In a firewall rule, what is included in "LAN net" for IPv6?
-
@jimp What I ended up doing was a rule on the interface, that passed "any" to the link local multicast as destination. I used ff02::/16 which covers all of the Link-local multicast that I see on my net. Not sure about the other scopes yet. It would depend on what the router daemon does with them, but I would probably want to control them.
The issue I was running into, is that clients which do not use dhcp, use the multicast to do dns, look ups, etc. and that requires "fe80" addresses as source, and also I see "::" as a source address. Almost anything android based, behaves this way, since they don't support dhcp, but I also see it some on printers.
The router daemon is required to service those multicasts otherwise the protocol doesn't work. So I was seeing a lot of my devices falling back onto ipv4.
-
I did the same. Also for mDMS I created an extra rule.
-
@mrsunfire said in In a firewall rule, what is included in "LAN net" for IPv6?:
I did the same. Also for mDMS I created an extra rule.
It would probably be better, if there was a way to write a rule, that allowed multicast thru to the router daemon, which decides what to do with it, but not forward it out of the subnet. That is what I am not sure about. How to do that?
Really the router daemon should have its head out in the subnet before the firewall, servicing all of the multicast requests. But you probably would not want that on the WAN interface.
-
Thats the same I care about. Don‘t know if my solution is good or not. Right now it seens that there is nothing routet to WAN.
-
@jimp I know it has been a bit of time, but I have found one specific type of traffic, that maybe should be allowed in the default ruleset.
I am seeing traffic with a source address of :: (unspecified address) with a multicast to ff02::2.
Observing on Wireshark, what I am seeing is the network device is sending a multicast asking "who is the router" using the :: address as the source. If I create a easy pass rule in pfsense, I see the router respond with a router announcement. Otherwise it is default blocked and no response from router. The router does periodically give router announcements on its own.
I only see one device with this behavior, (Samsung TV) so not sure if this is something not normal, but it seems like it may be legal behavior.
-
@jimp I forgot to mention this is an ICMPv6 packet.

-
I can confirm this. My Samsung TV is doing the same think. If you block it, it doesn't use IPv6.
-
I had kind of ignored it for a while, assuming it was a Samsung peculiarity. But I checked the RFC 4861 - Neighbor Discovery in IPv6.
Par 4.1 Router Solicitation Message Format
IP Fields:
Source Address An IP address assigned to the sending interface, or the unspecified address if no address is assigned to the sending interface. Destination Address Typically the all-routers multicast address. -
After further checking I can confirm that Windows 10 does the same thing.
On power up, first thing it does is send icmpv6 multicast, from source address [::] to [ff02::2] (All routers on the local network segment). After that it uses its link local address as source for multicast.
So it is not just the Samsung.
-
Yeah reading through that RFC it does appear to need one more rule to allow from that.
I've got a commit coming that should fix it up in 2.4.4.
https://redmine.pfsense.org/issues/8791
You could make a manual and more specific rule to pass it than allowing
anysource, though: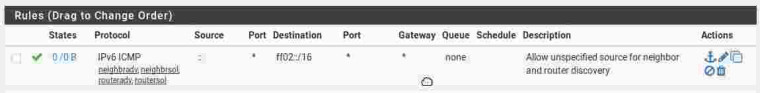
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
I am seeing traffic with a source address of :: (unspecified address) with a multicast to ff02::2.
That sort of packet shouldn't even be passed by pfSense, as it's intended to be for the local link only. Check the hop limit and you'll likely find it's 255. This value is used to ensure a packet has not passed through a router, as it would have been decremented from 0 and routers are supposed to discard any packet that has a hop limit of 0. And, a source address of :: or unspecified can never be a destination address, as it's only used by a device that doesn't yet know it's own address. So, you're looking at a packet that's intended to be used on the local network only and pfSense should not attempt to forward it.
-
@jimp said in In a firewall rule, what is included in "LAN net" for IPv6?:
I've got a commit coming that should fix it up in 2.4.4.
Why should a router or neighbour discovery ever be passed by psSense or any other router? Those are link local only functions. I'd seriously question that passes those off the local net.
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
Why should a router or neighbour discovery ever be passed by psSense or any other router? Those are link local only functions. I'd seriously question that passes those off the local net.
They need to be able to hit the firewall itself so the firewall can answer neighbor/router discovery queries from these clients. It's multicast so it's all local, won't leave its segment, but still valid for the firewall to pass.
-
I know why they're needed. However, I've been running IPv6 for over 8 years and this has never been an issue. I'll have to fire up Wireshark and try monitoring what happens with another computer.
BTW, I have a Samsung Blu-ray player that no longer connects to the Internet at all. They did something absolutely brilliant. When connecting to the Internet, one of the first things the player does is try to connect to a certain web site. Can't reach the site, no connection and it stops there. However, since that was set up, that site, along with many others, switched to https, which this player cannot handle. As I said, brilliant!
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
I know why they're needed. However, I've been running IPv6 for over 8 years and this has never been an issue. I'll have to fire up Wireshark and try monitoring what happens with another computer.
I've been running it for years as well without seeing this, but that doesn't make it invalid. It's valid per the RFC and certain (rare?) devices behave this way. There isn't a compelling reason to not allow the traffic. It won't be routed, it's only hitting the local segment.
-
@jimp said in In a firewall rule, what is included in "LAN net" for IPv6?:
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
I know why they're needed. However, I've been running IPv6 for over 8 years and this has never been an issue. I'll have to fire up Wireshark and try monitoring what happens with another computer.
I've been running it for years as well without seeing this, but that doesn't make it invalid. It's valid per the RFC and certain (rare?) devices behave this way. There isn't a compelling reason to not allow the traffic. It won't be routed, it's only hitting the local segment.
If you have been running dual stack then some ipv6 errors have been masked by falling back to IPv4.
In my mind I should only have to define a “pass” rule to allow traffic from one subnet to another.
The issue is that these rules are needed for services in the router to perform link local functions that are required by ipv6.
In this case the default rules are not there to allow the router internally to implement NDP on the local net so I am manually having to create pass rules to get them into the router.
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
I'll have to fire up Wireshark and try monitoring what happens with another computer.
I just did, with another computer running Linux. The first 3 packets were:
Neighbour solicitation for it's own link local address from ::, for duplicate address check (DAD)
Router solicitation, with link local address as source
Router advertisement from router to link local address.My question is why are those devices not doing a DAD to ensure they can use their address, as is required by the specs. Once a device passes DAD for it's link local address, it's free to use it, as shown in my test.
If a device is not doing DAD, it's defective. -
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
If you have been running dual stack then some ipv6 errors have been masked by falling back to IPv4.
What sort of errors? I just ran Wireshark filtering on the computer MAC address and ICMP6. No IPv4 involved at all. Incidentally, I've been running a browser add-in called "ShowIP" that shows the web site address, for years. If there was a problem, I'd have noticed it.
-
@jknott Your tests aren't going to tell us anything meaningful about how someone else's device behaves or should behave. Only how yours behave, which is not relevant to this discussion.
-
@jimp said in In a firewall rule, what is included in "LAN net" for IPv6?:
Your tests aren't going to tell us anything meaningful about how someone else's device behaves or should behave. Only how yours behave, which is not relevant to this discussion.
If a device doesn't do DAD, it's defective. Those other people should be running Wireshark to see exactly what's happening. Packet Capture can also be used, but it's not as useful as Wireshark.
I'm just getting set up to test a W10 computer, to see what happens with it.