Finished my first project
-
Hi Johnpoz, thanks for the reply and sorry for not including this detail before.
The motherboard is a Jetway JNF592-Q170, with 7 of the ports currently bridged until i learn if there is a better way. The board to the right is a separate switch, thats not linked to the router part in any way other than power.
Trev
-
Ah so to link the switch ports to an interface on the MB you need to use a patch cable between the ports.. So the switch board is just dumb or can it do vlans? I would guess dumb.. Do you have a make and model number of this board.
What is the rest of your network.. Why did you think you needed/wanted so many ports on your router - along with a switch that that is just dumb?? Other than trying to fit all into 1 box? At the loss of features and usability. Sure you can bridge those interfaces - but now it becomes a really BAD switch, that you could of gotten better switch for for like $30 ;)
8 gig nics would be fantastic on a router.. But trying to use them as a switch by bridging never going to be a good idea ;) For the sake of some space? So your going to rack this somewhere? Why could you not just put a nice smart/fully managed switch which is only going to be another 1u in the rack.. And now you would be cooking with gas, 8 port router with lots of fully managed switch ports in the space of 2u..
-
The switch is a Netgear GS108.
"8 gig nics would be fantastic on a router." Exactly thats what i want, i want to try to set it up to route the traffic not just bridge everything.
I would like to set it up so the DHCP server is shared across the lan ports, but then i can setup firewall rules on what traffic from a given interface and access other interfaces. Is there any advice on how to best achieve this?Ie control my Access Point and what that can hit, same as my kodi box.
Trev
-
Well they are 8 different nics, so yes they could be 8 different networks wan, lan, opt1, optX etc.. But unless your going to then connect these ports to a smart switch that does vlans or individual dumb switches you would only ever have 1 device on them.
You could connect an AP that does vlans to 1 of the ports and run multiple wifi networks this way.
The gs108 is just dumb switch - so you just took it out of its case.. Nice idea, but should of be at min a gs108t (smart switch).
"I would like to set it up so the DHCP server is shared across the lan ports"
It doesn't work that way without bridging them.. But you can run dhcp server on each of the 7 different networks you could create. If you could give some idea of your devices and how many different networks/vlans you want we could figure out how best to set it up.. If your going to want multiple devices on the same L2 then your going to have to either bridge the ports or connect 1 of the ports to your dumb switch in the box and then all devices connected to any of those switch ports would be on the same layer 2 as the port you connected that switch to on your router ports.
As you already knew - bridging ports is bad ;) It has it needs.. But its shame to see such a nice setup that now lacks functionality because you wanted to fit it all in a 1 u box.. Can you not just get a 1u switch with say 24 ports to put in the same rack.. And then pretty much sky is the limit to what you could do with those 8 router ports and smart switch. Tied with some AP that does vlan and yeah sweet setup to be sure.. While if you bridge them it just turns into a misguided setup..
-
What I would like to know is the make and model of the case. I had been looking for a 1U case for a long time for a pfSense build – until I went in a different direction (case wise)
And did you have to cut up the case in order to fit the motherboard and the GS108 board in there?
-
Ooo, shiny! ;D
I would like to set it up so the DHCP server is shared across the lan ports
What are you calling the LAN ports here?
The only reason you would want to bridge ports normally in this sort of setup if of you have devices that cannot 'find' things outside their own subnet. Often that would be smart TVs looking for media servers for example.
However I thought Kodi was better than that.
Yeah, bridging is bad and should be avoided but it will work.
Steve
-
Man, thats mad clean!
Very nice work, beats my Basic 1U ITX AMD Mobo into a 1U Case loL!
Nicely done!
-
amazing job, maybe change some fans for noctuas fan if noise is a problem, ::)
do you mind to tell how much it cost? I´m planning to start my own pfsense too, to tired of comercial routers…
-
Thanks for the comments, ive started setting the pfsenses lan ports up as a router, and my main house lan runs through the switch to the right. I still want to work on the rules to control what protocols and ports are used by certain interfaces. Currently they are using the default rule. Appart from that im very pleased.

Its surprisingly quitet and alot of the time the cpu is idling but im keeping an eye on temps.
with regards to the case it was based off a PENN ELCOM R2110/1UK 19" Rack Enclosure:1U. Although i replaced the sides and back as there isnt enough space as it stands to house the power supply. Cost wise im not really sure. The Jetway JNF592-Q170 motherboard and cpu was the biggest cost, although its not too bad when you compare it to other high end motherboards.
just need to work on the config now.
Trev
-
So if your running your left interfaces as actual interfaces and not bridged, So you only have 1 device on them or they are running to other switches or AP with vlans on them?
Give an example of what you have connected to each interface and what you want to allow or prevent from a traffic point of view and we can walk through how to setup the rules.
You place the rules on the interface where the traffic enters pfsense - rules are evaluated top down, first rule to trigger wins no other rules are evaluated. Its that simple.
If you don't want lan to talk to opt1, the non lan put a rule to block lan net from talking to opt1 net. Then under that you could leave your any any rule. all comes down to how granular you want to get and what exactly your wanting to prevent or allow between your networks or between specific IPs on different networks.
But I don't know dude that rack looks like its got some space where you could of just added a 1U smart/managed switch. Guess you still can.. So which cable did you connect from your switch over to your network interfaces? I would of just used a little 6, 9 inch or 1ft patch between right most nic and the 8 port switch on the right.
-
Note that there are sometimes problems with really short cable runs between devices. Not always, but worth being aware of the possibility, so if you have link issues you can try replacing a tiny cable with a 3 foot patch.
-
We have used 1 foot patches all the time.. I do not recall anything specifically in the ieee specs for min length of cat5 or 6 cable.. fiber is a different story. But if you have shoddy equipment or cable could always have some weirdness.
Check the ports for errors if you see them, then sure go with 1m cable.. But if your cable is certified.. then you should not have any problems.. You might have problem finding shorter than 1ft certified.. But just looked on 1ft patch on deepsurplus
http://www.deepsurplus.com/Network-Structured-Wiring/Cat6-Standard-Boot-1ft/1ft-Blue-Cat-6-Patch-Cable-Molded"Meets or exceeds the ANSI/TIA/EIA-568-B.2-1 standard for CAT 6 CMR, communication riser cable, and certified by UL, Underwriters Laboratories."
-
…. You might have problem finding shorter than 1ft certified.. But just looked on 1ft patch on deepsurplus
http://www.deepsurplus.com/Network-Structured-Wiring/Cat6-Standard-Boot-1ft/1ft-Blue-Cat-6-Patch-Cable-Molded"Meets or exceeds the ANSI/TIA/EIA-568-B.2-1 standard for CAT 6 CMR, communication riser cable, and certified by UL, Underwriters Laboratories."
6 inch patch cables that I use between my patch panel and switch.
https://www.monoprice.com/product?c_id=102&cp_id=10232&cs_id=1023203&p_id=9789&seq=1&format=2From the website:
Monoprice Ethernet cables are made of 100% pure bare copper wire, as opposed to copper clad aluminum (CCA) wire, and are therefore fully compliant with UL Code 444 and National Electrical Code TIA-568-C.2 fire and safety standards, which require pure bare copper wire in communications cables.
-
with regards to the case it was based off a PENN ELCOM R2110/1UK 19" Rack Enclosure:1U. Although i replaced the sides and back as there isnt enough space as it stands to house the power supply.
Thanks for the case information. Did you have to cut up the front yourself to have access to the ports, hdmi connection, lcd and the buttons?
-
There was minimum length on Ethernet once upon a time.
The length was a consequence of timing requirements in the CSMA/CD to reliably detect collisions, IE it shouldn't be an issue at all in switched Ethernet.
All based on my memory and about 20 years old network technology training (non of them are ECC) -
There was minimum length on Ethernet once upon a time.
The length was a consequence of timing requirements in the CSMA/CD to reliably detect collisions, IE it shouldn't be an issue at all in switched Ethernet.
All based on my memory and about 20 years old network technology training (non of them are ECC)And yet I've seen actual problems in the field where use of really short patch cables between transceivers was resolved by a coiled up longer cable. :) (The basis of the problems wouldn't be collision detection timing, it would be signal reflection. I've seen it far less often with newer ethernet chipsets, which tend to be far more forgiving of all sorts of cable problems than older ones were, and signal strength reduction for EEE may also help. That's why I characterize it as "something to be aware of" rather than "don't do this".)
-
^exactly.. If you were having weirdness and you were using very short patch - it would be something to look at for sure.. And it was good of you to bring it up so the user or others might be aware that sure very short cables could have issues… But I have used 6 in patch to uplink a desktop (cheap) switch to another sitting right on top of it, etc. And never had any issues..
And have had hundreds of 1ft patch in the DC without any problems.. But those are normally from switch to patch, but in some cases from switch to switch, etc. Your experience could vary - but if there is nothing in the spec that says patch has to be X inches long then if looks better short why not give it a go ;) Your talking a few bucks at most for a patch cable.
-
Hi,
Yes they are running as interfaces. Some go to switches and some dont, but there arnt currently any vlans.
CCTV
Lan (goes to the little switch on the right)
Media (goes to a small switch to two different devices)
NAS
SKY
TV (goes to a built in switch on the HDBaseT distribution)
WAN
WIFICurrently as a short term thing i have setup the default PF sense rule on each interface so effectivly every port and hit the other ports.
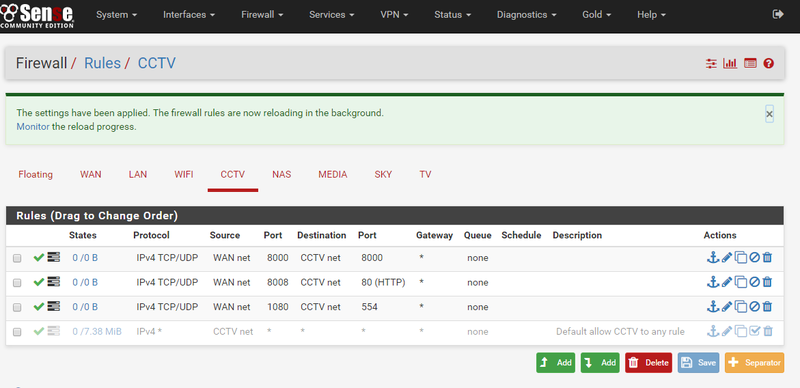
I would like to lock down the CCTV, Media, Nas, SKY, and TV ports.
Tonight i disabled the default rule i set on the CCTV interface and attempted the setup the correct ports but i think i must have got it wrong as i could nolonger view the CCTV via my mobile.
The ports are listed in this document http://www.hikvision.com/ueditor/net/upload/2015-06-10/3b56a0c6-f61c-4381-866e-dc49e5c30c88.pdf
It talks of
1080 external to 554 internal
8008 external to 80 internal
8000 external to 8000 internalbut i think i may have got it wrong somewhere.
There is another unit thats not in the rack at the mo, its a ZWave controller which is just going to be patched into the lan switch.
with regards to the front panel and replacement rear panel, i measured the motherboard ext and drew it in cad. I then cut it on a CNC router.
Trev
-