/28 subnet on DMZ
-
I'm trying to setup pfsense so that my public /28 subnet in on my OPT1 (DMZ) interface.
In order to get this working I've gone through the following documentation:
https://www.netgate.com/docs/pfsense/book/routing/routing-public-ip-addresses.htmlHowever the no nat role seems to mess everything up.
Because following the above tutorial to the letter didn't help I first set everything up so that the DMZ clients can get on the internet. This however shows the gateway address, which I assumed. As soon as I enable the NO NAT rule the DMZ lose their internet access although I've created a rule on DMZ to allow all outgoing traffic.
The DMZ interface has been configured with the first available IP address in my subnet and the DMZ clients use that IP address as their gateway.
I'm not sure what I'm doing wrong here and I hope someone is able to give me some pointers.
Kind regards,
Ronald -
Is the subnet routed to you on a separate interface subnet address or is the /28 on the WAN interface itself.
You can do anything you want in the former case, in the latter your best option is 1:1 NAT to private addresses inside.
-
If my provider, Hetzner, has configured it like I asked to my configuration is as follows:
Physical server gets an IP
PF sense on vmware receives a different IP on the WAN interface and the /28 is totally different and should be routed to the PF sense WAN IP.Anyway if this configuration is done right by Hetzner I assume the link I send in my first post is what I should be using, right?
-
Yeah. Put the /28 on the inside and bypass outbound NAT for those sources.
-
Maybe I'm doing something wrong or pfsense is working against me somehow.
I've followed the instructions, however this led my DMZ clients to be unable to reach outside.For some reason I decided to try the following;
Under firewall/Nat/outbound I created a mapping with:- Interface: WAN
- Source: My DMZ subnet
- Source port: *
- Destination: *
- Destination port: 80 (instead of blank as in the instructions)
- NAT Address: NO NAT
- NAT Port: *
I also added a second identical mapping with destination port 443.
Under firewall/rules/DMZ I created the following rule :
- Protocol: ipv4 *
- Source: DMZ net
- Port: *
- Destination: *
- Port: *
- Gateway: *
With just one of the 2 mappings and this last rule I can now ping to the outside.
In order to also test webbrowsing I also created the second mapping. This however made no difference.
With these mappings and rule I can only ping outside but nothing else.What am I missing here?
EDIT: If I leave these mappings and rule but don't fill anything in in the destination port I can't ping outside.
-
What is the IP numbering of your WAN interface?
What is your DMZ subnet?
-
The IP of the WAN interface is:
144.76.37.145
and the subnet is:
5.9.254.80/28 -
OK so you need to number an inside interface with something like:
Address: 5.9.254.81 /28
That lets you set inside hosts to:
Available: 5.9.254.82-5.9.254.94
They should set their default gateway to: 5.9.254.81You need firewall rules passing from those source addresses, all protocols.
No idea why you are setting the destination port to 80 on your NO NAT rule.
Outbound NAT only affects connections initiated from the inside.
Anything coming in from the outside is handled by the rules on WAN and the stateful firewall.
-
That is indeed exactly how I have configured my setup.
Just to be sure I disabled the rules on the DMZ and created 1 new allowing everything outside and instead of DMZ NET as source defined the test client IP address (5.9.254.82).
Under outbound NAT I removed the destination port setting. I know I shouldn't have messed with that in the first place but now it behaves just like before and the test client lost all possibilities connecting/ping to the outside.
Only when I define some port number in outbound NAT is it that the client can ping outside, no browsing however.
-
You're going to have to post your rules and outbound NAT.
This all just works unless they are really not routing those addresses to you.
-
Just a quick question, is this behavior consistent with Hetzner not routing my subnet to the proper (WAN) IP Address?
-
Depends.
You can tell whether they are routing it to you by packet capturing on WAN.
Packet capture for one of the DMZ IP addresses. Ping it from the outside. If the ISP ARPs for the address, they are not routing it. If the pings just show up to that destination they are.
-
Thanks for the tip, why didn't I think of this sooner. Would have saved lots of headache.
It seems after a packet capture that indeed the subnet is not correctly routed by Hetzner.
I'll come back with an update after I got them to route correctly.. -
Okay, it seems that they (Hetzner) have now router everything correctly.
To be sure I did a factory reset of pfsense and configured it again. Unfortunately nothing seems to have changed, DMZ clients still can't connect to the outside.
I've included several screenshots of my configuration.
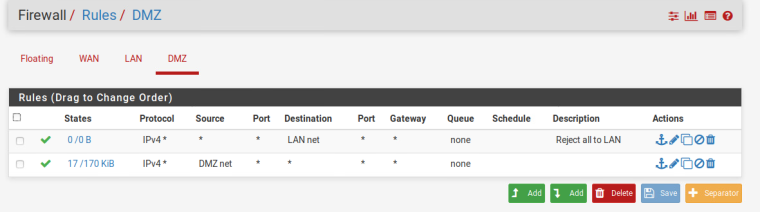
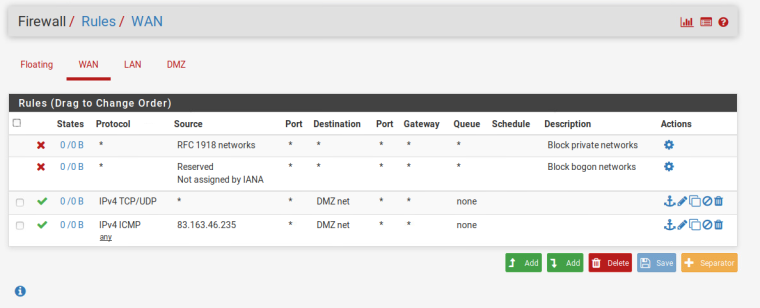
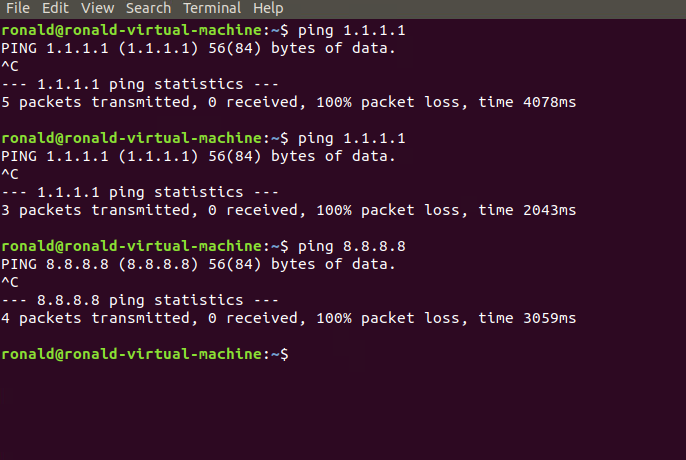
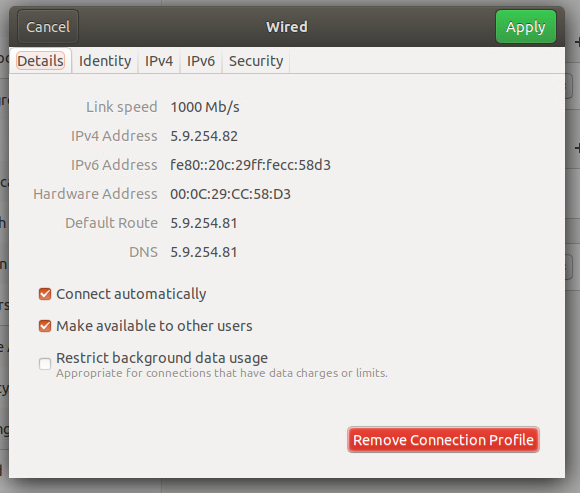
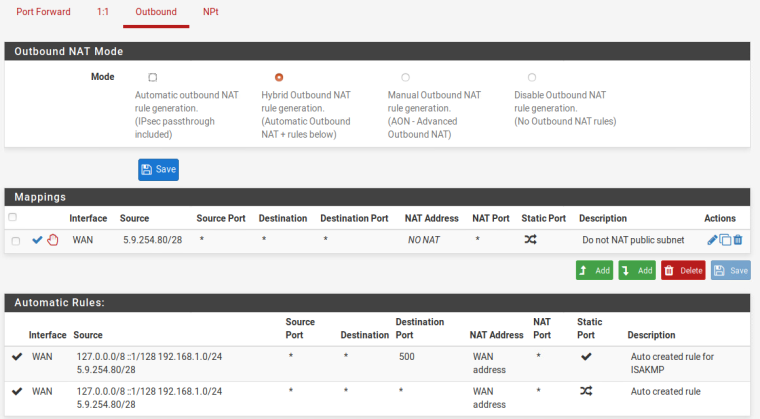
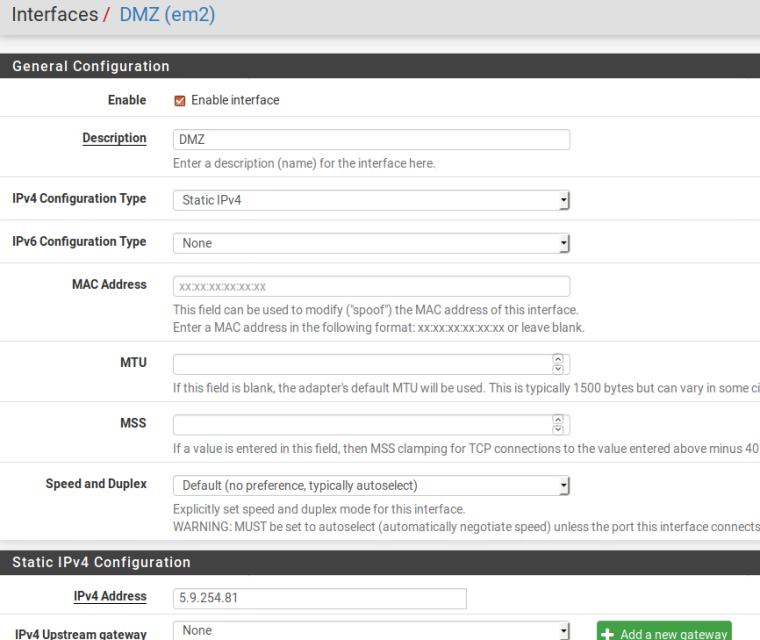
I hope this helps in trying to figure out where I went wrong.
-
Thanks for the support given so far. At seems as though I was to early. A couple of hours after Hetzner said they made the change in routing it started working.
So now everything works as it should.