DNSBL modify default bloked webpage
-
@ronpfs said in DNSBL modify default bloked webpage:
@occamsrazor Under Firewall / NAT / Port Forward You should have NAT entries pointing to the VIP.
Did you enable Permit Firewall Rules under Firewall / pfBlockerNG / DNSBL ? Do you see those Rules under Firewall / Rules
That check box was not enabled. I've enabled it now, restarted router and client machine, and see the rules under Floating:
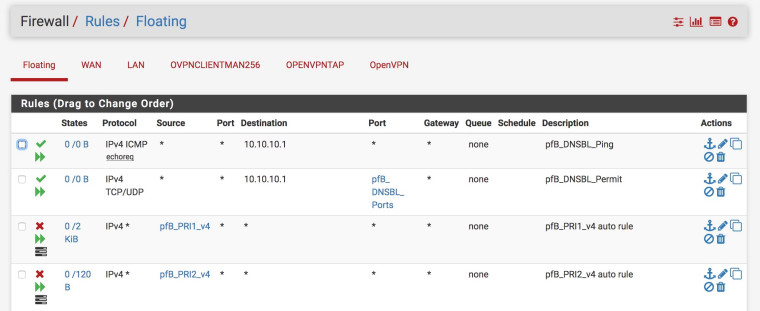
But still don't get any response from http://10.10.10.1/ or that domain you posted.
-
Aha... I notice the pfB_DNSBL_Ports alias refers to ports 8081 and 8043 only. When I type http://10.10.10.1:8081/ in the browser I get a response:
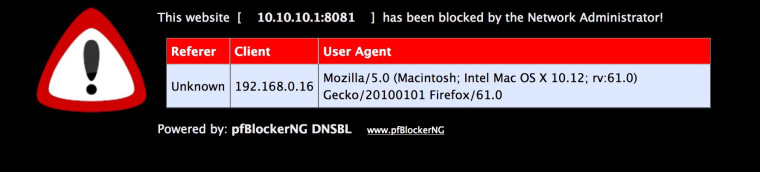
But even if I manually add port 80 to the pfB_DNSBL_Ports alias it doesn't give me that page when going to http://10.10.10.1
-
@occamsrazor The NAT should take care of redirecting port 80 and 443.
-
@ronpfs said in DNSBL modify default bloked webpage:
@occamsrazor The NAT should take care of redirecting port 80 and 443.
I see a corresponding port-forward in Firewall > NAT Port > Forward but it doesn't seem to be working:
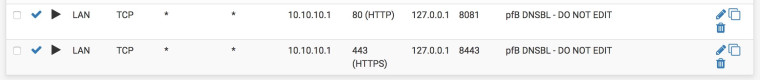
-
Make sure that your LAN devices DNS settings are only set to pfSense, and not any other DNS server or else that will bypass DNSBL.
-
@bbcan177 said in DNSBL modify default bloked webpage:
Make sure that your LAN devices DNS settings are only set to pfSense, and not any other DNS server or else that will bypass DNSBL.
They all use pfsense as DNS server (Resolver with forwarding) and I have rule to block DNS going elsewhere:
DHCP Server DNS settings:
Redirect any other DNS requests to pfSense
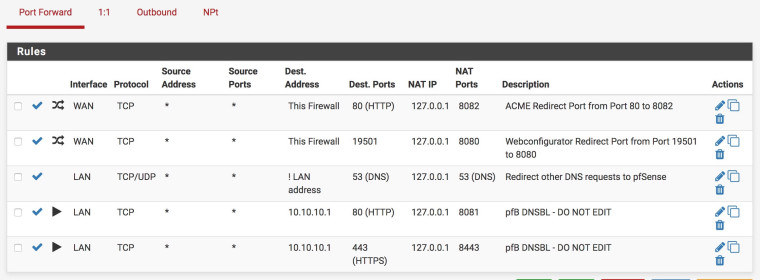
NAT settings
LAN Rules
The things is DNSBL IS working.... as bad domains are resolving to 10.10.10.1 in terms of DNS - it's just I am not getting the redirect webpage at 10.10.10.1
-
@occamsrazor said in DNSBL modify default bloked webpage:
The things is DNSBL IS working.... as bad domains are resolving to 10.10.10.1 in terms of DNS - it's just I am not getting the redirect webpage at 10.10.10.1
That blocked page only shows when the root domain is blocked. It won't show when it blocks an AD or a sub-domain.
-
@bbcan177 said in DNSBL modify default bloked webpage:
That blocked page only shows when the root domain is blocked. It won't show when it blocks an AD or a sub-domain.
If we take the example RonPfs gave above, if I do a ping I get this, which would indicate DNSBL is working:
BenMBPwifi:~ ben$ ping agkn.com
PING agkn.com (10.10.10.1): 56 data bytes
64 bytes from 10.10.10.1: icmp_seq=0 ttl=64 time=44.806 ms
64 bytes from 10.10.10.1: icmp_seq=1 ttl=64 time=1.503 msBut when I go to http://agkn.com I just get a timeout. It's not a big deal as DNSBL is working, just strange I never, ever see that page. I should add I have TLD enabled, though I didn't before and also never saw that block page.
-
@occamsrazor said in DNSBL modify default bloked webpage:
But when I go to http://agkn.com I just get a timeout. It's not a big deal as DNSBL is working, just strange I never, ever see that page. I should add I have TLD enabled, though I didn't before and also never saw that block page.
Is that domain in a blacklist?
grep "agkn.com" /var/db/pfblockerng/dnsbl/*
As a test, try to browse to "101com.com"
-
@bbcan177 said in DNSBL modify default bloked webpage:
Is that domain in a blacklist?
Yes it is...
Shell Output - grep "agkn.com" /var/db/pfblockerng/dnsbl/* /var/db/pfblockerng/dnsbl/EasyPrivacy.txt:local-data: "agkn.com 60 IN A 10.10.10.1"As a test, try to browse to "101com.com"
Shell Output - grep "101com.com" /var/db/pfblockerng/dnsbl/* /var/db/pfblockerng/dnsbl/MVPS.txt:local-data: "wtrs.101com.com 60 IN A 10.10.10.1"Seems 101com.com isn't in my blocklists but wtrs.101com.com is.
When I ping 101com.com I get a real IP, when I ping wtrs.101com.com I get 10.10.10.1
When I browse to wtrs.101com.com I get a timeout, when I browse to 101com.com I get through to some server. -
@occamsrazor said in DNSBL modify default bloked webpage:
@ronpfs said in DNSBL modify default bloked webpage:
Do you get something from http://10.10.10.1/
No, just a "Waiting for......" in the bottom of the browser screen and page never loads.
Do you have VLANs? If so, please ensure that in the DNSBL tab, that you have selected the "DNSBL Permit" option, and select all of the VLANs in the dropdown selection box.
Otherwise, try to disable the other two port forwards and see if one of those is causing a conflict?
There shouldn't be any timeouts.
-
@BBcan177 in PFBlocker-devel is it possible to disable the DNSBL NAT rule and disable the lighthttpd? Before you used a NAT rule (and used floating rules/etc) I just had a simple reject rule if someone attempted to access the DNSBL lighthttpd via http/https, but using the current stable version, I cannot seem to find a way to reject (seems NAT is always evaluated first?)
Thanks!
-
@crusher4 said in DNSBL modify default bloked webpage:
@BBcan177 in PFBlocker-devel is it possible to disable the DNSBL NAT rule and disable the lighthttpd? Before you used a NAT rule (and used floating rules/etc) I just had a simple reject rule if someone attempted to access the DNSBL lighthttpd via http/https, but using the current stable version, I cannot seem to find a way to reject (seems NAT is always evaluated first?)
To fix that Cert error for HTTPS sites, create a new DNSBL Group and add the domains that are causing issue to the customlist at the bottom of the page. Then disable logging and set the Order to "Primary" which will cause this Group to load first.
Follow that with a Force Reload DNSBL... That will null block those domains to 0.0.0.0 and avoid the cert errors.
-
@bbcan177 said in DNSBL modify default bloked webpage:
@occamsrazor said in DNSBL modify default bloked webpage:
@ronpfs said in DNSBL modify default bloked webpage:
Do you get something from http://10.10.10.1/
No, just a "Waiting for......" in the bottom of the browser screen and page never loads.
Do you have VLANs? If so, please ensure that in the DNSBL tab, that you have selected the "DNSBL Permit" option, and select all of the VLANs in the dropdown selection box.
Otherwise, try to disable the other two port forwards and see if one of those is causing a conflict?
There shouldn't be any timeouts.
Thanks for the help. I don't run any VLANs but in any case tried with that Permit box checked. Also tried disabling the Port Forwards, still the same. At this stage I think I'm going to give up as it's not a huge deal and the blocking functionality is working properly, but still strange...
-
Kind of glad I found this post since I thought I've been going crazy the past 2 weeks. I've install pfSense multiple times, rebooted multiple times, tried pfBlockerng and pfBlockerng-devel, multiple times. Watched about 10 youtube videos where they all go, click here, here and here, then bam! bada bing badda boom! Everything works.
Well I still get timeouts for blocked pages which really slows down browsing for people. Or am I just not properly understanding pfBlocker? Maybe that's it.
Running:
pfSense 2.4.3-RELEASE-p1 (amd64) (And I've tried this on a VM as well)
pfBlockerng-devel 2.2.5_11 (Tried with pfBlockerng 2.1.4_9 for a few days, then thought maybe the devel package is getting more love)I have the default LAN 192.168.1.1/24
So I'm using the 10.10.10.1 VIP for DNSBLDNS resolver is running, no forwarding.
If I nslookup 101com.com
101com.com
Server: pfSense.concord.home
Address: 192.168.1.1
Name: 101com.com
Address: 10.10.10.1That works!
If I browse to:
http://10.10.10.1:8081 - works, get the "Page blocked by DNSBL"
https://10.10.10.1:8443 - works, get the "Page blocked by DNSBL"
http://192.168.1.1:8081 - works, get the "Page blocked by DNSBL"
https://192.168.1.1:8443 - works, get the "Page blocked by DNSBL"but
http://10.10.10.1 - times out with "This site can’t be reached"
https://10.10.10.1 - times out with "This site can’t be reached"
http://101com.com - "This site can’t be reached. 101com.com took too long to respond."On the firewall settings the VIP is there
10.10.10.1/32 LAN IP Alias pfB DNSBL - DO NOT EDITThe 2 NAT port forward auto created rules are there (80 -> 8081, 443 -> 8443)
I have no VLANs, only a WAN and LAN network and "default" pfSense install, no other port forward or blocking rule. Nothing! defaultSo lighttpd_p is running on 8081 and 8443, but the problem is plain 10.10.10.1 (80 and 443) is not resolving but timing out. Which slows down browsing.
I feel so dumb!! What am I doing wrong? Or am I expecting pfBlocker to work differently then it actually does and it's all in my head?Sorry I tagged on to this thread, but this is the closest to the symptoms I am getting.
-
Is your pfSense GUI in HTTP or HTTPS? Are you using a proxy or something else on these ports?
-
@BBcan177 (Sorry forgot to tag reply, noob here)
So under:
System / Advanced / Admin access
Only HTTPS radio button is selected, nothing else. As in nothing else selected. Everything default install. The "TCP Port" option is empty, which reads the following for details: "Enter a custom port number for the webConfigurator above to override the default (80 for HTTP, 443 for HTTPS). Changes will take effect immediately after save."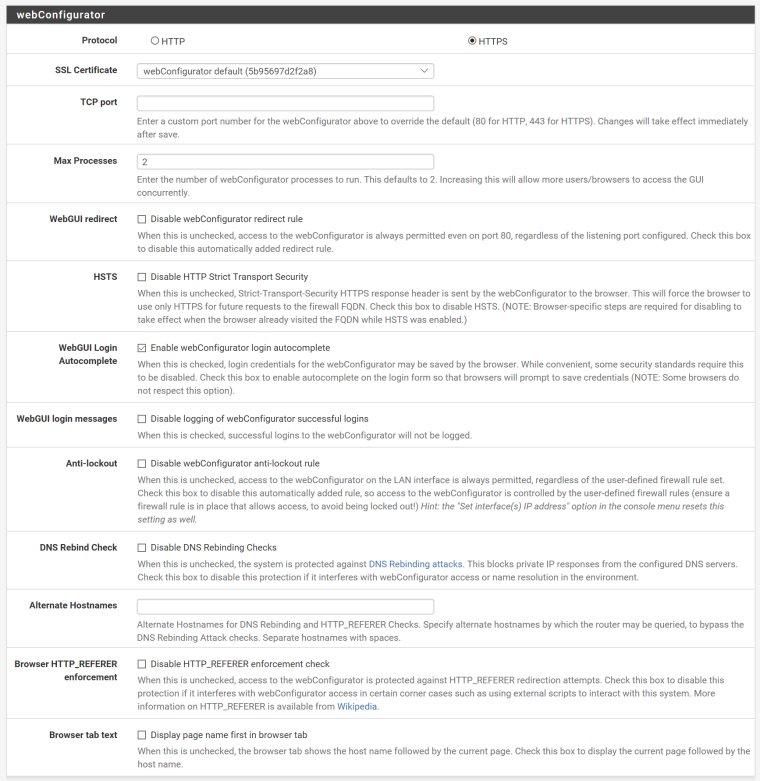
and then for System / Advanced / Miscellaneous / Proxy, it's all default blank
-
@bbcan177 said in DNSBL modify default bloked webpage:
To fix that Cert error for HTTPS sites, create a new DNSBL Group and add the domains that are causing issue to the customlist at the bottom of the page. Then disable logging and set the Order to "Primary" which will cause this Group to load first.
Follow that with a Force Reload DNSBL... That will null block those domains to 0.0.0.0 and avoid the cert errors.The thing is that basically you will need to add all https sites in there (well, almost) as most of them are using HSTS for that matter nowadays. (facebook, google and almost all majors)
No mentioning logging, alerts, etc...
That's actually the exact reason, why i'm trying to get away from this bulky and messy squid+samba+squidguard construction. But here with lighthttpd you're using static private cert which is not trusted by local cert authorities. Why can't you consider to issue at least trusted with local CA cert? I'd imagine that'll help with majority if issues.... Also i've heard rumors from of this forum, that if we will be using the squid's way with auto generating valid subCA certs for users from local CA it "would be both complicated and slow." But squid had been working with that for years, I haven't noticed any issues with it's performance... (yes there is caching also, but still)
Could you please comment? (I'm on latest dev 2.2.5_17 now) -
@bbcan177 said in DNSBL modify default bloked webpage:
To fix that Cert error for HTTPS sites, create a new DNSBL Group and add the domains that are causing issue to the customlist at the bottom of the page. Then disable logging and set the Order to "Primary" which will cause this Group to load first.
Could you please list the exact steps for this suggestion? I'm not sure what you mean by DNSBL "Group" and don't see that term anywhere under Firewall -> pfblockerNG or anywhere else.
Also, I'm seeing in other threads that this was incorporated already into pfblockerNG... If so, where is that option, because I'm definitely seeing these HTTPS certificate errors. (I'd much prefer that you allow pfblockerNG to use a certificate I provide, presumbaly using pfSense's certificate manager, so that I can pre-install the signing CA in my clients. I don't want to give up the blocked web page that's delivered -- I'm on MacOS, where Safari will let me work around the issue by installing the HTTPS server certificate in my Keychaain, but Chrome and Firefox still won't work with that for HSTS sites (like googleadservices.com)).
pfSense 2.4.4-RELEASE-p2 / pfBlockerNG-devel 2.2.5_21
-
This is where you create a new "DNSBL Group" (I am renaming DNSBL Feed -> DNSBL Group in the next release):
Click on the DNSBL Tab
Click "DNSBL Feeds"
Click "Add"Set the Name and Header field
Set the Action to Unbound
Set the Logging to Disabled
Set Group Order to Primary
Add the domains that are causing those Cert issues, to the bottom Custom List.Save, "Force Reload - DNSBL"