In a firewall rule, what is included in "LAN net" for IPv6?
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
@jimp said in In a firewall rule, what is included in "LAN net" for IPv6?:
Except those packets won't make it to the stack to be processed if they are blocked by pf, hence the problem.
Are you suggesting pfSense is blocking ICMP to itself? That's guaranteed to break SLAAC etc..
Can you ping the pfSense device on either IPv4 or IPv6? Does SLAAC work on your network without rules passing ICMPv6?That is what I was observing and is the problem we are discussing.
In my opinion, if it is an internal service within pfsense, the user should not have to write a "pass" rule just to get it to the internal service within pfsense.
I, as a user, would not have anyway to know that it would go to pfsense only. I definitely would not want these packets to be forwarded on to other subnets because of my "pass" rule. Only the developers have this knowledge and should have it in the default rules.
-
@jimp said in In a firewall rule, what is included in "LAN net" for IPv6?:
That's the entire problem we've been actually discussing in this thread, which you seem to have missed entirely.
There is a default set of rules in pfSense to pass specific ICMPv6 packets at all times, for things like ND, RA, and so on. These are in place to ensure these features function properly even without a user adding rules to pass them. These rules did not pass from a source of :: to the multicast destination. I added a rule to pass them so it will work.As I mentioned above, I'd like to know what that TV is sending out. Does it correspond to what I'm seeing from Linux & Windows, that is DAD>RS>RA? Is that RS from :: valid? Is a router expected to send a RA when it doesn't have a valid RS source address? If so, where to? That info appears to be missing from the RFCs. I don't have the means to craft custom ICMP6 to test.
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
Those other people should be running Wireshark to see exactly what's happening. Packet Capture can also be used, but it's not as useful as Wireshark.
I just tried a capture with both. Packet Capture showed a total of 6 packets, compared to 9 with Wireshark. It also missed all 3 unspecified address DAD packets, including the one that preceded the RS. I'll have to try again after the new rules are available.
Since it appears pfSense is also missing the DAD packets, that could cause problems on a network with multiple routers, as each pfSense router will try to have a link local address of fe80::1:1 and not see the others when it runs DAD.
-
@jknott Periodically, the Samsung will send out:
ICMPv6 Src :: -> Dst ff02::2 Router Solicitation
If I have aforementioned pass rule, then pfsense immediately responds with a router advertisement icmpv6 packet
ICMPv6 Src fe80::1:1 -> Dst ff02::1 Router Advertisement
if not pass rule, pfsense doesn't respond in a timely manner, but maybe later on its own schedule.
-
I have seen Windows 10 do the same behavior at initial start up. But you have to be looking for it.
Samsung is more a Chatty Cathy, sort of like it has amnesia and forgets who and where it is.
-
@jknott On a related, but separate issue, I have noticed the same thing with other multicast, where pfsense should respond.
I have the Avahi package installed, and I see that the ipv6 multicast, ff02::fb (multicast DNS) is being blocked.
If I write a pass rule, I can see the pfsense respond with a DNS response, but otherwise it doesn't respond. So what happens then, is that the net device falls back to ipv4 multicast DNS and gets a response from pfsense via ipv4.
IPv6 uses link local (fe80::) and multicast for a LOT of the housekeeping activities on a link, and the pfsense in some cases is not participating until I write a "pass" rule to allow link local to multicast rule.
I would prefer not to do that since I worry that something could get passed on to other subnets inadvertently.
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
ICMPv6 Src :: -> Dst ff02::2 Router Solicitation
What does the source address show? You'll need Wireshark to see that. You can download the Packet Capture capture file to view it in Wireshark.
-
I just tried adding that rule and capturing the traffic as the test computer boots up. Wireshark shows the same as before, but Packet Capture now shows 14 packets captured, but none of them are DAD. Something strange is going on here. Packet Capture is running on the pfSense firewall and Wireshark on a computer connected via a managed switch, configured to mirror the traffic.
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
ICMPv6 Src :: -> Dst ff02::2 Router Solicitation
What does the source address show? You'll need Wireshark to see that. You can download the Packet Capture capture file to view it in Wireshark.
I am seeing on Wireshark, that the source address is ::
it is coming from the Samsung Mac address. -
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
I am seeing on Wireshark, that the source address is ::
it is coming from the Samsung Mac address.So, that brings us back to whether it's appropriate to use an unspecified address with a RS. Does it generate a RA when that rule is added? If so, what's the destination address?
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
I just tried adding that rule and capturing the traffic as the test computer boots up. Wireshark shows the same as before, but Packet Capture now shows 14 packets captured, but none of them are DAD. Something strange is going on here. Packet Capture is running on the pfSense firewall and Wireshark on a computer connected via a managed switch, configured to mirror the traffic.
What I use for testing, is a "pass" rule, IPv6 "any" to "ff02::0/16"
Then if you use Wireshark, you will see pfsense participating more on the link.
When you disable the rule, not so much pfsense. Also, a lot of the traffic gets repeated, trying to find the router.
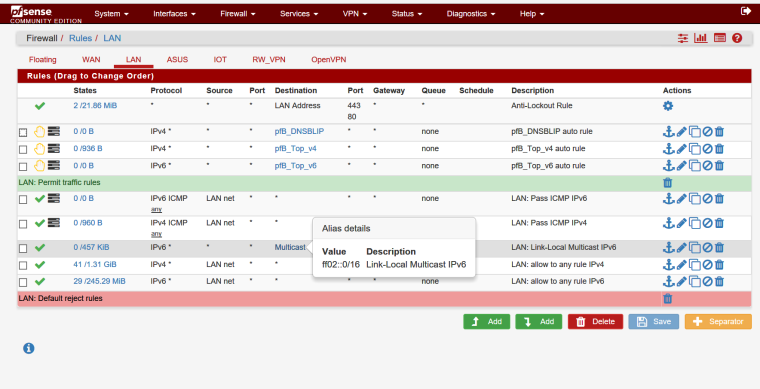
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
ff02::0/16
I am getting more, just not the DAD. BTW, there's no difference between ff02::/16 and ff02::0/16. The :: simply means a string of 0 bits in the area specified.
When pfSense is updated to include the rule, they should test to make sure it is working properly. There shouldn't be any difference between PC and Wireshark.
-
@jknott said in In a firewall rule, what is included in "LAN net" for IPv6?:
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
ff02::0/16
I am getting more, just not the DAD. BTW, there's no difference between ff02::/16 and ff02::0/16. The :: simply means a string of 0 bits in the area specified.
yeah, I had been trying more restrictive multicast addresses in my alias as part of my testing,
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
I am seeing on Wireshark, that the source address is ::
it is coming from the Samsung Mac address.Does it also show a DAD? It's supposed to be all but mandatory. Here's what RFC 4862 says:
"5.4. Duplicate Address Detection
Duplicate Address Detection MUST be performed on all unicast
addresses prior to assigning them to an interface, regardless of
whether they are obtained through stateless autoconfiguration,
DHCPv6, or manual configuration, with the following exceptions:-
An interface whose DupAddrDetectTransmits variable is set to zero
does not perform Duplicate Address Detection. -
Duplicate Address Detection MUST NOT be performed on anycast
addresses (note that anycast addresses cannot syntactically be
distinguished from unicast addresses). -
Each individual unicast address SHOULD be tested for uniqueness.
Note that there are implementations deployed that only perform
Duplicate Address Detection for the link-local address and skip
the test for the global address that uses the same interface
identifier as that of the link-local address." ...
I doubt a TV would have that variable set to 0
-
-
@jknott If I unplug the tv then back on, I see all what you are describing.
Once it is operating normally. I will see about every minute and a half I see about 6 or 7 ICMPv6 packets between the Samsung and pfSense:
Samsung sends:
[::] to [ff02::2] Length 63 Router Solicitationpfsense responds:
[fe80::1:1] to [ff02::1] Length 198 Router Advertisement (includes prefix, domain, DNS, etc.)Samsung responds with 2 packets, using it's link local address:
[fe80::56bd:79ff:fe17:54b] to [ff02::16] Length 90 Multicast Listener Report Message v2pfsense responds:
[fe80:1:1] to [ff02::16] Length 90 Multicast Listener Report Message v2That is the only time I see the [::] used as a source address.
It is some sort of joining a multicast conversation. -
@isaacfl I mistyped the record length above 63 should be 62.
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
Once it is operating normally. I will see about every minute and a half I see about 6 or 7 ICMPv6 packets between the Samsung and pfSense:
You'd normally see DAD when a device first connects to a network, such as when powering up. Once it's verified the address, it won't need to do it again. Also, watch for it with Wireshark, as Packet Capture seems to miss DAD, even with that rule change. Still I don't understand why it would use :: after it's up & running. That sounds to me like a problem with that TV. It shouldn't be using the unspecified address when it knows it has a valid address, as it uses with those multicast listener reports. I also see pfSense is sending the RA to the all nodes address, as the RS doesn't contain a valid source address.
Based on what you've described, there is definitely a problem with that TV. Maybe you could contact Samsung and provide them with the info, including the stuff in the RFC. You'll likely have to escalate as first level support is unlikely to have a clue.
I've had to contact manufacturers a few times about a problem. It can take a fair bit of effort to reach the right person. On one occasion, many years ago, I found a bug in the Western Digital 8250 UART, which was used in the original IBM PC serial ports. After reaching an engineer, they verified I had found a bug that they were unaware of. There have also been a couple of times when I had to escalate problems with my ISP/cable provider, as the problem was well beyond what the first level support could even understand. I feel sorry for ordinary customers, who don't have the technical background I have, that would enable them to push a problem through to the right person.
-
@jknott I have looked at the RFC 4861, and it says it is ok to use :: as the source address in a router solicitation.
RFC 4861 page 49:
"Router Solicitations in which the Source Address is the unspecified
address MUST NOT update the router's Neighbor Cache; solicitations
with a proper source address update the Neighbor Cache …"So it is a router solicitation without updating the neighbor cache on the router.
-
@isaacfl said in In a firewall rule, what is included in "LAN net" for IPv6?:
So it is a router solicitation without updating the neighbor cache on the router.
The question is why is that TV doing that? It should not be using the unspecified address for router solicitations. The reason why the cache is not updated is because that RS does not contain a valid address.
Can you upload a Wireshark, not Packet Capture, capture from boot up to after it stabilizes? I'd like to examine the entire sequence. If it's as bad as it sounds, you should be complaining to Samsung about their defective gear. This sounds about as brilliant as my Samsung Blu-ray player that no longer connects to the Internet.
-
@jimp This seems to have fixed my Android device as well. Before upgrade to 2.4.4, I was unable to have v6 running on my network because it would cause my cellphone to constantly drop it's WiFi connection because it though that it didn't have an Internet connection. After the upgrade, it works perfectly.