Unable to access internal websites when connected through VPN behind pfSense
-
Hi,
Wondering if someone could help me here, I am fairly new to pfSense and working my way in setting this up.
I am running my own small domain at home and with a Windows Active Directory.
Here is my current configuration:
1 - Windows Active Directory with DNS and DHCP enabled (server A) - 10.100.1.1 (static)
2 - pfSense with DNS Resolve enabled (Server B) - 10.100.1.245 (static)
3 - Server with Tomcat running on port 7001 (server C) - 10.100.1.10 (static)
4 - Client System - dynamically assignedAll systems are part of Domain on server A.
On pfSense I have created a NAT and firewall rule to allow for port 7001 to be forwarded to server C. this works fine.On Server A I have DNS Forwarding pointing to pfSense and root hints turned off
DHCP Server is configured to give the following:
Gateway - 10.100.1.245
DNS - 10.100.1.1Everything is fine, and works as expected, the tomcat landing page can be accessed internally and externally over port 7001.
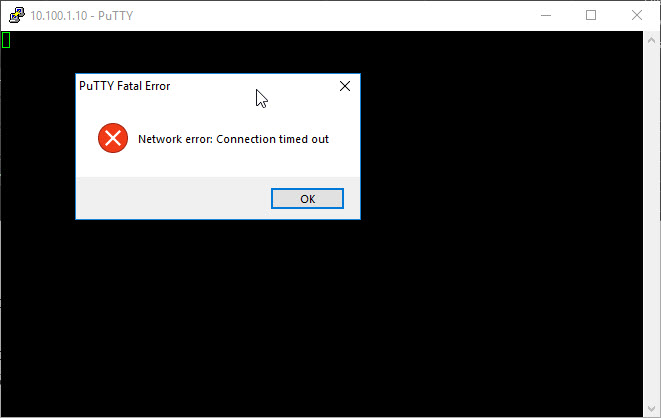
However when I connect to my works network using VPN (being behind pfsense), the website cannot be accessed the following is given:
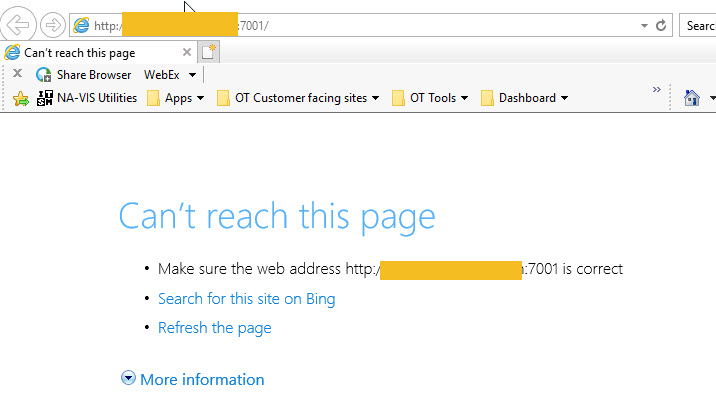
This was working fine with my old firewall\router.
Is there a setting in pfSense that I need to set?
The same issue occurs if I attempt to RDP to any of the severs (server A or server C)
Thanks in advance
-
@sunnyg One thought I have is that if you're using the resolver, your client is probably still trying to use your pfSense machine as its DNS server. If that's the case, you may need to add the IP address range assigned by your work's VPN to the resolver's access lists (Services > DNS Resolver > Access Lists). However, if you can access other sites normally (i.e. if you know that DNS is working), then disregard this advice :)
-
@thenarc
Hi, normal external sites can be accessed, such as youtube, microsoft, etc.it's just the one being hosted internally that cannot be accessed.
-
From your VPN client, can you telnet to the server by IP and port? E.g.,
telnet.exe 10.100.1.10 7001 -
-
So.... In your original post, the situation of not being able to connect to any internal servers only happens when you're connected to work's VPN.
I think this is by design. Enterprise VPN's typically isolate your VPN client to ONLY connect to work's network, and your local subnet will be inaccessible. The fact that it worked before just means that your VPN client used to be able to perform "split tunneling". But generally, enterprise VPN's disable this feature for security.
-
^ agreed most work vpns do not allow split, was your old network different address space. Possible your work vpn allowed you to split to access that specific address space.
-
Hi, not the old network had the same network address space. both internally and externally.
I have confirmed with our work VPN team that nothing has changed in the way that the VPN connection is made.
What's even more odd is that if I ping the external FDQN when connected to the VPN the packets respond back from the external IP address, so I am pretty that something on pfSense is blocking the request.
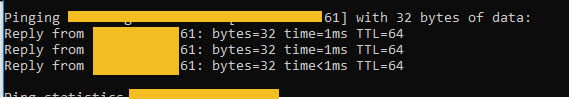
-
just occurred to me to try this but the pfsense web site is accessible both locally and using the external IP address while connected to the VPN
-
@sunnyg
"What's even more odd is that if I ping the external FDQN when connected to the VPN the packets respond back from the external IP address, so I am pretty that something on pfSense is blocking the request."If that's true, then while connected to VPN, you should be able to browse the FQDN (public IP) of your pfSense box on port 7001, and the target webserver should be there. Unless... your work firewall is blocking port 7001 outbound. Sounds like you'll have to choose... access your internal server or be connected to work (or use a different machine). It's pretty normal to not be able to do both.