Can't access DMZ bridge public IP's internally
-
Hi.
I'm setting up a server rack for a friend on AT&T Small Business with a /25 block on a Cisco SG300-52 switch.
If you have any experience with AT&T, you'll know that their modem is probably the biggest piece of crap on the planet and doesn't have a real bridge mode.
What it does have is an IP Passthrough mode that lets me assign the primary WAN IP straight to pfSense.
He has a pretty nice switch that is already pretty overkill for >10 servers on a rack, so for now I'd like to bridge WAN and in this case VLAN5 to create a DMZ interface for all of his servers, and a couple other VLAN's for internal network, guest network, etc.
I setup the IP passthrough, created my WAN/VLAN5 bridge, created allow-all firewall rules across the board for test purposes, and for testing purposes; only configured his cPanel server to start with the IP's.
Externally, they are all accessible, routed properly, the nameservers and 1 test domain all work as intended, etc.
Internally, when trying to access the public IP on a machine that isn't inside the DMZ– I can't connect whatsoever. I'm not finding anything in Firewall logs and the only firewall on the fresh CentOS 7.3/cPanel install is CSF and it's disabled.
I tried adding Virtual IP's for his /25 block as both Proxy ARP and Other-- neither really make a difference and it doesn't seem that I need that to configure the IP's for the servers on the bridge.
For the CentOS 7.3/cPanel server-- I configured 14 IP's to it and they all work perfectly externally, such as my phone-- but nothing internally.
I've tried changing outbound NAT rules around, enabling/disabling every Advanced -> Firewall NAT reflection checkbox, adding a static route for my IP's, and pretty much everything else I could find on Google.
The only thing I think I may have done wrong is configuring the Bridge? Most of the example setups I see are to setup pfSense entirely as a passthrough filter-- it seems the VLAN solution is more-so frowned upon but with him already having a pretty nice switch, I'd really like to avoid doing another type of configuration. I've tried toggling net.link.bridge.pfil_bridge/member around a bit but it doesn't seem to make a difference. With how much it's mentioned when Googling, it makes me question my configuration even more.
Here's some basic screenshots of my configuration to hopefully show my mistakes more clearly :) -- I put it in an imgur album so the random sizes don't make my post even more of an eyesore.
http://imgur.com/a/aQvfM
Thanks in advance for any help on this.
-
https://doc.pfsense.org/index.php/Why_can%27t_I_access_forwarded_ports_on_my_WAN_IP_from_my_LAN/OPTx_networks
-
https://doc.pfsense.org/index.php/Why_can%27t_I_access_forwarded_ports_on_my_WAN_IP_from_my_LAN/OPTx_networks
I should've included that page in my original post– would this be relevant considering the devices in question are on the bridge? I've tried all the NAT reflection stuff in method 1 but as far as method 2 goes, I don't have an internal IP for the servers in my bridge and my modem assigns the external static IP configured on the server directly (thus doesn't give it an internal IP via DHCP)
Only way I could really get an internal IP would be to give my Bridge an internal static range and setup DHCP but I can't imagine that'd be sane nor work.
Thank you for taking the time to reply.
-
It would be up to the bridge to reflect that then. Probably can't help.
-
It would be up to the bridge to reflect that then. Probably can't help.
Thanks anyway. If anyone else has any ideas or input it'd be greatly appreciated.
-
Still banging my head against the wall on this one. :-[
-
Like I said, it probably has to be done upstream at the device that actually has control of those addresses.
Maybe I am misunderstanding you. A diagram might help.
Split DNS too. NAT reflection is hacky.
-
Like I said, it probably has to be done upstream at the device that actually has control of those addresses.
Maybe I am misunderstanding you. A diagram might help.
Split DNS too. NAT reflection is hacky.
There's not much I can really do upstream at the device. But, if I WiFi straight to the crappy AT&T Modem, I can access everything just fine. It's only when my Laptop for example is running through LAN on pfSense that I can't ping those IP's.
You keep bringing up Split DNS– am I missing something? How am I supposed to do Split DNS if the servers are assigned external IP's straight from WAN due to the bridge and a static configuration? The entire point of the bridge is to bypass NAT on my servers.
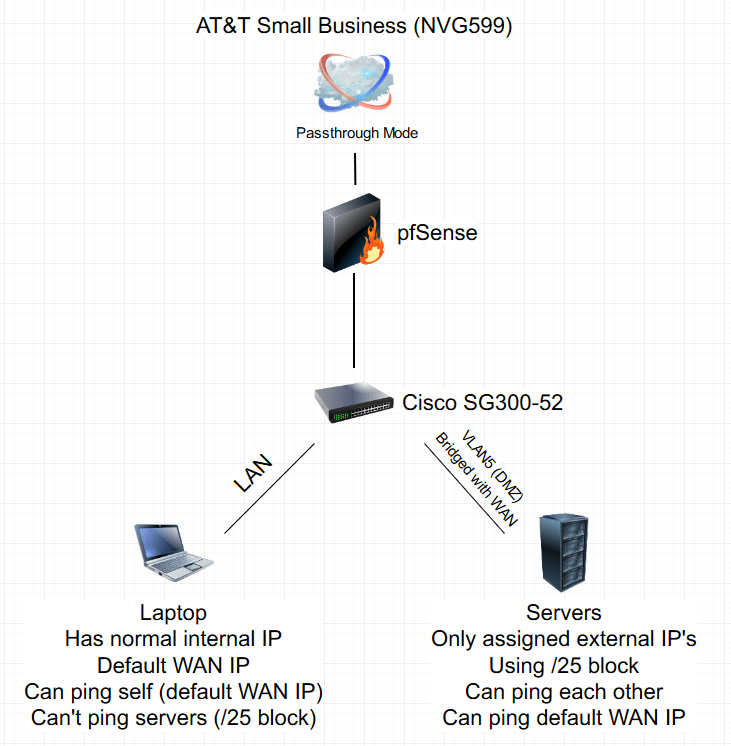
Here's my masterpiece of a diagram. It's all pretty straight forward, really.
-
Couple ports on the Cisco switch are Untagged on VLAN5
-
Uplink to pfSense is Tagged
-
VLAN5 is bridged to WAN to create a 'DMZ'
-
Modem assigns the server IP's in the /25 block directly due to bridge & each server having everything configured static
-
Servers are not running a firewall nor any iptables whatsoever
-
pfSense Firewall is allow all'd across the board
-
I've tried every NAT reflection checkbox, dropdown menu, etc. combination possible: nothing.
-
LAN gets assigned normal internal IP's via DHCP and uses the default WAN IP that is passthrough'd to pfSense with the NVG599
-
The servers full /25 block if routed is perfectly accessible from the outside world, but not when trying to ping it on a machine connected to the internet through pfSense and not on VLAN5
-
If I WiFi straight to the AT&T modem, it's accessible from there as well. This only occurs on LAN via pfSense– despite the internet working perfectly fine on LAN devices otherwise
Please let me know if I can provide any more details.
Thanks in advance for a reply.
-
-
Yeah, pfSense won't be able to do NAT reflection there. Nor should it be necessary if those hosts are really bridged with WAN.
Check your rules on the bridge members and the bridge itself.
-
Well, I never got my Bridge to work, but I ended up not needing a bridge at all.
I was able to simply assign the last usable IP of my /25 block to my VLAN5 interface and then use it as a gateway on all of my servers with manual outbound NAT.
Works great now!
I'm kinda blown away out of the dozens of hours of research I didn't find a single thread suggesting this implementation.
Thanks a lot to TandyUK in #pfsense on freenode.