FTP Server Behind pfSense
-
Before I receive the usual comments...
- No it has to be normal FTP.
- No I cannot change it since it would require getting an entire industry (the Automative Industry) to change, which is something I do not have the ability to do.
We have an FTP Server (ProFTPD) on a server that is behind pfSense.
It works find in Passive but we MUST have it work in Active (again due to not being able to change anything outside our control).
pfSense -> NAT is setup to Pass all port 20 and 21 traffic from anywhere to the private IP address of the machine running the FTP Server.
pfSense -> Firewall is setup to Pass all traffic (both IPv4 and IPv6 -- just in case) from the private local network (which includes the FTP Server) to the rest of the world.
As an added bonus.... pfSense is behind an AT&T U-verse Gateway (Pace 5268AC) which is setup to Allow and forward all traffic to the public IP address for ports 20 and 21 to the firewall (pfSense).We would like it to work in Active, not just Passive.
Any reasonable thoughts? -
Active mode requires an ALG at the FTP CLIENT side. There is nothing you can do on the server side to make it work.
-
@rsecor said in FTP Server Behind pfSense:
pfSense -> NAT is setup to Pass all port 20 and 21 traffic from anywhere to the private IP address of the machine running the FTP Server.
Learn how FTP works would be my suggestion.. Port 20 is never going to be destination port in FTP... Its a source port that would be used to talk to the port in an active connection.
As stated by derelict if your ftp server is behind pfsense.. If your not blocking your ftp server from creating outbound traffic, active not working has zero to do with the server side... There is NOTHING you can do on pfsense to have this work if the client doesn't allow the data connection from your server.. Or for that matter sends the wrong freaking IP in the first place. Have seen many a client send their rfc1918 IP..
-
@Derelict The server the connection is coming from had no issue connecting to other servers via active. If ALG is not on the FTP Client side what would this mean?
@johnpoz My understanding from http://slacksite.com/other/ftp.html is that under an active connection Port 20 is a data port on the server which could receive data from the data port on the client side. Is this incorrect?
I tried it from a different machine out in the wild with some debugging on showing that the data port the client machine is opening up is received by the server but subsequent data port related commands die after a timeout.
ftp> pass
Passive mode off.
ftp> ls
ftp: setsockopt (ignored): Permission denied
---> PORT x,x,x,x,224,109
200 PORT command successful
---> LIST
425 Unable to build data connection: Connection timed out -
FTP Servers inside the firewall:
FTP in active mode requires an FTP Application Layer Gateway at the client end to open the ephemeral destination port sourced from the ftp-data port (port 20) for the data connection from the server to the client based on what it sees in the FTP protocol stream (the PORT command sent from the client telling the server where to connect for ftp-data).
If the FTP Data connection is allowed from the server outbound by the server side firewall the server side firewall's job is done.
Looks to me like the client does not have permission to open the dataport listener on the local host based on those logs but not sure what you're using there.
-
@rsecor said in FTP Server Behind pfSense:
Port 20 is a data port on the server which could receive data from the data port on the client side. Is this incorrect?
It would never be used as a DEST port... It would be the SOURCE port... So there would never be a reason to port forward it anywhere..
PORT x,x,x,x,224,109
So that command is telling the server to contact IP x.x.x.x on port (224*256)+109 = port 57453... Now it would more than likely do that from "source" port 20... So on the client side port 57453 has to be allowed and forwarded to the client.
20 never comes into play on any forward or firewall rule.. Unless the server outbound firewall was set to say only allow outbound traffic from source port 20.. 20 is never need to be forwarded in any ftp setup be it active, passive..
-
From the other side of this (the client side) is able to connect active with no problem elsewhere.
Which is why we believe it is something on our side. -
Well sniff the freaking traffic... Do you send SYN to their port they call for in their control channel? If so then its NOT you!!
If your not sending the SYN to their data port then it is you... But there is NO setting to do in pfsense that makes this work... The client side is the one that has to allow the traffic... If your not blocking your server from making outbound connections on any port the data connection is on then its NOT pfsense.
Simple sniff on pfsense wan will tell you this in like 30 seconds..
-
Here I fired up ftp server on my nas... Did a simple port forward - sniff and boom there you go..
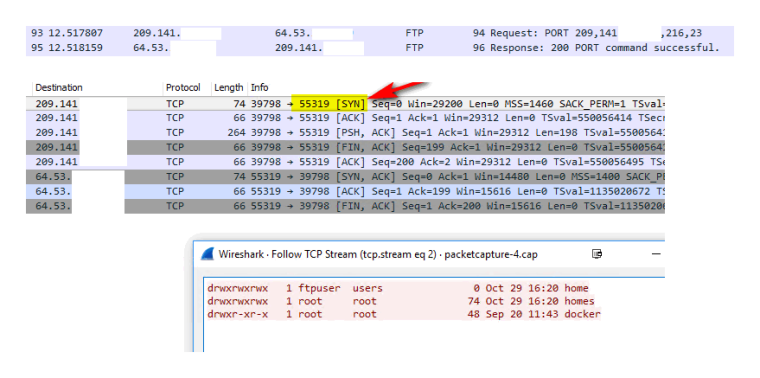
You can see the port command 216*256 + 23 is port 55319... There you go you see my syn and then answer, etc.
Now since pfsense is doing NAPT source port would be random that pfsense changes.. that is how any nat works.. Are they restricting you have to come from source port 20??
validate you send the SYN...
-
Static source port 20 outbound NAT rule. That's probably it.
-
Get a routed public IP and route it directly to the machine running the FTP server (you want it in a DMZ anyway). This way the FTP server is directly connected to the Internet and no NAT is happening, any issues when using either active or passive are then on the client side.
-
Just kill FTP with
