All freeradius eap-tls authentications fail when an SSL revocation list is enabled
-
I've been configuring a new Netgate appliance to replace an obsolete model. I'm having an issue with the freeradius package on the new appliance. The old appliance has freeradius 0.15.5_2 on pfsense 2.4.2-RELEASE-p1, while the new is freeradius 0.15.5_5 on pfsense 2.4.4.
Freeradius is configured to authenticate eap-tls from my wifi clients. The certificates are issued using the pfsense certificate manager.
Authentication with eap-tls works fine until I enable the ssl revocation list in the 'Certificates for TLS' section of the eap config. If I leave this as 'none', authentication is good. If I chose the CRL I've configured in the cert manager, then all logons fail, even if I have an empty CRL. I've tried recreating the CRL, to no avail.
The error I get is: 'Login incorrect (Failed retrieving values required to evaluate condition)'
On the old system I could enable the CRL without having any logon issues. Although, in that case I even people with revoked certs were still allowed on the network, even after I restarted freeradius as the instructions say, so now I'm having the opposite issue, where nobody can logon as long as any CRL exists.
-
I can test this when I get home..
-
Hmmm yeah this looks to be broken.. Have to look into this more.. But clearly something is not right..
-
Ok this came up before here
https://forum.netgate.com/topic/70749/freeradius-2-with-eap-tls/9And that jogged my memory.. From a quick test I don't think the ca and crl are being combined.. When you look in
/usr/local/etc/raddb/certsAnd you change your freerad to use your crl.. Doesn't look like it adds it to your ca.pem file? Need to look at if further.. But there also seems to be an issue with 2.4.5 and freerad checking cert attributes... I will look to see if crls are working in 2.4.5.. They for sure use to work.. Would have to fire up a copy of 2.4.3 to test - all my systems have been moved to 2.4.4 or 2.4.5
-
Ok... Seems if there is NO certs in the crl it doesn't get added to the pem.. So I created a dummy cert, then added it to the crl.. And now it does get added to the ca_cert.pem file
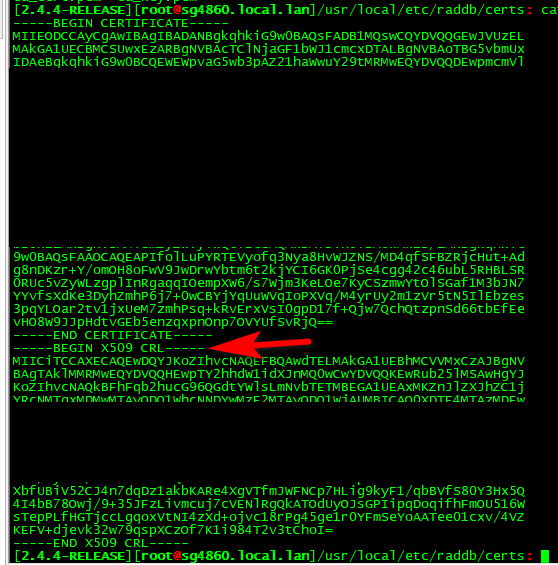
I am not sure if it has always been this way or not? But should prob be documented somewhere or changed so that CRL gets created even if empty and added to the freerad ca pem files that get created for freerad to use.
I have to look into who manages the freerad package to discuss..
-
Thanks for checking. To be clear, my issue occurred even with a non-empty CRL. In other words I had a CRL populated with several revoked certs. My own cert was not revoked, but I was unable to logon. As soon as I disabled the CRL in the freeradius settings, I was able to logon. I then tried with the empty CRL and had the same issue.
-
I don't see any code in FreeRADIUS that checks to see if the CRL is empty or not.
If it finds the CRL it puts in the text of the CRL.
Before you added the dummy cert did your CRL have a
texttag in the config with content? -
What I found jimp was that if the CRL was created but empty everyone failed.. But if you put in a dummy cert that was revoked it worked. When the crl was created but empty it didn't seem to update any info in the pem that there was even a crl..
-
Right but what I'm asking is if the config.xml entry for the CRL had a
textentry when it was defined but did not have a certificate present. -
oh didn't check for that.. sorry.
-
@smacdoug but if your crl was empty and didn't update the pem with CRL info - then yeah everyone would fail.. Because it can not find the CRL to even check if your client is in the CRL or not.. If you call for CRL - the pem has to have the CRL added to it - or everyone will fail.
Here is error that was logged for me, when no CRL in the pem - but crl set to yes
Oct 30 04:27:07 radiusd 81992 (13) Login incorrect (Failed retrieving values required to evaluate condition): [j-iphone/<via Auth-Type = eap>] (from client uap-pro port 0 cli D0-C5-F3-1F-EB-FF) 192.168.2.2 -
So now I told it to not use crl...
The pem was updated to remove the crl info from it.Then deleted the dummy cert that was in the crl. Then reenabled the empty crl and it update the pem show the X509 CRL info..
-
Ok - so I parsed out the x509 crl into its own pem... Then checked it with openssl and you can see no certs listed.. Before this was never added to the ca_cert.pem that freerad uses for the CRL.
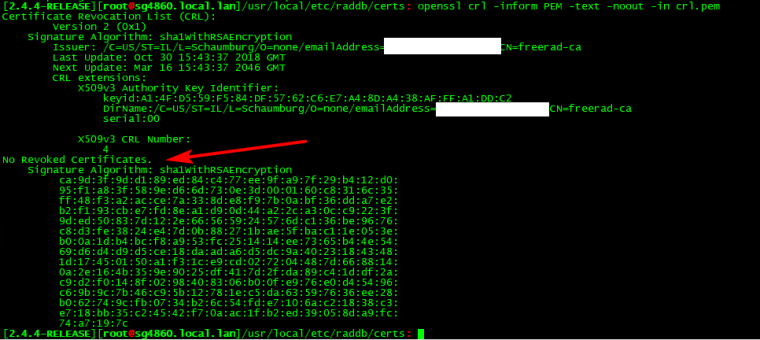
-
Maybe change this bit of code in
/usr/local/pkg/freeradius.inc:if ($crl_cert != false) { $crl = base64_decode($crl_cert['text']); $check_crl = "check_crl = yes"; } else { $check_crl="check_crl = no"; }To this:
if (($crl_cert != false) && !empty($crl_cert['text'])) { $crl = base64_decode($crl_cert['text']); $check_crl = "check_crl = yes"; } else { $check_crl="check_crl = no"; } -
Your the developer ;) Do you need a report of this to implement that? Or can you put it in without a redmine.
I'm not exactly sure what
$crl_cert['text']Actually does.. Normally that is a part of an array right.. To be honest having a hard time following what exactly you change is doing different. Other then doing some extra check on some variable.
-
I just meant to try that change to see if it helps.
The text is the PEM generated content of the CRL that gets updated when the system updates the CRL, usually when adding or removing a certificate or making another change to the CRL.
If that text is empty it would explain why you hit the error condition you did.
-
Oh would prob have to start over to try and recreate the problem.. Since its working for me now.. like I said when back to empty crl and its working, etc.
Maybe the OP can chime in.. It works just fine - even with empty crl it adds the crl to the ca_cert.pem file.
-
While it seems that you guys have it working for yourselves, at least with a blank CRL, my original issue still remains.
I never cared about blank CRLs, this was only a test I tried to see if a blank CRL would work any better than a populated one. My issue is that when any CRL is enabled, my logon fails, even though my cert is not in the CRL. I've tried deleting and recreating the CRL as well as using just a blank CRL, but the only time I can authenticate is when I leave the CRL setting as none.
-
And you validated your CRL is actually getting added the pem file?
-
There is a: -----BEGIN X509 CRL----- section in ca_crt.pem that appears when I enable the CRL, there is no crl.pem that ever appears.