Inter VLAN Routing - Internet Access
-
I have a Netgear GSM7248v2 L2 switch. I was searching for a L3 switch as I needed to stop all inter VLAN traffic from going through pfSense. 5TB backups and file transfers were killing the network. After some research I found that my switch infact can do VLAN routing. Found a netgear manual online and followed the steps and now have a good internal routed vlan environment.
My problem now is that only the first VLAN is able to browse the internet and the rest 3 VLANs can only browse if the gateway is set to the respective pfSense NIC instead of the switch IP. With this config the data is still routed through pfSense which kinda beats the purpose of routed VLANs.
Here is my setup.
Switch
LAN (VLAN 10) - 10.1.1.1
VoIP (VLAN 20) - 10.2.1.1
Video (VLAN 30) - 10.3.1.1
.. and so onThe above are IP configured with virtual ports on the switch. Devices on vlan 10 can ping and connect to vlan 20/30 and vice versa. They can all ping the virtual interfaces 10.1.1/1.2/1.3
on pfSense I have similar network with dedicated (no vlans) NICs for each network
LAN - 10.1.1.2
VoIP - 10.2.1.2
Video - 10.3.1.2
.. and so onNow with normal setup the DHCP on each network assigns the pfSense network interface as the default gateway. This is causing all the devices to route through pfSense to hop on to the other VLAN for file transfers. Tested it multiple times and still see traffic going through pfSense.
Online netgear documentation says to assign the routing vlan IP as the default gateway, which makes sense. But the moment I set the default gateway in DHCP to 10.1.1.1 or 10.2.1.1 for each network, I am unable to browse or route to the internet. I can't even ping the pfSense IP 10.1.1.2 from the other networks as data is not flowing through the VLAN to pfSense.I believe its a simple routing fix I need to do in pfSense to show it the downstream router/switch IP (10.1.1.1/10.2.1.1….) for directing WAN traffic to the specific network since I can ping from pfSense to the devices in all the subnets as well. I need to change the default gateway for each subnet/network their respective switch IP 10.1.1.1/10.2.1.1....
Could someone please provide step by step direction on how to get this done in pfSense?
Example..
Video network.
IP 10.3.1.xx
Subnet 255.255.255.0
Gateway 10.3.1.1 (switch IP) (internet works when this is set to 10.3.1.2)
DNS 10.3.1.2 (pfSense DNS) -
What is your transit network? If you going to connect pfsense to a downstream router, ie your L3 switch doing routing.. Then pfsense would be connected via a transit network.. Its firewall rules for internet on this transit interface would have to allow your downstream networks, and your outbound nat has to be adjusted to outbound nat your downstream networks.
I am confused about your vlan IPs given.. Why are you changing the second octet if your using a /24 mask.. Why would you networks not be 10.1.1, 10.1.2, 10.1.3 ??
Here is how you would do pfsense with a downstream router.
" rest 3 VLANs can only browse if the gateway is set to the respective pfSense NIC instead of the switch IP. "
Huh?? Are you sure you have actually created vlans on your switch and routing them, vs just creating 1 big layer 3 network and using different IP ranges??

-
Thanks for the detailed diagram. Much appreciated. I guess I am a bit confused on the implementation. The network addresses have been this way for many years and I suppose I need to change them now.
At the moment I think my problem is that I am using netgear document which does not use a transit ip but uses the first subnet as the primary and piggy backs the rest. But the implementation is flawed as it used just netgear gateway for static routes within the same 192.168.x.x network.
Now my question is, I have 4 separate NICs (for lan, voip, video and home network) on pfsense for which pfsense did all the routing.if I move all the 4 networks to the L3 switch, should the pfsense now have just one transit network to connect to the switch? And I can delete the networks from pfsense?
Secondly the transit ip on the netgear switch is an ip of the physical switch..correct? And not a vlan routed ip?
-
Yes you would only have 1 transit network.. Pfsense does not need interfaces in network its not routing/firewalling for. You should delete these networks off pfsense since you are moving them to your downstream router.
No this transit network does not need to be vlan tagged, unless your connecting this transit across multiple switches?? Which I doubt.
"Secondly the transit ip on the netgear switch is an ip of the physical switch..correct? And not a vlan routed ip?"
As to physical IP? You mean management IP, or the IP you have assigned to vlan 1? What IP you use for management has little bearing on anything, normally you do not use the transit IP but sure you could use this to access the switch if you wanted. It does not need to be tagged, sure it could be your management IP. The only thing the switch needs to know is that IP of pfsense on this transit network is its gateway..
Are you using vlan 1 on your switch? For management or any other ports? This could be your transit, or you could create another vlan on the switch and use that vlan as your transit. Just no reason to tag it, unless you want to create a vlan on pfsense, etc.
What are you looking at from netgear for doing intervlan routing? Can you provide link and will take a look..
-
Yes with physical I meant the management ip. Typically I set it at a 192.168.x.x address which is on vlan 1. I do not use the management vlan.
For lan I have vlan 10, voip I have vlan 20 and so on.
So to start, I would first create a 172.16.x.x single vlan for transit which will be the only physical connection to pfsense. Since this is a vlan I would need to untag it on the switch port connecting it to pfsense transit port on the same vlan network.
Next I will re-create my lan, voip..etc "routing vlans" with 10.1.1.x, 10.1.2.x etc. And for the default route next hop I will put the single pfsense 172.16.x.x ip.
Should the transit vlan be in the routing vlan or single vlan is fine?
I will send the netgear doc link shortly.
-
"Should the transit vlan be in the routing vlan or single vlan is fine?"
I think your not grasping the concept of what a transit network is actually? Routing vlans? You mean your vlans off your downstream switch - why are you calling them routing vlans? Been in the biz for 30+ years, that is not a actual term ;) You mean the downstream networks?
-
Ha! Netgear has them as routing vlans. Just using their terms. :D There is a separate tab in the switch to create routing vlans and has a "van routing wizard". Though in the end you can make changes to all vlans in the main vlan configuration page.
Check this …http://kb.netgear.com/24709/How-do-I-use-the-VLAN-Routing-Wizard-on-a-smart-switch?cid=wmt_netgear_organic
And this is the routing vlan doc from netgear I referred to earlier.
http://kb.netgear.com/30818/How-to-configure-routing-VLANs-on-a-NETGEAR-managed-switch-with-shared-internet-access?cid=wmt_netgear_organic
There is no mention of a transit ip. And in the end they use a netgear gateway for static routing.
OK so I will do the below.
Vlan 10 - 10.1.1.1 - ip on virtual port for lan (it's usually 4/1 on my switch)
Vlan 20 - 10.1.2.1 - ip on virtual port for voip (4/2)
Vlan 30 - 10.1.3.1 - ip on virtual port for video (4/3)
Vlan 40 - 10.1.4.1 - ip on virtual port for home (4/4)Vlan 100 - 172.16.1.1 - transit ip to pfsense (4/5)
172.16.1.2 - transit ip (single lan ip) on pfsenseLet me know if this is right.
-
Wow – what a shitty document..
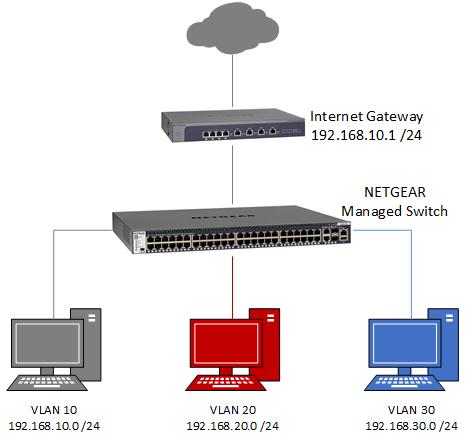
So they create asymmetrical routing condition… Since you have hosts on what is your transit network ;)
So they show to set the gateway of clients to be the switches IP in their "routing vlan" 192.168.10.254.. So I have a client that is on this 192.168.10 say .100, where does it send its traffic to get to the internet.. its gateway is .254 the switch, who then sends it on in the same network to the router at internet gateway at .1. Now when that traffic gets back, where does it send it? To the client directly, why would it send it to .254? So now you have asymmetrical condition..
Yeah wouldn't in a million years set it up like that.. If your going to put hosts on your transit, then you have to host route on them or you end up with hairpins and asymmetrical conditions. And with a firewall in play as well that leads to trouble with out of state traffic..
-
This is the very reason I opened this thread.
OK so now did go ahead and wiped all vlans and created a new set of vlans as per my post above.
The devices within vlan 10 to 40 and 100 can ping each other and I can ping the virtual ips of each vlan.. like 10.1.1.1 and 10.1.2.1..
Now I have a new issue. Transit ip on switch 172.16.0.1 can't ping back to pfsense ip 172.16.0.2. From pfsense I can ping the switch transit ip 172.16.0.1 successfully.
-
So look at your firewall rules.
Where traffic needs to exit the firewall there has to be a route telling it where to go. (Policy route, connected interface, static route, default route.)
Where traffic needs to enter the firewall there has to be a rule allowing it to enter.
-
Tried that already.
Here is my pfsense LAN (transit) firewall rule
IPv4 * 172.16.0.1 * 172.160.0.2 * * none Switch to Firewall
IPv4 * LAN net * * * * none Default allow LAN to any ruleIPv6 * LAN net * * * * none Default allow LAN IPv6 to any rule
I have the LAN (transit) cable coming from pfSense on port 44 on the swtich.
On the switch, I have vlan 100 with port 44 untagged. If I tag it I can't ping from pfSense. No other port is enabled on that vlan. The switch transit ip is 172.16.0.1 and pfSense is 172.16.0.2.
I even tried assigning an IP directly to the port in IP Routing tab on the switch. Same results, can ping from pfSense but not from the clients inside the vlans.
-
Looks like a typo here:
IPv4 * 172.16.0.1 * 172.160.0.2 * * none Switch to Firewall
16 != 160
-
Just a typo .. it was 30 past midnight 8)
It's 172.16 on pfsense.
-
So all those rules allow is switch to talk to pfsense.. Doesn't allow any of your other traffic..
You have all your downstream networks, your transit interface rule has to allow for that. I went over that in 1st post.. Your switch is not NATTING to its IP in the tranist..
Also its much easier to post screenshot of your rules..
-
OK.. finally some progress. I connected to the transit network just to get my head around it and saw that I could connect to both 172.16.0.1 (switch) and .0.2 (pfsense) and the internet was working. But I of course couldn't ping 10.1.1.0/24 network on the switch. So I added a new gateway on pfSense for the LAN 172.16.0.1 and in static routing I pointed the network 10.1.1.0/24 to it. That got me reach to 10.1.1.0/24 netowork on the swtich. I then added a static route on pfSense for destination 10.1.1.0/24 use the gateway 172.16.0.1. That got my 10.1.1.0/24 network to start pinging the pfSense and the outside world.. 8.8.8.8
-
your outbound nat has to be adjusted to outbound nat your downstream networks.
I am on the default "Automatic outbound NAT rule generation." and my internal switch network is pointed to pfSense LAN (transit ip) 172.16.0.2 for DNS and its working. Am I doing this right? If not, then could you please guide me on what the setting need to be?
-
Dude post up your outbound nat.. How is psense going to know to nat these downstream networks when it doesn't have them directly connected..
You don't need to create multiple routes for all your /24's on pfsense - just use a summary route. They are all in the 10 space, so 1 route to 10/8 gets you to your switch. On your switch pfsense is internet, so that is the default route..
-
I didn't even touch the outbound nat. I think it took the static routes and updated the mappings. All I did is create static route for each subnet and pointed the transit ip as the gateway.
Here is my automatic outbound nat.
Interface Source Source Port Destination Destination Port NAT Address NAT Port Static Port Description
WAN 127.0.0.0/8 10.1.1.0/24 10.1.2.0/24 10.1.3.0/24 10.1.4.0/24 172.16.0.0/30 * * 500 WAN address * Auto created rule for ISAKMP
WAN 127.0.0.0/8 10.1.1.0/24 10.1.2.0/24 10.1.3.0/24 10.1.4.0/24 172.16.0.0/30 * * * WAN address * Auto created rule -
I then added a static route on pfSense for destination 10.1.1.0/24 use the gateway 172.16.0.1. That got my 10.1.1.0/24 network to start pinging the pfSense and the outside world.. 8.8.8.8
So what's still not working?
-
The comment by johnpoz "your outbound nat has to be adjusted to outbound nat your downstream networks." got me thinking if I may be missing something that needs to be in place not to break the routes and if its not working the way it should.
Hey as long as I don't have to manually change the settings I am a happy camper ;D
Now if there was a way just to get pfSense DHCP relayed to the downstream networks it would had been icing on cake. I think I will move pfSense back to vmware and install a dhcp vm on the same hardware. With all my vlan traffic now handled by the switch I barely see any CPU usage on pfSense.