Update from 2.3 to 2.4.2 Causes individual Phase 2's to not reconnect after IKE rekey
-
This is my frequent flier.
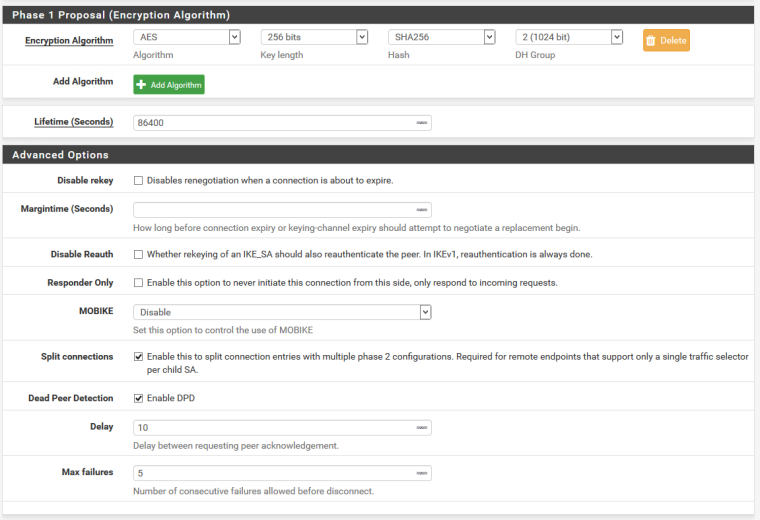
There are 4 identical P2's with the below config, but only one of them goes down. It's connected to a SonicWALL on the other side, and SonicWALL doesn't allow for separate P2 settings. Again, ran solidly for over a year on 2.3 with no config changes.
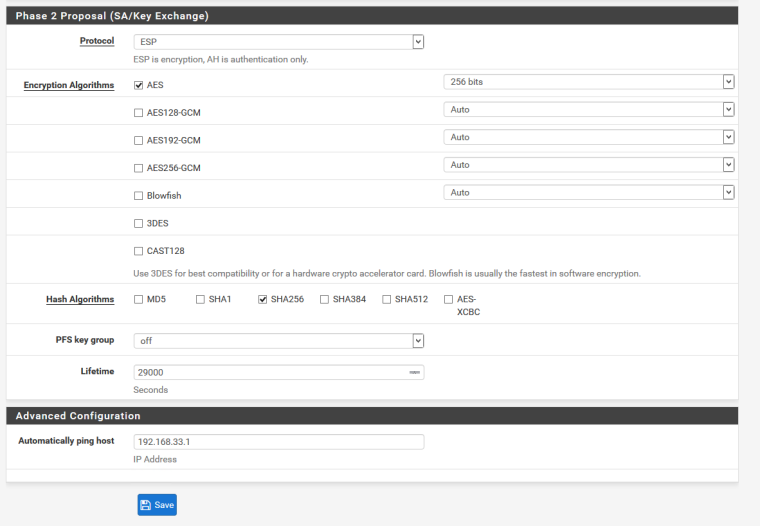
-
Were you able to resolve this problem? I am having what seems to be the same problem.
-
Nope. No resolution. So far, the best we’ve been able to do is change the P1 and P2 rekeys to 24 hours, try to keep them going during the day, and have a quick VPN setup on the Oncall person’s phone so they can disconnect the P1 real quick as soon as the alert comes in that the site is unreachable. Not a solution at all, and it’s driving me nuts while I’m Oncall. I guess this is what we get for using Community-based software and not paying for software support from Netgate...
-
Same here. I'm on version 2.4.3 and have an IPSEC VPN with 6 P2 with rekey lifetime of 1 hour and a P1 with rekey lifetime in 8 hours. I've noticed that even with P1 up, all hosts behind P2 network is offline. So I have to manually go to Status > IPSEC to disconnect and reconnect the P1 tunnel.
When this rekey occurs without monitoring, I've noticed that the tunnel is down for about 5-10 minutes and reconnects again. My other peer is a Checkpoint vendor. Any idea to keep all sessions behind a P2 tunnel?
Thanks
-
I upgraded to 2.4.3 just before you posted this response. I'm still having the problem. I did find a similar thread. here
-
I've definitely had that particular issue before. In this case now though, the Old P2's aren't hanging around. There's still only 1 P2, and that one only takes traffic one-way. It's really odd.
-
Does anyone have the same issue with Pfsense in both sides?
-
guys are you experiencing a similar issue to this that I am having?
https://forum.netgate.com/topic/132900/ipsec-phase-2-duplicate-causes-vpn-tunnel-to-get-stuck
-
leo.f - I haven't had the problem with any of my setups that have PFSense on both sides. Currently I have about a dozen sites that have IPSEC from PFSense to PFSense, and we've never seen the problem on any of those links.
Harow - I absolutely have seen that issue more than once, but so far, it hasn't actually impacted functioning. It just displays with tons of P2's but the primary P2 still functions fine. I always considered it a cosmetic GUI glitch.
-
@dkase279 mine prevents the tunnel from working as client machines can not ping through to my main site via the VPN. I'm going to log a call with Netgate if possible as it's preventing service. I also might put logs on here once it happens again.