Tunnel is working, but no traffic over it
-
I have set up a ipsec tunnel with my Pfsense box (2.0) and my Zyxel NBG460 (home) router, the tunnel comes up easily and show up active on the pfsense box and the Zyxel, but i cant ping from both sides.
I try to ping from a workstation behind the pfsense to a workstation behind the home router, but it fails. When i try from home workstation to workstations behind pfsense it fails too…
I do have a firewall rule on the ipsec tab allow 'any to any' (all proto's and ports)
This is my racoon.conf:# This file is automatically generated. Do not edit path pre_shared_key "/var/etc/psk.txt"; path certificate "/var/etc"; listen { adminsock "/var/db/racoon/racoon.sock" "root" "wheel" 0660; isakmp 84.53.113.133 [500]; isakmp_natt 84.53.113.133 [4500]; } remote 84.82.252.146 { ph1id 1; exchange_mode main; my_identifier address 192.168.0.1; peers_identifier address 192.168.3.1; ike_frag on; generate_policy = off; initial_contact = on; nat_traversal = on; dpd_delay = 10; dpd_maxfail = 5; support_proxy on; proposal_check claim; proposal { authentication_method pre_shared_key; encryption_algorithm 3des; hash_algorithm md5; dh_group 2; lifetime time 28800 secs; } } sainfo subnet 192.168.0.1/23 any subnet 192.168.3.1/24 any { remoteid 1; encryption_algorithm 3des; authentication_algorithm hmac_md5; pfs_group 1; lifetime time 28800 secs; compression_algorithm deflate; }This is the ipsec log:
Dec 9 10:16:40 racoon: [Thijs-Thuis]: INFO: IPsec-SA established: ESP 84.53.113.133[500]->84.82.252.146[500] spi=3024575947(0xb4475dcb) Dec 9 10:16:40 racoon: [Thijs-Thuis]: INFO: IPsec-SA established: ESP 84.82.252.146[0]->84.53.113.133[0] spi=258636965(0xf6a7ca5) Dec 9 10:16:40 racoon: INFO: Adjusting peer's encmode UDP-Tunnel(61443)->Tunnel(1) Dec 9 10:16:40 racoon: INFO: Adjusting my encmode UDP-Tunnel->Tunnel Dec 9 10:16:40 racoon: WARNING: attribute has been modified. Dec 9 10:16:39 racoon: INFO: NAT detected -> UDP encapsulation (ENC_MODE 1->61443). Dec 9 10:16:39 racoon: [Thijs-Thuis]: INFO: initiate new phase 2 negotiation: 84.53.113.133[500]<=>84.82.252.146[500] Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: ISAKMP-SA established 84.53.113.133[500]-84.82.252.146[500] spi:539465d20c654c9f:04e75bda866433a6 Dec 9 10:16:38 racoon: WARNING: ignore INITIAL-CONTACT notification, because it is only accepted after phase1\. Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: KA list add: 84.53.113.133[500]->84.82.252.146[500] Dec 9 10:16:38 racoon: INFO: NAT detected: PEER Dec 9 10:16:38 racoon: INFO: NAT-D payload #1 doesn't match Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: Hashing 84.82.252.146[500] with algo #1 Dec 9 10:16:38 racoon: INFO: NAT-D payload #0 verified Dec 9 10:16:38 racoon: INFO: Hashing 84.53.113.133[500] with algo #1 Dec 9 10:16:38 racoon: INFO: Adding remote and local NAT-D payloads. Dec 9 10:16:38 racoon: INFO: Hashing 84.53.113.133[500] with algo #1 Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: Hashing 84.82.252.146[500] with algo #1 Dec 9 10:16:38 racoon: INFO: Selected NAT-T version: draft-ietf-ipsec-nat-t-ike-00 Dec 9 10:16:38 racoon: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-00 Dec 9 10:16:38 racoon: INFO: begin Identity Protection mode. Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: initiate new phase 1 negotiation: 84.53.113.133[500]<=>84.82.252.146[500] Dec 9 10:16:38 racoon: [Thijs-Thuis]: INFO: IPsec-SA request for 84.82.252.146 queued due to no phase1 found.This the Zyxel configuration:
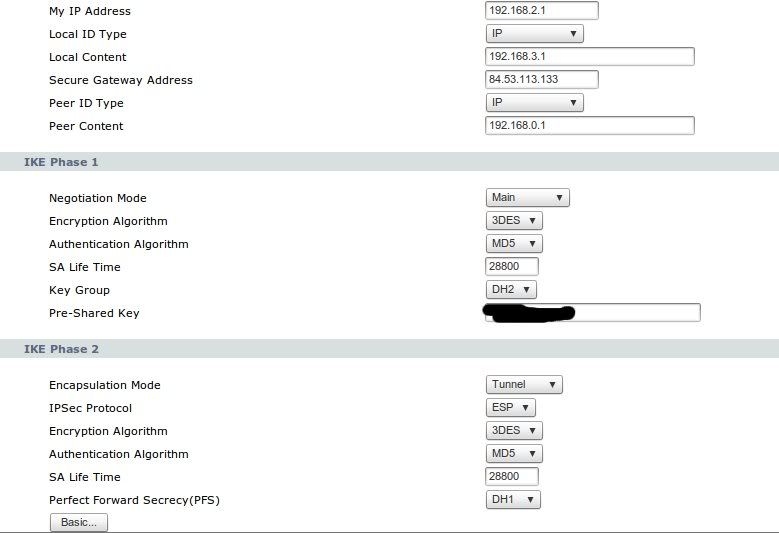
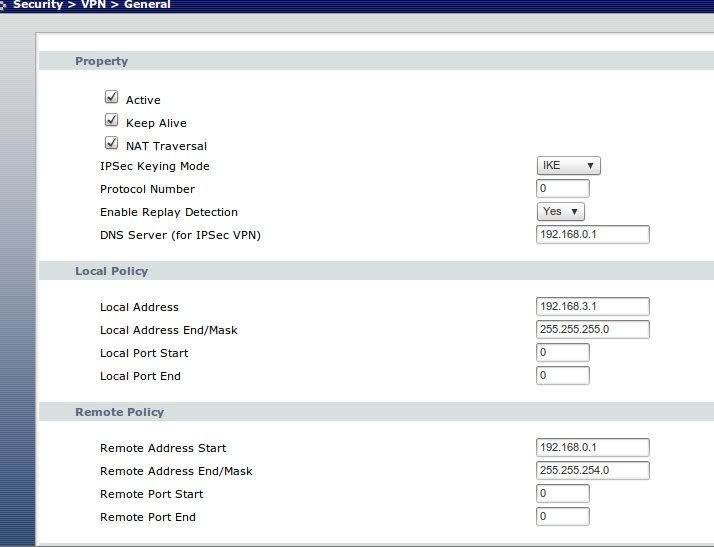
The Zyxel (wan 192.168.2.1, lan 192.168.3.1) is behind a ADSL NAT router (192.168.2.254) which is configured IPSEC and ESP ports forwarded to the zyxel.
VPN has worked to the Zyxel previously with another firewall, so that should not be the problem.This is the Zyxel Log:
1 12/09/2010 10:15:49 Rule [2] Tunnel built successfully 84.53.113.133 192.168.2.1 IKE 2 12/09/2010 10:15:49 Adjust TCP MSS to 1398 192.168.2.1 84.53.113.133 IKE 3 12/09/2010 10:15:49 Recv:[HASH] 84.53.113.133 192.168.2.1 IKE 4 12/09/2010 10:15:49 Send:[HASH][SA][NONCE] 192.168.2.1 84.53.113.133 IKE 5 12/09/2010 10:15:49 Start Phase 2: Quick Mode 84.53.113.133 192.168.2.1 IKE 6 12/09/2010 10:15:49 Recv:[HASH][SA][NONCE][KE][ID][ID] 84.53.113.133 192.168.2.1 IKE 7 12/09/2010 10:15:48 Phase 1 IKE SA process done 192.168.2.1 84.53.113.133 IKE 8 12/09/2010 10:15:48 Send:[ID][HASH][NOTFY:INIT_CONTACT] 192.168.2.1 84.53.113.133 IKE 9 12/09/2010 10:15:48 Recv:[ID][HASH] 84.53.113.133 192.168.2.1 IKE 10 12/09/2010 10:15:48 Send:[KE][NONCE] 192.168.2.1 84.53.113.133 IKE 11 12/09/2010 10:15:47 Recv:[KE][NONCE][UNKNOWN(130)][UNKN 84.53.113.133 192.168.2.1 IKE 12 12/09/2010 10:15:47 Send:[SA][VID][VID] 192.168.2.1 84.53.113.133 IKE 13 12/09/2010 10:15:47 Recv:[SA][VID][VID][VID][VID][VID][ 84.53.113.133 192.168.2.1 IKE 14 12/09/2010 10:15:47 Recv Main Mode request from [84.53.113.133] 84.53.113.133 192.168.2.1 IKE 15 12/09/2010 10:15:47 Rule [2] Receiving IKE request 84.53.113.133 192.168.2.1 IKE 16 12/09/2010 10:14:53 Send:[HASH][DEL] 192.168.2.1 84.53.113.133 IKE 17 12/09/2010 10:14:53 Adjust TCP MSS to 1460 192.168.2.1 84.53.113.133 IKE 18 12/09/2010 10:14:53 Send:[HASH][DEL] 192.168.2.1 84.53.113.133 IKEWhen i log the firewall rules and ping from Zyxel workstation to pfsense workstation i do see traffic coming from 192.168.3.33 'enc0' to lan (192.168.0.151) and the traffic is passed.
When i ping from pfsense workstation to the zyxel workstation i see traffic from lan (192.168.0.151) going to 192.168.3.33 and getting passed..So all looks fine, but i cant ping or do anything else with the tunnel…
Thanks for your help -
In addition to above post:
I am running the IPsec tunnel on my OPT1 (wan2ADSL) interface, which is (currently) default gateway. Should I add a static route to route the IPSEC traffic trough OPT1 or not??
-
Found out what the problem was.
My WAN interface is down, and i configered the IPsec tunnel from opt1.
When i Disabled WAN interface my vpn was working :)