IPv6 Network details from ISP
-
@lin4fun said in IPv6 Network details from ISP:
Regarding the "2A02:DC0:C:6::2/56 Customer link-adresse" are this a "public" network I can use like I have in IPv4? There i got a /29 network which gives me 6 public adresses.
Yep, they're public, all 4,722 billion, billion of 'em.
-
They will route 2A02:DC0:C900:600::/56 via your WAN interface.
Seems odd to me that your ISP lists a /64 & /56 for 2A02:DC0:C:6::, maybe ask them to clarify.
2A02:DC0:C:6::/64 Linknet to ISP
2A02:DC0:C:6::1 Gateway
2A02:DC0:C:6::2/56 Customer link-adresse -
@lin4fun said in IPv6 Network details from ISP:
I hear everywhere that IPv6 is much simpler than IPv4, this I can not confirm!
That depends on what you're referring to. It is in some ways, others not. One big example is the LAN normally has only one prefix size, /64, unlike IPv4 where you also have to consider subnet size. One real big improvement is we no longer need NAT to get around the IPv4 address shortage.
-
@lin4fun said in IPv6 Network details from ISP:
Hello,
I got from my ISP the IPv6 details I asked for. Now I try to find out what is what.
I got from the ISP this details:
2A02:DC0:C:6::/64 Linknet to ISP
2A02:DC0:C900:600::/56 Customer LAN-adresse
2A02:DC0:C:6::1 Gateway
2A02:DC0:C:6::2/56 Customer link-adresse
Routed 2A02:DC0:C900:600::/56 to 2A02:DC0:C:6::2
DNS bla:bla:bla:110
DNS bla:bla:bla:111That doesn't make a lot of sense. But we can make a guess what they are trying to say.
2A02:DC0:C:6::/64 Linknet to ISP
2A02:DC0:C:6::2/56 Customer link-adresse
2A02:DC0:C:6::1 GatewayEverything looks good there except the /56. That is probably /64 instead.
pfSense WAN configuration:
IPv6 Configuration Type: Static IPv6
IPv6 Address: 2A02:DC0:C:6::2 /64
IPv6 Upstream Gateway: 2A02:DC0:C:6::1Routed 2A02:DC0:C900:600::/56 to 2A02:DC0:C:6::2
This means you can assign the following /64 networks to your inside interfaces:
2A02:DC0:C900:600::/64
through
2A02:DC0:C900:6ff::/64
You have 256 of them.
An example configuration on a LAN interface would be:
IPv6 Configuration Type: Static IPv6
IPv6 Address: 2A02:DC0:C900:600::1 /64Then, In Services > DHCPv6 Server & RA
On LAN, disable DHCPv6 Server if enabled.
On Router Advertisements, select Unmanaged and leave the defaults.
Be sure IPv6 traffic from 2A02:DC0:C900:600::1 /64 is passed by the firewall rules on LAN.
That should give you a very basic IPv6 configuration with SLAAC on the LAN side.
I have a LAN, DMZ, WAN. Also, a second ISP line out which I manually set to a client if needed.
My problem is that I can not clearly identify where to set which addresses. When I set up the DMZ interface or the LAN interface then I get a conflict of addresses.
Can anybody tell me which address I have to configure where? How do I split the "Customer LAN-address" to LAN and DMZ or can I configure the "Customer link-address" to the DMZ servers?
I have looked to many tutorials and also saw at the IPv& hangout but I just can not identify al the settings.
-
Thank you all for the information.
To get started I split the /56 now into /64 which gives a lot of networks but I don
t want so huge networks, thats why I split down to /64.I also got the communication established and ipv6 tests confirmed the communication based on ip v6.
Unfortunately, after a whole day work, I needed to revert the whole thing again. I couldn`t find out why, but the web servers were not able to be reached anymore. So a restore was necessary.I will start over again and check all network services after every single step to find the problem.
But at least the clients were able to switch to ipv6, that`s a great start!
However, I still think the whole IPv6 thing is more complicated than Pv4. Even I could handle everything in IPv4 well, the change to IPv6 makes me nervous.
I am still not 100% sure about how the security will change. Where is the best to secure by lockdown ports and how to build up a security tree, There are still not many useful examples which describes a bigger scenario with several networks & services.
-
@lin4fun said in IPv6 Network details from ISP:
To get started I split the /56 now into /64 which gives a lot of networks but I dont want so huge networks, thats why I split down to /64.
Normal practice is to split down to individual /64s. A network won't work properly with any other size, as things like SLAAC depend on it.
-
However, I still think the whole IPv6 thing is more complicated than Pv4. Even I could handle everything in IPv4 well, the change to IPv6 makes me nervous.
I am still not 100% sure about how the security will change. Where is the best to secure by lockdown ports and how to build up a security tree, There are still not many useful examples which describes a bigger scenario with several networks & services.
Dual stack, I don't even notice if my hosts are using IPv4 or IPv6 now it just works.
Just think no more NAT its routable and just needs firewall rules.
-
2: ens18: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 4a:1d:53:c2:ba:c5 brd ff:ff:ff:ff:ff:ff
inet 192.168.200.203/24 brd 192.168.200.255 scope global ens18
valid_lft forever preferred_lft forever
inet6 2a02:fe0:c900:601::ffff/128 scope global dynamic noprefixroute
valid_lft 7173sec preferred_lft 4473sec
inet6 fd2e:8850:8d4c:0:481d:53ff:fec2:bac5/64 scope global mngtmpaddr noprefixroute
valid_lft forever preferred_lft forever
inet6 2a02:fe0:c900:600:0:ffff:c0a8:c8cb/64 scope global
valid_lft forever preferred_lft forever
inet6 fe80::481d:53ff:fec2:bac5/64 scope link
valid_lft forever preferred_lft foreverWhat in .... where do all these addresses come from and what are they? This is IP output of one server I configured through netplan with single ipv6 & ipv4 address. ( inet6 2a02:fe0:c900:600:0:ffff:c0a8:c8cb/64 scope global )
DHCP4 & DHCP6 is set to "no". It is an Ubuntu 18.04 server. -
Think you need to read up on IPv6 :)
https://en.wikipedia.org/wiki/IPv6_address
-
Also : Sign up here : https://ipv6.he.net/certification/
It's worth every penny ... no ... whait, they will pay you ! In the past, they even send you a free T-Shirt https://blog.he.net/2011/04/22/hurricane-electric-ipv6-gear/ I don't know if they still do so ...
-
@NogBadTheBad
funny... Of course I have read this article, already long time ago!
Like I wrote:
"I have looked to many tutorials and also saw at the IPv& hangout but I just can not identify al the settings."Thats why I ask. I am aware of link local and the manual configured.
@Gertjan
That looks interesting! First I thought this is education, but this is to verify the IPv6 connectivity, right? -
@lin4fun said in IPv6 Network details from ISP:
Have you done this, how long did you used if? I can`t find any prices. That looks interesting!
The image I posted is "mine", and not a static one, but generated by their web site - check out the URL ^^
Took me :
Several hours, if not days, because I wanted MY tShirt ....
The beginning is easy, like IPv4, even my grand mother could answer them.
Then it becomes more complex.
I remember that moment when I recalled myself that some said to me : IPv6 is easier as IPv4 .... they have lied.
Final advantage : no more NATting ...and no more "hop to the box with 192.168.1.1" ... (mine uses "2001:470:1f13:5c0:2::1", never typed that one by hand) -
typing v6 addresses or even have them all in mind like it is with v4 is impossible i guess as "normal" human. So DNS naming becomes even more important i think. Even if I work now with the details from my isp now about 2 weeks, i do not get them in my mind and i do not want to.
I started with the thing from he.net. Like you said, in the beginning, everything looks easy. I got the server also online with v6 now and the clients are all the way through also talking in v6 now. So great so far, until it comes to security...
I just began to understand the concept behind the whole v6 thing and I must say even the nat-ing was a bit tricky due to all the things you need to take care, it is also somehow a kind if security advantage as the public site is never talking directly to the services.
V6 NAT do exist as well and sometimes, like i have read, it makes sense as well but basically not at all.So setting up the firewall is kind of tricky if you are not full into v6 yet. In my example, I didn`t get any ping responses through even opened ICMPv6 request & echo from the public to the internal service. If I open up completely, means "from WAN any to DMZ any Allow", I could ping and so on. Of course, this is not the way it can be even not for a couple of minutes.
So here I came to the question "what is initially needed for IPv6 communication?" So I added a lot of rules, opened a lot of ICMP package types and it went fine at the end.
An hour later I deleted the whole thing again because I felt completely uncomfortable since I didn´t actually know what I have opened up there.To go from IPv4 to IPv6 is not done in a couple of days that´s for sure and it takes a lot of learning and going into the detail to be and feel also save with IPv6 security & firewall!
-
@lin4fun said in IPv6 Network details from ISP:
it is also somehow a kind if security advantage as the public site is never talking directly to the services.
Yes, they are directly connecting. NAT is not a proxy. It just translates the addresses and ports.
There is zero security advantage to having a firewall pass traffic to a publicly-routable address without NAT vs a NAT port forward to a private address for the same service/port.
-
@lin4fun said in IPv6 Network details from ISP:
, I didn`t get any ping responses through even opened ICMPv6 request & echo from the public to the internal service.
See my rules :
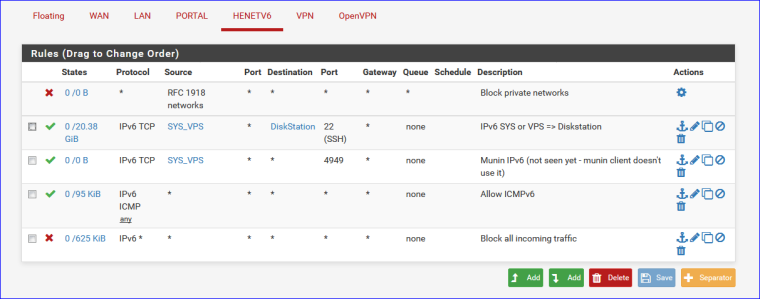
Rule 1 : ... dono - but it looks nice ;)
Rule 2 : A dedicated server somewhere on the net that saves to my Syno NAS, using IPv6 only.
Rule 3 : Munin collector running on the same dedicated server chechking the Munin process on pfSense to make this.
Rule 4 : The Ipv6 ICMP hassle - I was told that was needed.
Rule 5 : Block all ruleThe catch : there is no corresponding NAT rule for all this. IPv6 needs no NAT.
Btw : when I visit http://http://ipv6-test.com/ I obtain this :
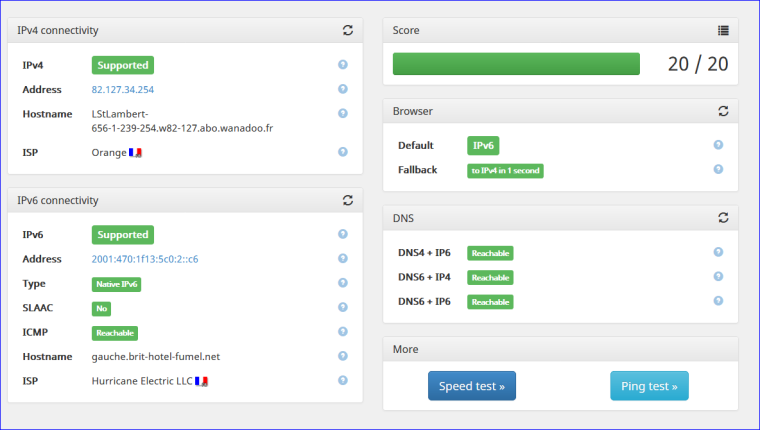
The "Hostname shows" up because I have this ""IPv6 Reverse DNS zone" on my DNS server (runs on the dedicated server on the net) so "people" can find the reverse name of an IPv6 (a device on my LAN ... dono if that is good, but I like it)
Also : my Mega big ISP (France : Orange ) doesn't support IPv6 yet where I live§work (middle of nowhere) - so I use the pretty perfect IPv6 from he.net : a static /48 for live !
-
@lin4fun said in IPv6 Network details from ISP:
I just began to understand the concept behind the whole v6 thing and I must say even the nat-ing was a bit tricky due to all the things you need to take care, it is also somehow a kind if security advantage as the public site is never talking directly to the services.
NAT does nothing for security that a properly configured firewall can't do. Most firewalls start off with deny all to which you add exceptions to allow what you want.
So here I came to the question "what is initially needed for IPv6 communication?" So I added a lot of rules, opened a lot of ICMP package types and it went fine at the
I suspect you started off by making things more complicated than needed. Once you have IPv6 up and running with your ISP, then you worry about what you want.
To go from IPv4 to IPv6 is not done in a couple of days that´s for sure and it takes a lot of learning and going into the detail to be and feel also save with IPv6 security & firewall!
For the most part, working with IPv6 is very similar to IPv4, with the advantage that you don't have to worry about NAT.
-
@jknott
If you use private v4 addresses on the inside of nat then you have a security advantage.
I do not want to make things more complicated but not all ICMP is necessary and good to have if not necessary.The network I am working on is not a home network even it is at my home. I have service running here for other companies and several web servers so it is well important to think a bit more about what to open.
Even though that a so small company I am running should not be interesting to anybody to hack I had intensive attacks in the past. They weren't lucky to come through but they showed up points of attack where I before never thought about.
Not needed ICMPv6 packages should be blocked and filtered about reachable, package size, parameter problems, header 2 / 3 and so on, antispoofing, no tunnel traffic...
-
@lin4fun said in IPv6 Network details from ISP:
If you use private v4 addresses on the inside of nat then you have a security advantage.
Please enumerate said advantage.
-
@derelict
like you may know are private networks not routed in wan. So the only reachable point is the public address the nat is configured to. That is the advantage.
If the server has a public IP then it is much easier to reach it somehow even with a firewall in front because do the attacker find a way through this firewall the server will answer due to the public address. Private will may answer inside the lan but will not be routed outside of the lan. -
If an attacker can find a way through the firewall they will be going through NAT too. No advantage gained.
You either block the traffic or you don't.
You either have another way into the network or you don't.