Destination Ports versus NAT ports in pfSense Firewall NAT
-
Hello IT Fellows,
I would like to learn from a brief explanation on the difference between the destination ports and the NAT ports in Firewall / NAT / Port forwarding on a FreeBSD 11.1-RELEASE-p7 pfSense.
Basically, there are two implementations for MS RDP port forwarding and each go to NAT port 3389 which is the default MS RDP port.
But, the destination ports differ for each. One implementation goes to 33389 and the other to 33390. Yet both use NAT port 3389.
I suppose what I am asking is this a matter of firewall ports in LAN versus NAT WAN ports? Or physical vs logical ?
I am just want to understand better. Thank you in advance.
Alexi
-
@virtuousmight said in Destination Ports versus NAT ports in pfSense Firewall NAT:
I would like to learn from a brief explanation on the difference between the destination ports and the NAT ports in Firewall / NAT / Port forwarding on a FreeBSD 11.1-RELEASE-p7 pfSense.
Sorry I don't understand exactly what you are talking about.
Basically, there are two implementations for MS RDP port forwarding and each go to NAT port 3389 which is the default MS RDP port.
Two implementations from whom? Microsoft in implementing RDP?
But, the destination ports differ for each. One implementation goes to 33389 and the other to 33390. Yet both use NAT port 3389.
Could you elaborate on that or explain with a link etc.?
What I make of it is that one wants to use 33389 and 33390 ports to connect to two differen hosts maybe? That would be just a simple port forwarding issue.
-
Yeah have read your post like 3 times... Not getting what your asking?
Yes the default rdp port is 3389.. You can change this on the device, or you could forward some other port like 33389 to 3389 if you so desired in your port forward rule..
Are you talking about a 1:1 nat vs a port forward?
-
@jegr I do not mean to confuse....here is a screen snip of the setting I am seeking to understand:
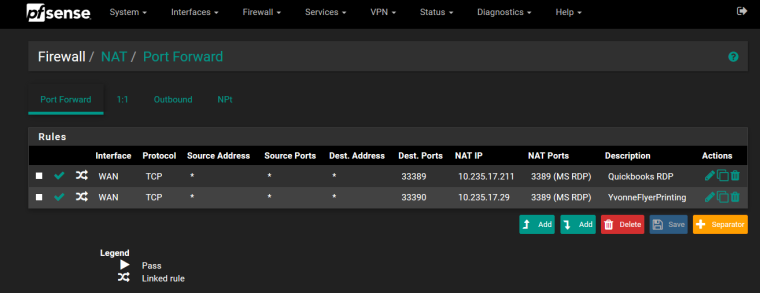
My incomplete understanding has to do with the destination ports differing from the NAT ports. So two remote employees access two desktops from outside the LAN, so why do they have identical NAT ports but different destination ports? Are NAT ports WAN-LAN firewall specific and the destination ports desktop node specific ?
Is it because one is assigned by the NAT ISO standard and the destination ports are taken from the LAN as a logic port ?
I apologize in advance if this is considered to be common knowledge but I worked primarily with software code as I am a computer science major but was able to get this job as an IT which leaves plenty to learn in network topology, infrastructure, etc.
-
@johnpoz I do not mean to confuse....here is a screen snip of the setting I am seeking to understand:

My incomplete understanding has to do with the destination ports differing from the NAT ports. So two remote employees access two desktops from outside the LAN, so why do they have identical NAT ports but different destination ports? Are NAT ports WAN-LAN firewall specific and the destination ports desktop node specific ?
Is it because one is assigned by the NAT ISO standard and the destination ports are taken from the LAN as a logic port ?
I apologize in advance if this is considered to be common knowledge but I worked primarily with software code as I am a computer science major but was able to get this job as an IT which leaves plenty to learn in network topology, infrastructure, etc.
-
The default port that rdp listens on is 3389, that is the nat port you see in your screen shot.
You have 2 forwards and different dest ports because you have only 1 wan IP I take it.. So if you want to hit machine 10.235.17.211 on rdp you set your rdp client on the to hit your WAN IP, lets call it 1.2.3.4:33389 and you will be forwarded to .211 box.
If you hit 1.2.3.4:33390 on your rdp client you will be forwarded to the .29 box on 3389.
this allows you to have 1 IP send traffic to multiple machines behind your nat on the same port.
None of which I would suggest to be honest, you should not have rdp open to the public internet.. Why do these users not just VPN into your network when they need to RDP to a machine?
-
I appreciate the explanation as well as the consideration to suggest a superior alternative.
I understand the distinctions with this port forward configuration more so now.
With VPN, that would be more optimal and I would gladly implement it but that will not happen until the company
decides to invest in it and allocate funds in the budget for it.Same goes for a domain controller/on-prem server. They are operating on peer-to-peer user workstation network with about 50 employees.
I do not know when they plan on getting a client/server based network.
Thanks again.
-
If you have pfsense you already have vpn... The only limitation would be on bandwidth and hardware pfsense is running on. And then whatever setup time there, etc.
-
Well then, I can work on that .
With the hardware specs listed, will it suffice to implement VPN?
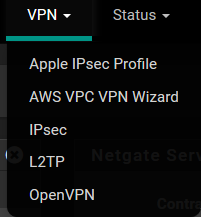
If so which one would be recommended of these:
-
First thing I would recommend is move to 2.4.4 ;)
All comes down to what you want to run - to me the openvpn is easy, and clients for everything windows, mac, linux ios android, etc.
There is is just no built in client on user devices. Running L2TP might be able to leverage built in clients - comes down to what clients your using. Or the Apple ipsec if all you had was apple devices... Then again nothing saying you can't run all of them ;)
Any box can run vpn - if it can run pfsense. What I meant was more how many clients, how fast it would be would be limitation of your hardware and your pipe.. 8860 should handle quite a few clients if you have a fat enough pipe. But a sg1000 can also run vpn.. As long as your not talking a 100 simultaneous clients the sg1000 would be fine etc.. As to how many clients an 8860 can handle... I would guess if your pipe is fat enough your 50 users should not be an issue.
-
Indeed, I am planning on doing the version upgrade tomorrow when no one else is in the office :)
Now openVPN is what I am thinking considering this would be a first for me.
As for bandwidth pipe we are on AT&T dedicated fiber 150x150 if that is what you mean. However, only two remote employees would actually by using the VPN from outside our LAN, 3 including myself. All other employees work from within our local IP domain subnet. If I am not making sense please do guide.
pFSense is currenty running on appx. 60% windows machines and 40% apple devices for ~30 - 50 nodes on network. 5 juniper switches and an Aruba Virtual Controller IAP cluster with 6 WLAN units.
-
3 vpn users and 150/150 - yeah your fine ;) heheheh
Openvpn is easy peasy lemon squezzy to setup.. Just run through the wizard - check out the openvpn section in the pfsense book.
If you have questions - just ask in the openvpn section.