Multi WAN not Load Balancer and Failover
-
Dear all,
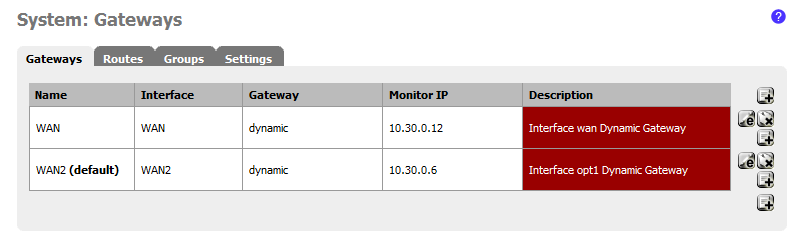
At the present, I have two fiber line which come from two ISP A and B were connected to 2 interfaces directly ( interface rl0 (WAN 1) and rl1 (WAN 2)) on pfsense with PPoE connection type. I use pfsense 2.0 beta. I connected internet with two line. I can't load banlancer and failover with two line. I readed topic " Outbound Load Balancing is replaced " and I edit as WAN Tier 1, WAN 2 Tier 1 but it not load balancer. You can help me load banlancer with step to step. In pfsense 2.0 beta I don't find tick Load Banlancer or tick Failover as pfsense 1.2.3. I'm new bie. Please help me. Thanks all.
ISP A ISP B
| |
| |
|Interface rl0 | Interface rl1
| |
WAN 1 (PPOE) WAN 2 (OPT1) (PPPoE)
–-------------- PFSense ---------------
|
|
|Interface re0
|
LAN -
I like the way they did it in this version… All you have to do is get to the gateway setup area under "Status" and then "Gateways". In there you will see the gateways you setup for your two ISP's for the interface setup. There is also a tab for Gateway Groups. You can make as many groups as you want and assign the gateways different weights which will either allow bandwidth sharing or failover. Then just assign the gateway groups to your traffic via the Rules screen.
Vola!
Hope this helps... If you need a better description, search this forum a little more. That is how I got this far.
-
A lot of fixes went into the gateway code last Friday, so before you do anything else, make sure you are at least on a snapshot from last Saturday or Sunday, but preferably a fresh new one.
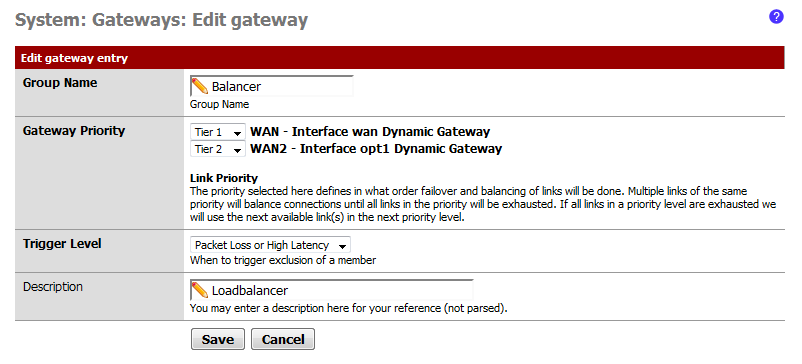
If you make a gateway group where both members are of the same tier, they will load balance, if setup properly.
I know it works because I'm using it right now, on DSL and Cable, and the gateway weighting works very well too.
-
I just download and setup snapshot pfSense-2.0-BETA1-20100505-2043.iso.gz (05-May-2010 21:02) but I don't setup loadbalancer and failover. I make a gateway group where both members are of the same tier 1. What I need it work ? Thanks all
-
Use the gateway group on a Firewall->Rule.