1:1 NAT not working. Replacing Checkpoint with Pfsense
-
@Derelict The DMZ network is 128.50.0.0/16. Should I change it to class C IP address for the NAt to work?
-
No, it doesn't matter, but those are not private addresses, they are assigned to the United States Department of Defense.
https://en.wikipedia.org/wiki/Private_network
-
Why in the world would of used 128.50?? Clearly those are NOT yours... And a /16 - so 65k some hosts?
Just at a loss here. Yes you should fix it - you should use rfc1918 space - what its designed for.. And you should use an appropriate sized network.. If for no other reason you don't look like an idiot next time you have a question and post up your details..
-
@johnpoz It is still in my private network. How is that going to affect the NAT?
-
It is not private address space.. Its owned by the DOD..
NetRange: 128.50.0.0 - 128.50.255.255
CIDR: 128.50.0.0/16
Organization: Department of Defense (DEPART)Sure you can technically use it - as long as you don't want any of those devices to talk to or get talked to by that network.. It just clearly points out to anyone that learns it that you don't understand even basic principles..
-
@johnpoz Thank you for the reply. I will change it.
-
Hello,
I got a break through. I changed the DMZ IP to 10.50.20.0/25. I NATted it to the DMZ server, Now I get connection refused error and not connection timed out error. I think the firewall is not letting the connection through.
-
Why are you hiding your 10.50 address? /25 - so you go from a /16 to a /25... Ok Sure you didn't mess up something in the mask?
Firewall would not send a RST or anything if it was blocking it.. Unless you setup a specific REJECT rule.. So sounds more like your end box at 10.50.x.x you know that super secret rfc1918 address that nobody can know ;)
Simple sniff shows you if pfsense sends on the traffic to end device.
-
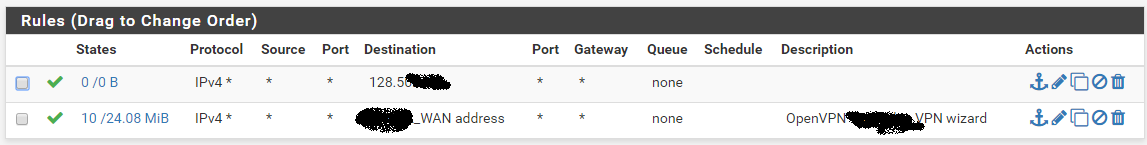
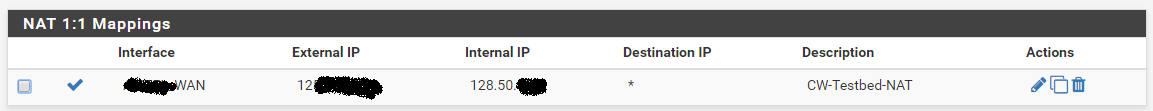
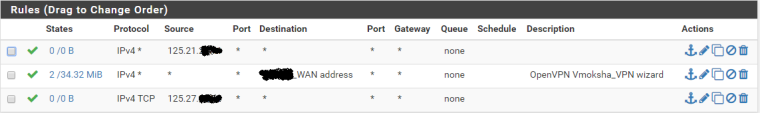
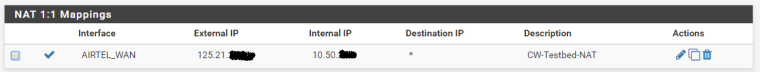
Alright, As you see the public ip is NATed to the DMZ server. Public IP : 125.21.XX.XX DMZ server IP : 10.50.20.3.
NAT 1:1 MappingInterface : WAN
External IP : 125.21.xx.xx
Internal IP : 10.50.20.3WAN Rules
Protocol : IPV4
Source : 125.21.xx.xx
port : Any
Destination : Any.Now the error is connection refused, Earlier it was connection timed out.
-
You are never going to have traffic into WAN sourced from an IP address on the WAN interface. The firewall rule should be sourced (presumably) from any which is any host on the internet.
The destination address should be the post-NAT real address of the destination server, or 10.50.masked.masked.
-
You can for sure limit the source to your actual source out on the internet to get to this host your sending the nat too.. But if your putting in your actual wan IP, then as Derelict has stated - that is never going to work.