Time is not syncing
-
Boom THAT was why I had the manual NAT. Now my out-of-band management VLAN can get onto the internet and this violates DoD STIG requirements. THAT was why I was trying to keep the manual NAT. Again everything routes by default which creates THAT problem. I just need that network to be on its own separate from the rest of the networks. There are no rules on the ADMIN VLAN to allow anything so why am I able to route on the ADMIN VLAN. That was what I didn't want to do.
-
@brunovic said in Time is not syncing:
Boom THAT was why I had the manual NAT. Now my out-of-band management VLAN can get onto the internet and this violates DoD STIG requirements. THAT was why I was trying to keep the manual NAT. Again everything routes by default which creates THAT problem. I just need that network to be on its own separate from the rest of the networks. There are no rules on the ADMIN VLAN to allow anything so why am I able to route on the ADMIN VLAN. That was what I didn't want to do.
Because interface rules are checked in the inbound direction, not outbound. Through your lack of understanding of how pfSense works, you created the misconfiguration that allowed it to happen. You keep shooting your own feet and then wondering why it hurts.
You need to read through the docs more and understand how pfSense operates at a more fundamental level before ranting about how it doesn't work the way you expect. You're still applying Cisco concepts to pfSense when they do not apply at all.
-
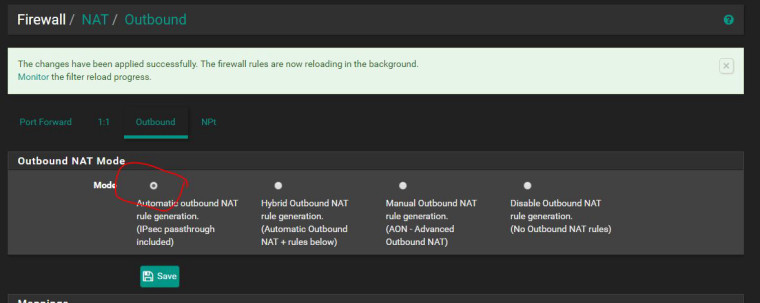
WITH Auto NAT:
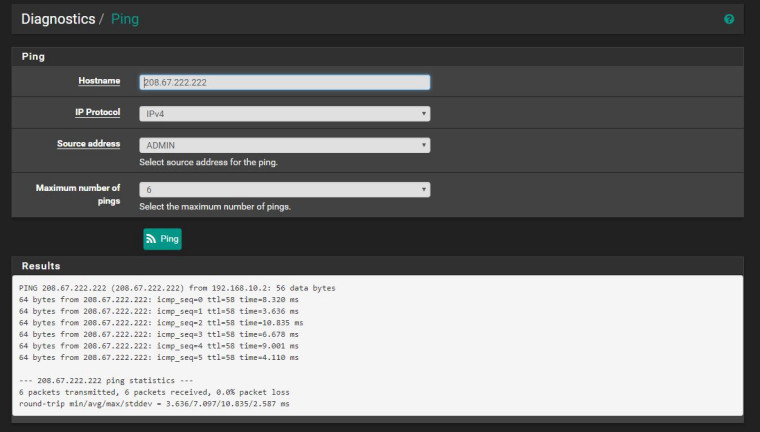
WITHOUT Auto NAT (Manual excluding the ADMIN network):
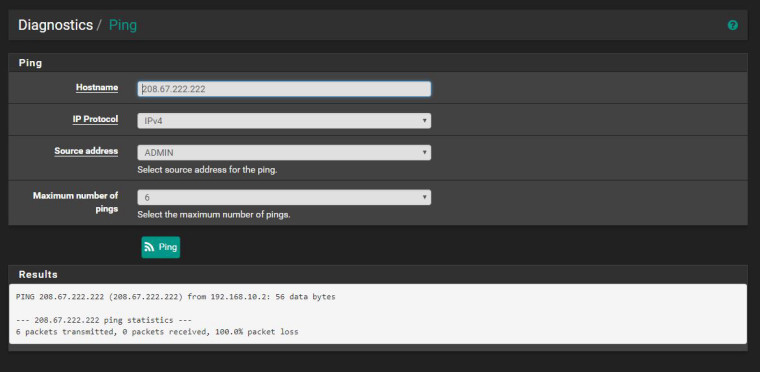
The second one is what I need to happen. There are no rules on the ADMIN VLAN however it is still able to route out.
-
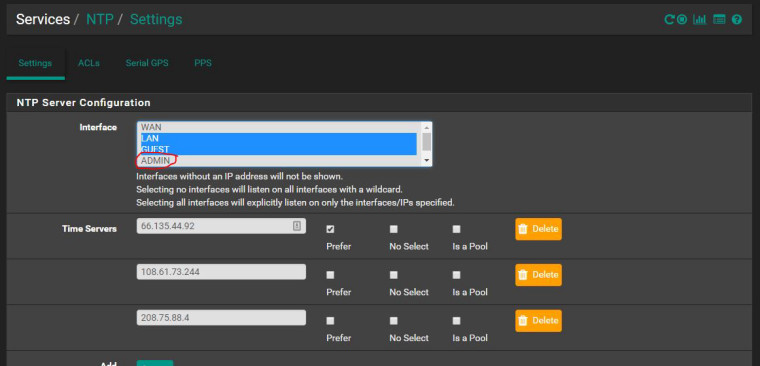
YOU GOT TO BE KIDDING! The simple answer was to NOT select the ADMIN interface under NTP settings! I didn't even select it but when I remembered why I did manual NAT I had a hunch that that was the problem. BECAUSE traffic cannot route out the ADMIN interface NTP failed! That makes absolutely NO sense!
-
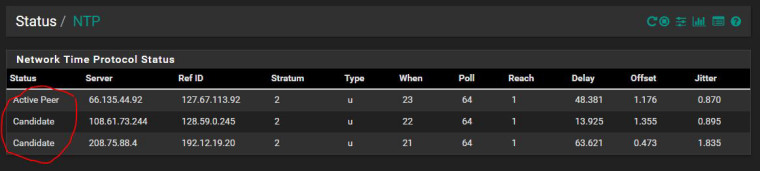
As you can see I've fixed it myself without your help. Instead of helping me you kept troubleshooting things that did not need troubleshooting. You kept arguing with me and would not listen to a word I said. I have said REPEATEDLY that NAT is not the problem because I was able to ping sourcing the LAN interface. You kept insisting it was the problem. I kept asking you HOW exactly the NTP client was reaching the NTP server. The best answer I got was that it was "listening" on those interfaces. That really does not help me out. If that is the case even IF the ADMIN interface which does not have a NAT rule was selected so was LAN and GUEST. So it should still have been able to reach the NTP server on those interfaces. I still do not understand WHY I need to remove the ADMIN interface in order for it to work and I doubt I will get a straight answer from you. But I needed to remove the ADMIN network from NAT because it was automatically routing traffic. This is why I brought up Cisco. NOT to show off but to give you a reference point of where I stand from a Network Engineer perspective. By default there are no routes when VTIs are created. That is what I was expecting from pfSense. Yes I know pfSense is NOT a Cisco device but I need THAT function to act like Cisco. Cisco has designed VLANs to be independent network FOR security reasons. To have automatic routing is a security vulnerability and I need for that to not happen. The ONLY work around I could find was to remove the NAT and make exclusion rule to segment off networks.
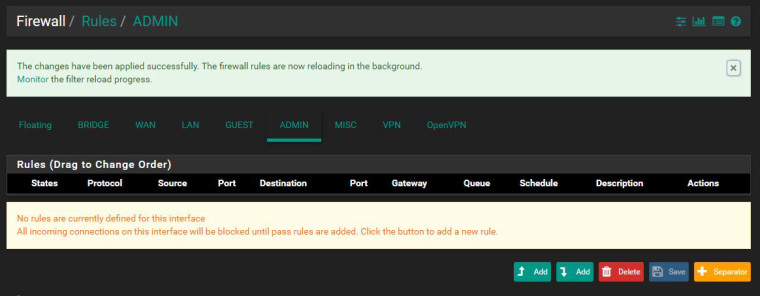
With ADMIN selected and Manual NAT:
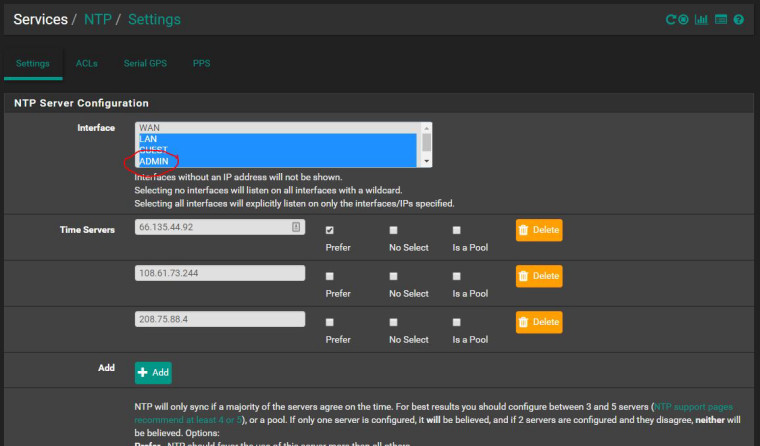
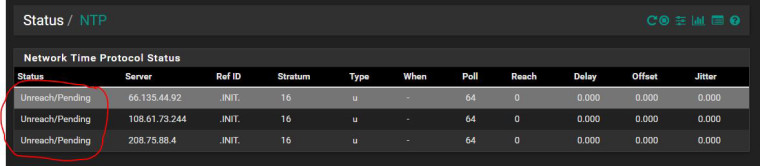
Without ADMIN selected and Manual NAT:
-
Good for you ;)
I am glad it got sorted, for sure gives me more things to ask the next user on stuff they could of dicked up.
I agree with jimp here - you shot yourself in the foot.. You should of mentioned out of the gate that you were not using a default gateway and not using automatic nat, etc.
Unless the user mentions it, you have to assume pfsense is in a default configuration mode.. So normally these threads come down to pulling the info out of the user and trying to figure out what thing did they dick with or multiple things to break it..
-
This is BS: https://youtu.be/FlVjrB4SByQ?t=2m18s
You are saying there is an implicit deny in this video. That said if there are no rules then I should NOT be able to route between VLANs. Is that my "lack of understanding" you are referring to? If that is the case with no rules on the ADMIN interface I should not have been able to ping out on the WAN much less any other local network. Let me show you something. I will add the auto NAT rules back in and remove ALL rule on the ADMIN network and show you that I am still able to ping out and internally. IF there is an implicit deny statement then I should not be able to do this right? Then why am I able to do this? Please don't come at me with that "lack of understanding" crap. Your own documentation and video contradict the results. What I do understand is what is happening on my pfSense. If rules are supposed to allow traffic then why is it when I have no rules traffic is still allowed. THAT is why I had to manually configure my NAT!
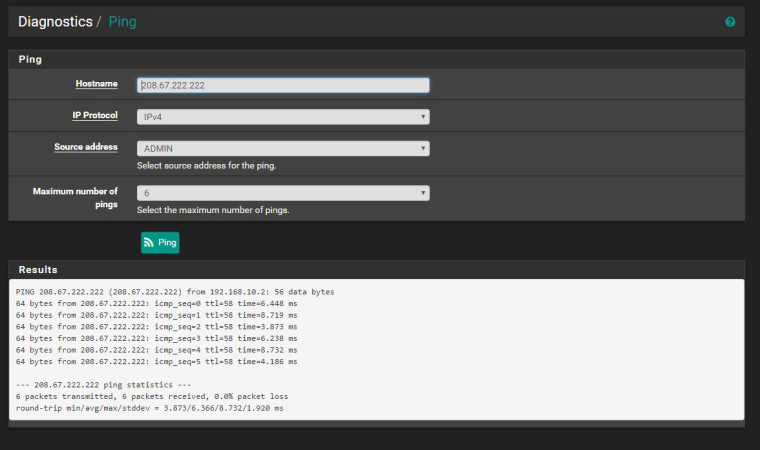
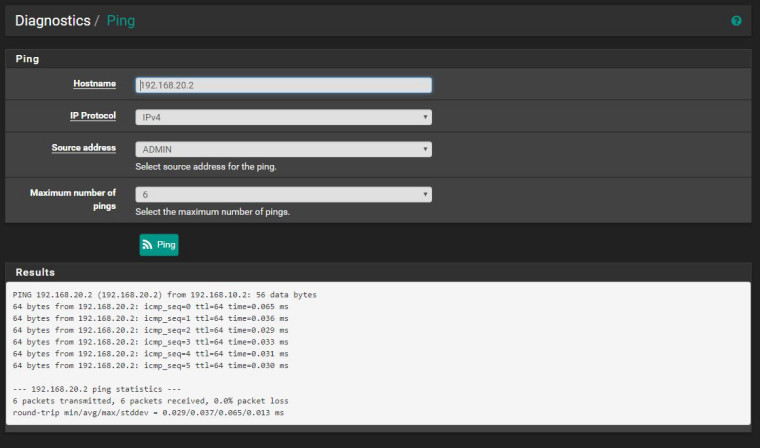
-
As you can see I’ve fixed it myself without your help.
Good for you.
Instead of helping me you kept troubleshooting things that did not need troubleshooting. You kept arguing with me and would not listen to a word I said.
Except that I did, and you assumed you were right and I was wrong and missed the point completely.
I have said REPEATEDLY that NAT is not the problem because I was able to ping sourcing the LAN interface. You kept insisting it was the problem.
Except NAT was the problem. See below.
I kept asking you HOW exactly the NTP client was reaching the NTP server. The best answer I got was that it was “listening” on those interfaces. That really does not help me out.
Except that it was the most correct answer to what you asked with the information you provided. You did not show your NTP settings anywhere. You did not mention any "admin" interface being selected in NTP, only LAN.
If that is the case even IF the ADMIN interface which does not have a NAT rule was selected so was LAN and GUEST.
The lack of NAT for admin was the problem because it chose the Admin interface as the source. With multiple interfaces selected the OS picks whichever interface is "closest" to the targets, for whatever reason, Admin came up first in that decision making process.
So it should still have been able to reach the NTP server on those interfaces.
Except that it didn't, the NTP daemon picked the Admin interface for whatever reason, and NTP apparently doesn't try other addresses automatically.
I still do not understand WHY I need to remove the ADMIN interface in order for it to work and I doubt I will get a straight answer from you.
Because ADMIN has no outbound NAT, and NTP is trying to communicate with the outside world using the Admin interface IP address.
But I needed to remove the ADMIN network from NAT because it was automatically routing traffic.
Wrong. Taking it out of NAT does not prevent it from routing. The traffic still exits WAN, just without NAT. You need proper firewall rules.
This is why I brought up Cisco. NOT to show off but to give you a reference point of where I stand from a Network Engineer perspective.
But as you have shown, that experience means little to anything other than Cisco.
By default there are no routes when VTIs are created. That is what I was expecting from pfSense.
By default in pfSense there are no rules when interfaces are created.
Yes I know pfSense is NOT a Cisco device but I need THAT function to act like Cisco. Cisco has designed VLANs to be independent network FOR security reasons. To have automatic routing is a security vulnerability and I need for that to not happen. The ONLY work around I could find was to remove the NAT and make exclusion rule to segment off networks.
Again, it works this way by default if you create a proper set of firewall rules. It isn't a security vulnerability, it's mismanagement by the admin.
-
@brunovic said in Time is not syncing:
This is BS: https://youtu.be/FlVjrB4SByQ?t=2m18s
You are saying there is an implicit deny in this video. That said if there are no rules then I should NOT be able to route between VLANs. Is that my "lack of understanding" you are referring to? If that is the case with no rules on the ADMIN interface I should not have been able to ping out on the WAN much less any other local network. Let me show you something. I will add the auto NAT rules back in and remove ALL rule on the ADMIN network and show you that I am still able to ping out and internally. IF there is an implicit deny statement then I should not be able to do this right? Then why am I able to do this? Please don't come at me with that "lack of understanding" crap. Your own documentation and video contradict the results. What I do understand is what is happening on my pfSense. If rules are supposed to allow traffic then why is it when I have no rules traffic is still allowed. THAT is why I had to manually configure my NAT!
Pinging from the firewall itself that traffic does not enter the interface and thus is not subjected to the rules on interface tabs.
Your testing is flawed, as is your understanding.
-
Locking this as it's gone completely off topic.