Internet secondary networks can't reach lan servers at all
-
So this is a conundrum that is making me dizzy.
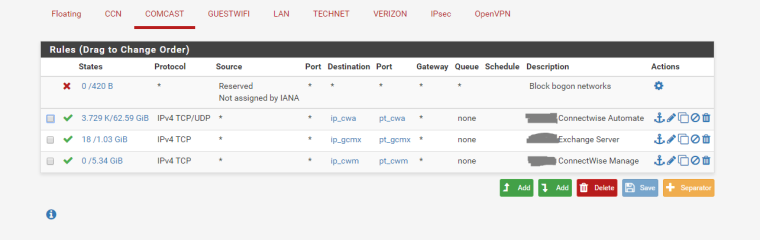
I have two wans, with a number of static IPs each. I have servers hosted over a bunch of IPs and I force outbound traffic to go out its inbound traffic IP for these servers.
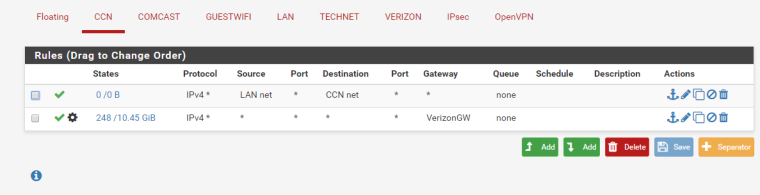
From the LAN I have a bunch of servers, all with their own IP. I can reach those servers internally or through the external IP no problem.
From the two other networks that I have, I can't see the servers internally or externally, yet I can reach everything from LAN.
I put it all sorts of rules allowing LAN to OPT and all that - it just doesn't want to work. I have PureNAT enabled and Hybrid outbound based on IP.
I have a more indepth breakdown here: https://forum.pfsense.org/index.php?topic=147965
But the network AGC and CCN I want to be able to see my LAN external servers without issue.
-
I'm looking to get an answer to this...
-
@meeleikon said in Internet secondary networks can't reach lan servers at all:
I can’t see the servers internally or externally, yet I can reach everything from LAN.
What does that mean.. How about you show the rules you have on your interface. And what your trying to do to this server in the lan. What IP are you hitting are you trying to use nat reflection?
-
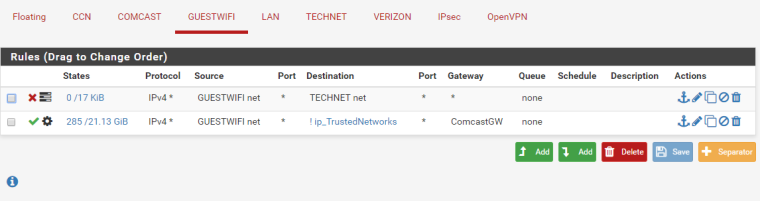
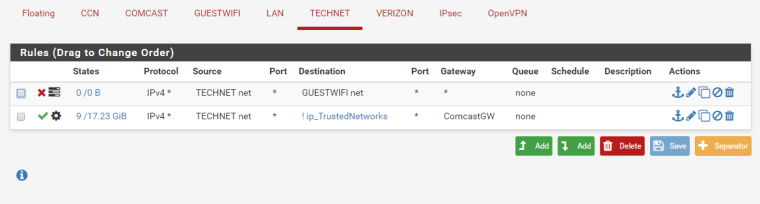
While on either CCN network, the GuestWifi network or the Technet network, I am totally unable to reach any of my servers hosted from the LAN by their external IP addresses. Now on the GuestWifi and Technet I want to block all access to my local lan through LOCAL addresses, but still be able to access my servers from their EXTERNAL addresses.
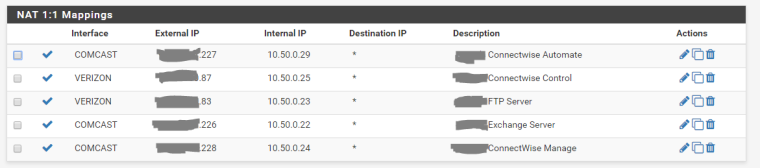
For example, I am on the Guest Wireless with an IP address of 172.16.2.16 and I try to reach mail.mycomp.com which resolves to 123.234.111.226 which has a 1:1 NAT for 10.50.0.22, I am unable to reach it. When I am on the LAN, I can reach it from it's external address. Even on CCN, I am unable to reach mail.mycomp.com from it's external address but from CCN if I did 10.50.0.22, I would have no problem.
I have everything set up for Pure-NAT.
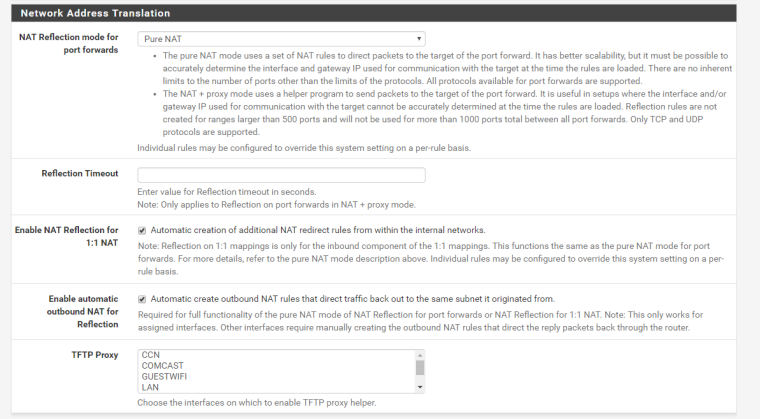
Interfaces
 image url)
image url)1:1 Mappings
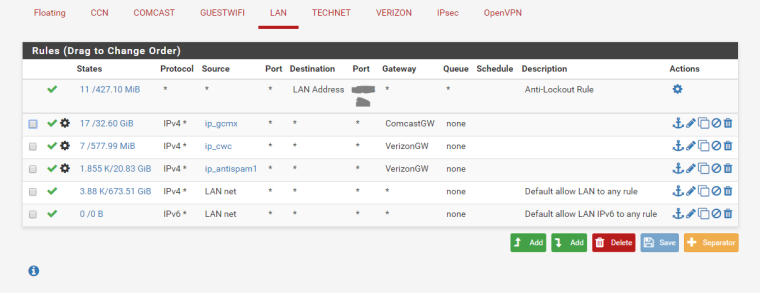
Rules
-
@meeleikon said in Internet secondary networks can't reach lan servers at all:
from the LAN by their external IP addresses.
Didnt read past that... Why would you do that?? So you want to go out wan 1, out the public internet down the public internet via the other connection, etc..
Just setup host overrides to connect to the local IP..
And your forcing traffic down gateways in you rules as well. You need to allow for the local access before you shove something out a gateway.
-
we own the building and provide guest wireless, but we have tenants, other companies. We don't need their people seeing our LAN. However, we are an MSP, so at the same time we may have Labtech agents on their machines that need to talk to support.mycomp.com by that external. We also may have PC's in for repair on the technet, that may be infected with viruses or anything else, but we still need access to our tools from the web.
So yes, on the wifi I literally want it to go out the GuestWifi Net, out the external WAN that is set on and come right back in through the firewall as if it was a completely segregated network with its own firewall but without me stuffing anymore stuff in my racks.
We can't use Host file overrides. #1 these machines may be here temporarily and then they would not work after they leave here, and I don't want to have to set all that up, the tenants in my building who are also customers of our IT services, it's probably 80 - 90 machines.
-
Well do that for them then... You would not be using any nat reflection if you want to go out the internet and come back in another internet.
If you want to allow access locally not using internet path, then allow that..
-
I'm not sure I follow. Turn off PureNAT then?
What would happen to the LAN, which works fine?
-
Honestly, it sounds like you are trying to get one router doing more than it should be being asked to do. Not really that it can't do it but there are two distinctly different purposes in play here.
we own the building and provide guest wireless, but we have tenants, other companies. We don’t need their people seeing our LAN. However, we are an MSP, so at the same time we may have Labtech agents on their machines that need to talk to support.mycomp.com by that external. We also may have PC’s in for repair on the technet, that may be infected with viruses or anything else, but we still need access to our tools from the web.
So yes, on the wifi I literally want it to go out the GuestWifi Net, out the external WAN that is set on and come right back in through the firewall as if it was a completely segregated network with its own firewall but without me stuffing anymore stuff in my racks.
The router is not going to send something out to the internet when it is destined for an address on the router itself. Maybe with policy routing. But it really sounds like things might make more sense if you had a Guest/ISP/Tenant firewall and an MSP/Development/Testing firewall.
All gets infinitely easier with a proper routed subnet you can use on an inside interface instead of this 1:1 + NAT reflection stuff.
To expand on your specific example (thank you for that) when you enable NAT reflection the NAT happens when the connection enters the GUESTWIFI interface. Then the firewall rules on that incoming interface are processed. When you connect from 172.16.2.16 to 123.234.111.226, the first thing that happens is the NAT reflection.
Now you are dealing with a connection from 172.16.2.16 to 10.50.0.22 as far as the firewall rules are concerned.
You are passing traffic on the GUESTWIFI interface to ! ip_TrustedNetworks Does that traffic match the post-NAT destination? I am guessing not as I am assuming 10.50.0.0/24 is included in the ip_TrustedNetworks alias.
(Blocking traffic using a pass to ! rule is another issue for another day. My advice is to BLOCK/REJECT to ip_TrustedNetworks then PASS to any)
So, on GUESTWIFI, you probably want to specifically pass the connections to the REAL IP ADDRESS of the destination host, 10.50.0.22 in this case (limiting to specific ports, etc ok here to, such as destination TCP 25, 587, 465, 110, 143, 993, and 995 for your typical, non-microsoft mail server.)