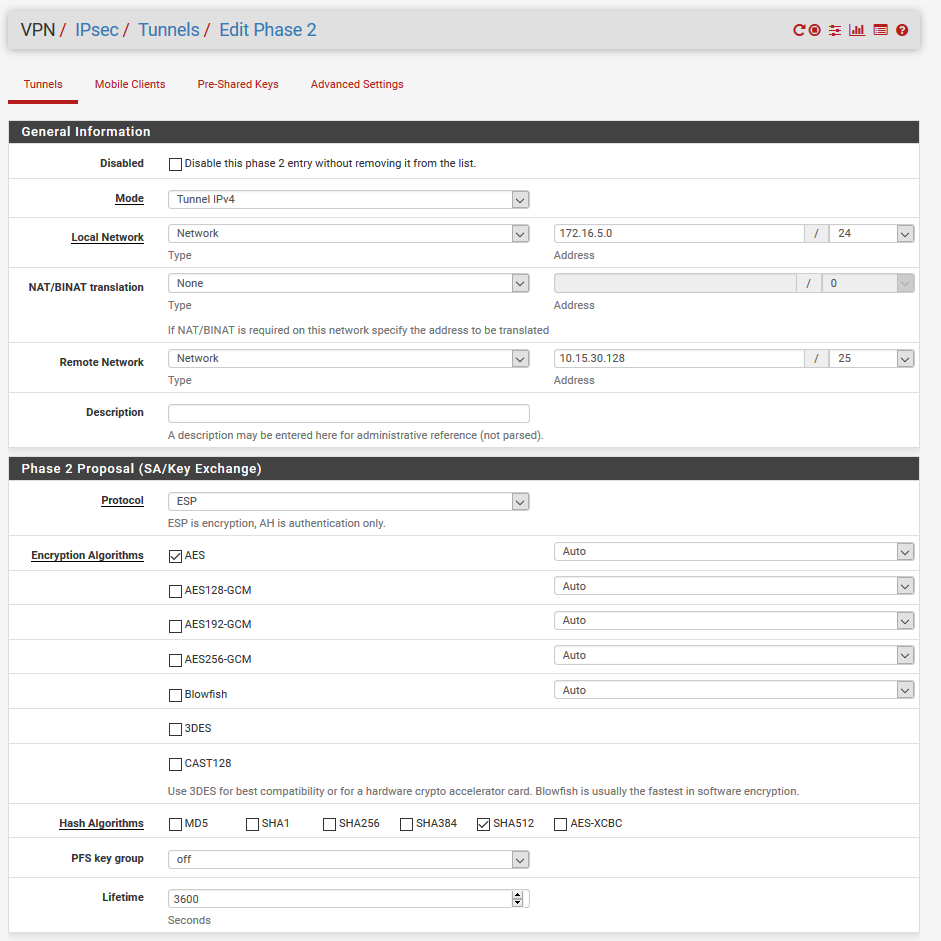
IPsec tunnel mode with ASR
-
Hello eveyrone,
I want to build a IPSec Tunnel with an ASR.
ASR router is configured with IPSec tunnel method (tunnel protection) because the tunnel has to be mounted from a specific VRF (so crypto map is not possible)
Here is the sanitized configuration of the ASR :
hostname ASR ! vrf definition INTERCO rd 10.107.254.18:1 ! address-family ipv4 route-target export 10.107.254.18:1 route-target import 10.107.254.18:1 exit-address-family ! ! crypto ikev2 proposal aes-cbc-256-proposal encryption aes-cbc-256 integrity sha512 group 24 ! crypto ikev2 policy policy_pfsense proposal aes-cbc-256-proposal ! crypto ikev2 keyring mykeys-pfsense peer pfsense address 5.5.5.6 pre-shared-key ########## ! crypto ikev2 profile pfsense description IKEv2 profile match identity remote address 5.5.5.6 255.255.255.255 identity local address 5.5.5.5 authentication remote pre-share authentication local pre-share keyring local mykeys-pfsense lifetime 3600 ! crypto ikev2 dpd 10 2 on-demand ! crypto logging ikev2 ! crypto ipsec transform-set ESP-AES256-SHA512 esp-aes 256 esp-sha512-hmac mode tunnel ! crypto ipsec profile pfsense set transform-set ESP-AES256-SHA512 set ikev2-profile pfsense ! interface Loopback1 vrf forwarding INTERCO ip address 10.15.30.140 255.255.255.128 ! interface Tunnel100 vrf forwarding INTERCO no ip address tunnel source GigabitEthernet2 tunnel destination 5.5.5.6 tunnel protection ipsec profile pfsense ! ! interface GigabitEthernet2 ip address 5.5.5.5 255.255.255.252 negotiation auto no mop enabled no mop sysid ! ! ! ip route vrf INTERCO 172.16.5.0 255.255.255.0 Tunnel100 ! line con 0 stopbits 1 line vty 0 4 login local transport input ssh endThe IPsec configuration of PfSense is in tunnel IPv4 and the local network is the LAN subnet (172.16.5.0/24) and the remote network is 10.15.30.128/25
In debug mode on the ASR, i have the error : "Failed to find a matching policy" and the IKEv2 SA is flapping between UP & DOWN...
If I disable the IPsec Phase 2 entrie on PfSense, the IKEv2 and the interface tunnel 100 on the ASR turns to UP.
I think it's because of the ACL sent by the Pfsense with the remote network and local network but i can't be sure of this...
With a crypto map, we can make matching the IPSec traffic to an ACL but how can we do the same thing with the tunnel profile method ?
Is anyone have an idea ? (or had already got the same problem ?)
If you need more informations, feel free to ask me ! ;)
Thanks to you !
Trif