How to prevent DDOS using Snort?
-
Do you have rules on WAN passing traffic to that port? Do you know what is on 8080 on WAN?
You are getting bad information because you called it a DDoS.
The very first thing I asked was "Attacked how?"
-
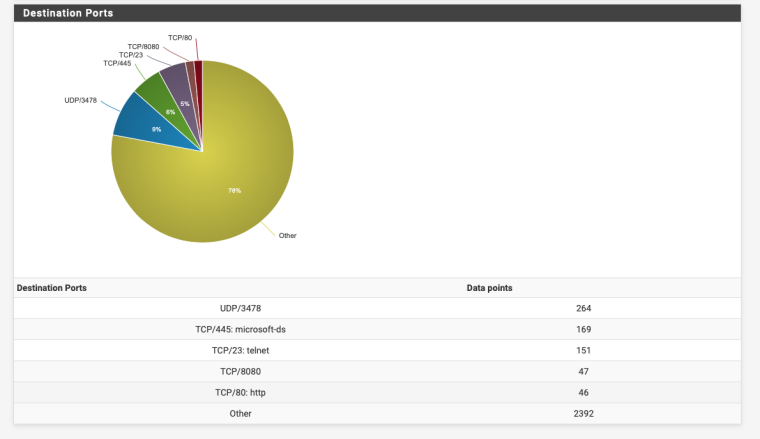
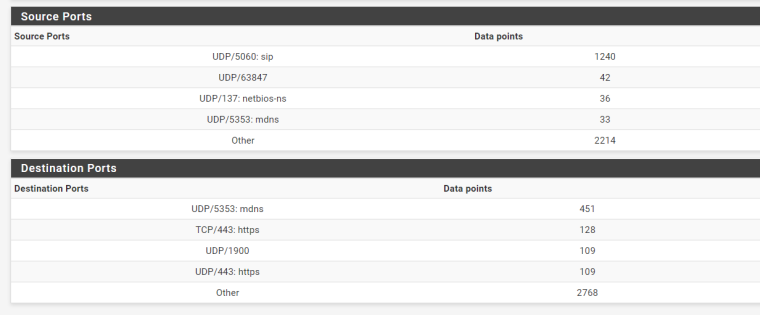
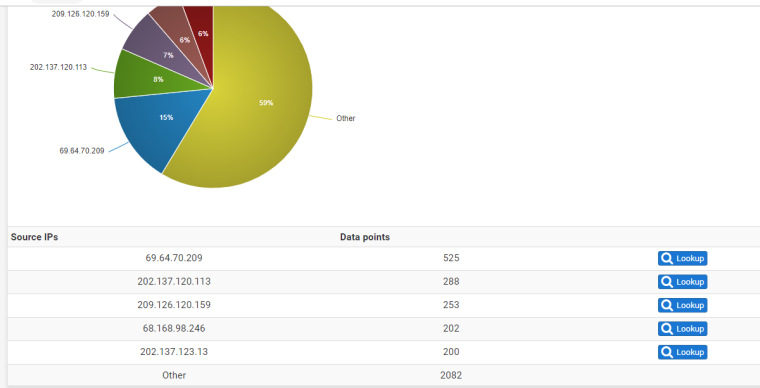
Just to give us an idea post a screenshot of the bottom of Status -> System Logs -> Firewall -> Summary View.
Here's mine I only have 3000 ish drops in total.
-
-
@derelict said in How to prevent DDOS using Snort?:
Do you have rules on WAN passing traffic to that port? Do you know what is on 8080 on WAN?
You are getting bad information because you called it a DDoS.
The very first thing I asked was "Attacked how?"
what should i do sir?
-
Please answer the questions asked for starters.
-
no 8080 there, have you cleared the firewall logs ?
But as Derelict mentioned in his first post if it is a DDoS there isn't much you can do apart from talking to your ISP.
-
@derelict i dont have a RULES for that port. im using the default rules.
-
Then the connections would have been being blocked and there's not much you can do but talk to upstream to stop it.
Hard to imagine someone sending enough TCP SYNs to a blocked port to be a problem though.
-
@derelict said in How to prevent DDOS using Snort?:
you can do but talk to upstream to stop it
what do you mean by upstream? "you can do but talk to upstream to stop it"
Internet provider? -
Yes.
-
this PFBlockerNG and Snort are useless ? can i just close my WAN ports?
Thank you So much.
-
You said they WERE closed.
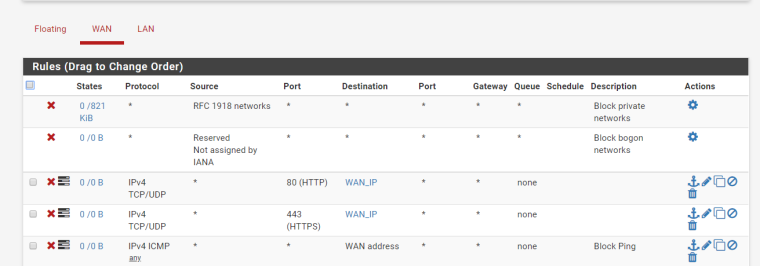
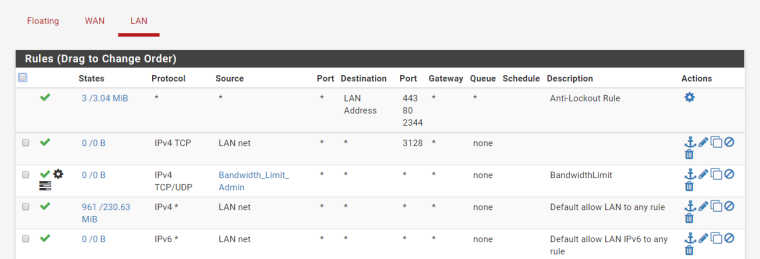
Post your WAN rules.
-
Unless you created a port forward, or running openvpn or something where the wizard would all traffic on your wan to port vpn listen on ALL unsolicited traffic to your wan is dropped/blocked out of the box.
Please post your wan rules as asked, and actually state why you feel you were attacked? A couple hundred hits? Is that even your WAN.. the 5353 and 1900 are most likely broadcast traffic from your lan side.. Or its BS noise from your ISP layer 2 on your wan.
-
-
Any floating rules ?
-
-
The rules on your wan are pointless!!! All interfaces have default deny on them.. Its pointless for those rules unless you have turned off default logging and just want to log those ports and pings.
And again where is this attack?, I see nothing in your logs but some very LOW level amount of noise...
-
@johnpoz said in How to prevent DDOS using Snort?:
The rules on your wan are pointless!!! All interfaces have default deny on them.. Its pointless for those rules unless you have turned off default logging and just want to log those ports and pings.
what should i do sir ? delete the port 80 and 443 rules? to avoid incoming SYN flood to my WAN IP?
-
What? They are pointless in that fact that they are dropped by default... There is no reason for those rules unless you had turned off default logging of default rule and wanted to log them as see you have enabled logging on the rules.
Those have ZERO to do with any SYN flood ;)
Again where is this attack? If you had say 1000 hits in a second or something you might have something to investigate... But you have nothing but very very low amount of typical noise in your logs.
-
@johnpoz sorry noob question where i can check if i got 1000 hits per seconds ? maybe im just curious last night ?