Site-to-Site OpenVPN Connectivity Problem
-
Those look like gateway monitoring. you can disable that if you don't want it. Else filter on the source or target host IP address so you don't have to look at them.
Are you sure the far side will respond to pings from a remote subnet? Windows firewall?
Start at the source. pcap on the lan receiving the echo request. Then pcap on the OpenVPN on that side. Then pcap at the openvpn on the far side. Then the LAN on the far side. If the pings are going through but there is no response there, check the target host. Else see where the replies die.
-
Yup, you're right - those echos were gateway monitoring agents; they're off on both sides for now. To answer your questions:
Yes, i'm sure the far side should respond. Windows firewall is off and I can ping it from pfsenseB>clientB.
Start at the source - here are the results. I kind of did those before because other posts suggested that as a form of troubleshooting, but now i did it more thorough....here are the findings:
pfsenseA > clientA = success
pfsenseB > clientB = success
pfsenseA > clientB = fail
pfsenseB > clientA = failI can try pinging some other-side gateway IPs from each pfsenseX, but i'm not sure which ones to ping. From other forum posts I also gathered that some shouldn't even reply so I don't want to add to confusion by including that in the above tests.
So so far it still looks like there is no connectivity between the two sides. I also checked the firewall logs and I don't see any rejections that jump out, i.e on ovnpns2(A) or ocpnc1(B) interfaces....
Appreciate your help. Anything else I can try, or should i be pcap'ing with different switches?
-
No. You need to packet capture the pings at progressive hop points, not report success or failure of the pings.
-
Ok, gotcha. Then the results are the same. I can't see any pings crossing the tunnel. I see them on each sides pfsense, but they don't come out on the other end.
-
That is not enough information to provide any help.
Post a pcap of something like a
ping -c3 destat each hop, detailing exactly where each pcap is taken. -
Sorry for the delay in my response - was out of office. Please let me know if you need more info, or if i misunderstood anything.
clientA > pfsenseB (ping -c 1 10.0.105.51)
clientA:
C:\WINDOWS\system32>ping -c 1 10.0.105.1
Pinging 10.0.105.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.Ping statistics for 10.0.105.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),C:\WINDOWS\system32>
pfsenseA:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ovpns2, link-type NULL (BSD loopback), capture size 262144 bytes
14:17:33.076313 IP 10.0.100.121 > 10.0.105.1: ICMP echo request, id 1, seq 779, length 40
14:17:37.670815 IP 10.0.100.121 > 10.0.105.1: ICMP echo request, id 1, seq 780, length 40
14:17:42.681825 IP 10.0.100.121 > 10.0.105.1: ICMP echo request, id 1, seq 781, length 40
14:17:47.687779 IP 10.0.100.121 > 10.0.105.1: ICMP echo request, id 1, seq 782, length 40pfsenseB:
tcpdump is emptyclientA > clientB (ping -c 1 10.0.105.51)
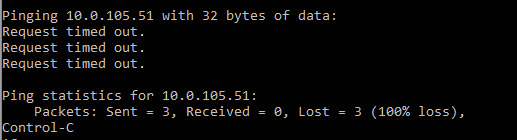
ClientA:
C:\WINDOWS\system32>ping -c 1 10.0.105.51Pinging 10.0.105.51 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.Ping statistics for 10.0.105.51:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),C:\WINDOWS\system32>
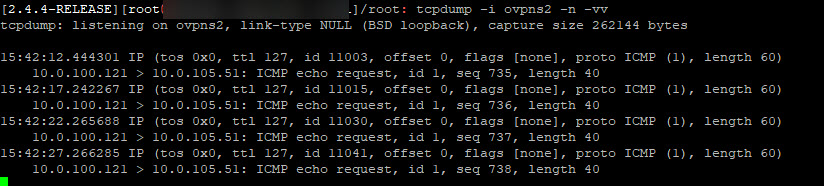
pfsenseA:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ovpns2, link-type NULL (BSD loopback), capture size 262144 bytes
14:21:43.005849 IP 10.0.100.121 > 10.0.105.51: ICMP echo request, id 1, seq 787, length 40
14:21:47.666048 IP 10.0.100.121 > 10.0.105.51: ICMP echo request, id 1, seq 788, length 40
14:21:52.670818 IP 10.0.100.121 > 10.0.105.51: ICMP echo request, id 1, seq 789, length 40
14:21:57.685270 IP 10.0.100.121 > 10.0.105.51: ICMP echo request, id 1, seq 790, length 40pfsenseB:
tcpdump is empty. -
@jamesva said in Site-to-Site OpenVPN Connectivity Problem:
pfsenseB:
tcpdump is empty.Listening where?
Sorry. You don't need the
-c 1flag. I forget sometimes that some people still use Windows.Don't need any more ping results. We know it isn't working.
-
pfsenseB is the other side psfsense console.
-
Right but capturing on what interface? Need specifics here.
And can you ping the pfSense LAN interface address on the other side?
-
The captures are running on the ovpn interfaces. Should i have been capturing on another interface?
As far as ping LAN interface - no, i can't reach it from one side to another. However if the client is on the same side, pfsense's LAN int responds to pings just fine.
-
Having said that, it looks like I can ping clients on Side A if i'm sitting on the console of pfsenseB.....
however it doesn't work the opposite way, i.e. if i'm on the console of pfsenseA, i can't reach anything on side B.
-
It doesn't make any sense that you are seeing traffic exit the VPN at A but it does not arrive in a capture on openvpn at B.
-
Could it have something to do with the fact that pfsenseB WAN IP is on 10.x.x.x subnet?
-
Not unless it's within or conflicting somehow eith the others. And you'd still see the packets in the capture on the OpenVPN.
-
hmm ok, what else can you suggest I try? I do have multiple ovpn instances on SideA, but i can't imagine that would conflict with any of them since they're running on different ports....
-
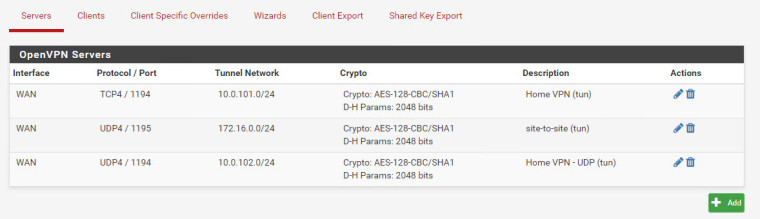
It's not about ports but addresses/networks. They all need to be unique.
-
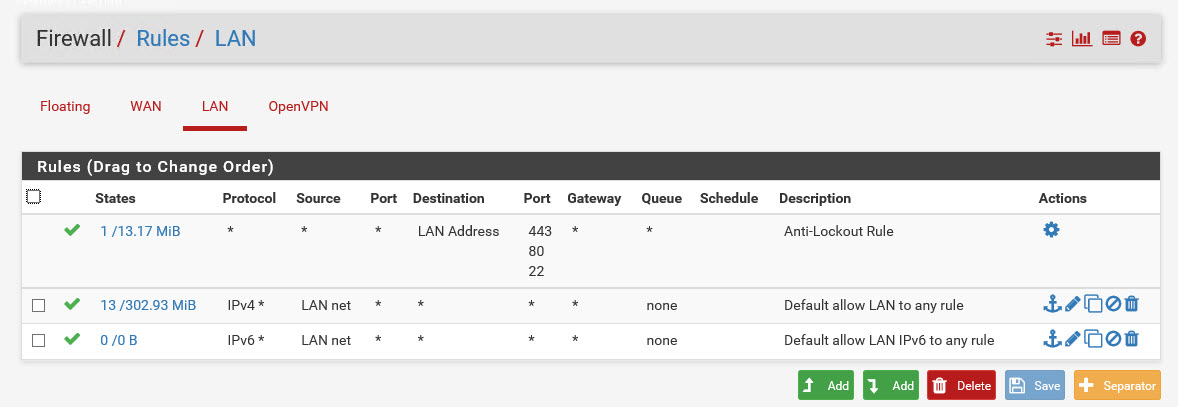
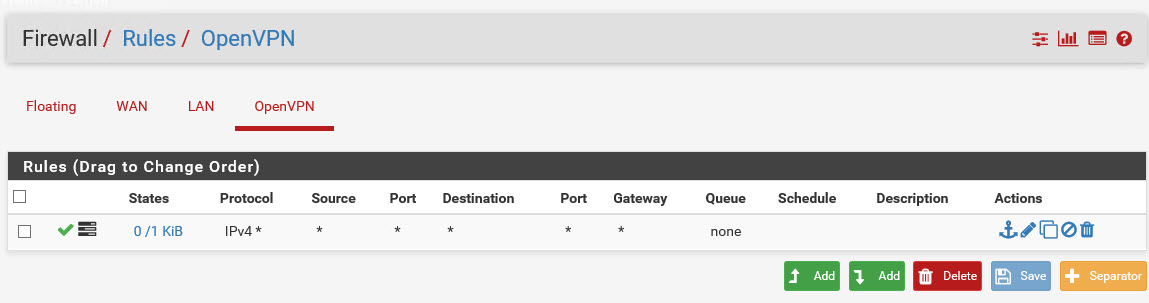
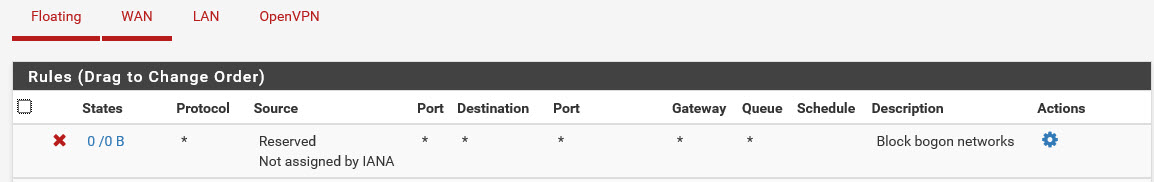
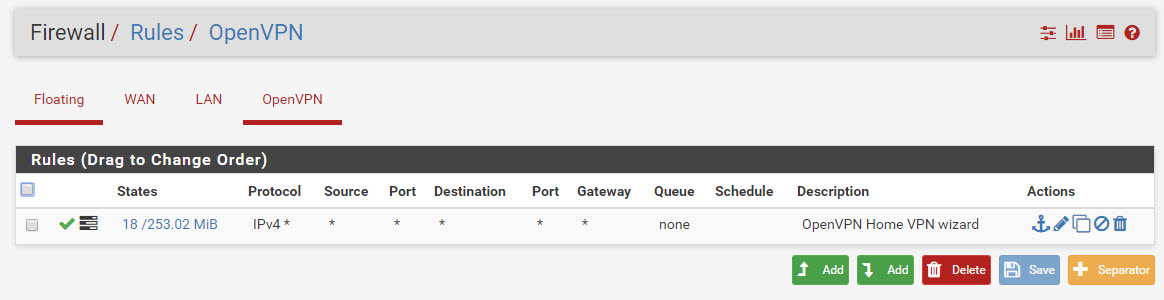
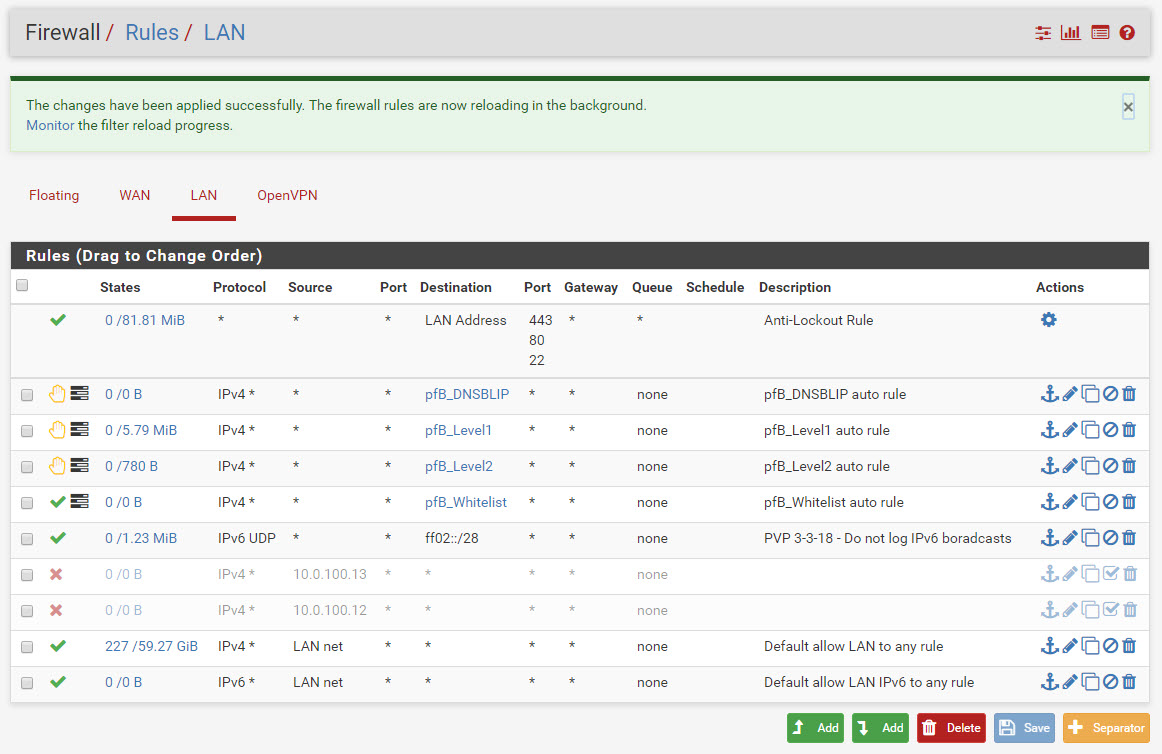
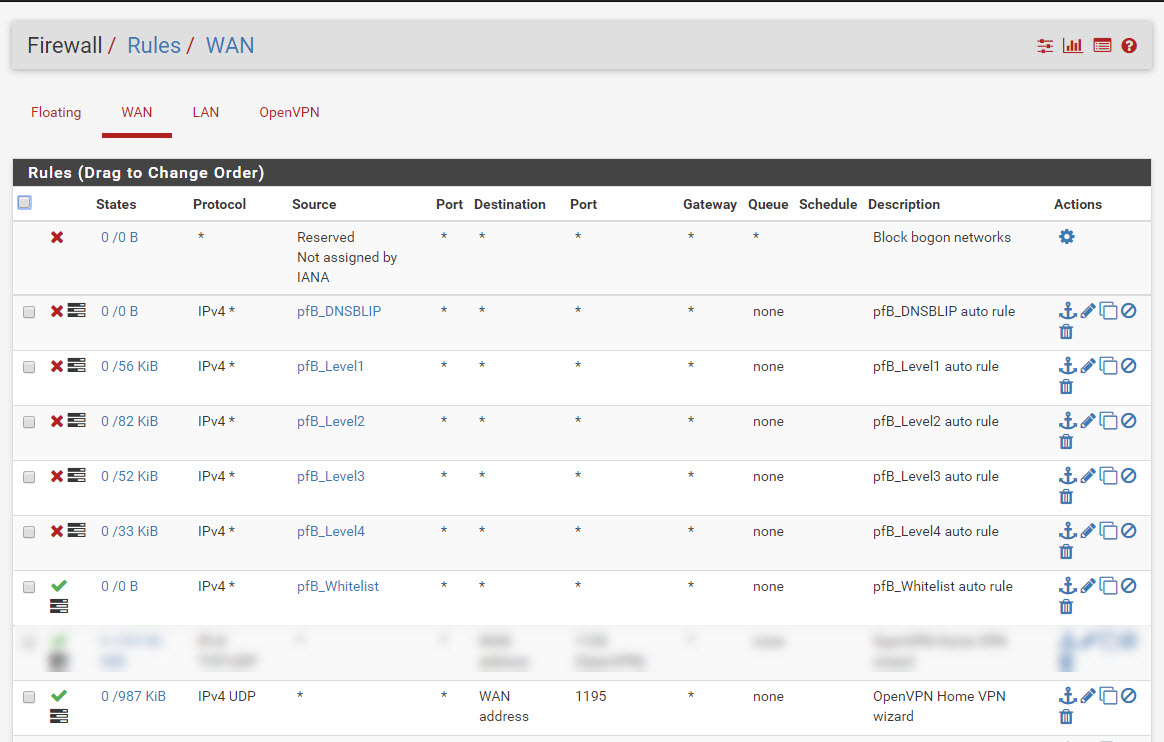
they are; screenshot below.
-
what would be the next think i try that you would suggest?
-
Don't know. I asked for some files in chat. Did you upload those?
-
Done. Thanks for taking a look at it!