DNS leaks my host IP address??
-
I configured Squid proxy for transparent mode, set my DNS to those of my VPN service provider, then tested for IP leaks here:
https://ipleak.net/
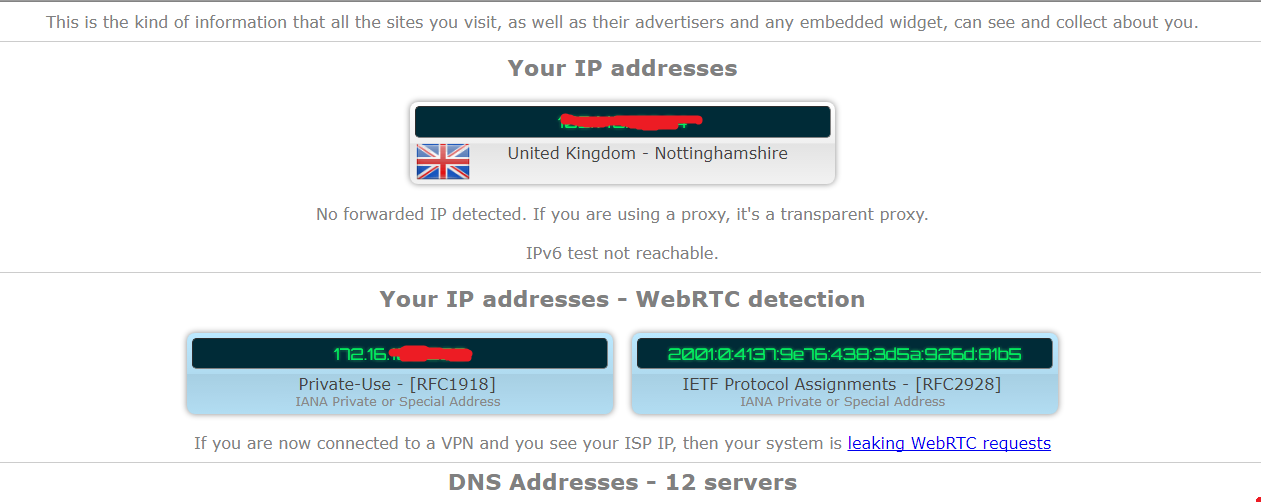
Result as attached, my host IP is leaked.
Is this normal for pfsense as I was just expecting the internet IP to be visible.? How is my host ip being passed through in transparent mode?Help please.

 -
Same thing here as well. :o
-
if your using unbound as resolver, then yeah its going to show your IP. Since its resolving not forwarding.
-
Read further down the page at ipleak.net
What is a "WebRTC leaks"?
WebRTC implement STUN (Session Traversal Utilities for Nat), a protocol that allows to discover the public IP address. To disable it:
Mozilla Firefox: Type "about:config” in the address bar. Scroll down to “media.peerconnection.enabled”, double click to set it to false.
Google Chrome: Install Google official extension WebRTC Network Limiter.
Opera: Type "about:config" in the address bar or go to "Settings". Select "Show advanced settings" and click on "Privacy & security". At "WebRTC" mark select "Disable non-proxied UDP". -
if your using unbound as resolver…......
.Thanks, Yes I am, but isn't that always the case using pfsense cached DNS and site blocking? I plugged in my ISP technicolor router and it's secure, well it shows the public IP which I'd expect, but it doesn't show the client IPs on the local network. gjaltemba - I think you are saying I can block IP leaks in the browser? If host IPs leak from pfsense, surely that means they are still discoverable, whatever is done inside client browsers and you are relying on the browser to stop IP addresses being forwarded? I'm trying to get pfsense to do most of the privacy, security, ad blocking and site tracker blocking presently done on each network client PC. Should I be cautious now to test everything and not make assumptions it is being done inside pfsense? I didn't want to start Wireshark packet capturing to prove integrity, but I might have to.
I had a similar problem proving that SSL MITM filtering was actually working so clamAV could filter on HTTPS/SSL sites - which is most sites now.
My Firefox media.peerconnection is already set to false. and since I tried the same browser config with a hardware router and don't get the leak, it must be due to the pfsense setup?
According to the doc: "Unbound provides DNS Rebinding protection by stripping any answers that contain RFC1918 addresses."
Not to get confused, abdul201588 posted his result which didn't show his local RFC1918 address, but mine did. If I'm behind a VPN I accept the public (VPN assigned) IP is visible, but don't expect my local private addresses to be.
-
I didn't look to what IP you were sending, since you blocked out part of it - figured it was public.. But its rfc1918.. So that is your browser via webrtc as gjaltemba stated..
-
Gee… When I go there, it shows 172.16.1.10. Better block that. It's supposed to be secret! ;)
Seriously, if it's showing RFC1918 addresses, you've got nothing to worry about.
-
Oh my gawd they know my 192.168.0.100 address… They are going to hack me for sure now ;) heheheh
-
Oh my gawd they know my 192.168.0.100 address… They are going to hack me for sure now ;) heheheh
Quick! Change your address to 127.0.0.1! This will protect you!
My Firefox media.peerconnection is already set to false. and since I tried the same browser config with a hardware router and don't get the leak, it must be due to the pfsense setup?
Don't ever believe some software settings. Take Wireshark/Message Analyzer and see the real traffic your PC generate.
it must be due to the pfsense setup
Written above applies to pfSense too, BUT:
Unbound has nothing to do with WebRTC, this is entirely different protocol which doesn't implemented in Unbound in any way.
Thats like supposing what your microwave oven has ability to wash your clothes. -
Here I turned it off in firefox - see attached pic. Ran test, shows my local IP. Changed setting in firefox to false, refreshed - local IP gone.
As stated this really has nothing to do with pfsense or unbound. A webrtc leak is your browser just answering what was asked of it, etc. Blocking it via firewall rule not going to work. Without breaking the internet for you pretty much ;)
If you don't trust your browser to do it, then you would need to proxy your connection with a proxy that could prevent it.

-
Read further down the page at ipleak.net
What is a "WebRTC leaks"?
WebRTC implement STUN (Session Traversal Utilities for Nat), a protocol that allows to discover the public IP address. To disable it:
This is why we should move to IPv6 as soon as possible, to avoid the hacks such as NAT and STUN that continued use of IPv4 requires. As long as IPv4 is in use, the Internet will be broken.
-
So that statement is going to bring in our fav nat is still needed guy in ;) So I am just going to stay quiet, wouldn't want to be accused of trolling again ;) hehehe
-
So that statement is going to bring in our fav nat is still needed guy in ;) So I am just going to stay quiet, wouldn't want to be accused of trolling again ;) hehehe
It's not just him. There are plenty of people, including a couple of my friends who think similar. With one friend, I can attribute it to ignorance, but the other should know better. They can't seem shake the idea that adding hacks on top of hacks to an already inadequate system is better than moving to a new system that's already taking a significant amount of traffic. I've often heard that all you have to do is change X in IPv4 to fix some problem. Well, instead of fixing and patching something that's long been broken, why not just toss it and move onto something that's much better?
-
I started this thread when I asked why pfsense with Squid proxy might be leaking my IP address. I'm slowly building up a set of web urls to test what I think my pfsense box does and finding out it isn't what I might expect. The following website told me I was on a proxy server and uses the via, Forwarded, X forwarded-For or client -ip headers to determine that.
In my case my local private IP from DHCP was exposed, just as I'd posted. With information from the proxy test I disabled VIA Header and turned off x-forwarded header Mode (Default on) but then set it to transparent. The webcheck confirms my local IP isn't in the packets and with X-Forwarded Header Mode set to transparent I'm not detected as on a proxy. I'm a beginner so I don't know yet what other consequences are, but I'm not leaking my private IP any more.
If you have Squid proxy enabled, try the link and see what your pfsense config is telling everybody:
http://www.lagado.com/proxy-test
-
You have nothing to worry about, if it's leaking an RFC1918 address, which you would be using behind NAT. There is nothing to tie that address to you. It could also be used by gazillions of others.
-
Thanks, That's re-assuring. Still its nice to discover what a remote site can tell you about your proxy and what different Squid proxy settings can reveal.
There's a lot of discussion at the moment about media streaming services blocking VPN providers, which is why I'm interested in what 'goes out'. The consensus seems to be that despite geolocation being correct, service providers are being blocked by their IP addresses. This didn't seem true when I tested. OpenVPN on pfsense is detected as out of region, but my VPN service provider Windows client app also using openVPN isn't detected. I'm researching VPN tunneling and suspect their client app establishes dynamic tunnel ports which change with each connection.
For now my immediate problem is working out how to bypass pfsense openVPN selectively so it remains permanently enabled for everything except those sites. Sounds simple, but I'm not finding it so. There's plenty written to use static IP for clients on pfsense and filter those for specific sites to pass direct to the WAN. But this isn't practical when client IPs are from DHCP and can be portable devices over wifi. In Windows VPN client setup there are commands for 'deny all with IP exceptions' and the complement 'accept all with IP exceptions'. So far I've only found OpenVPN 'route-nopull', not its complement.
-
"But this isn't practical when client IPs are from DHCP and can be portable devices over wifi"
Huh?? You set a reservation for the device based upon its mac, now it always gets the IP you want it to have. You then create rules so it either goes out the vpn or not, etc.
-
Easiest way to resolving leak of Private IP is by setting X-Forwarded VIA Header Mode to "off". Located Proxy Server: General Settings/ General tab. Problem Solved.