Two Phase 2 entries wont connect other two will
-
Out of the 5 phase 2 entries I have in IPsec, only 3 are connecting:
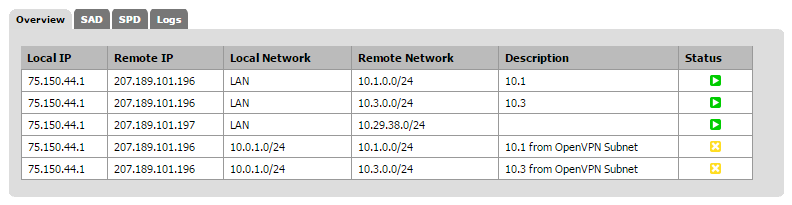
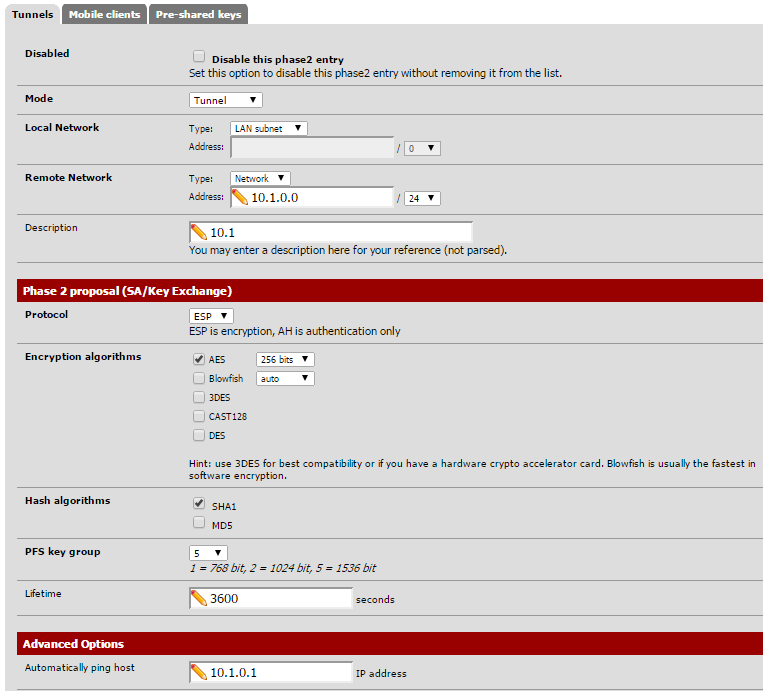
These are the settings of one of the working ones:
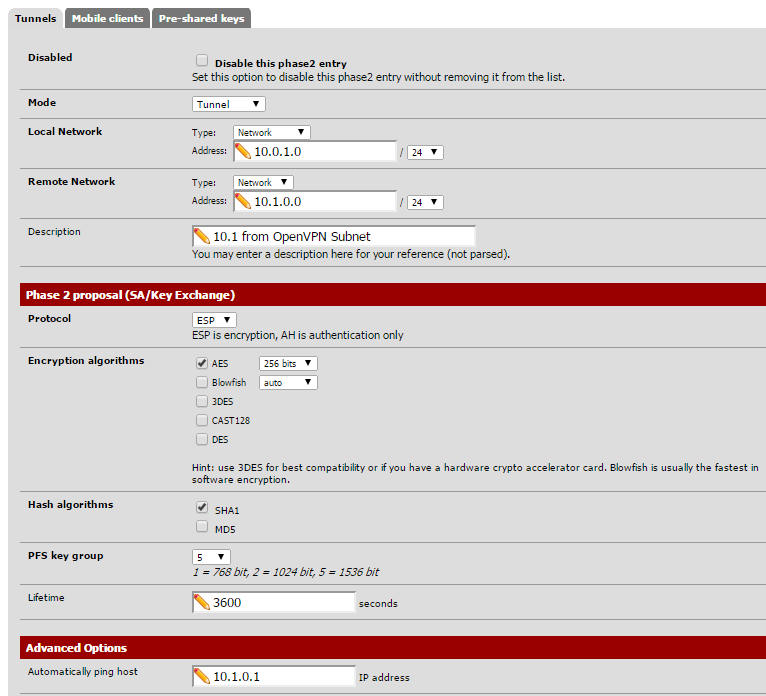
Here's one of the ones that doesn't work, setup exactly the same:
Any idea where I can start troubleshooting? Are there some logs I can look at that might provide more info?
-
Nevermind, found the problem. It was in the OpenVPN configuration settings.
-
Would you mind sharing what OpenVPN setting caused the IPSEC phase 2 connection to not connect? I'd like to know for the knowledge to keep in mind in case I run into something in the future - we have a similar setup.
Thanks!
-
I'm following thread to know how is OpenVPN will cause Ipsec phase 2 not working.
I have this issue as well.
-
I'm following thread to know how is OpenVPN will cause Ipsec phase 2 not working.
I have this issue as well.
I too would be intrigued to find out more. One of my tunnels consists of pfSense 2.1.5 <-> pfSense 2.2, one of the P2s is a supernetted range of VLANs, some of which are OpenVPNs (at the 2.1.5 end). This has been stable for 11 days.
2.2 end - 192.168.x.0/24
2.1.5 end - 10.x.0.0/16 + 192.168.x.0/24The 10.x is actually lots of 10.x.y.0/24. y=250,251,252 are OpenVPN tunnels.
IPSEC should not care what subnets or for what purpose or even if they exist locally.