Multiple LAN networks on one LAN Port
-
@stephenw10 said in Multiple LAN networks on one LAN Port:
Yes, what is your pfSense LAN interface configured as right now?
From what he stated above
(The IP address of pfSense box is 192.168.1.247).
I would be more curious what the gateway is set for on the clients in the 192.168.1/24 network - and what they are set for in the other segments. Are they pointing to SVI's on the cisco? Can 192.168.1/24 access your other segments? Can your other segments access 192.168.1/24?
Just my guess but seems more like he is trying to combine his previous setup that had 3 routers using those 3 different segments into 1 box (pfsense) ? But that is just a guess - and it is common for users to state they have a L3 when all they are using it for is L2.. My sg300's at home are both in L3 mode - but I just use them as L2 for example... But the cisco sg300 is in fact capable of L3.
If memory serves more often then not when users state they have an L3 its not being used as such - which is always confusing ;)
How many interfaces does this pfsense box have? Are the 3 ISPs all public IPs into different physical interfaces, are they vlans into the same physical port on pfsense? Etc.. We can for sure help you with any sort of configuration you want - be it pfsense doing all the routing, be it with a downstream. But info is required to help you get to where you want - how are you wanting to leverage the 3 different ISP connections - in failover, in loadsharing - what are the speeds of the 3 different connections. Do any of them have IPv6 that you want/need to leverage, etc.
-
@johnpoz Nice, missed that!
In which case, yeah, I'd bet this is running layer2.
But if it isn't and it's somehow setup correctly as layer 2 to that segment only you need static routes in pfSense to the other subnets and firewall rules to allow them on LAN.
Steve
-
Hello all,
Sorry for the delay in responding.
First things first.
My present network is running on Fortigate firewall without any transit network (As my earlier diagram).
Am planning to move to PFSense.
My focus is to move from Fortigate to PFsense without disturbances.
Am attaching a more detailed diagram for better understanding....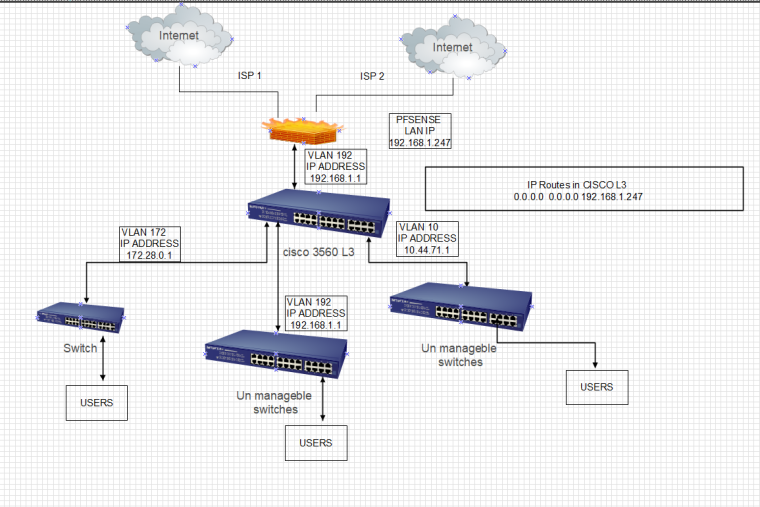
Now my only focus is to give internet to the users on 10.44.71.0/24 and 172.28.0.0/16 subnets. And by default 192.168.1.0/24 users are getting internet.
Let me know what should I do in PFSense firewall to allow internet to all the subnets.
Thanks in advance. -
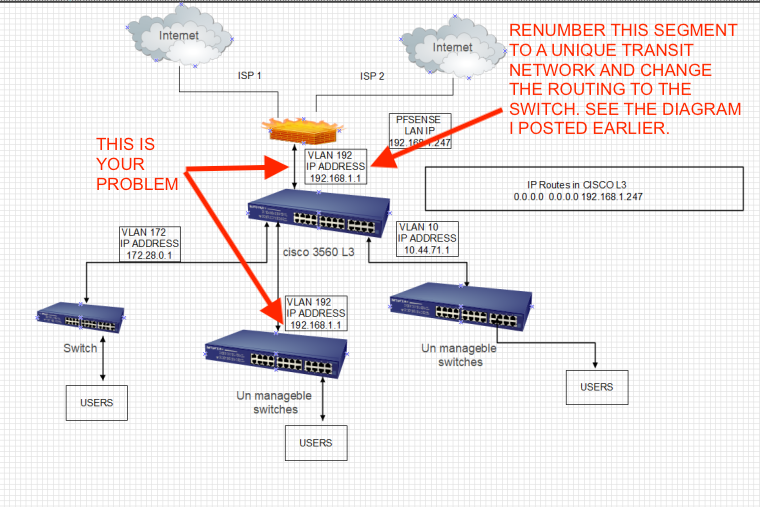
That is an asymmetrical MESS!!
You should FIX that!!! is what you should do!!
-
Yes, there are a number of better ways to do this but.....
If it really is routing at the L3 switch you need to add 192.168.1.1 as a gateway in pfSense and then add static routes to 10.44.71.0/24 and 172.28.0.0/16 via that gateway.
Then add firewall rules on LAN to allow traffic from those subnets.
If your outbound NAT rules are still at automatic those sunbets should be included. If not then they will need manual rules there too.
Steve
-
What he should do is do it correctly with a transit - takes all of 2 minutes to just use a transit network..
-
Yup. Or use VLANs and layer 2 if you don't need the routing speed between those subnets the switch provides. Or do need the filtering pfSense would provide.
Steve
-
@vijaydsk said in Multiple LAN networks on one LAN Port:
Hello all,
Sorry for the delay in responding.
First things first.
My present network is running on Fortigate firewall without any transit network (As my earlier diagram).
Am planning to move to PFSense.
My focus is to move from Fortigate to PFsense without disturbances.
Am attaching a more detailed diagram for better understanding....
Now my only focus is to give internet to the users on 10.44.71.0/24 and 172.28.0.0/16 subnets. And by default 192.168.1.0/24 users are getting internet.
Let me know what should I do in PFSense firewall to allow internet to all the subnets.
Thanks in advance.Care to share the running-config on cisco 3560 and interface assignments on pfSense?
-
-
Thank you.
With all your support I could able to give internet to all the links.@johnpoz
Yes I am in process of removing other networks apart from 172.28.0.0/16.
Once they removed only one big network will remain.
@stephenw10
I did as per your advise, I could able to give internet.
@Derelict
Thanks for giving me an idea, with which I could figure out the problem.Am attaching the backup (off course after taking precautions
 ) of my configuration.
) of my configuration.
It may be useful for any one who has got the same issue, they can follow the same.
Please let me know attaching backup is a violation, will remove for sure.0_1540451309619_config-pfSense.localdomain-20181020154833.xml