Problems with LDAP Authentication and cisco routing.
-
Good morning guys, I'm simulating a small network where a pfSense is implemented and the topology includes an internet link, a cisco router and an LDAP server (the pfsense is before the router, that is from the internet: link-pfsense-router) . In the Router there is NAT. There is also port redirection: ip nat inside source tcp 10.0.5.65 389 192.168.1.254 389. The problem is that authentication is not performed properly and I am sure that the LDAP configuration is correct, any suggestions?
Thanks everyone, greetings. -
@malad said in Problems with LDAP Authentication and cisco routing.:
Good morning guys, I'm simulating a small network where a pfSense is implemented and the topology includes an internet link, a cisco router and an LDAP server (the pfsense is before the router, that is from the internet: link-pfsense-router) . In the Router there is NAT. There is also port redirection: ip nat inside source tcp 10.0.5.65 389 192.168.1.254 389. The problem is that authentication is not performed properly and I am sure that the LDAP configuration is correct, any suggestions?
Thanks everyone, greetings.I add what the logs of the system indicate about the event:
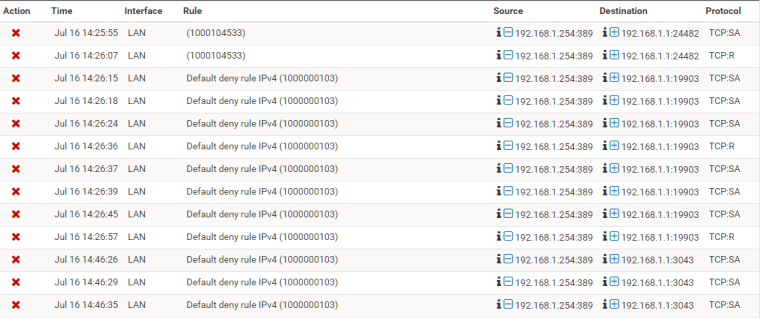
-
All of that traffic is out of state or R anyway.
Why are you trying to to port redirection?? Yeah that is normally going to cause all sorts of asymmetrical traffic if you do not source nat it as well.
I would suggest you draw up how you have this all connected and lay out how you think traffic should flow on this drawing.
-
Thank you very much for the answer, the following graph indicates the simulated topology: the red arrows indicate all the outgoing traffic (internet browsing), the blue arrows indicate the authentication of the vpn by LDAP against the AD server (Winserver) and the arrow black the incoming traffic of the vpn. Greetings.
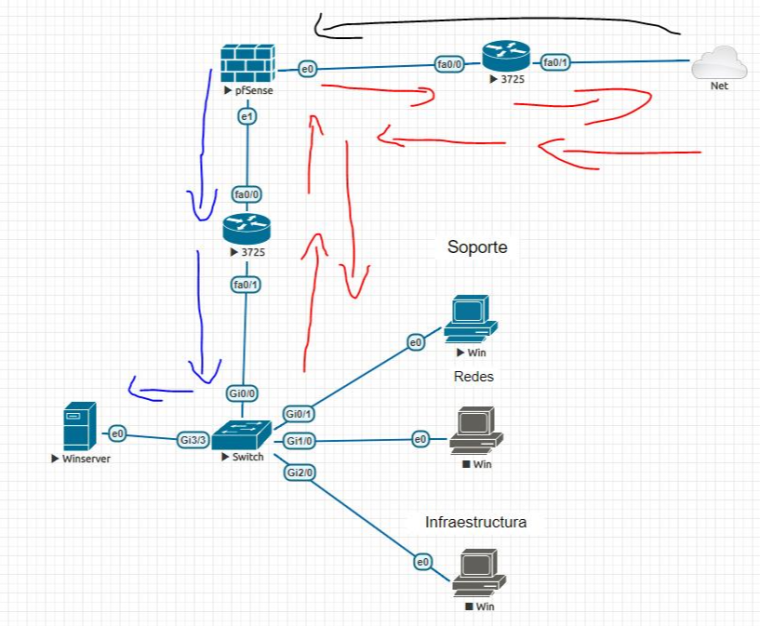
-
@malad said in Problems with LDAP Authentication and cisco routing.:
ip nat inside source tcp 10.0.5.65 389 192.168.1.254 389
where does that come into play?
What is the point of the router between pfsense and the switch? Seems pointless..
-
In the communication between the pfSense (fa 0/0: 192.168.1.254) and the Winserver server (e0: 10.0.5.65). In the cisco router there is a NAT applied, it is located there because it is a project and it is required that the sea works in that way, it can not be removed. Saludos.
-
Why would you nat? There is no reason to nat rfc1918 in such setup.
So pfsense wants to auth to your winserver.. He would send traffic to router IP on 192.168.1.254 and it would get forwarded to 10.0.5.65 by the router.
The SA would be answer to the Syn... It should not be blocked. Unless the traffic went out some other direction, etc.
-
If the NAT is removed from the router, the rest of the network below it can not exit to pfSense.
-
Thank you very much for your help, I already solved by removing the NAT. regards