New to pfsense and issues already
-
Ok think I have managed to add whats required.
Is there a rule where I can allow all incoming traffic briefly as I am having a problem with 1 site and I want to prove its not pfsense?
When you say 'all incoming traffic', what do you mean? Do you mean allow all hosts on the internet or all ports from the hosts in your alias list?
If you are getting success from all the remote points except one, then that will indicate the forwarding is working correctly and the issue lies at the remote end of the one problem point. Before you start opening up your network to the world, I would be inclined to check the logs first. Search for the remote address of the problem site and see what rule is blocking it. This should give you a better idea of the cause of the problem without removing your security entirely. If you can't find an entry for the remote problem site then the issue will almost certainly be some rule or other blocking it at the other end.
-
Yes I mean open all ports and addresses
Yes I know this is not ideal and im aware of the dangers but I would like to have the option of allowing all addresses and ports through the firewall briefly
-
Just add a firewall rule to the WAN that allows everything. Any protocol, any source, any destination, any port.
You can disable it afterwards but leave it there in case you want to enable it again for future testing.Steve
-
What Stepehnw10 has said is pretty much it. But rather than give you instructions which would go against every professional bone in my body, maybe it would be better if you described the problem you're having with this one site? Instead of giving you advice which would leave your system open to a potentially devastating attack it would probably be far more constructive to help with the actual issue. Can you give details on what the difficulty is?
If you'd rather not go into it, then fine. But don't say I didn't warn you.
-
That's a good point. Whatever you do make sure you remove/disable the rule afterwards. ;)
A safer way to test if traffic is arriving from your suspect location would be to run a packet capture on WAN and thgen search it for the address.
There are also options to disable the firewall completely if you need to.
Steve
-
Even adding those rules it still appears there is 0 traffic reaching the LAN looking at the firewall log its shows traffic but its all being blocked still with so much down time think im going to have to abandon the use of PFsense as its just not user friendly
-
Before you throw in the towel, why not post a few more screen grabs? If you can take a shot of your NAT forwarding and firewall rules again, particularly the properties for your specific NAT rule you set up on Phil's instruction then that would help. The aliases you've set up for the remote sites and the destination ports would also help. Port forwarding really isn't that difficult under pfSense - certainly much easier than many other firewalls I've worked with.
I take it that you're unable to receive traffic from ANY of the remote sites? Is this right? Or is it just one or a few sites which aren't working?
-
Think it may be down to the local server maybe I haven't been clear my local server has 2 nics 1 to join my work domain this has its own static IP default gateway and DNS the other is to receive this traffic from the PF sense I have added a static IP of 10.1.1.11 to this nic to connect with the PFsense LAN thats on 10.1.1.10 but I have not added any DNS details is this correct?
-
Ok, that's a little different. What route is the local server using? In order to respond to port forwards via the firewall, the server must have it's default gateway set to the internal NIC of the pfSense.
You don't mention whether your server is a Windows or Unix machine. Assuming it's Windows, open up a command prompt and type 'route print'. The default gateway should show the pfsense IP as the default gateway out. If not, edit the network settings on the server and set the default gateway to 10.1.1.10 (your pfsense firewall). Then try seeing if your port forwards operate successfully.
-
Ok well its a windows machine what I would trying to achive would be to allow all traffic to get it working then lock it down with all the IP/Hostnames and ports once I have proven it works the problem is the software supports a multitude of different protocols meaning a number of ports both TCP and UDP
So one last shot of where I am at I have removed all Aliases at this time.
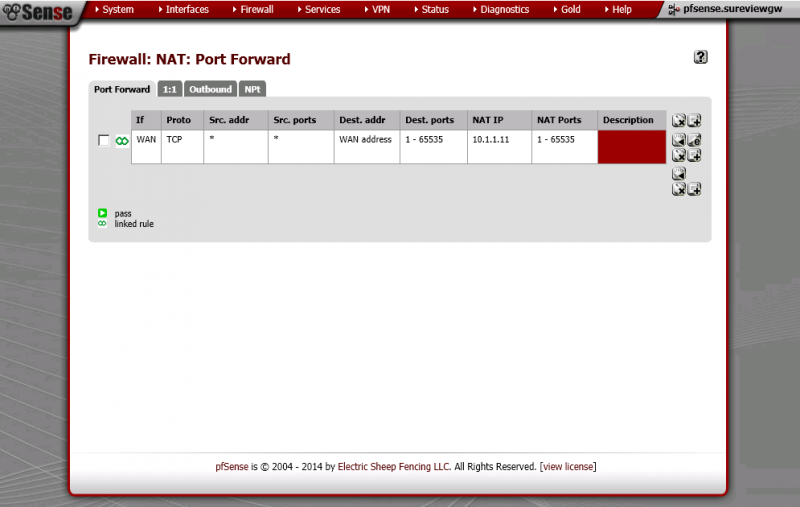
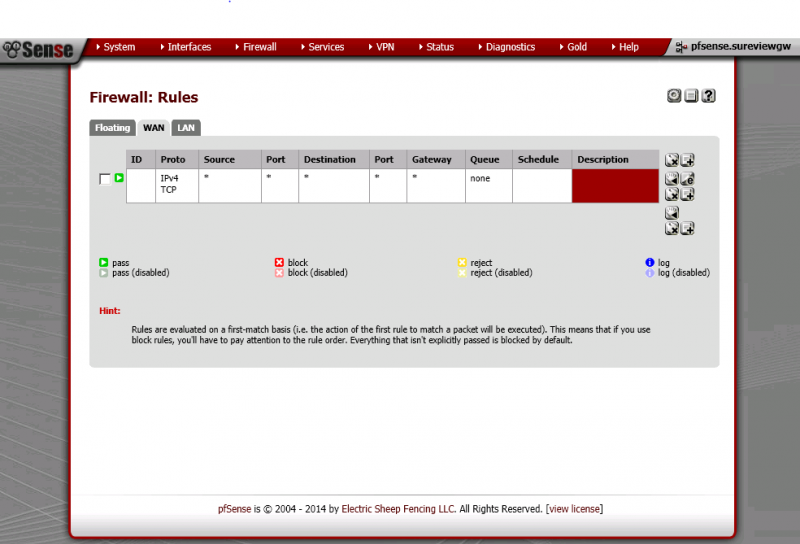
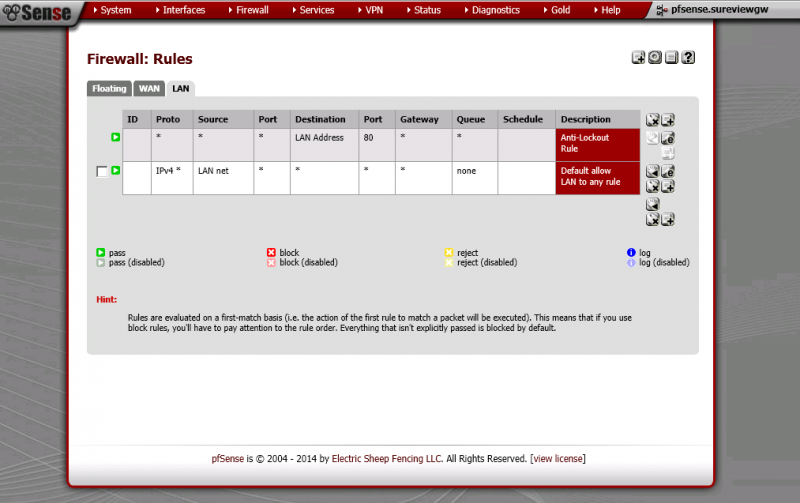
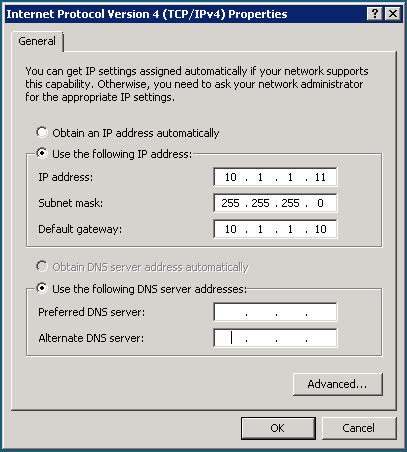
not to sure what else you would need to see
-
Your screen grab is showing the LAN rules, not the WAN rules. The WAN rules will have the port forwarding rules you created on Phil's instruction.
In short, can you post screen grabs of the following:
NAT rules (Firewall/Nat + Port foward tab)
Firewall rules (Firewall/Rules + WAN tab)
IP Aliases (Firewall/Aliases + IP tab)
Port Aliases (Firewall/Aliases + Port tab) -
Ok - some more thoughts. Can you do a screen grab of the firewall logs (Status/System Logs + Firewall tab)? If anything is trying to access the server it should show up on these logs. Can you initiate an attempted connection from one of your remote sites and take a snapshot of this log page?
Also, are you running any kind of firewall locally on your server? If you are then this may be what's keeping the traffic from reaching the server.
-
You hit the nail on the head massive oversight on my behalf blocked by the windows firewall disabled that and all of a sudden a mass of traffic and alarms 8)
-
As ever, it's always the simplest things that prove to be the problem. Glad to hear it's sorted. Now please disable that 'allow all' rule before you find your server is being used to peddle cheap Russian viagra.
-
I have disabled the rule and spent some time fine tuning all appears to be working as it should now
Just want to thank you to muswellillbilly and anyone else who has aided me these last couple of days I couldn't of done it with out you
-
Yes, he pulled you back from the brink of giving up. ;)
I hope you have a less frustrating time with pfSense in future, have fun!Steve
-
thanks Steve makes a lot more sense now its working as I was beginning to think it was my ability of understanding and following instruction but now I have a much better understanding and proving to be a rather powerful tool three cheers for the community!