BIND Package
-
Before I start messing around my system with bind package do I have to disable DNS Resolver and change some pfsense settings
Thank you
-
anyone?
-
If you want to use bind, then yeah your going to want to turn off either the forwarder or resolver (dnsmasq or unbound) since they would be listening on 53, etc.
-
OK
When enable BIND the IP of the DNS server become the IP of the pfsense itself again right?
Sorry this might seems stupid question for you but lat time I tried to configure BIND was a disaster for my network :) and this time I will ask a lot of stupid questions until I am sure I know what I am doing so I won't repeat my last mistakes. :) -
Yes if you enable bind it will listen on the IP address of the interfaces you tell it to listen on.
If your are not comfortable with BIND and how it works - why are you trying to use it vs the default resolver.. Unless you have some specific need of feature that bind can do that unbound can not - I would suggest you just use the default resolver..
Bind does bring lots of features to the table, and is meant as authoritative NS.. But even with a gui - its not as easy to configure as unbound. ACLs, Views, etc.. Can for sure confuse new user to it.
-
Yes I need BIND because I have 3 sites that need to be resolved trough VPN
I am currently configuring the authoritative NS in let say loc 2
I know it is confusing but I have to learn to configure some time step by step with help
I don't have to become a DNS engineer just to do the basic job I need.I can't find any post in this forum or any other forum about basic configuration of BIND on pfsense with multiple sites and some basic DNS security so I started one It might help someone else who is confused like me some day. :) and it is a very useful package on pfsense
-
@xlameee said in BIND Package:
Yes I need BIND because I have 3 sites that need to be resolved trough VPN
And why is it you think you need bind exactly?
The reason you prob don't find any posts about setting up bind, etc. Is that anyone using BIND would know how to use it - and that is why they are using it ;) hehehe All the bind package is adding a gui to what is normally done in the conf file.
More than happy to answer any and all questions you might have about bind - but lets be sure you actually need it.. And not something that can be one out of the box with pfsense... You could have 1000's sites connected via vpn wouldn't mean you need to run bind..
When you say sites - you mean 3 fqdn that you want vpn connected people to resolve to an IP, or 3 different sites connected to you via vpn in s2s configuration and you want them to resolve what exactly?
When you say sites do you mean domains/zones -- with MULTIPLE entries in each domain... Multiple record types? Or do you mean 3 FQDN in total? that might be
host.domainX.tld
otherhost.somethingelse.tld
other.domainX.tld??
-
@johnpoz When I say sites I mean exactly zones/domains
site1.domain.com
site2.domain.com
site3.domain.combut unbound cannot sync to other unbound so I have to add each host to each unbound manually.
-
No those are the same domain with three hosts... You could do that in 2 seconds with host overrides in the either the dns forwarder or unbound which is default on in pfsense out of the box. There is no reason to need to run bind for something that simple.
-
no not really... You can just create a domain override in the other sites pointing to your NS for domain.com
If your vpn is down, then there would be little reason to resolve them anyway. So that is a 1 time thing.. Or so what if you create the records in multiple locations. Your talking 3 fqdn there - that would take you all of 30 seconds each location.
Do these records change like every day or something? even if they do - once you setup the domain override any record you create in your unbound host overrides would be resolvable by any other site that point to you for that domain.
Are your other sites all using the same domain? That is not good idea...
-
all 3 sites are using the same domain let say domain.com
let see if I am getting this correctly "domain.com" is a main domain "site1.domain.com" is a sub-domain, right? -
yup that would be subdomain of domain
So you have multiple records in these domains? Give me 2 seconds and will draw up what I think your talking about and how you could just do it with unbound out of the box. I would suggest you use
site1.tld
site2.tld
site3.tldvs subdomains - but it works either way.. Just easier to understand with different domains vs sub, and can be shorter fqdn vs
host.site1.domain.tld
-
So is this make sense? You have 3 sites connected via vpn... With 3 different domains and simple domain overrides.
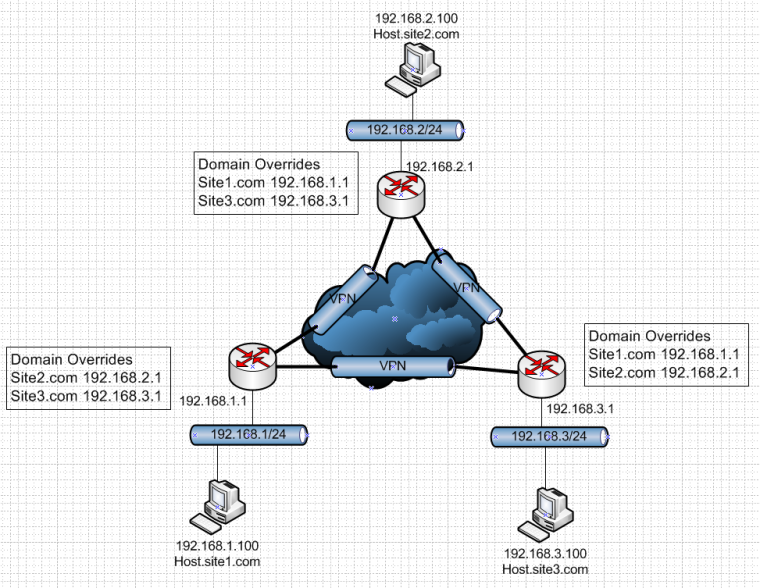
Sure if you want to use
site1.domain.tld
site2.domain.tld
site3.domain.tldthat works too.
Now if host.site2.com needs to resolve host.site3.com it asks its local unbound 192.168.2.1. Unbound says oh for site3 I go ask 192.168.3.1 which should have the record(s) for all devices there.
-
@johnpoz OK
Just domain override will do the job. Just want to point on each site each host have its own unique name there is no such thing as mgmt-server.site1.com and mgmt-server.site2.comIn order to resolve a hostname not FQDN on site2 from site1 this won't work because I tried.
let say I have a freenas server mgmt interface is 192.168.1.100 hostname is freenas1 on site2
when I enter https://freenas1 fron site1 host on the browser won't resolve I have wondering if BIND can do this -
Nothing is going to work without FQDN, even if you used bind and zone transfers... Your clients would still need to use search suffix to allow for resolving anything... The only way to resolve just a host name is with a broadcast on the same layer 2..
If you want to just use hostnames without being fqdn since all the hostname are unique just have your different domains listed in your search suffix on your clients.
Why would anyone ever enter http://host ever in the first place? just put in http://host.domain.tld and save it as as book mark, or shoot once you do that once most browsers will autofill it in for you the next time you even start putting in the name ;)
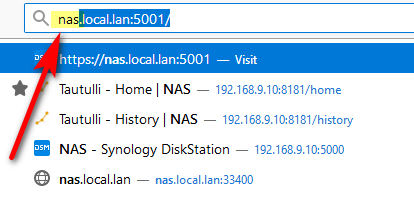
I start with typing nas and the browser gives me options that are fully qualified or even IP based..
-
@johnpoz hello
Sorry about the late replay I was busy with some firmware issues on my network
I've been reading about dns resolver on pfsense however limited information I could find, but from what I understand if I want to resolve OPENVPN traffic I have to setup a access list
Can you help me to do that ?
in Advance Settings--Advance Privacy Option
I have ticked "Hide Identity" "Hide Version" and there are 2 more options I don't understand
"Query Name Minimization" "Strict Query Name Minimization" If I tick them will increase privacy, but will this somehow affect performs on the DNS ?Also I found some custom options and I am not sure if will do more privacy
#prevent DNS leaks in Win 8 and above
push "block-outside-dns"
also if you know some custom option that my DNS will increase privacy
I really like some advice setting up the dns specially on privacy siteThank you
-
Out of the box access list are going to be auto - but you might need to add that for your vpn tunnel network sure.
query name min is when you are walking down from roots and vs asking for www.domain.tld you only ask roots for tld, he says oh .com go ask the ns for .com, you then go ask .com ns hey whats ns for domain.tld..
Only when you get to the actual authoritative NS do you ask for the full record.
Keep in mind this can cause issues with some domains and cnames, etc.. There are some threads here where testing that and believe technet and stuff from ms one of the domains that wouldn't resolve..
How is it you couldn't look up the RFC that is clearly listed in the notes about that setting
"Only send minimum required labels of the QNAME and set QTYPE to A when possible. Best effort approach; full QNAME and original QTYPE will be sent when upstream replies with a RCODE other than NOERROR, except when receiving NXDOMAIN from a DNSSEC signed zone. Default is off.
Refer to RFC 7816 for in-depth information on Query Name Minimization."You really have little use in the advanced section until you know what your doing ;) And are wanting to do something a bit out of the box. Quick look there and one thing you might want to enable is
"Serve cache records even with TTL of 0" Prob give you better cache hits.Your hide options are exactly that - they will NOT answer those sorts of queries.. Unless you were going to let the public query it there is no reason to enable those... Unless you think someone on your own local network or connected to your vpn is going to query your unbound for its version info and then from that HACK it ;)