DNS irrelevant with ATT Fiber?
-
@kom said in DNS irrelevant with ATT Fiber?:
How would we know what AT&T is doing? Run a DNS Leak test and see if it's reporting your ISP's DNS or what you specify. Is your WAN set by DHCP? If so, make sure you have WAN set to block DNS Server overrides in General setup.
https://www.dnsleaktest.com/
http://dnsleak.com/
https://ipleak.net/
The tests all show ATT:
Hostname: tukgav3dnsr77.infra.aic.att.net
ISP: AT&T Services -
You could try calling them and yelling at them to stop intercepting your DNS. I doubt they will listen since ISPs realized they could monetize DNS by injecting ads in nxdomain replies, for example.
Perhaps try forcing DNS over TLS to get around AT&T?
https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
-
@kom said in DNS irrelevant with ATT Fiber?:
How would we know what AT&T is doing? Run a DNS Leak test and see if it's reporting your ISP's DNS or what you specify. Is your WAN set by DHCP? If so, make sure you have WAN set to block DNS Server overrides in General setup.
https://www.dnsleaktest.com/
http://dnsleak.com/
https://ipleak.net/
In my General Setup, I have both boxes for DNS Server Override and Disable DNS Forwarder as unchecked
-
@kom said in DNS irrelevant with ATT Fiber?:
ou could try calling them and yelling at them to stop intercepting your DNS. I doubt they will listen since ISPs realized they could monetize DNS by injecting ads in nxdomain replies, for example.
Perhaps try forcing DNS over TLS to get around AT&T?I had bookmarked a similar article regarding using TLS... as I thought that might be a workaround. Guess I will give that a go
-
well.. that was simple. It looks to have worked! Is there any speed difference going over TLS?
res300.atl.rrdns.pch.net Cloudflare
-
Not that I know of. Have you noticed any delays when doing a lookup?
-
Initially Cloudflare seemed faster than ATT.. then I switched to Quad9 as I was interested in their additional (I believe) security.. and that seemed slower (and actually didn't resolve initially). I think I will have to use one for a while to see if I will chose speed over the additional security
-
@3dogs said in DNS irrelevant with ATT Fiber?:
well.. that was simple. It looks to have worked! Is there any speed difference going over TLS?
res300.atl.rrdns.pch.net Cloudflare
It seems fractionally slower to me for first lookup, but as pfSense will be caching responses anyway its not a major issue and WAY more secure as your ISP cannot snoop on what DNS lookups are being done.
There is one catch though, any device not using pfSense for DNS (Google love to do this on Android devices) will still be picked up by your ISP unless you add a firewall rule to force all DNS via pfSense (basically what your ISP is doing). https://www.netgate.com/docs/pfsense/dns/blocking-dns-queries-to-external-resolvers.html
-
Just a note that you can even simplify what they did in that article... they created two rules, one to allow DNS to your pfSense router, then one to block all others... it could be done in one rule, using most of the block all others settings, but instead of the destination being *, make the destination be "not LAN Interface" (check the box to invert, then select "LAN Interface" as the destination). This would allow DNS queries to your pfSense LAN interface, but anything else would be blocked.
Note that Reject might result in faster failover than block, as pfSense will send a message back that the connection is rejected, rather than the device needing to time out.
If you have multiple interfaces you want this applied to, you could create a floating rule using "This Firewall" instead of "LAN Interface" and select the interfaces you want it applied to in the rule. Floating rules are processed before interface-specific rules.
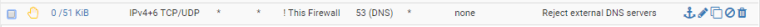
-
@virgiliomi Right, its how I did it actually using a different guide - that was just the first one that came up from a search.