Getting only 80mbps on a 175mbps WAN connection
-
How does the home hub physically talk to the STBs? Are they Ethernet? Wi-Fi? MoCA?
I'm starting to get a little lost. Maybe it's time for a summary drawing populated with what we know.
ONT ethernet (outside) interface:
TAGGED VLAN 35 INTERNET
TAGGED VLAN 36 IPTV (Must be .1p >=4 ??)HOME HUB ethernet (inside) interface:
UNTAGGED INTERNET ??
TAGGED VLAN 36 IPTV ??Do the STBs use the same VLAN as your general internet or are there three? IPTV, STB internet, and general internet?
Are we talking about this with VLAN 36 instead of 34 for IPTV?

-
Yup, we're talking that.
I have the Home Hub 2000 (made by Sagemcom) instead of the Actiontec.
From that diagram, it looks like the STBs don't use the same LAN as the rest of the network, but I remember my STB did have an IP address in the same subnet as my LAN.
I'm going to reconnect the Home Hub 2000 just to confirm that, but I'm pretty sure that's how it worked.
Is there any way to combine two VLANs together? Basically the normal LAN which gets NATed, but then I want to add the VLAN 36 from the ONT onto that. That might be a stupid question, I'm not a network expert by any means. :)
-
Is there any way to combine two VLANs together?
Combine them into what? Ethernet? Wi-Fi? MoCA? How are the STBs physically connected (for the third time?)
-
Is there any way to combine two VLANs together?
Combine them into what? Ehternet? Wi-Fi? MoCA? How are the STBs physically connected (for the third time?)
I'm sorry, you're right, I did keep asking that.
They (I actually only have one) are connected by Ethernet.
-
Two vlans are combined together on ethernet all the time with VLAN tags. It is possible for one and only one VLAN on the port to be untagged. If the pfSense interface in question was re2, you would:
Create VLAN X on re2
Assign the untagged VLAN to re2
Assign the tagged VLAN to re2_vlanXBut without knowing exactly what needs to be done it's all just a lot of guessing.
Do we know what VLAN tags are being used by the Home Hub to talk to the STBs on the private side?
Do you have a managed switch or not?
-
In one of those posts I linked to it implied that the supplied router simply bridged VLAN36 onto the LAN.
Steve
-
Two vlans are combined together on ethernet all the time with VLAN tags. It is possible for one and only one VLAN on the port to be untagged. If the pfSense interface in question was re2, you would:
Create VLAN X on re2
Assign the untagged VLAN to re2
Assign the tagged VLAN to re2_vlanXBut without knowing exactly what needs to be done it's all just a lot of guessing.
Do we know what VLAN tags are being used by the Home Hub to talk to the STBs on the private side?
Do you have a managed switch or not?
You are awesome for continuing to help me, thank you!!
So, my LAN port is re1 (that's the one where NATing occurs and gets the rest of my network out to the internet).
I have extracted VLAN 36 from re0 which is connected to the ONT, just as I have extracted VLAN 35 from re0 in order to get general internet access which works great.
So currently:
physically:
ONT (port 1) -> pfSense (re0)
pfSense (re1) -> 24-port switch (port 1)
24-port switch (port 2) -> desktop
24-port switch (port 3) -> Bell STBVLAN:
ONT (VLAN 35) -> pfSense (re0_vlan35)
ONT (VLAN 36) -> pfSense (re0_vlan36)re0_vlan35 is doing PPPoE to get a public IP and that works great. I then NAT re1 to re0_vlan35
re0_vlan36 is doing DHCP to get a private IP from Bell's data center and that is working too.I just don't know how to get that VLAN onto the re1 physical LAN and have it propagate through my switch. I also have to do QoS on it and make sure it is set to 4 somewhere…
Yes I have a fully managed switch which is currently operating in "dumb" mode except for two ports which are LAGged for a Lenovo NAS.
I don't know which VLAN tags are being sent out on the LAN by the Home Hub 2000 when it is set up as the router. I suppose I will have to connect it all together and do some packet capturing. I was just hoping to avoid that. :)
@Steve, that's exactly what I want to try. :)
-
Add a VLAN36 interface to re1.
Disable DHCP on re0_VLAN36, set it as type 'none'. The set top box needs to pull an IP from Bell not your firewall.
Make sure those sysctls are still set to remove filtering on bridge members.
Add a bridge that includes re0_VLAN36 and re1_VLAN36.Hope.
Steve
-
Add a VLAN36 interface to re1.
Disable DHCP on re0_VLAN36, set it as type 'none'. The set top box needs to pull an IP from Bell not your firewall.
Make sure those sysctls are still set to remove filtering on bridge members.
Add a bridge that includes re0_VLAN36 and re1_VLAN36.Hope.
Steve
Done (see attached). Fingers crossed. Restarting the STB now.

-
Question, where do I set the QoS to 4? On which interface?
The STB is still booting :P
–--
10 minutes later...
It's still booting, well, it's stuck on a screen that just says "Bell Fibe", so I have a feeling it might just sit here.
It was on before even though there was no signal, but I had turned it on when it did have a signal. Maybe if it doesn't get a signal, it just doesn't boot? That would be kinda weird...
I'll keep tinkering with it tomorrow, my girlfriend wants me to prove I exist. :P
The next morning....
So the STB sat at the "Bell Fibe" screen all night and didn't boot up fully into a menu. ARGH! That's pretty ridiculous. The nice thing about the STB system info page is it shows its IP address as well as whether or not IPTV is connected. I'm assuming IP address it gets from DHCP and IPTV on or off is determined by whether or not it can find VLAN 36.
I will go back to the drawing board today. :)
-
I only had a chance to try something now. Here's what I tried:
I plugged the ONT into an un-managed 1gigabit switch (port 1 – but port is irrelevant)
I plugged the WAN port of the pfSense box into the same gigabit switch (port 23)
I plugged the WAN port of the Home Hub 2000 into the same gigabit switch (port 24)
I told the Home Hub 2000 not to do internet (by putting in the wrong PPPoE password)Like this, everything works... both internet and TV.
So it begs the question, why isn't the bridge from VLAN 36 on the WAN port of the pfSense to VLAN 36 on the OPT1 port working?
I'm ok with using the Home Hub 2000 for TV service... I can live with that, but I just don't understand why the pfSense bridge isn't working.
Maybe I should "waste" three ports on my 24-port fully managed switch to do what the outside un-managed switch is doing?
I'm not sure how to make a network "segment" using my Netgear GS724T, but I imagine there must be a way...
OK so when I say TV is working perfectly, I mean, that I can watch TV.
But when I try to run apps which rely on an internet connection, it doesn't work... just another reason why I need to get this VLAN 36 bridged. ARGH!!!
The Home Hub 2000 is definitely doing DHCP to the Fibe service... I don't know what it does once it connects though. That is most probably why just bridging VLAN 36 isn't working, I really need to do DHCP for some reason. Although my set top box gets a private IP on the same network as any other internet device connecting to the Home Hub...
I guess I really need to talk to a Bell network expert to know what's going on in there.

-
It could well be the QoS thing. Could also be IP options not getting through.
I think i would be doing some packet sniffing at this point.Steve
-
So I got a chance to email a senior Bell technician who is helping me out on the case… here was his short but sweet reply (see attached).
I'm not completely sure what he means by it...
I'm thinking the 10.0.0.0/16 is wrong, it should likely be 10.0.0.0/8. Problem is I use 10.50.0.0/16 as my LAN, so this might be an issue. But I got DHCP working on the VLAN36 of WAN side, and I get an IP of 10.240.0.0, so I could maybe just route that. I attached a screenshot of the route I made. Not sure if that's right.
Also, I don't know if I need to bridge VLAN36 back to the LAN interface... I've asked him, don't know if he'll reply. :)
Edit: Would someone be able to tell me where I'm supposed to set the QoS settings?

-
I wouldn't ask him what to do, I would ask him for the specifics of what his gear expects in an equipment-agnostic fashion. Then we just make pfSense do that.
Are you still guessing that you need QoS or do you know that you need QoS?
-
I wouldn't ask him what to do, I would ask him for the specifics of what his gear expects in an equipment-agnostic fashion. Then we just make pfSense do that.
Are you still guessing that you need QoS or do you know that you need QoS?
Yes, he's totally giving me equipment agnostic info, which is awesome. He's telling me what to set up etc…
It turns out the current issue is an IGMP issue. I need to proxy 224.0.0.0/4 to the IPTV LAN. That's what I'm working on now. I can't quite get it though. I might have my settings wrong.
I manage to get 5 seconds of TV (which is sent TCP unicase), but then when it kicks into IGMP multicast mode, I lose TV. :( There are other articles about this on the net, but none that applies specifically to Bell Fibe.
I'm super close though!
-
Yes I have a fully managed switch which is currently operating in "dumb" mode except for two ports which are LAGged for a Lenovo NAS.
Sorry if I chime in here … that was a Netgear switch, right? Which model?
For another thread I read just yesterday that some of the ProSafe GS724 or 726 or so switches have problems with LAGG in combination with Jumboframes enabled.
Keep it in the back of your mind just in case...PS: This has nothing to do with the fact that Derelict and I both dislike Netgear (ProSafe) switches from own experiences. We don't even know each other...
-
So I got everything working perfectly!
The key component at the end was properly configuring the IGMP proxy. These are the IGMP proxy settings that worked finally:
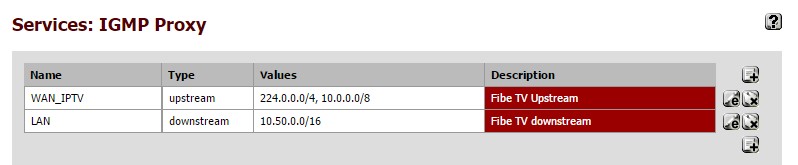
I will make a post with all the settings necessary soon. For now, I'm super happy to have bypassed that Bell router, and that everything CAN work with pfSense!
Sorry if I chime in here … that was a Netgear switch, right? Which model?
For another thread I read just yesterday that some of the ProSafe GS724 or 726 or so switches have problems with LAGG in combination with Jumboframes enabled.
Keep it in the back of your mind just in case...Yup it's a GS724T. In the end, I didn't have to fiddle with any settings on the switch at all.
-
So you can confirm that IGMP proxy is working correctly in pfSense 2.2?
Someone was having a problem with it but as it turned out he uses 2.1.5 -
So you can confirm that IGMP proxy is working correctly in pfSense 2.2?
Someone was having a problem with it but as it turned out he uses 2.1.5I can definitely confirm that for my application (IPTV on the Bell Fibe network in Quebec/Ontario), IGMP proxy is working correctly in pfSense, yes. :)
-
Awsome job. Persistence for the win! :D
No QoS requirement in the end then?
Steve