Extreme slowdown of download speed with Netgate SG-1000
-
Why would you not just vpn if you need to access multiple devices and multiple ports?
That doesn't sound like 1 IP, so how would you do it a forward or even a "dmz host" as you call it to that... Sure you can forward ALL the ports to an IP... But you can not forward all the ports to multiple IPs... You can forward port X to IPA and Y to IPB but those are different rules.
Why would your devices not be able to be on different network segments. Only thing that needs to be on the same layer 2 is shitty soho devices that use some L2 discovery protocol to find what they are looking for. As long as the application or device allows you to set an IP, and use IP or fqdn to get to whatever it is it needs to talk to. Then they can be on the internet, or different network segment.
You can then limit access to specific ports and protocols on the firewall between your segments.
Butt if your controlling this remote to your cabin, accessing your camera's etc.. Then you should VPN into this cabin and access it whatever it is you need to access without any need to port forward anything.
So your guests to control something while they are there - go out to the internet and back in. Or do you have wifi at this cabin they connect to?
-
This isn't multiple IP's. They are all running on the same virtual machine (except for Node-RED and Hass, wich runs on a Rasberry PI, but they don't change their ports, and they go through the home automation VM with MQTT). And I don't want to be rude, but I don't really need these suggestions and questions, I only need a simple answer to the simple question of how I route all ports to one IP, if you have that answer. I have been running a system like this for several years without problems, before I came to the first device I've had that does not have a dedicated DMZ.
-
Create a port forward and forward the range you want 1 to 65k if you want all the ports... Its that simple..
https://www.netgate.com/docs/pfsense/nat/forwarding-ports-with-pfsense.html
or just do a 1:1 Nat..
https://www.netgate.com/docs/pfsense/nat/1-1-nat.html -
Thanks! :)
-
@mastiff @johnpoz
I really need to learn more about my device so I can move my IOT devices into their own network. I use Philips Hue, Ecobee, Lutron, Nest...I still want to see the devices inside the Home app with a device that belongs on the main network. Just don’t know how yet so eveything is on the one network currently. Works great but not secure. -
I see my devices on my phone..
Here are 2 things that use lutron, and I have both nest thermo and protect.. These devices create outbound connections and you control them from their connection to the internet. They do not use local connectivity.
I can not speak to philips or ecobee but anything that requires you to allow unsolicited inbound traffic would be a problem if you ask me..
These devices of mine are NOT on the same network my phone is on.. My phone uses a eap-tls wifi network, that is isolated to only my trusted devices. My phone, my wifes phone, our laptops, tablet, etc. Other devices are on different wifi vlans.
-
@johnpoz
My main issue is lack of knowledge. I admit that and I’m working on it and will commit to learning what I need so I can segment the devices. I forgot really that most of my devices are accessed via their service and not directly. Their local IP is just so they have a path to the internet in order to call home. I can do this. -
Here to help so fire up your own threads with any sort of specific questions you have. Its best if your ? is specific to how to do X.. Or if a general question then put in the general section and say you have this and that, and what to accomplish X giving as much detail of the this and that as possible.
Then can discuss the best way to skin the cat to get you to your goal.
There really should be zero issues in isolating your iot devices on to their own segment. Problem with moving things to their own segment happen when whatever application or whatever you use to interact with them expect them to be on your typical home flat network everything on the same layer 2 and they use layer 2 discovery to find and talk to whatever else your wanting to do... Most smart home devices are not like that - and just want to get to the internet...
Where you might have problems is music related stuff, dlna stuff like a player and your plex server, etc. I have my plex box on different network than my roku player, etc.. But I allow roku device to talk to plex on 32400 so there is no issue.. They play everything direct and don't go through internet to stream stuff.
Yes it can be a bit of a learning curve - lots of help here.. Just ask!
-
Hey, Johnpoz? I started to think here. I have been doing networks for 20+ years, but only for myself (and friends and family), and I have never done anything which sounds like you are suggesting a bit up for the Opt1 plug. So let me get this straight: I have two separate networks, one private and one for somebody who rents 2/3 of my house. I'm 52, and my wife's 51, and our kids have moved out. So we only needed the small appartment in the house and prefer to let the main part of the house pay our mortgage. ;) What I have now is like this:
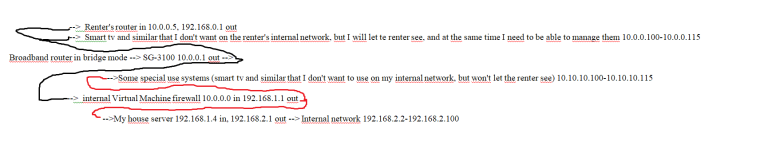
I hope that's understandable. I have used it this way so that I can go out from my router to mangage the renter's router, smart tv and stuff (which belongs to me, I rent it out with everything, and rent it to tourists in the summer) on the 10.0.0.x segment (the things are open for WAN managment, with extremely strong passwords). Would it be possible for me to use the Opt 1 for my own network, so I could drop the virtual machine firewall and have my 10.10.10.x segment there but STILL be able to log on to the 10.0.0.x segment from my opt 1 10.10.10.x segment? Please don't ask me to draw a flow chart, I'm hopeless with that stuff!

EDIT: Idiotic system on this board, I had to make a screenshot into a picture, it insisted on splitting what I had into different bits of code! Se picture at the bottom. Seems like the same system that the Home Assistant board is using, and I really, really, really hate it! ;)
-
Trying to make sense of that somewhat of a diagram?
You can create as many networks/vlans you want on the sg3100. Be using the opt1 as native or with vlans on it and then your 4 ports can all be broken up into individual networks.
Seems like your wanting to break up say a 10.10.10 network in ranges. But keep in mind you have all of rfc1918 space to deal with.... So keep your networks simple if you want to use 10.10.10, ok then create your other networks 10.10.11/24, 10.10.12/24 or 192.168.1/24 and 192.168.2/24
You can then isolate or control access in and out of these different networks via firewall rules on pfsense.
What switches do you have if anything? Do they support vlans? Can you not draw up how you have stuff connected currently? Here is a site you could use to do a network diagram.
https://www.draw.io/
-
Sorry I've been slow, but I've been fighting with my other system (I have one at my cabin and one at my house). In the house I have an Atom based pfSense, and I can't get it to port forward everything there! I have set up the NAT rule:
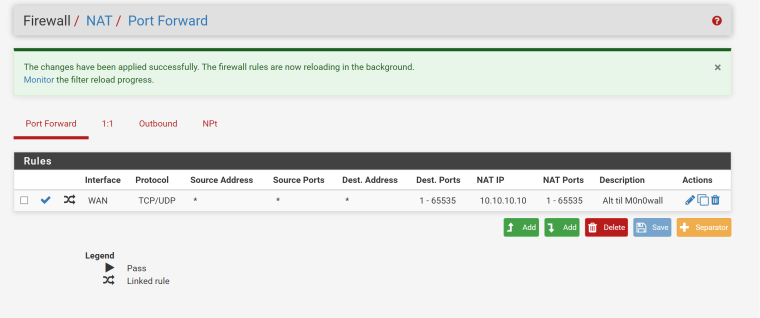
And the firewall rule should be there too:
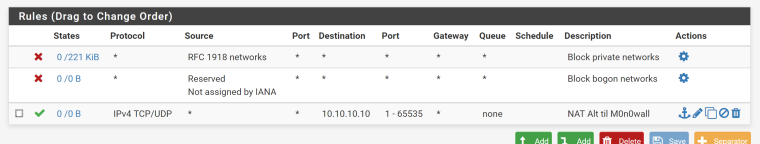
So shouldn't this have sendt eveything to 10.10.10.10? As it is nothing's going there. :(
-
I have tried 1:1 NAT too, but I guess I'm not doing that correctly either:
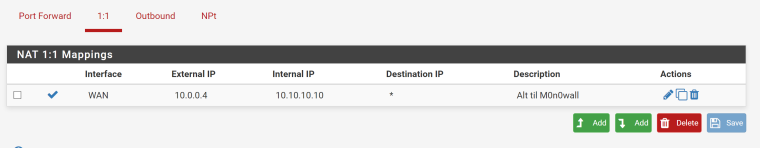
The .4 address is the WAN address of the system. I tried with .1 which is the adress of my modem (I haven't had a chance to bridge that yet), but it didn't change anything.
-
If your external address is rfc1918.. Means you have a nat in front - so you would have to forward it there first. Also out of the box pfsense blocks rfc1918 on its wan. So you would have to turn that off.
-
Thanks! That gave me the idea that solved it. I checked the broadband modem/router that was going to send it on to the pfSense, and it turned out that the damn thing had lost the DMZ settings when I changed the static IP from the old Asus router to the pfSense box (I had DMZ setup for the 10.0.0.4 IP address, but something must have happened, because that was wiped out)! So I spent the minutes it took and set the modem to bridge mode. That should prevent that ever happening again.