Discovery across vlans
-
The Macbook Pro is connected to the vlan30 subnet directly?
Is that app using mDNS to discover the service even?
If it's using DLNA/upnp you might have more luck with the IGMP proxy.
The better way would be to just enter the IP address on the amp in the clients directly and not rely on some discovery protocol which is not meant to work across subnet. However many app developers seem to omit this simple option.
Steve
-
The Macbook is connected to VL20.
Spotify doesn't allow direct IP connection.
-
@stephenw10 said in Discovery across vlans:
IGMP proxy
is there anything I should do on the switch for this?
-
Ah, you edited while I was typing. Where are you seeing that logged error?
Your switch may well have some igmp filtering features that could be causing a problem.
I suspect your Macbook is using some different discovery method. You might be able to see something in a packet capture to determine what each device is using.
It's a mystery to me why typing an IP address seems to be considered beyond the capability of average users by whoever is developing these things but that's how they apparently think.

Steve
-
@mtk said in Discovery across vlans:
Spotify doesn’t allow direct IP connection.
I would scream at them loudly and often then.. Just moronic to not support direct IP or FQDN access and only use discovery that is designed for everything to be on the same layer 2..
-
@stephenw10 said in Discovery across vlans:
Ah, you edited while I was typing. Where are you seeing that logged error?
in the Status/System Logs/System/General
-
@johnpoz said in Discovery across vlans:
@mtk said in Discovery across vlans:
Spotify doesn’t allow direct IP connection.
I would scream at them loudly and often then.. Just moronic to not support direct IP or FQDN access and only use discovery that is designed for everything to be on the same layer 2..
The Marantz/Denon app, allows manual input of an IP, but the device does not response (no error log).
The device does respond to a normal web access (port 80), as it should, and is pingable. -
How should I set the IGMP Proxy in this case?
-
@mtk said in Discovery across vlans:
in the Status/System Logs/System/General
That was Avahi logging that?
@mtk said in Discovery across vlans:
The Marantz/Denon app, allows manual input of an IP, but the device does not response (no error log).
The device does respond to a normal web access (port 80), as it should, and is pingable.Now that's more interesting. Do you have allow all rules between those subnets/VLANs?
If not do you see anything blocked?Or any states created from the client to the amp IP on other ports?
Configuring the IGMP provxy should just be a matter if choosing the interfaces to have it listen on. However there was an issue using it with VLAN interfaces a while ago. I'm unsure of the status of it currently.
Steve
-
@stephenw10 said in Discovery across vlans:
@mtk said in Discovery across vlans:
in the Status/System Logs/System/General
That was Avahi logging that?
yes:
May 27 21:03:12 avahi-daemon 79804 Invalid response packet from host 192.168.30.102.@mtk said in Discovery across vlans:
The Marantz/Denon app, allows manual input of an IP, but the device does not response (no error log).
The device does respond to a normal web access (port 80), as it should, and is pingable.Now that's more interesting. Do you have allow all rules between those subnets/VLANs?
If not do you see anything blocked?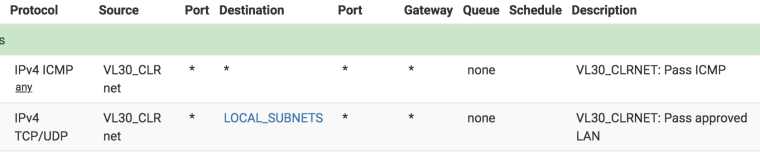
(equivalent rule on the other side)Or any states created from the client to the amp IP on other ports?
There is nothing being logged on either the amp IP (on VLAN30) or my phone's (on VLAN20)
Configuring the IGMP provxy should just be a matter if choosing the interfaces to have it listen on. However there was an issue using it with VLAN interfaces a while ago. I'm unsure of the status of it currently.
Over VLAN is the whole issue here, isn't it?
-
Try passing protocol any instead of just TCP/UDP.
Maybe the server itself has some type of firewall that only allows for same-subnet traffic.
Packet capture on the interface with the destination server on it. If you see the traffic but no response, you'll have to fix that.
-
@derelict said in Discovery across vlans:
Try passing protocol any instead of just TCP/UDP.
Maybe the server itself has some type of firewall that only allows for same-subnet traffic.
Packet capture on the interface with the destination server on it. If you see the traffic but no response, you'll have to fix that.
UPDATE1: an iPhone (on VLAN20) actually does manage to discover the Marantz (on VLAN30) and play music on it. But does not see it on the Marantz app itself :/
UPDATE2: Package capture doesn't see anything on either interface when trying to discover.
UPDATE2 This is what the package capture gets:22:02:44.494202 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.494599 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 0 22:02:44.496907 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.498638 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 31 22:02:44.498932 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 0 22:02:44.500913 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 95 22:02:44.501213 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 0 22:02:44.507831 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 600 22:02:44.510033 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.511287 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 600 22:02:44.513255 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.513645 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 600 22:02:44.516195 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.516654 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 1420 22:02:44.519214 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.519402 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.519680 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 0 22:02:44.520178 IP 192.168.30.102.8080 > 192.168.20.102.40681: tcp 0 22:02:44.521788 IP 192.168.20.102.40681 > 192.168.30.102.8080: tcp 0 22:02:44.523255 IP 192.168.20.102.55259 > 192.168.30.102.80: tcp 0 -
That pcap doesn't show much. You probably just want to download the pcap from that page and upload it here. Or at least set detail to full and view it and paste that. (the pcap allows people to use wireshark to help you which makes things a lot easier on them).
This is probably going to understand what your audio system requires. Maybe they have a guide for home theater installers or something that goes into more detail about what is required.
-
@derelict said in Discovery across vlans:
That pcap doesn't show much. You probably just want to download the pcap from that page and upload it here. Or at least set detail to full and view it and paste that. (the pcap allows people to use wireshark to help you which makes things a lot easier on them).
This is probably going to understand what your audio system requires. Maybe they have a guide for home theater installers or something that goes into more detail about what is required.
22:24:24.083356 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 27065, offset 0, flags [DF], proto TCP (6), length 60) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [S], cksum 0x4121 (correct), seq 692373871, win 65535, options [mss 1460,sackOK,TS val 10920150 ecr 0,nop,wscale 8], length 0 22:24:24.084121 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 58: (tos 0x0, ttl 127, id 11303, offset 0, flags [none], proto TCP (6), length 44) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [S.], cksum 0x7938 (correct), seq 12761273, ack 692373872, win 65535, options [mss 1460], length 0 22:24:24.087501 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27066, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x90f5 (correct), seq 1, ack 1, win 65535, length 0 22:24:24.088242 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 85: (tos 0x0, ttl 64, id 27067, offset 0, flags [DF], proto TCP (6), length 71) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [P.], cksum 0xe2ea (correct), seq 1:32, ack 1, win 65535, length 31: HTTP, length: 31 GET /description.xml HTTP/1.1 22:24:24.088600 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11304, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [.], cksum 0x90f5 (correct), seq 1, ack 32, win 65504, length 0 22:24:24.090639 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 149: (tos 0x0, ttl 64, id 27068, offset 0, flags [DF], proto TCP (6), length 135) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [P.], cksum 0xefc4 (correct), seq 32:127, ack 1, win 65535, length 95: HTTP 22:24:24.091000 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11305, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [.], cksum 0x90d6 (correct), seq 1, ack 127, win 65440, length 0 22:24:24.098115 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 654: (tos 0x0, ttl 127, id 11306, offset 0, flags [none], proto TCP (6), length 640) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [P.], cksum 0x91a7 (correct), seq 1:601, ack 127, win 65535, length 600: HTTP, length: 600 HTTP/1.1 200 OK CONTENT-TYPE: text/xml;charset="utf-8" CONTENT-LENGTH: 3139 <?xml version="1.0"?> <root xmlns="urn:schemas-upnp-org:device-1-0" xmlns:ms=" urn:microsoft-com:wmc-1-0" xmlns:smsc="www.smsc.com" xmlns:qq="http://www.tencent.com" xmlns:pnpx="http://schemas.microsoft.com/windows/pnpx/2005/11" xmlns:df="http://schemas.microsoft.com/windows/2008/09/devicefoundation"> <specVersion> <major>1</major> <minor>0</minor> </specVersion> <device> <dlna:X_DLNADOC xmlns:dlna="urn:schemas-dlna-org:device-1-0">DMR-1.50</dlna:X_DLNADOC> <pnpx:X_compatibleId[!http] 22:24:24.100132 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27069, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x8e1f (correct), seq 127, ack 601, win 65535, length 0 22:24:24.101839 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 654: (tos 0x0, ttl 127, id 11307, offset 0, flags [none], proto TCP (6), length 640) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [P.], cksum 0xe79d (correct), seq 601:1201, ack 127, win 65535, length 600: HTTP 22:24:24.104647 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 654: (tos 0x0, ttl 127, id 11308, offset 0, flags [none], proto TCP (6), length 640) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [.], cksum 0xe4bc (correct), seq 1201:1801, ack 127, win 65535, length 600: HTTP 22:24:24.104984 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27070, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x8bc7 (correct), seq 127, ack 1201, win 65535, length 0 22:24:24.107181 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27071, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x896f (correct), seq 127, ack 1801, win 65535, length 0 22:24:24.107681 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 1474: (tos 0x0, ttl 127, id 11309, offset 0, flags [none], proto TCP (6), length 1460) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [P.], cksum 0x8758 (correct), seq 1801:3221, ack 127, win 65535, length 1420: HTTP 22:24:24.109682 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27072, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x83e3 (correct), seq 127, ack 3221, win 65535, length 0 22:24:24.109925 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 27073, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [F.], cksum 0x83e2 (correct), seq 127, ack 3221, win 65535, length 0 22:24:24.110268 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11310, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [.], cksum 0x83e2 (correct), seq 3221, ack 128, win 65535, length 0 22:24:24.110626 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11311, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.8080 > 192.168.20.102.40704: Flags [F.], cksum 0x83e1 (correct), seq 3221, ack 128, win 65535, length 0 22:24:24.110918 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 17224, offset 0, flags [DF], proto TCP (6), length 60) 192.168.20.102.55282 > 192.168.30.102.80: Flags [S], cksum 0x5145 (correct), seq 3846628242, win 65535, options [mss 1460,sackOK,TS val 10920154 ecr 0,nop,wscale 8], length 0 22:24:24.111385 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 58: (tos 0x0, ttl 127, id 11312, offset 0, flags [none], proto TCP (6), length 44) 192.168.30.102.80 > 192.168.20.102.55282: Flags [S.], cksum 0x8ee0 (correct), seq 12825400, ack 3846628243, win 65535, options [mss 1460], length 0 22:24:24.112413 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 38173, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.40704 > 192.168.30.102.8080: Flags [.], cksum 0x3a45 (correct), seq 128, ack 3222, win 18844, length 0 22:24:24.115102 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 17225, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55282 > 192.168.30.102.80: Flags [.], cksum 0xa69d (correct), seq 1, ack 1, win 65535, length 0 22:24:24.115140 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 106: (tos 0x0, ttl 64, id 17226, offset 0, flags [DF], proto TCP (6), length 92) 192.168.20.102.55282 > 192.168.30.102.80: Flags [P.], cksum 0x71df (correct), seq 1:53, ack 1, win 65535, length 52: HTTP, length: 52 GET /goform/formiPhoneAppControlJudge.xml HTTP/1.1 22:24:24.115540 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11313, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55282: Flags [.], cksum 0xa69d (correct), seq 1, ack 53, win 65483, length 0 22:24:24.117586 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 144: (tos 0x0, ttl 64, id 17227, offset 0, flags [DF], proto TCP (6), length 130) 192.168.20.102.55282 > 192.168.30.102.80: Flags [P.], cksum 0x5a13 (correct), seq 53:143, ack 1, win 65535, length 90: HTTP 22:24:24.117972 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11314, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55282: Flags [.], cksum 0xa669 (correct), seq 1, ack 143, win 65445, length 0 22:24:24.119319 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 71: (tos 0x0, ttl 127, id 11315, offset 0, flags [none], proto TCP (6), length 57) 192.168.30.102.80 > 192.168.20.102.55282: Flags [P.], cksum 0xe631 (correct), seq 1:18, ack 143, win 65535, length 17: HTTP, length: 17 HTTP/1.0 200 OK 22:24:24.121381 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 17228, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55282 > 192.168.30.102.80: Flags [.], cksum 0xa5fe (correct), seq 143, ack 18, win 65535, length 0 22:24:24.121781 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 160: (tos 0x0, ttl 127, id 11316, offset 0, flags [none], proto TCP (6), length 146) 192.168.30.102.80 > 192.168.20.102.55282: Flags [.], cksum 0x41c1 (correct), seq 18:124, ack 143, win 65535, length 106: HTTP 22:24:24.121813 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 157: (tos 0x0, ttl 127, id 11317, offset 0, flags [none], proto TCP (6), length 143) 192.168.30.102.80 > 192.168.20.102.55282: Flags [P.], cksum 0x0587 (correct), seq 124:227, ack 143, win 65535, length 103: HTTP 22:24:24.124007 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 17229, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55282 > 192.168.30.102.80: Flags [.], cksum 0xa594 (correct), seq 143, ack 124, win 65535, length 0 22:24:24.124332 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 17230, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55282 > 192.168.30.102.80: Flags [.], cksum 0xa52d (correct), seq 143, ack 227, win 65535, length 0 22:24:24.124576 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11318, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55282: Flags [F.], cksum 0xa52c (correct), seq 227, ack 143, win 65535, length 0 22:24:24.127845 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 17231, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55282 > 192.168.30.102.80: Flags [F.], cksum 0xa52b (correct), seq 143, ack 228, win 65535, length 0 22:24:24.128198 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11319, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55282: Flags [.], cksum 0xa52b (correct), seq 228, ack 144, win 65535, length 0 22:24:24.128493 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 15253, offset 0, flags [DF], proto TCP (6), length 60) 192.168.20.102.55283 > 192.168.30.102.80: Flags [S], cksum 0x7286 (correct), seq 206347081, win 65535, options [mss 1460,sackOK,TS val 10920156 ecr 0,nop,wscale 8], length 0 22:24:24.128924 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 58: (tos 0x0, ttl 127, id 11320, offset 0, flags [none], proto TCP (6), length 44) 192.168.30.102.80 > 192.168.20.102.55283: Flags [S.], cksum 0xb5a3 (correct), seq 12889527, ack 206347082, win 65535, options [mss 1460], length 0 22:24:24.130247 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15254, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xcd60 (correct), seq 1, ack 1, win 65535, length 0 22:24:24.130424 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 91: (tos 0x0, ttl 64, id 15255, offset 0, flags [DF], proto TCP (6), length 77) 192.168.20.102.55283 > 192.168.30.102.80: Flags [P.], cksum 0xfb60 (correct), seq 1:38, ack 1, win 65535, length 37: HTTP, length: 37 GET /goform/Deviceinfo.xml HTTP/1.1 22:24:24.130701 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11321, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xcd60 (correct), seq 1, ack 38, win 65498, length 0 22:24:24.133255 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 144: (tos 0x0, ttl 64, id 15256, offset 0, flags [DF], proto TCP (6), length 130) 192.168.20.102.55283 > 192.168.30.102.80: Flags [P.], cksum 0x80e5 (correct), seq 38:128, ack 1, win 65535, length 90: HTTP 22:24:24.133599 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 11322, offset 0, flags [none], proto TCP (6), length 40) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xcd3b (correct), seq 1, ack 128, win 65445, length 0 22:24:24.236063 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 71: (tos 0x0, ttl 127, id 11323, offset 0, flags [none], proto TCP (6), length 57) 192.168.30.102.80 > 192.168.20.102.55283: Flags [P.], cksum 0x0d04 (correct), seq 1:18, ack 128, win 65535, length 17: HTTP, length: 17 HTTP/1.0 200 OK 22:24:24.238440 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15257, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xccd0 (correct), seq 128, ack 18, win 65535, length 0 22:24:24.238895 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 160: (tos 0x0, ttl 127, id 11324, offset 0, flags [none], proto TCP (6), length 146) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x6893 (correct), seq 18:124, ack 128, win 65535, length 106: HTTP 22:24:24.238926 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 178: (tos 0x0, ttl 127, id 11325, offset 0, flags [none], proto TCP (6), length 164) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xc067 (correct), seq 124:248, ack 128, win 65535, length 124: HTTP 22:24:24.238965 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 180: (tos 0x0, ttl 127, id 11326, offset 0, flags [none], proto TCP (6), length 166) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x4627 (correct), seq 248:374, ack 128, win 65535, length 126: HTTP 22:24:24.238995 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 127, id 11327, offset 0, flags [none], proto TCP (6), length 182) 192.168.30.102.80 > 192.168.20.102.55283: Flags [P.], cksum 0x352a (correct), seq 374:516, ack 128, win 65535, length 142: HTTP 22:24:24.241261 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15258, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xcc66 (correct), seq 128, ack 124, win 65535, length 0 22:24:24.241294 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15259, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xcbea (correct), seq 128, ack 248, win 65535, length 0 22:24:24.241386 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15260, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xcb6c (correct), seq 128, ack 374, win 65535, length 0 22:24:24.241552 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15261, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xcade (correct), seq 128, ack 516, win 65535, length 0 22:24:24.241900 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 192: (tos 0x0, ttl 127, id 11328, offset 0, flags [none], proto TCP (6), length 178) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x5830 (correct), seq 516:654, ack 128, win 65535, length 138: HTTP 22:24:24.241931 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 175: (tos 0x0, ttl 127, id 11329, offset 0, flags [none], proto TCP (6), length 161) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x207c (correct), seq 654:775, ack 128, win 65535, length 121: HTTP 22:24:24.241968 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 163: (tos 0x0, ttl 127, id 11330, offset 0, flags [none], proto TCP (6), length 149) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x8d82 (correct), seq 775:884, ack 128, win 65535, length 109: HTTP 22:24:24.242000 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 102: (tos 0x0, ttl 127, id 11331, offset 0, flags [none], proto TCP (6), length 88) 192.168.30.102.80 > 192.168.20.102.55283: Flags [P.], cksum 0x3778 (correct), seq 884:932, ack 128, win 65535, length 48: HTTP 22:24:24.244032 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15262, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xca54 (correct), seq 128, ack 654, win 65535, length 0 22:24:24.244279 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15263, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc9db (correct), seq 128, ack 775, win 65535, length 0 22:24:24.244457 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15264, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc96e (correct), seq 128, ack 884, win 65535, length 0 22:24:24.250709 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 122: (tos 0x0, ttl 127, id 11332, offset 0, flags [none], proto TCP (6), length 108) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x31e2 (correct), seq 932:1000, ack 128, win 65535, length 68: HTTP 22:24:24.251179 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 172: (tos 0x0, ttl 127, id 11333, offset 0, flags [none], proto TCP (6), length 158) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xda88 (correct), seq 1000:1118, ack 128, win 65535, length 118: HTTP 22:24:24.252190 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 169: (tos 0x0, ttl 127, id 11334, offset 0, flags [none], proto TCP (6), length 155) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x852d (correct), seq 1118:1233, ack 128, win 65535, length 115: HTTP 22:24:24.252693 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 173: (tos 0x0, ttl 127, id 11335, offset 0, flags [none], proto TCP (6), length 159) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x6b81 (correct), seq 1233:1352, ack 128, win 65535, length 119: HTTP 22:24:24.252896 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15265, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc93e (correct), seq 128, ack 932, win 65535, length 0 22:24:24.253082 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15266, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc8fa (correct), seq 128, ack 1000, win 65535, length 0 22:24:24.253116 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15267, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc884 (correct), seq 128, ack 1118, win 65535, length 0 22:24:24.253670 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 192: (tos 0x0, ttl 127, id 11336, offset 0, flags [none], proto TCP (6), length 178) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xdd63 (correct), seq 1352:1490, ack 128, win 65535, length 138: HTTP 22:24:24.254321 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15268, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc811 (correct), seq 128, ack 1233, win 65535, length 0 22:24:24.254493 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15269, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc79a (correct), seq 128, ack 1352, win 65535, length 0 22:24:24.255829 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 172: (tos 0x0, ttl 127, id 11337, offset 0, flags [none], proto TCP (6), length 158) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x204e (correct), seq 1490:1608, ack 128, win 65535, length 118: HTTP 22:24:24.256259 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15270, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc710 (correct), seq 128, ack 1490, win 65535, length 0 22:24:24.256824 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 190: (tos 0x0, ttl 127, id 11338, offset 0, flags [none], proto TCP (6), length 176) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xd635 (correct), seq 1608:1744, ack 128, win 65535, length 136: HTTP 22:24:24.258023 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 183: (tos 0x0, ttl 127, id 11339, offset 0, flags [none], proto TCP (6), length 169) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x4e48 (correct), seq 1744:1873, ack 128, win 65535, length 129: HTTP 22:24:24.258180 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15271, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc69a (correct), seq 128, ack 1608, win 65535, length 0 22:24:24.258413 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15272, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc612 (correct), seq 128, ack 1744, win 65535, length 0 22:24:24.259519 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 170: (tos 0x0, ttl 127, id 11340, offset 0, flags [none], proto TCP (6), length 156) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x2da7 (correct), seq 1873:1989, ack 128, win 65535, length 116: HTTP 22:24:24.260131 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 174: (tos 0x0, ttl 127, id 11341, offset 0, flags [none], proto TCP (6), length 160) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x84ed (correct), seq 1989:2109, ack 128, win 65535, length 120: HTTP 22:24:24.260391 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15273, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc591 (correct), seq 128, ack 1873, win 65535, length 0 22:24:24.261476 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 175: (tos 0x0, ttl 127, id 11342, offset 0, flags [none], proto TCP (6), length 161) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xc857 (correct), seq 2109:2230, ack 128, win 65535, length 121: HTTP 22:24:24.262085 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 191: (tos 0x0, ttl 127, id 11343, offset 0, flags [none], proto TCP (6), length 177) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x1f22 (correct), seq 2230:2367, ack 128, win 65535, length 137: HTTP 22:24:24.263134 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15274, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc4a5 (correct), seq 128, ack 2109, win 65535, length 0 22:24:24.263559 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 165: (tos 0x0, ttl 127, id 11344, offset 0, flags [none], proto TCP (6), length 151) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x0f66 (correct), seq 2367:2478, ack 128, win 65535, length 111: HTTP 22:24:24.263735 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15275, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc3a3 (correct), seq 128, ack 2367, win 65535, length 0 22:24:24.264455 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 184: (tos 0x0, ttl 127, id 11345, offset 0, flags [none], proto TCP (6), length 170) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x57b4 (correct), seq 2478:2608, ack 128, win 65535, length 130: HTTP 22:24:24.265632 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 184: (tos 0x0, ttl 127, id 11346, offset 0, flags [none], proto TCP (6), length 170) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x5530 (correct), seq 2608:2738, ack 128, win 65535, length 130: HTTP 22:24:24.265854 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15276, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc2b2 (correct), seq 128, ack 2608, win 65535, length 0 22:24:24.266534 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 127, id 11347, offset 0, flags [none], proto TCP (6), length 182) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x2952 (correct), seq 2738:2880, ack 128, win 65535, length 142: HTTP 22:24:24.267885 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 187: (tos 0x0, ttl 127, id 11348, offset 0, flags [none], proto TCP (6), length 173) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x5130 (correct), seq 2880:3013, ack 128, win 65535, length 133: HTTP 22:24:24.268680 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 196: (tos 0x0, ttl 127, id 11349, offset 0, flags [none], proto TCP (6), length 182) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x03ba (correct), seq 3013:3155, ack 128, win 65535, length 142: HTTP 22:24:24.269978 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 177: (tos 0x0, ttl 127, id 11350, offset 0, flags [none], proto TCP (6), length 163) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x9e7f (correct), seq 3155:3278, ack 128, win 65535, length 123: HTTP 22:24:24.270033 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15277, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc08f (correct), seq 128, ack 3155, win 65535, length 0 22:24:24.271312 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 178: (tos 0x0, ttl 127, id 11351, offset 0, flags [none], proto TCP (6), length 164) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xf9ec (correct), seq 3278:3402, ack 128, win 65535, length 124: HTTP 22:24:24.272162 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15278, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xc014 (correct), seq 128, ack 3278, win 65535, length 0 22:24:24.272290 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 176: (tos 0x0, ttl 127, id 11352, offset 0, flags [none], proto TCP (6), length 162) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xce46 (correct), seq 3402:3524, ack 128, win 65535, length 122: HTTP 22:24:24.273461 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15279, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xbf1e (correct), seq 128, ack 3524, win 65535, length 0 22:24:24.273655 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 188: (tos 0x0, ttl 127, id 11353, offset 0, flags [none], proto TCP (6), length 174) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xd7b4 (correct), seq 3524:3658, ack 128, win 65535, length 134: HTTP 22:24:24.274583 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 197: (tos 0x0, ttl 127, id 11354, offset 0, flags [none], proto TCP (6), length 183) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x61b3 (correct), seq 3658:3801, ack 128, win 65535, length 143: HTTP 22:24:24.275768 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 182: (tos 0x0, ttl 127, id 11355, offset 0, flags [none], proto TCP (6), length 168) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0xee64 (correct), seq 3801:3929, ack 128, win 65535, length 128: HTTP 22:24:24.275817 c0:ee:fb:24:9d:c8 > 00:0d:b9:44:59:b1, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 15280, offset 0, flags [DF], proto TCP (6), length 40) 192.168.20.102.55283 > 192.168.30.102.80: Flags [.], cksum 0xbe09 (correct), seq 128, ack 3801, win 65535, length 0 22:24:24.276682 00:0d:b9:44:59:b1 > c0:ee:fb:24:9d:c8, ethertype IPv4 (0x0800), length 192: (tos 0x0, ttl 127, id 11356, offset 0, flags [none], proto TCP (6), length 178) 192.168.30.102.80 > 192.168.20.102.55283: Flags [.], cksum 0x2a50 (correct), seq 3929:4067, ack 128, win 65535, length 138: HTTP -
No discovery there. Everything there looks normal.
-
@derelict said in Discovery across vlans:
No discovery there. Everything there looks normal.
also the broken XML?
HTTP/1.1 200 OK CONTENT-TYPE: text/xml;charset="utf-8" CONTENT-LENGTH: 3139 <?xml version="1.0"?> <root xmlns="urn:schemas-upnp-org:device-1-0" xmlns:ms=" urn:microsoft-com:wmc-1-0" xmlns:smsc="www.smsc.com" xmlns:qq="http://www.tencent.com" xmlns:pnpx="http://schemas.microsoft.com/windows/pnpx/2005/11" xmlns:df="http://schemas.microsoft.com/windows/2008/09/devicefoundation"> <specVersion> <major>1</major> <minor>0</minor> </specVersion> <device> <dlna:X_DLNADOC xmlns:dlna="urn:schemas-dlna-org:device-1-0">DMR-1.50</dlna:X_DLNADOC> <pnpx:X_compatibleId[!http]BTW, This is when trying to manually tell the Marantz APP to find the device (by IP).
-
I don't know how much we are going to be able to help you here.
-
@derelict said in Discovery across vlans:
I don't know how much we are going to be able to help you here.
I found this in the States:
VL30_CLR udp 192.168.30.102:52241 -> 239.255.250.250:9131 NO_TRAFFIC:SINGLE 23 / 0 3 KiB / 0 B(this is the IP of the Marantz)
-
I assume 192.168.20.102 was the IP of the phone at that point?
If you entered the IP if the amp and there was two way traffic between them it's hard to say why it wouldn't show as available.
As Derelict says there may well be some installation instructions for operating across subnets. It's not that unusual.
Steve
-
@stephenw10 said in Discovery across vlans:
I assume 192.168.20.102 was the IP of the phone at that point?
Yes
If you entered the IP if the amp and there was two way traffic between them it's hard to say why it wouldn't show as available.
As Derelict says there may well be some installation instructions for operating across subnets. It's not that unusual.
Steve
And yet, nowhere to be found...
