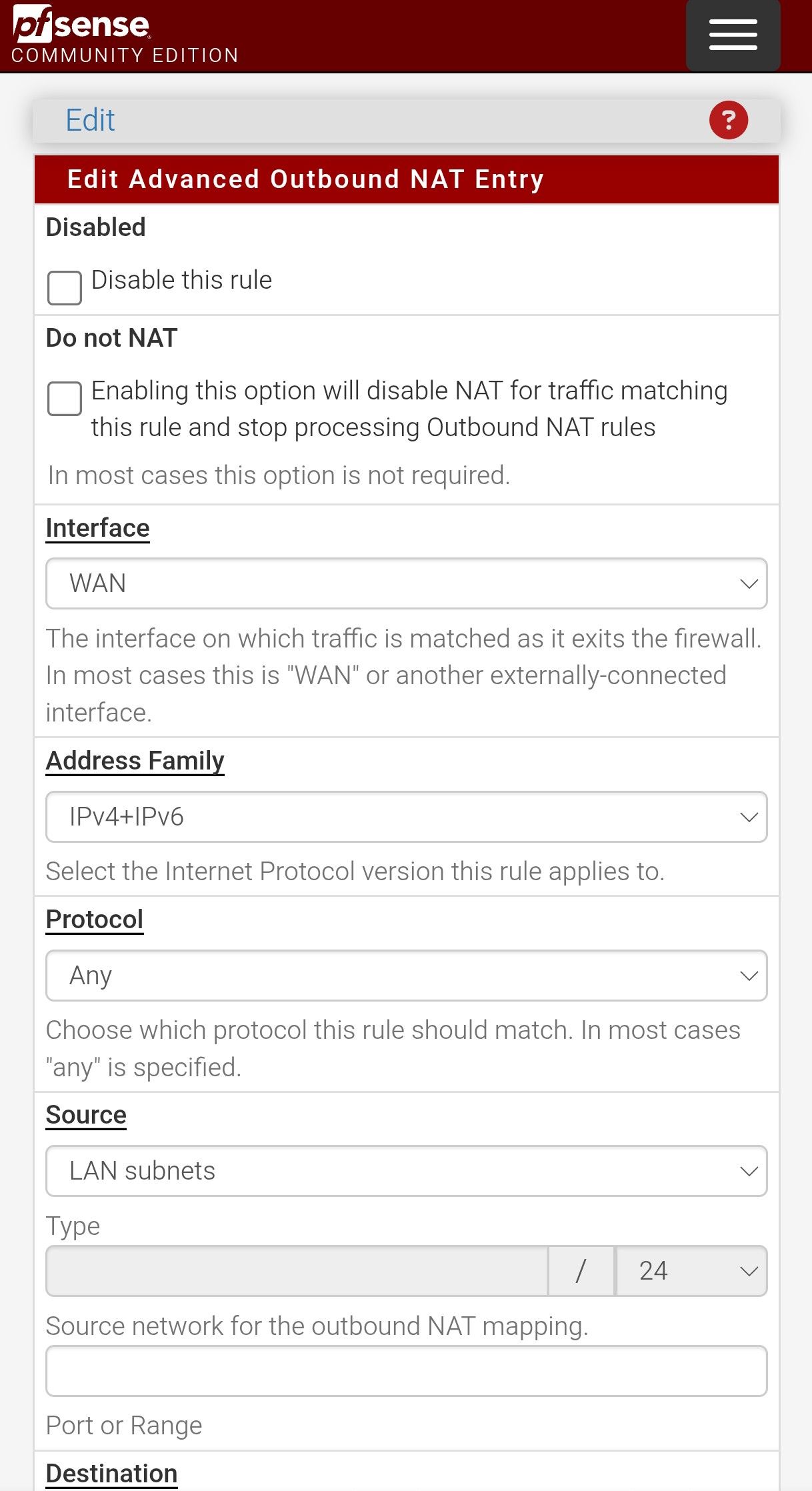
Here is my advanced configuration:
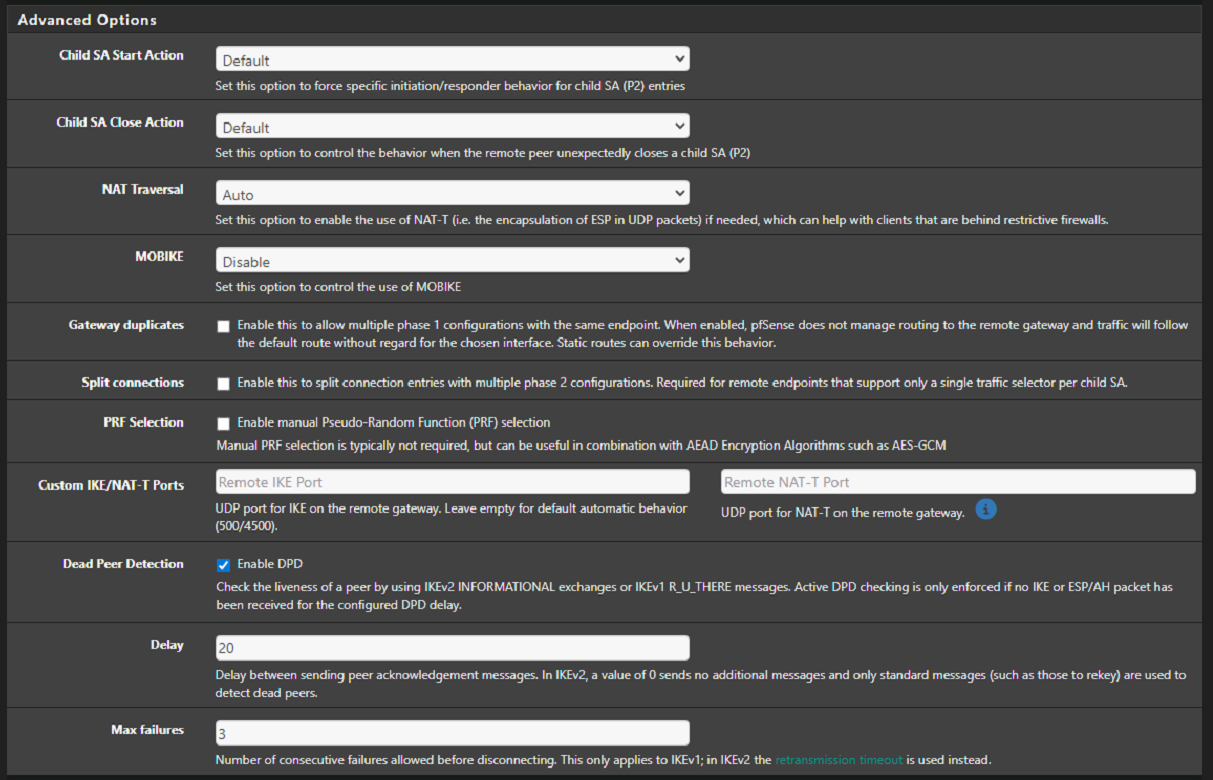
-
@dcuadrados said in Problems with IPsec in HA:
I’m using the CARP VIP on the WAN interface as stated in the official documentation.
Did you also translate IPSec outbound traffic to the CARP VIP?
-
This post is deleted! -
-
@dcuadrados
I was talking about outbound NAT rules (2) for IPSec from pfSense itself.
Should look like this:Interface: WAN
Source: network > 127.0.0.0/8
destination: any
destination port: 500
translation: VIP
static port: checkedInterface: WAN
protocol: UDP
Source: network > 127.0.0.0/8
destination: any
destination port: 4500
translation: VIP -
@viragomann OK, I’ve created it this way and I’m going to monitor the status to see what happens and how the tunnel behaves from this point on. Thanks a lot!