Cannot get mobile IPSEC client to route over IPSec site-to-site tunnel
-
@jedblack said in Cannot get mobile IPSEC client to route over IPSec site-to-site tunnel:
I’ve opened up the WAN, LAN, and IPSEC interfaces with an ANY/ANY firewall rule.
Please immediately delete that pass any any rule on WAN. That has NOTHING to do with what is passed over an IPsec tunnel. Technical term for that rule is: "bad"
-
Yep, I should have mentioned that was deleted before I made this post. I just did it as a hail mary test since I can't see any issues.
-
Each side definitely needs phase 2 entries which include the other side's mobile tunnel network.
Each side needs rules on the IPsec tab passing traffic FROM the other side's mobile tunnel network.
-
Hey @Derelict – thanks for your help in this thread. Actually running into the identical issue here, but don't quite understand what the solution is here.
I've got a similar setup:
IPSec Mobile: 10.1.0.0/24
LAN1: 10.1.1.0/24...and multiple site-to-site VPNs configured from the pfSense to other appliances/AWS (which live at 10.2.1.0/24, 10.3.1.0/24, etc.)
For the life of me, can't get any IPSec Mobile clients to access any networks outside of LAN1 on the pfSense appliance itself. I also see the correct in/out SPDs for 10.1.0.0/24 <--> 0.0.0.0/24, and there are no firewall rules to my knowledge that could be intercepting this traffic.
Would appreciate any help!
-
@yuddu2md said in Cannot get mobile IPSEC client to route over IPSec site-to-site tunnel:
I also see the correct in/out SPDs for 10.1.0.0/24 <--> 0.0.0.0/24
0.0.0.0/24? or 0.0.0.0/0?
You might want to start nother thread with details about your specific issues.
-
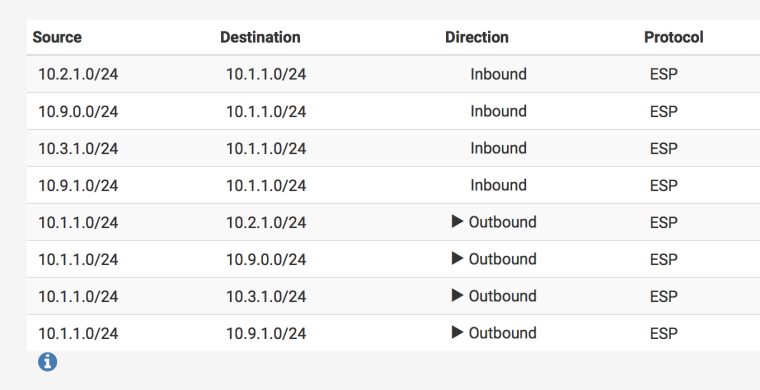
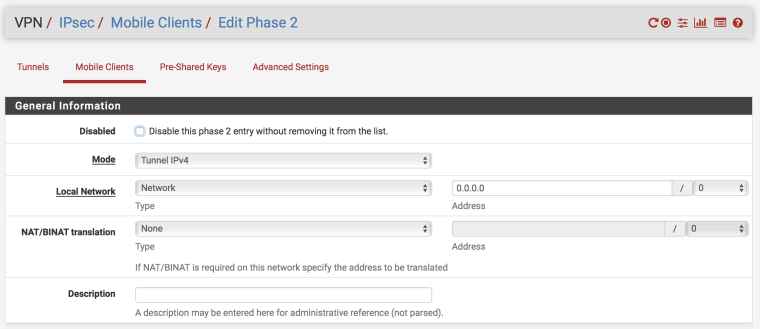
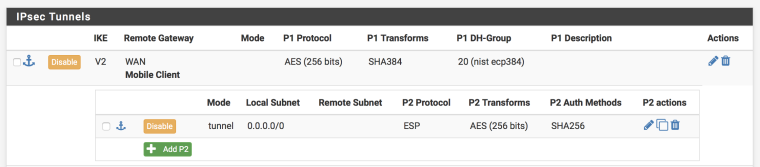
Err, sorry. It is indeed 0.0.0.0/0. Screenshots attached as well if they're helpful.
-
None of those traffic selectors will forward traffic between, for instance, 10.9.1.0/24 and the mobile clients at 10.1.0.0/24. They need to be told to send traffic destined for 10.1.0.0/24 to this firewall over the tunnel. The local subnet 10.1.1.0/24 does not need such a tunnel.
-
@Derelict Thank you and understood, but how do you achieve that with the IPSec Mobile Client setup? Doesn't seem to be an option to specify other subnets to clients / create tunnels across other subnets.
-
It is not a problem with the mobile IPsec, but with the other tunnels. They need a "Phase 2" that matches the traffic.
-
Bingo! That did the trick. Thank you :)