DNS OVER TLS ABSOLUTE BEST CONFIGURATION FOR STUBBY
-
Supplement for https://forum.netgate.com/topic/130832/solution-posted-dns-tls-getdns-stubby-from-pfsense-freebsd-ports
See here for readily legible ( more easy to read ) configuration Stubby: https://forum.opnsense.org/index.php?topic=8579.0
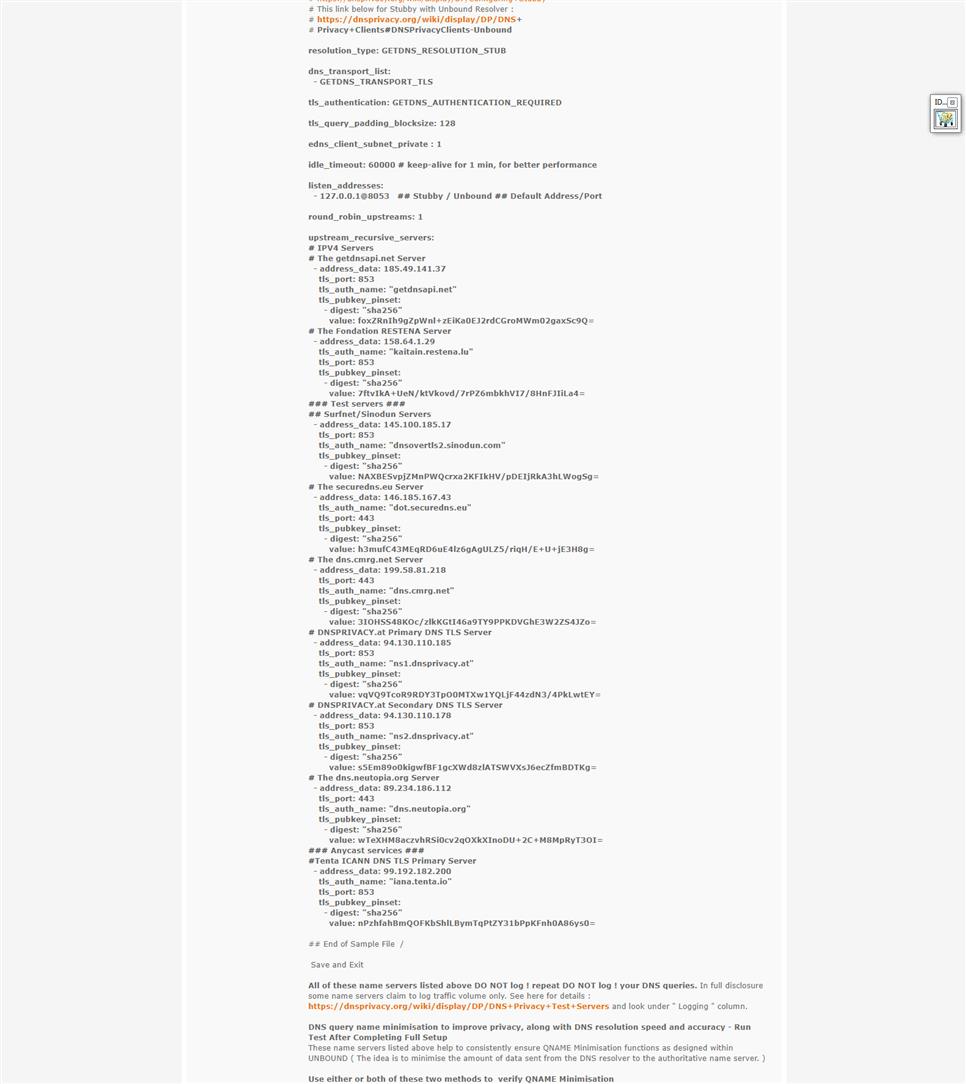
These are the best DNS PRIVACY NAME SERVERS for the detailed reasons listed below.Edit your /usr/local/etc/stubby/stubby.yml - SSH and enter nano /usr/local/etc/stubby/stubby.yml - Use this Stubby configuration below:
#This link below for Stubby with Unbound Resolver :
#See here for how to configure Stubby:
#https://github.com/getdnsapi/stubbyresolution_type: GETDNS_RESOLUTION_STUB
dns_transport_list:
- GETDNS_TRANSPORT_TLS
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 128
edns_client_subnet_private : 1
idle_timeout: 60000 # keep-alive for 1 min, for better performance
listen_addresses:
- 127.0.0.1@8053 Stubby / Unbound ## Default Address/Port
round_robin_upstreams: 1
upstream_recursive_servers:
-
address_data: 185.49.141.37
tls_port: 853
tls_auth_name: "getdnsapi.net"
tls_pubkey_pinset:- digest: "sha256"
value: foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9Q=
- digest: "sha256"
-
address_data: 158.64.1.29
tls_auth_name: "kaitain.restena.lu"
tls_port: 853
tls_pubkey_pinset:- digest: "sha256"
value: 7ftvIkA+UeN/ktVkovd/7rPZ6mbkhVI7/8HnFJIiLa4=
- digest: "sha256"
-
address_data: 145.100.185.17
tls_port: 853
tls_auth_name: "dnsovertls2.sinodun.com"
tls_pubkey_pinset:- digest: "sha256"
value: NAXBESvpjZMnPWQcrxa2KFIkHV/pDEIjRkA3hLWogSg=
- digest: "sha256"
-
address_data: 146.185.167.43
tls_auth_name: "dot.securedns.eu"
tls_port: 443
tls_pubkey_pinset:- digest: "sha256"
value: h3mufC43MEqRD6uE4lz6gAgULZ5/riqH/E+U+jE3H8g=
- digest: "sha256"
-
address_data: 199.58.81.218
tls_port: 443
tls_auth_name: "dns.cmrg.net"
tls_pubkey_pinset:- digest: "sha256"
value: 3IOHSS48KOc/zlkKGtI46a9TY9PPKDVGhE3W2ZS4JZo=
- digest: "sha256"
-
address_data: 94.130.110.185
tls_port: 853
tls_auth_name: "ns1.dnsprivacy.at"
tls_pubkey_pinset:- digest: "sha256"
value: vqVQ9TcoR9RDY3TpO0MTXw1YQLjF44zdN3/4PkLwtEY=
- digest: "sha256"
-
address_data: 94.130.110.178
tls_port: 853
tls_auth_name: "ns2.dnsprivacy.at"
tls_pubkey_pinset:- digest: "sha256"
value: s5Em89o0kigwfBF1gcXWd8zlATSWVXsJ6ecZfmBDTKg=
- digest: "sha256"
-
address_data: 89.234.186.112
tls_port: 443
tls_auth_name: "dns.neutopia.org"
tls_pubkey_pinset:- digest: "sha256"
value: wTeXHM8aczvhRSi0cv2qOXkXInoDU+2C+M8MpRyT3OI=
- digest: "sha256"
-
address_data: 99.192.182.200
tls_auth_name: "iana.tenta.io"
tls_port: 853
tls_pubkey_pinset:- digest: "sha256"
value: nPzhfahBmQOFKbShlLBymTqPtZY31bPpKFnh0A86ys0=
- digest: "sha256"
-
Save and Exit
Your /usr/local/etc/stubby/stubby.yml config file should look like this screen shot when done editing:
All of these name servers listed above DO NOT log ! repeat DO NOT log ! your DNS queries. In full disclosure some name servers claim to log traffic volume only. See here for details : https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers and look under " Logging " column.
DNS query name minimisation to improve privacy, along with DNS resolution speed and accuracy - Run Test After Completing Full Setup. These name servers listed above help to consistently ensure QNAME Minimisation functions as designed within UNBOUND ( The idea is to minimise the amount of data sent from the DNS resolver to the authoritative name server. )
Use either or both of these two methods to verify QNAME Minimisation
A - Run command : drill txt qnamemintest.internet.nl
and / or
B - Run command: dig txt qnamemintest.internet.nl +short and / or dig -t txt qnamemintest.internet.nl ( for more complete readout including DNSSEC results ).
AD = Authenticated Data (for DNSSEC only; indicates that the data was authenticated)
The results in any of these scenarios will show either:
HOORAY - QNAME minimisation is enabled on your resolver :)!”
or “NO - QNAME minimisation is NOT enabled on your resolver :(.”
Reference https://discourse.pi-hole.net/t/unbound-and-qname-minimisation/10038/4
You will and should get HOORAY ! - if you used the name servers listed in this guide for your Stubby configuration.Note: Starting with Unbound 1.7.2 qname minimisation is enabled by default.
However, I still add these settings manually.
These settings are entered under Unbound " Custom Options":
qname-minimisation: yes
qname-minimisation-strict: yes
harden-below-nxdomain: yesConfigure your Unbound DNS Server to use Stubby for DNS Over TLS.
UNBOUND GENERAL SETTINGS
Network Interfaces = WAN LAN ( all of your LAN interfaces if you have more than one ) And You Must Select Localhost - repeat - You Must Select Localhost !Under Custom options enter the following :
server:
do-not-query-localhost: no
forward-zone:
name: "." # Allow all DNS queries
forward-addr: 127.0.0.1@8053Outgoing Network Interfaces = Localhost
Make Sure to NOT CHECK - DO NOT CHECK - the box for DNS Query Forwarding. Save and Apply Settings
Next -Under System > Settings > General Settings
Set the first DNS Server to 127.0.0.1 with no gateway selected /
Make sure that DNS server option
A - Allow DNS server list to be overridden by DHCP/PPP on WAN - Is Not I repeat - Is Not Checked !
and DNS server option
B - Do not use the DNS Forwarder/Resolver as a DNS server for the firewall Is Not - I repeat - Is Not Checked !
Optionally, along with 127.0.0.1 enter Tenta nameservers 99.192.182.200 and 99.192.182.100 under System > General Setup > DNS Server Settings > DNS Servers. Things Will Work Fine and as Intended. Your DNS will still resolve using the upstream name servers you selected in stubby.yml - I have found that it is best to use Tenta name servers as " custom DNS servers " for the System. I chose Tenta DNS because their name servers support both emerging DNS privacy standards - DNS-over-TLS, and DNS-over-HTTPS, which both provide last mile encryption to keep your DNS queries private and free from tampering. Tenta DNS also is the only AnyCast DOT service which includes built-in BGP integration, offering single engine convenience for DNS Anycasting with QNAME minimisation enabled on its' name servers by default. Main benefits of Tenta DNS as the backbone name servers on PfSense:
A - Stop ISPs from spying on your browser history. DNS-over-TLS adds a layer of encryption over your DNS requests, keeping your ISP from seeing which websites you visit.B - Stay private online. Tenta DNS logs a counter instead of queries so your data stays private. No one, not even Tenta, has access to your browsing data. These are the folks that developed and support the Tenta Browser see here: https://github.com/tenta-browser/tenta-dns and read About Tenta section at the very bottom of the page.
https://tenta.com/dns-setup-guides- Save and Apply Settings
Enjoy,
ubernupe
As far as IPV6 goes - I will be honest as I do not use it. However the way I put this together is as follows:
1 - First go to this page - https://dnsprivacy.org/jenkins/job/dnsprivacy-monitoring/( I mentioned this in tutorials to add GET and STUBBY ).
2 - Next Look along the top row - start with Configuration Matrix this lists the specific DNS PRIVACY Name Servers.
3 - Go to the first Name Server listed under Configuration Matrix - dnsovertls.sinodun.com - then look for V6 then Go across to the QNAME min column. In this instance, you will see that dnsovertls.sinodun.com does not have QNAME minimisation enabled.
4 - Repeat this process for each and every DNS PRIVACY Name Server listed under Configuration Matrix
V6. You also can ( should ) refer to this page as it details proper layout and examples - parts may be a bit outdated. However, there is much useful information.
https://github.com/getdnsapi/stubby/blob/release/0.2.3/stubby.yml.example This is why it is best to to go with " LIVE MONITORING " page for the most current status and features of DNS PRIVACY Name Servers.
once again here: https://dnsprivacy.org/jenkins/job/dnsprivacy-monitoring/In order to save you some time - here is a list of IPV6 DNS PRIVACY Name Servers which are QNAME minimisation enabled:
This list contains in order Hostname for TLS authentication, IP address, TLS Port ( s ) and SPKI pin
getdnsapi.net 2a04:b900:0
 :37 853 foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9S=
:37 853 foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9S=cloudflare-dns.com 2606:4700:4700::1111( or 1001 ) 853 yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc=
kaitain.restena.lu 2001:a18:1::29 853 7ftvIkA+UeN/ktVkovd/7rPZ6mbkhVI7/8HnFJIiLa4=
dnsovertls2.sinodun.com 2001:610:1:40ba:145
 185:17 853 NAXBESvpjZMnPWQcrxa2KFIkHV/pDEIjRkA3hLWogSg=
185:17 853 NAXBESvpjZMnPWQcrxa2KFIkHV/pDEIjRkA3hLWogSg=dns.cmrg.net 2001:470:1c:76d::53 53053/853/ or 443 5zFN3smRPuHIlM/8L+hANt99LW26T97RFHqHv90awjo=
dot.securedns.eu 2a03:b0c0:0:1010::e9a:3001 853/443 h3mufC43MEqRD6uE4lz6gAgULZ5/riqH/E+U+jE3H8g=
ns1.dnsprivacy.at 2a01:4f8:c0c:3c03::2 853 vqVQ9TcoR9RDY3TpO0MTXw1YQLjF44zdN3/4PkLwtEY=
ns2.dnsprivacy.at 2a01:4f8:c0c:3bfc::2 853 s5Em89o0kigwfBF1gcXWd8zlATSWVXsJ6ecZfmBDTKg=
dns.neutopia.org 2a00:5884:8209::2 853 /443 wTeXHM8aczvhRSi0cv2qOXkXInoDU+2C+M8MpRyT3OI=
PS -
Tenta DNS OVER TLS does not support IPV6 as of yet - but keep checking the DNS PRIVACY Monitoring Page as these things change frequently and all the time. This whole process is relatively new after all. In this case, use Local host 127.0.0.1 and Cloudflare 1.1.1.1 and 1.0.0.1 DNS SERVERS under System > General Setup > DNS Server Settings > DNS Servers. Cloudflare supports DNS OVER TLS as well. I am not quite sure if you should enter Cloudflare DNS IPV6 Name Servers ( 2606:4700:4700::1111 and 2606:4700:4700::1001 ) here in the case you are using IPV6 blended with IPV4 or IPV6 exclusively.Peace,
ubernupe