Configuring VPN win7 clients with pfsense
-
Guys…i'm waiting you .
-
Waiting for what?
So now your pfsense has public IP on its wan? Then run through the openvpn wizard and your done.. Not sure what else you think you need to do?
What is not working now?
-
Waiting for what?
So now your pfsense has public IP on its wan? Then run through the openvpn wizard and your done.. Not sure what else you think you need to do?
What is not working now?
I'm waiting for this :i could see any device on my network (servers,printers,etc) .
-
Yeah once you vpn in, depending on what firewall rules you put in place you can access anything you want on your network. I vpn into my home network pretty much every day. I am on now - yes I can print to my printer if I want, I can remote desktop to any box on my network, I can access my file shares, etc. etc. etc.
D:>net view \storage.local.lan
Shared resources at \storage.local.lanMy storage server
Share name Type Used as Comment
–-----------------------------------------------------------------------------
J Disk
Media Disk
Molly Disk
temp Disk
The command completed successfully.Thats my NAS on my home network, while I am here at work.
-
Yeah once you vpn in, depending on what firewall rules you put in place you can access anything you want on your network. I vpn into my home network pretty much every day. I am on now - yes I can print to my printer if I want, I can remote desktop to any box on my network, I can access my file shares, etc. etc. etc.
D:>net view \storage.local.lan
Shared resources at \storage.local.lanMy storage server
Share name Type Used as Comment
–-----------------------------------------------------------------------------
J Disk
Media Disk
Molly Disk
temp Disk
The command completed successfully.Thats my NAS on my home network, while I am here at work.
So tell me what are rules will i use ?
thank you .
-
You wouldn't use any rules really unless you want to limit or block something - wizard should create the default rule
IPv4 * * * * * * none OpenVPN pfsense wizard
The above is what I have in my openvpn tab
-
You wouldn't use any rules really unless you want to limit or block something - wizard should create the default rule
IPv4 * * * * * * none OpenVPN pfsense wizard
The above is what I have in my openvpn tab
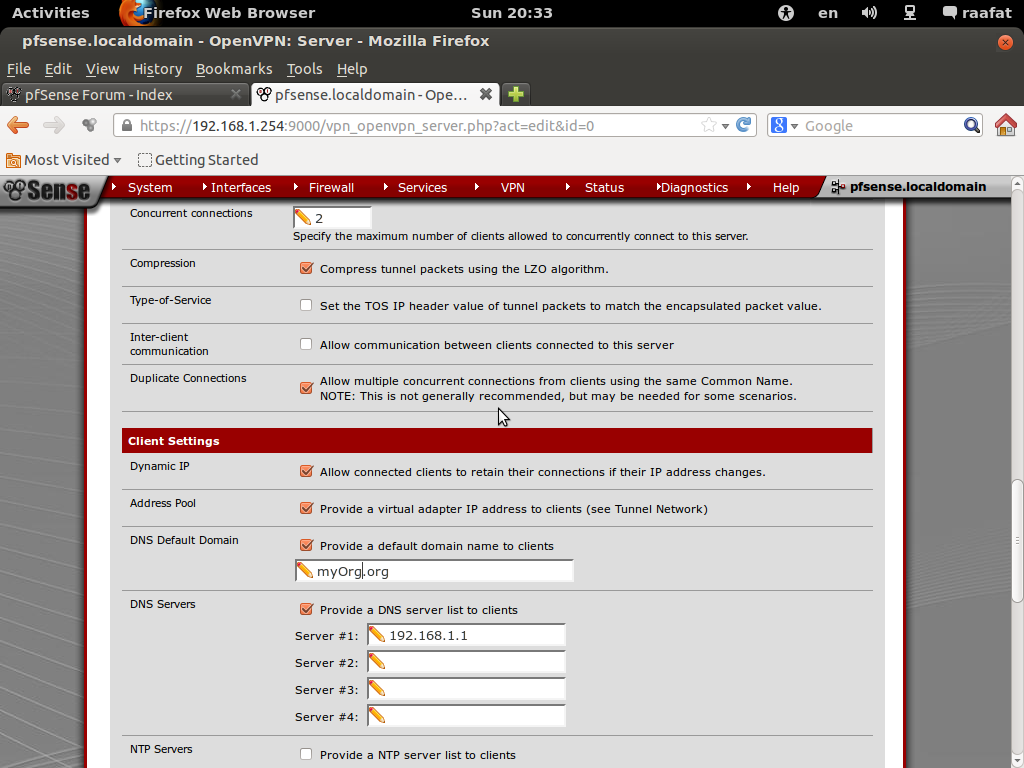
What is subnet' ip address are you using and for vpn' clients ?
-
You can use whatever you want.. I use 2 different ones for tcp or udp connections I use
NO TCP / 443 10.0.200.0/24 pfsense tcp
NO UDP / 1194 10.0.8.0/24 pfsense udpJust use something that is unlikely to conflict with the network segment connecting to you.
-
You can use whatever you want.. I use 2 different ones for tcp or udp connections I use
NO TCP / 443 10.0.200.0/24 pfsense tcp
NO UDP / 1194 10.0.8.0/24 pfsense udpJust use something that is unlikely to conflict with the network segment connecting to you.
So why i could not see any device on my network also i can't ping any device except my pfsense ?
i have a rule like your rule on my WAN and LAN
-
Are we to just guess your setup? For all I know you have host firewalls blocking ping. What does could not see mean? Are you talking like a windows browse list - thats not going to happen over different segments and a nat. You could run a wins server if you want to have browselists across segments.
For all we know you have 192.168.1.0/24 on your pfsense lan side and remote network is also 192.168.1.0/24 – are you sending your route, is the client getting the route?
Post up your openvpn config, did you do a traceroute from the client that could not ping your pfsense box? Is he sending the traffic down the tunnel?
-
Are we to just guess your setup? For all I know you have host firewalls blocking ping. What does could not see mean? Are you talking like a windows browse list - thats not going to happen over different segments and a nat. You could run a wins server if you want to have browselists across segments.
For all we know you have 192.168.1.0/24 on your pfsense lan side and remote network is also 192.168.1.0/24 – are you sending your route, is the client getting the route?
Post up your openvpn config, did you do a traceroute from the client that could not ping your pfsense box? Is he sending the traffic down the tunnel?
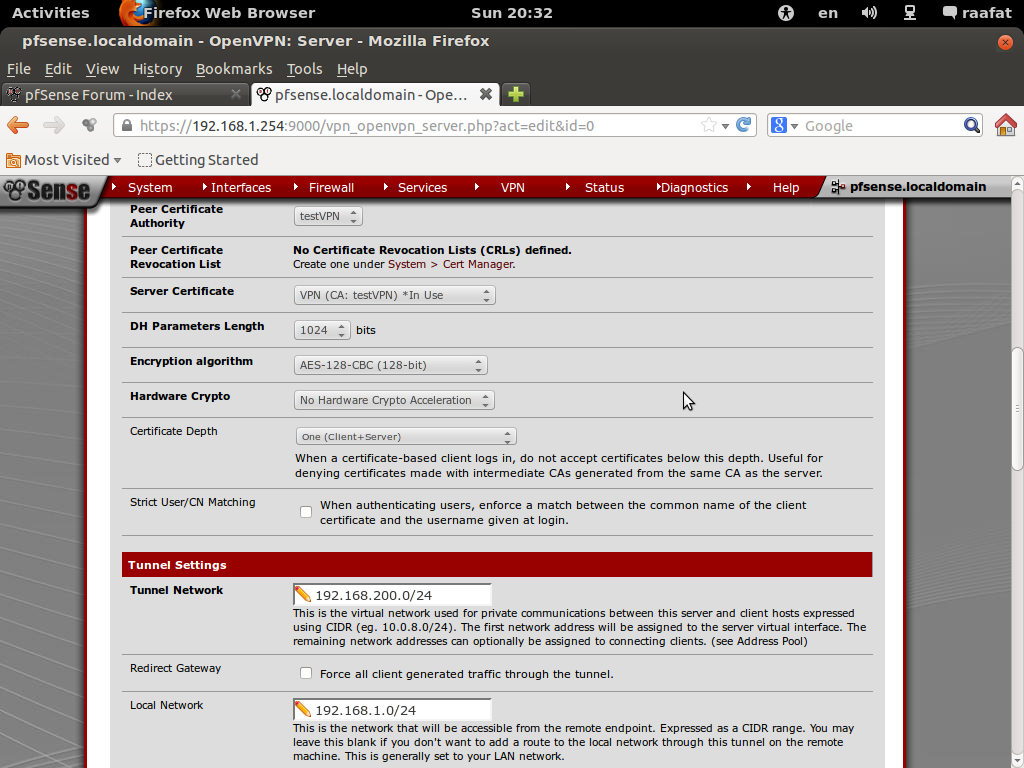
tunnel network : 192.168.10.0/24
my lan:192.168.1.0/24after connecting to my network i got 192.168.10.6 (windows told me that )
after that i can ping only pfsense box
tell me exactly what are you looking about openvpn confi because there are many fields with vpn confi .
Also about i could't see any device i mean at least i ping them (my devices:pritner,computers,servers)
and sharing files .i hope what i told you to be helpful .
thank you .
-
And where are you connecting from? What is that network?
Post up output of route print after you connect.
Do a traceroute to the IP your trying to ping.
So what if there are multiple fields, here attached is mine.. And then the client config from client export. Just snipped out part of public IP for privacy.
–
dev tun
persist-tun
persist-key
cipher BF-CBC
tls-client
client
resolv-retry infinite
remote 24.13.xx.xx 443 tcp
tls-remote pfsense-openvpn
pkcs12 pfsense-TCP-443-johnpoz.p12
tls-auth pfsense-TCP-443-johnpoz-tls.key 1
ns-cert-type server
comp-lzo
-
And where are you connecting from? What is that network?
Post up output of route print after you connect.
Do a traceroute to the IP your trying to ping.
So what if there are multiple fields, here attached is mine.. And then the client config from client export. Just snipped out part of public IP for privacy.
–
dev tun
persist-tun
persist-key
cipher BF-CBC
tls-client
client
resolv-retry infinite
remote 24.13.xx.xx 443 tcp
tls-remote pfsense-openvpn
pkcs12 pfsense-TCP-443-johnpoz.p12
tls-auth pfsense-TCP-443-johnpoz-tls.key 1
ns-cert-type server
comp-lzo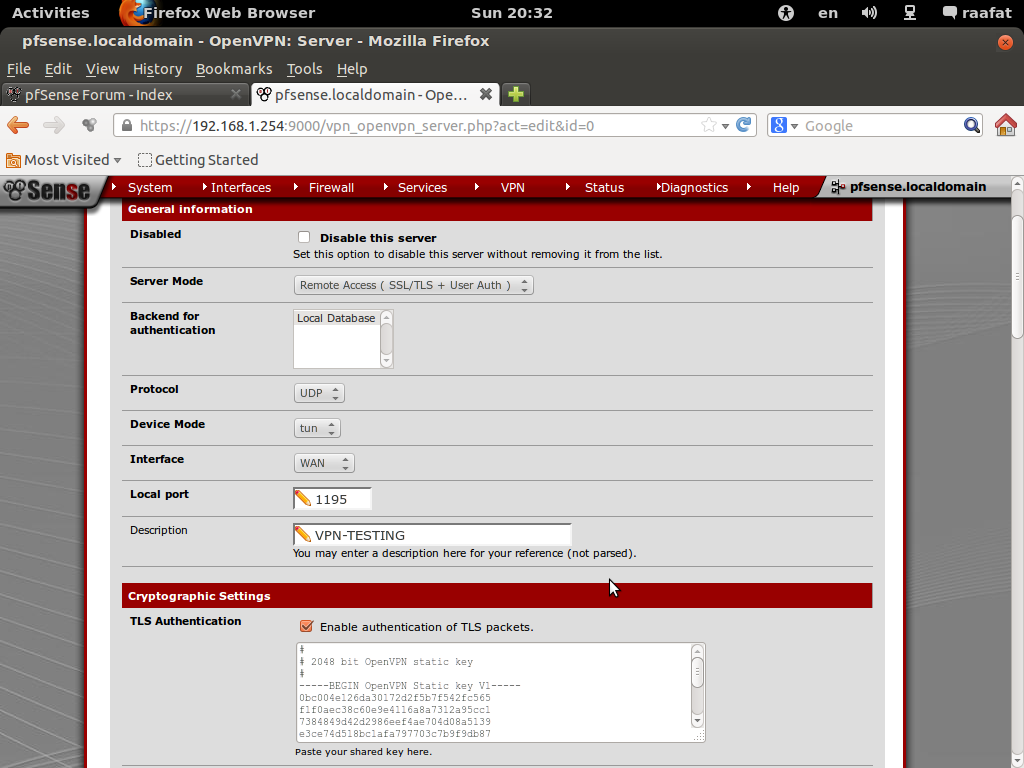
after connecting to my pfsense this is what i got :
Sun Feb 17 20:45:14 2013 OpenVPN 2.2.1 Win32-MSVC++ [SSL] [LZO2] built on Jul 1 2011 Sun Feb 17 20:45:17 2013 WARNING: Make sure you understand the semantics of --tls-remote before using it (see the man page). Sun Feb 17 20:45:17 2013 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables Sun Feb 17 20:45:17 2013 Control Channel Authentication: using 'pfsense-udp-1195-internal-ca-tls.key' as a OpenVPN static key file Sun Feb 17 20:45:17 2013 LZO compression initialized Sun Feb 17 20:45:17 2013 UDPv4 link local (bound): [undef]:1194 Sun Feb 17 20:45:17 2013 UDPv4 link remote: 37.xxx.xxx.xxx:1195 Sun Feb 17 20:45:17 2013 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Sun Feb 17 20:45:20 2013 [internal-ca] Peer Connection Initiated with 37.xxx.xxx.xxx:1195 Sun Feb 17 20:45:23 2013 TAP-WIN32 device [Local Area Connection 2] opened: \\.\Global\{BFEE7338-93E9-47C0-8501-430F8AC797C1}.tap Sun Feb 17 20:45:23 2013 Notified TAP-Win32 driver to set a DHCP IP/netmask of 192.168.200.6/255.255.255.252 on interface {BFEE7338-93E9-47C0-8501-430F8AC797C1} [DHCP-serv: 192.168.200.5, lease-time: 31536000] Sun Feb 17 20:45:23 2013 Successful ARP Flush on interface [23] {BFEE7338-93E9-47C0-8501-430F8AC797C1} Sun Feb 17 20:45:28 2013 WARNING: potential route subnet conflict between local LAN [192.168.1.0/255.255.255.0] and remote VPN [192.168.1.0/255.255.255.0] Sun Feb 17 20:45:28 2013 Initialization Sequence Completedafter pinging 192.168.1.1 :
reqeust timed outAlso :
Tracing route to 192.168.1.1 over a maximum of 30 hops 1 55 ms 55 ms 53 ms 192.168.200.1 2 * * * Request timed out. 3 * * * Request timed out. 4 * *thank you .
-
Also :
dev tun persist-tun persist-key proto udp cipher AES-128-CBC tls-client client resolv-retry infinite remote 37.xxx.xxx.xxx 1195 tls-remote internal-ca auth-user-pass pkcs12 pfsense-udp-1195-internal-ca.p12 tls-auth pfsense-udp-1195-internal-ca-tls.key 1 comp-lzo -
And what part do you not understand about this???
WARNING: potential route subnet conflict between **local LAN [192.168.1.0[/b]/255.255.255.0] and **remote VPN [192.168.1.0[/b]/255.255.255.0]
Your networks on both sides are the SAME!!!! NOT going to work!!
You have
192.168.1.0/24 –- tunnel --- 192.168.1.0/24
Does not work like that.. Even if client that is directly connected to the tunnel sends his traffic down the tunnel. And a client on the vpn side sees the traffic - its going to be from a 192.168.1.0 address, never going to send it back to pfsense because that is the vpn boxes LOCAL network, no need to talk to pfsense.
You need this
192.168.A.0/24 –- tunnel --- 192.168.B.0/24
You can not have the same network on both sides of a tunnel and expect it to work without doing some fancy NATing of the connection.. If your remote network is 192.168.1.0, make your local network 192.168.72.0/24 or something - that is unlikely to be used anywhere that would be remote into your network.****
-
Hmm also, so your pfsense box default gateway for clients on vpn side? If so then road warrior that uses the tunnel IP as its source should be able to talk to clients on the vpn side even with a dupe IP.
Site to site would be a major issue! But if the box on the vpn side is not using pfsense as default gateway - then again your not going to be able to talk..
So I notice you point dns to 192.168.1.1, but in your address bar your access pfsense at 192.168.1.254.. So this box your trying to talk to at 192.168.1.1 in your traceroute - is his default gateway off 192.168.1.0/24 the pfsense box at 192.168.1.254?
What is this 192.168.1.1 box? What is his default gateway?
-
Hmm also, so your pfsense box default gateway for clients on vpn side? If so then road warrior that uses the tunnel IP as its source should be able to talk to clients on the vpn side even with a dupe IP.
Site to site would be a major issue! But if the box on the vpn side is not using pfsense as default gateway - then again your not going to be able to talk..
So I notice you point dns to 192.168.1.1, but in your address bar your access pfsense at 192.168.1.254.. So this box your trying to talk to at 192.168.1.1 in your traceroute - is his default gateway off 192.168.1.0/24 the pfsense box at 192.168.1.254?
What is this 192.168.1.1 box? What is his default gateway?
Look
my remote network (my office) 192.168.1.0/24
DNS,DHCP server 192.168.1.1
Default gateway 192.168.1.254 (pfsense box)Tunnel network (as you saw before) 192.168.1.200.0/24
my local network (my house) 192.168.10.0/24
DNS,DHCP server 192.168.10.1
Default gateway 192.168.10.1 (a gateway , there is no a pfsense box)with that settings should be able to see all devices on the remote network ? (because i will try them tonight )
thank you
-
Yes there should be no reason why you can not access stuff on the remote network, unless they are running host firewalls?
If youh have problems, please show your connection info and route print. And traceroute
-
Yes there should be no reason why you can not access stuff on the remote network, unless they are running host firewalls?
If youh have problems, please show your connection info and route print. And traceroute
Okay as i told you i will try them…thank you man .
-
Hi…also nothing happen and as usual i could ping only pfsense box and i could't see any device on the remote network...(i forget to what you said to me about print route command but tonight i will post it here)
but i want to ask you : what rules need i to and on which will i apply them (WAN,LAN,vpnServer) ?
thank you .