IPSec phase2 problem - pfSense - Checkpoint
-
Dear all,
We have established a phase1 tunnel to a Checkpoint device.
The problem occurs when initiation QUICK_MODE or phase 2.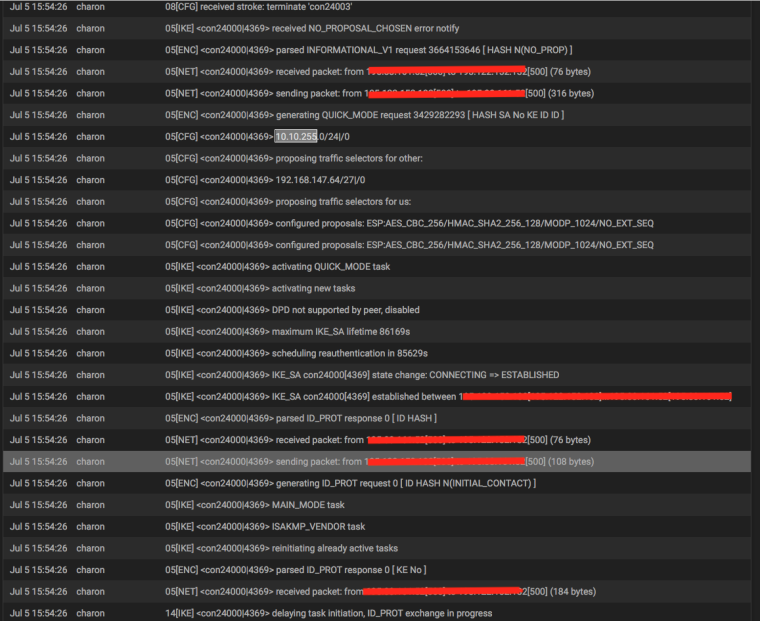
As seen in the logs the error is NO_PROPOSAL_CHOSEN and HASH N(NO_PROP).
We have tried symmetric configuration with all possible encryption and hash algorithms.
Is there maybe a vendor incompatibility here or just some algorithms are compatible between the two devices?
We are yousing pfSense 2.3.4-RELEASE-p1.
Miroslav.V.
-
Hello,
please double check the encryption parameters (AES, SHA, PFS).
Also please check the participating networks. They have to match exactly. Why is your subnet /24/0?!Is the checkpoint configured with "One VPN tunnel per subnet pair"?
-
Hello Bepo,
The solution to the problem was resolved by killing the IPsec service from terminal and starting it again.
All encryption parameters where always matching and in Checkpoint the configuration was all subnets on one VPN tunnel (one phase1 and many phase2).Why is your subnet /24/0?!
Do not know the reason why is it like that in system logs. On the configuration side only mask /24 was in use.
Evan when established the log is the same regarding subnet notation.
Thanks for the help!
-
Okay. Good to hear. Please mark the topic as resolved.
Kind regards
-
@Rosla said in IPSec phase2 problem - pfSense - Checkpoint:
killing the IPsec service from terminal
How to kill the IPsec service from terminal?
-
@mesibug, from terminal just type - ipsec stop to terminate service and ipsec start to initiate service.
-
Isn't the same achieved by stopping and starting IPSEC service with these functions?
and then Start Service.I've got a similar problem where the tunnels, a p1 and 2xp2, goes down after the p1 ttl reauth is happening. Driving me nuts! pfsense latest and greates and cisco asa... Kicking a own thread for this in a moment.
-
@iorx, it should do the same but in older versions of pfSenes i had trouble using it over GUI. I think it works now properly with 2.4.x.
Have you tried to set Automatically ping host in p2 Advanced Configuration? This setting has help me a lot in keeping the p2 tunnel always UP. -
Hi,
Didn't mean to hijack this thread with my issue. I found this which matches my problem, https://forum.netgate.com/topic/150126/masquerade-two-different-local-nets-into-ipsec-tunnel-solved
The other side is a cisco so ... trying out Split Connection (the logs indicates that something relay strange is going on reconnecting p2 after p1 has done a reauth) and wait it out 28800 seconds
And from the pf-docs,
Split Connections
(IKEv2 Only) When an IKEv2 tunnel has multiple Phase 2 definitions, some peer equipment does not properly handle how the traffic selectors are generated. This is especially common in Cisco equipment. Only check this option if the remote peer cannot properly negotiate in this situation. -
Hi ladies and germs.
Split Connection was the solution to my problems. IKE2, multiple phase 2 and Cisco ASA don't play well together (single phase 2 had no problems). Split Connection is what got my connection stable, 14h and counting now.A link from the pfsense UI to the docs or a hint in the description on the option that Cisco probably needs this when running multiple phase 2 had been very helpful and saved me a couple of hours.
Brgs,
