Can I hide/masquerade incoming IP?
-
I have an internal client with the following situation:
- Client has two interfaces: management (eth0) and data (eth1)
- Client routes all IP addresses on management network (192.168.123.0/24) to eth0
- Client default route is to a gateway (10.10.10.254) on data network (eth1)
- The gateway on the management network is 192.168.123.254
The problem is I want to ssh to the client via eth0. I have a port forwarding rule currently that lets me ssh from the outside. If I ssh from the inside on the management network then it works fine. But I can't ssh from outside because the client is set to route traffic to eth1 gateway by default. I can create a route for a specific external network but this is no good because ssh comes from multiple networks.
My questions are as follows:
- Is it possible for me to hide the IP of incoming connections so that it looks like it is coming from an internal IP on the management network, for example, the management gateway (192.168.123.254)?
- If not, is there a better way of doing what I am trying to do?
Thanks
-
What is the IP address you want to ssh from?
What is the address you want to ssh to.
You can almost certainly use outbound NAT to do what you want, but I can't make out exactly what that is.
-
The internal IP that I am wanting to ssh to is the IP of the client on the management interface, which is 192.168.123.81.
The address I want to ssh from could be anything. It is an external IP.
-
Then yeah. Set outbound NAT on the eth0 interface to a NAT address of eth0_address.
You can limit the rule to only destination address 192.168.123.81 port 22 if you like.
All connections to 192.168.123.81 would then appear to be sourced from 192.168.123.254.
NAT port forwards translate the destination. NAT Outbound translates the source.
You can add a free address on 192.168.123.0/24 as a Virtual IP address on eth0 and NAT the source address to that instead if you like.
-
@derelict Interesting. I thought that outbound NAT only dealt with traffic going out of the interface, not coming in.
Here is what I tried:
Interface: WAN
Source: any
Source Port: tcp/*
Destination: 192.168.123.81/32
Destination Port: tcp/22
NAT Address: 192.168.123.253/32
NAT Port: *
Static Port: checkThis doesn't appear to be working. When I attempt to ssh into the machine it is still using my client's IP address. Am I doing something wrong?
-
No idea what interface is what. Draw a network topology diagram.
-
Thanks for your help, here is a diagram.
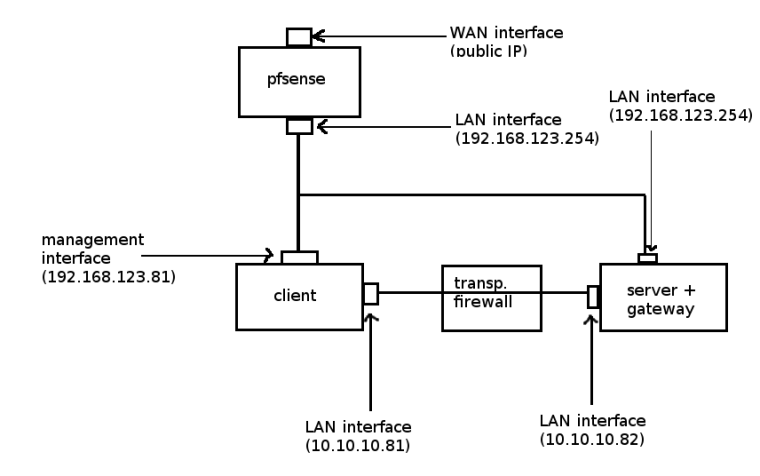
Traffic is routed to and from the internet through 192.168.123.254, the default gateway for most of the devices on my network. I realize that this diagram does not include vlans. The 192.168.123.0/24 subnet is for the management vlan. The 10.10.10.0/24 subnet is for the data vlan.For live traffic tests I want to route all traffic (except ssh) through the data vlan so that it can be scanned by the transparent firewall. So it goes through the firewall, to the gateway's data interface and then forwarded to 192.168.123.254 through the management interface to the Internet.
However for SSH I do not want this to go through the firewall at all, I want it to go through the gateway (192.168.123.254).
So here is what my routing table looks like on the client:
- default gateway is to 10.10.10.82 over eth1 (data interface)
- 192.168.123.0/24 is over eth0 (management interface)
- 10.10.10.0/24 is over eth1 (data interface)
The issue I am having is that it is still trying to route ssh traffic through 10.10.10.82 even though I created the outbound NAT rule above. Upon further investigation, the source IP for SSH traffic is not being translated at all; when I do a tcpdump on the client I can see it is still my original IP (I will call it 1.2.3.4). What I was hoping is that I could translate 1.2.3.4 to 192.168.123.253 so that the client would think this is the originating IP, and then route it to the management network, where the gateway would see it and know that it is intended for 1.2.3.4 and forward it accordingly.
I have researched other ways of doing what I want to do, including marking ssh connections and creating a table and route for those marked connections, but that did not work for me either.
Any help would be appreciated.
-
How do you have two interfaces both on 192.168.123.254?
That looks like an asymmetric nightmare.
-
@derelict Ooops my mistake. The server+gateway has the IP 192.168.123.82. Only the pfsense gateway has 192.168.123.254. Sorry for the typo.
-
Outbound NAT does not route traffic.
It only determines what NAT happens to traffic flowing out that interface when it is already routed that way.
@jusschwa said in Can I hide/masquerade incoming IP?:
So here is what my routing table looks like on the client:
- default gateway is to 10.10.10.82 over eth1 (data interface)
- 192.168.123.0/24 is over eth0 (management interface)
- 10.10.10.0/24 is over eth1 (data interface)
What is this client?
If that is its routing table and it is routing any traffic destined for 192.168.123.254 to 10.10.10.82 it is wrong.
Unless there is policy routing or something present outside the routing table you provided there routing that way.