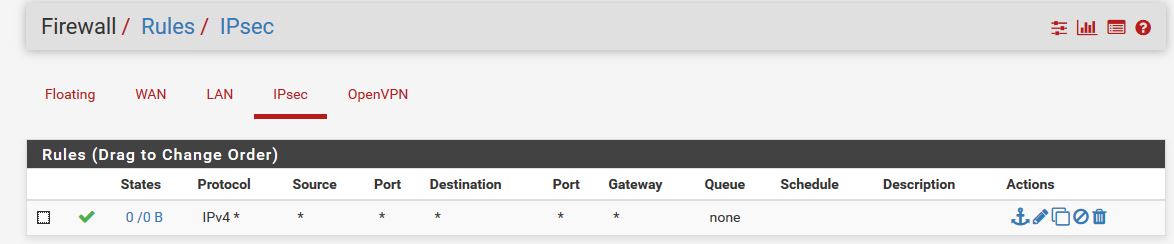
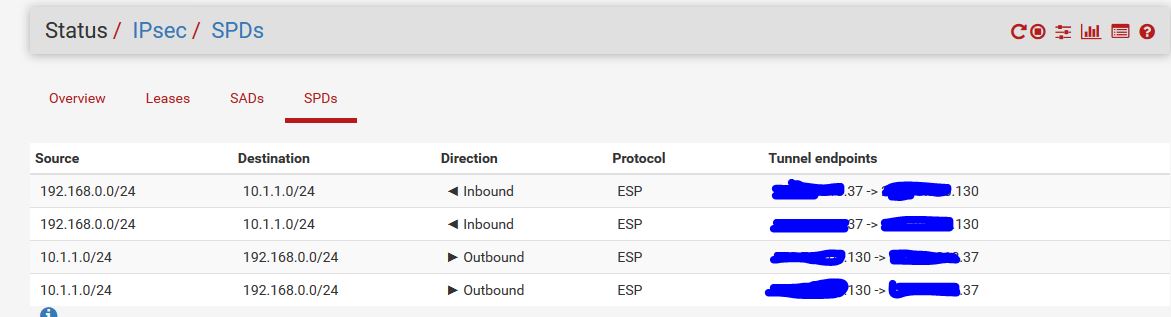
IPSEC to CradlePoint...Tunnel Established But No Ping
-
still trying to figure this out...
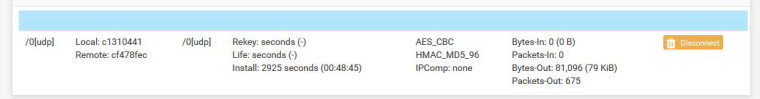
Can anybody tell me about the life vs install counter?:
-
First, uncheck Disable re-key on the Phase 1 and try again.
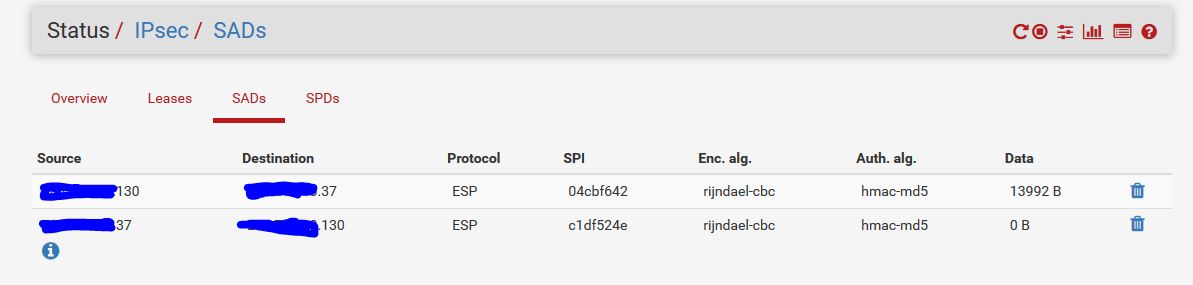
From those counters it's pretty obvious you are sending traffic out the tunnel but nothing is coming back.
-
@derelict, ok unchecked disable rekey.
Not sure why there was no inbound in that screenshot: There is now but still can't get a ping:
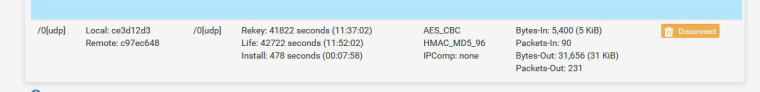
-
Exactly what are you pinging from where? IP addresses please.
-
the internal networks from both sides:
10.1.1.1 (pfsense lan ip) from 192.168.0.2 (cradlepoint lan ip) (and vice versa)
192.168.0.2 from 10.1.1.2 (server using pfsense as gateway) (and vice versa)
192.168.0.147 (static route added for 10.1.1.0 via 192.168.0.2) from 10.1.1.2 (and vice versa) -
Are you policy routing (gateways set on rules) on the 10.1.1.X interface?
If you are testing pings from the firewall are you positive you are sourcing from an interesting address/interface on the local side of the tunnel?
-
I'm not sure I know how to answer that...I'm not using VTI if that is what you mean. My assumption (forgive my limited knowledge) is that traffic will be routed over the tunnel based on the networks specified in the phase 2 parameters. Is this not correct? Let me put it this way...I've followed half a dozen pfsense standard tunnel ipsec tutorials looking for any steps related to routing that I may have missed and they are all the same...just getting the p1/p2 params to match and adding the rule to allow ipsec traffic.
I'm testing from everywhere. I did find a section in the pfsense book about adding a "fake" route and gateway for the sake of pinging right from pfsense, but that didn't help.
https://portal.pfsense.org/docs/book/ipsec/site-to-site.html#pfsense-initiated-traffic-and-ipsec
However, i continue to try from both the pfsense, cradlepoint, and other servers just to make sure it's not working in one place but not others.
-
Looking for the reason the traffic is going out WAN. In general that means:
- You are policy routing on the LAN interface so the traffic is being told to go a particular direction and is not caught by the IPsec traffic selectors.
- You are testing sourcing from an address that is not included in the traffic selectors. This is common when you use Diagnostics > Ping on the firewall and don't set LAN as the source interface, etc.
I am just going on what you said here:
One odd thing to me is that packet capture shows ping leaving WAN interface, instead of ipsec interface.
-
Yeah, that was probably before I understood the fluke with traffic originating from the pfsense itself (i only bought the gold/book today). I just ran another ping from a server and do see the traffic on the ipsec interface in the packet capture.
-
If there is no response you need to look at the other side.
-
yeah, i agree. I just discovered that the firmware upgrade on the cradlepoint gave me a similar packet capture functionality, and I can see the inbound ICMP packets.
Thank you much for helping me get this far.
-
ok, this is comical...deleted the tunnel off the cradelpoint, recreated it, and now it works. I know I've tried that before, but maybe, that in combination with the firmware upgrade fixed it.
-
Glad you got it working. Thanks for letting us know.