Inter VLAN routing
-
Here are screen shots of my rules:
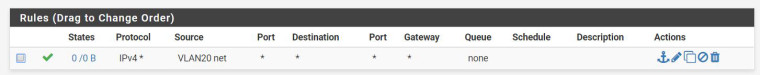
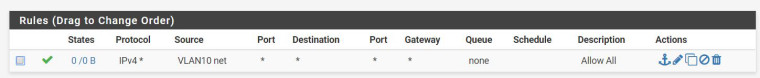
I did the capture and it looks like this:
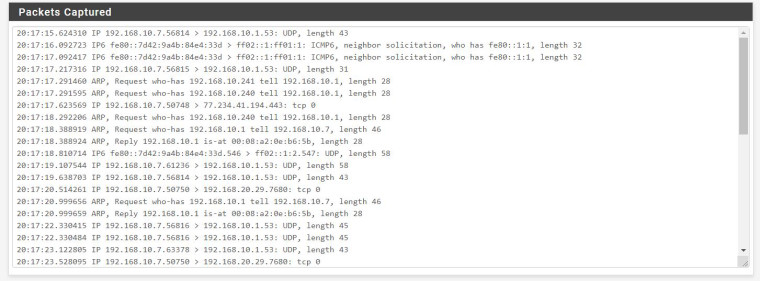
I also captured vlan 20:
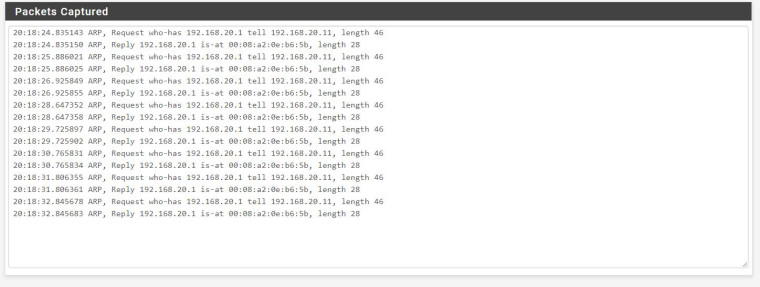
If I'm understanding the capture correctly they get to the gateway but not any farther. Am I reading that right?
-
There are no hits on your firewall rules.
Is the first rule you posted from vlan 20 or vlan 10?
-
The first rule is VLAN20 the second is VLAN10
-
I'd be looking at the switch config.
Do any mac addresses appear in the ARP table ?
-
Both of the Mac addresses show up in the ARP table.
-
I meant devices that aren't the router, i.e. PCs on vlan 10 & 20
-
There are zero hits on those rules... Can a device in a vlan even ping pfsense IP in that vlan?
-
Yes, there are other devices showing up in the ARP table from vlan 10 & 20.
I was able to ping the pfsense IP from each vlan. I just can't seem to ping/communicate from vlan to vlan.
-
Local firewalls on the hosts preventing traffic from other subnets?
-
@derelict
 yes, that was the issue. Thank you everyone for you help with this!
yes, that was the issue. Thank you everyone for you help with this! -
If you were hitting pfsense trying to go to another vlan, then the allow rules would show hits - or the default deny would log it, etc.
Do you have rules in your floating tab? Those are evaluated before the interface rules..
BTW - I stated host firewalls over 4 hours ago ;) heheeh
-
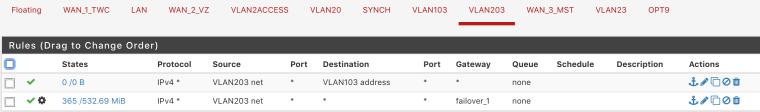
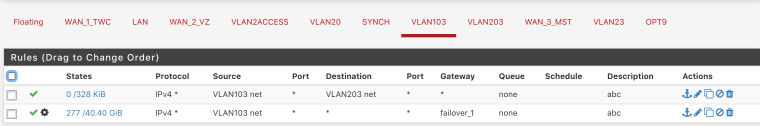
I have similar issue, 2 vlans, 103 and 203, I was trying to ping from iphone to printer or windows to printer or windows to iphone, no luck. All should be good imho. I even added extra rules to pass traffic between vlans but based you what you have here this is not needed.
rules for 103
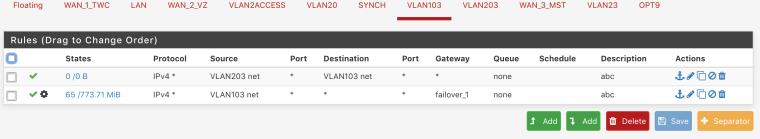
same logic for 203Diagnostics is a pass, weird
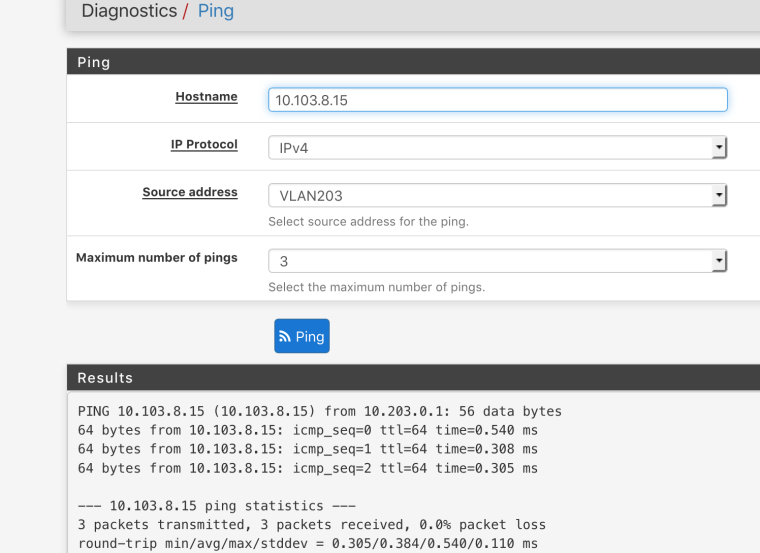
-
VLAN103 will never see traffic sourced from VLAN203 coming into it. That first rule is useless (note the 0/0 counters there since it's impossible for traffic to match it). If you want 203 to be able to ping 103, put the rule passing that traffic on 203.
That ping works because you are sourcing it from the firewall.
https://www.netgate.com/docs/pfsense/firewall/firewall-rule-basics.html
https://www.netgate.com/docs/pfsense/firewall/firewall-rule-troubleshooting.html
-
Both vlans 103 and 203 have imo correct rules
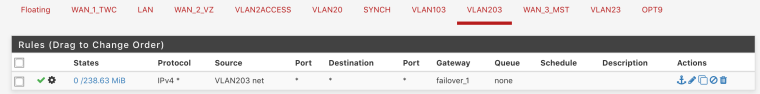
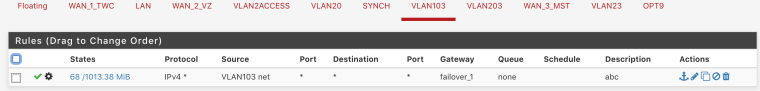
-
your forcing traffic out the gateway how can traffic from 1 vlan get to the other vlan - via that gateway your sending it out of.
If you want vlan 103 to talk to 203 then you need a rule that allows said traffic before you send traffic out some gateway. On the vlan 103 interface, and vise versa for 203 to talk to 103
You also have to be concerned that the device your trying to get to on the other vlan allows access from the source network IPs - ie the devices local firewall if any.
-
@johnpoz said in Inter VLAN routing:
If you want vlan 103 to talk to 203 then you need a rule that allows said traffic before you send traffic out some gateway. On the vlan 103 interface, and vise versa for 203 to talk to 103
The thing is I don't have internal gateway defined like 10.103.0.1 or 10.203.0.1, all are gateways form public blocks. Can I define internal one and use it then?
-
DONT assign a gateway... Just leave it the default * so it can use its internal routing tables.. Which is knows how to get to networks its direcctly attached to, ie the vlan 103 and 203.
Create a rule on vlan 103 that says dest vlan203 net and does not assign it a gateway. Put this rule ABOVE the rule where your forcing traffic out that failover gateway.
Reverse that for your vlan 203 interface
-
Yeah I didn't notice the policy routing in your rules. Sorry.
https://www.netgate.com/docs/pfsense/routing/bypassing-policy-routing.html
-
Sth is hitting the rule but still getting timeouts
13:16:54.028880 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:54.466404 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 432, length 40
13:16:55.032488 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:56.032418 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:57.032991 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:58.030264 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:59.032380 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:16:59.467559 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 433, length 40
13:17:00.032288 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:00.476238 IP 10.203.8.26 > 10.103.0.12: ICMP echo request, id 1, seq 434, length 40
13:17:01.032384 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:02.032336 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64
13:17:03.032353 IP 10.203.0.33 > 10.103.0.12: ICMP echo request, id 30840, seq 30840, length 64 -
And does the other end have a firewall? Windows machines for example out of the box will not answer ping from something not on its local network.
Simple do a sniff on the vlan 103 or 203 interface in pfsense when you ping from the other vlan - do you see the request go out.. If so and no response then its the host..